The dessert for this particular event was to be individual chocolate cakes, but someone took them out of the ovens to soon and the centers where not cooked enough and still liquefied. Well, there was no time to take them off the plates and cook them more, so the Chef simply had his wait staff introduce the dessert as Chocolate “Lava” Cake! Brilliant!

In the embed code for a video, you can change certain numbers for the width and height of your video in HTML.
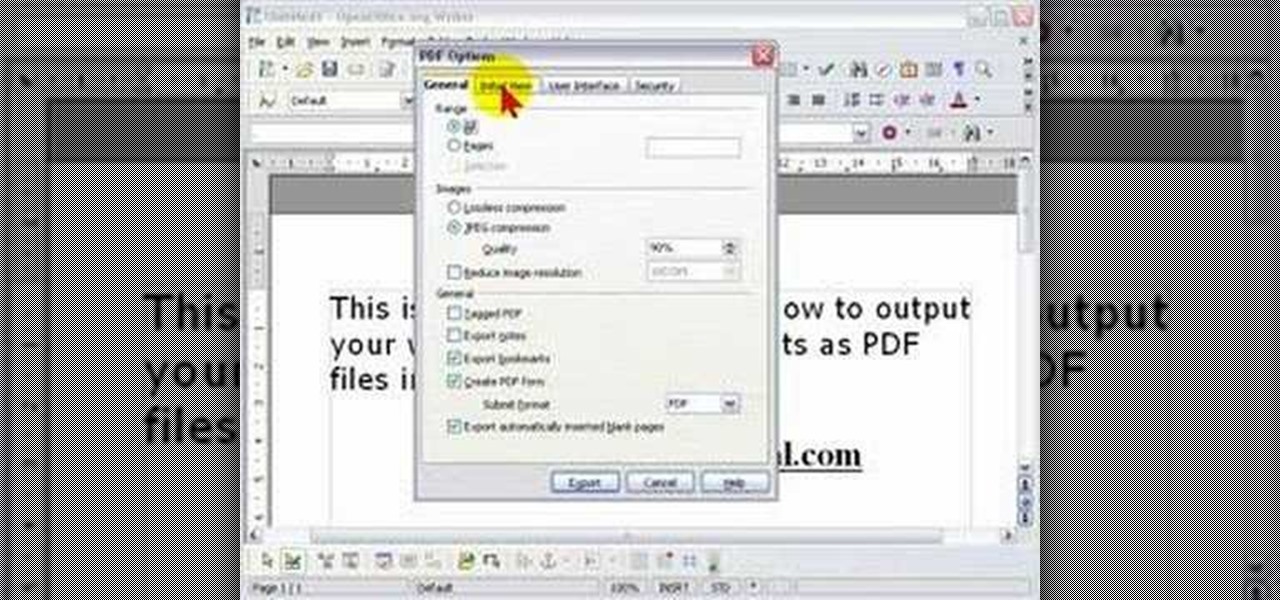
In order to protect your word processed documents, it is a good idea to export them for distribution as PDF files, which allows you to encrypt, and add password protection to your work.
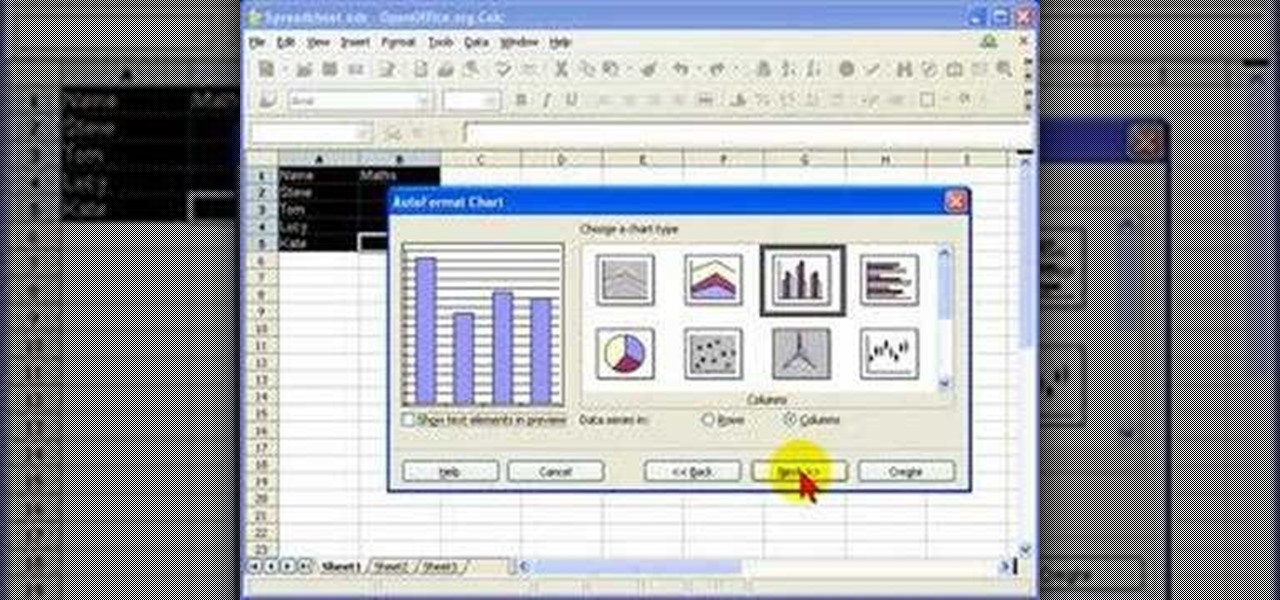
In this screencast tutorial, Steve shows you how to quickly and simply create a bar chart, from the data you have entered into your worksheet in Open Office Calc. If you're looking for a simple and clear way to represent your statistical data, then a simple bar chart is an option you should look at using. So check out this tutorial and start making OpenOffice Calc bar charts today.

There are many things that can make your audio sound better. One of them is simply making it louder. Just watch this installment of Izzy Video, and see how to adjust audio level in Soundtrack Pro.

This instructional how-to video, hosted by Simply Ming’s chef Ming Tsai, specializes in fresh oysters. Oysters are a very versatile type of seafood, they taste great with many or few ingredients. Watch this video cooking lesson as Ming shows you how the proper way to to shuck oysters.

This is actually a really easy and fun prank to pull off. What it does is simply switch the right click on your mouse, to the left click, and switch the left click, to the right click. Confused yet? Follow these simple instructions to test it out yourself, and enjoy your victims reactions when they get this prank pulled on them, trust me, it's funny!

Anuja and Hetal of ShowMeTheCurry.com show you how to make the perfect Basmati rice...simply delicious!

You can use a Gaussian Blur in a number of ways, but Israel Hyman's purpose in this video podcast is simply to expose you to some new possibilities. It’s a brief Izzy Video because he's just throwing out some ideas. In the future, he’ll show how to create the effect.

Want to learn the easiest way to get music off an iPod and onto a Mac? A Webb from howdoimac.com recommends using iPodDisk, a great little application that mounts your iPod as a hard drive. Your simply drag your music off the drive onto your computer and into iTunes!

Browned butter enriches just about anything it touches with a warm, nutty richness. From fish to squash, Brussels sprouts, even frosting, browned butter makes even simple preparations seem extraordinary.

What on earth does swinging the golf club on plane mean? Too many coaches assume we understand what the swing plane is. If, like the vast majority of golfers you don't, simply listen to this tip and you'll soon understand!

The fade is the most reliable golf shot shape to use under pressure - Colin Montgomerie swears by it. He reckons if you set up to shape the golf ball left-to-right in the air you'll have a far greater chance of hitting the fairway than if you simply aim straight.

With a little elbow grease, a sugar cube, and some can do attitude, you will be able to remove the logo off your cell phone. Simply polish up the area with the cube and remove any pesky logos left behind by the company.

This video is a demonstration of how to play latin patterns on the piano. A merengue pattern and a salsa pattern are demonstrated in Cmin. The patterns start simply and gradually become more complex.

Want to give your home-brewed DVDs and CDs a more professional look? You can do it easily simply by adding labels! This CNET video teaches you how to print labels on DVDs and CDs.

Roasted garlic has an appetizing flavor that is not as pungent as fresh garlic. To use the roasted garlic, simply remove the cloves from the head, and squeeze out the paste that is inside. This is perfect for spreading on bread or using in recipes such as mashed potatoes.

This may sound like a terrible thing to show you how to do, but the Neistat Brothers are simply victims of bicycle theft who got fed up. They use their own bikes to show you how to steal a bike in NYC (in broad daylight) so hopefully you can learn from them, how to better protect your ride.

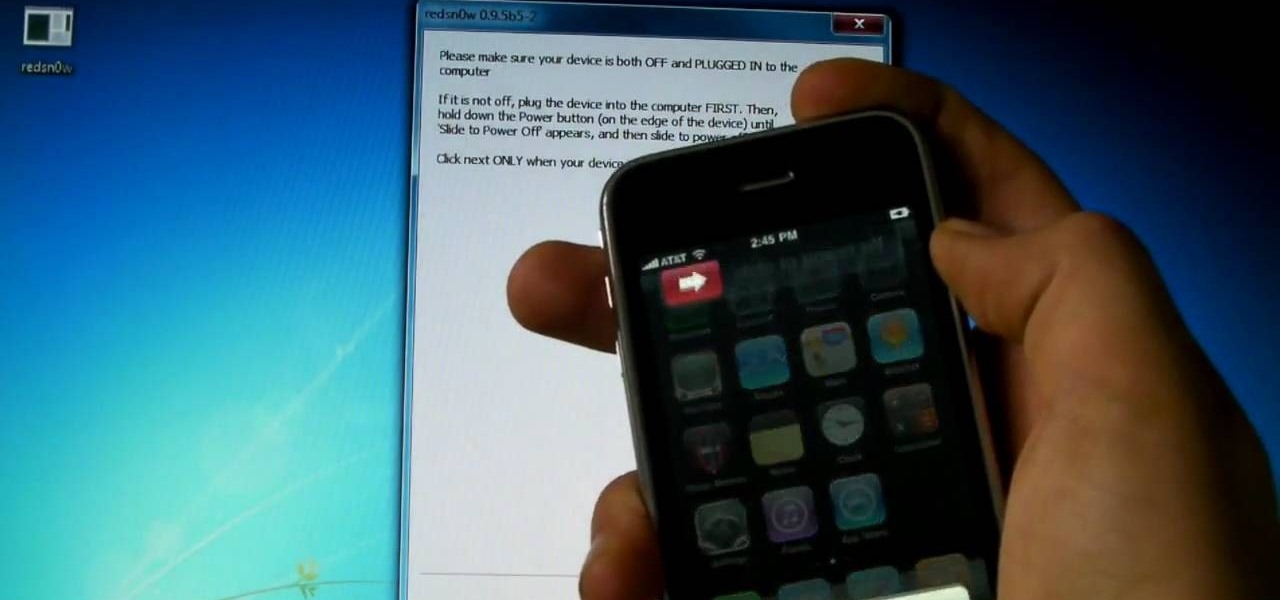
As of today, there are no legal barriers standing between you and jailbreaking your iPhone, iPad, or other mobile device. Hooray! If you were afraid of Apple coming to your house at night if you jailbroke your phone, you can finally let go of the fear and make your iDevice the beast it should have been all along! This video will show you how to jailbreak a iPhone 3G or iTouch 2G with iOS version 4.0 or 4.0.1 using Redsn0w. Now you can fully enjoy your Apple device.

Kipkay's ingenuity is enough to amaze us all, especially all of you indie filmmakers. These five tips for aspiring filmmakers will help you keep your sanity and avoid frustrating times. Have you ever got stuck in the rain while shooting? Have your recorder tapes ever gotten disorganized? Is your camera's display getting scratched up more than you want? Kipkay answers all of these questions with his five ingenious video tips.

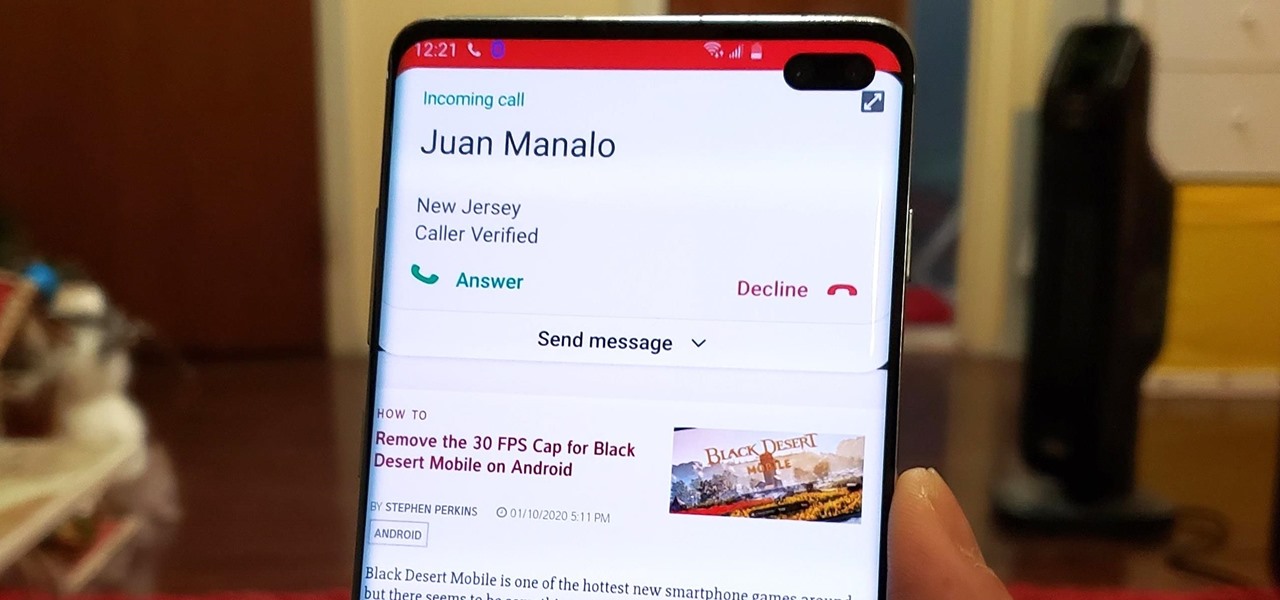
With all the things you can do with your Galaxy, it's easy to forget it's still a phone at heart, and incoming calls that take over your entire screen serve as a rude reminder of this fact. Thankfully, Samsung handsets like the S10 and Note 10 come with a setting built-in that aims to keep these interruptions to a minimum.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Users are often the weakest link when probing for vulnerabilities, and it's no surprise they can be easily fooled. One way to do this is called clickjacking. This type of attack tricks the victim into clicking something they didn't mean to click, something under the attacker's control. Burp Suite contains a useful tool called Clickbandit to generate a clickjacking attack automatically.

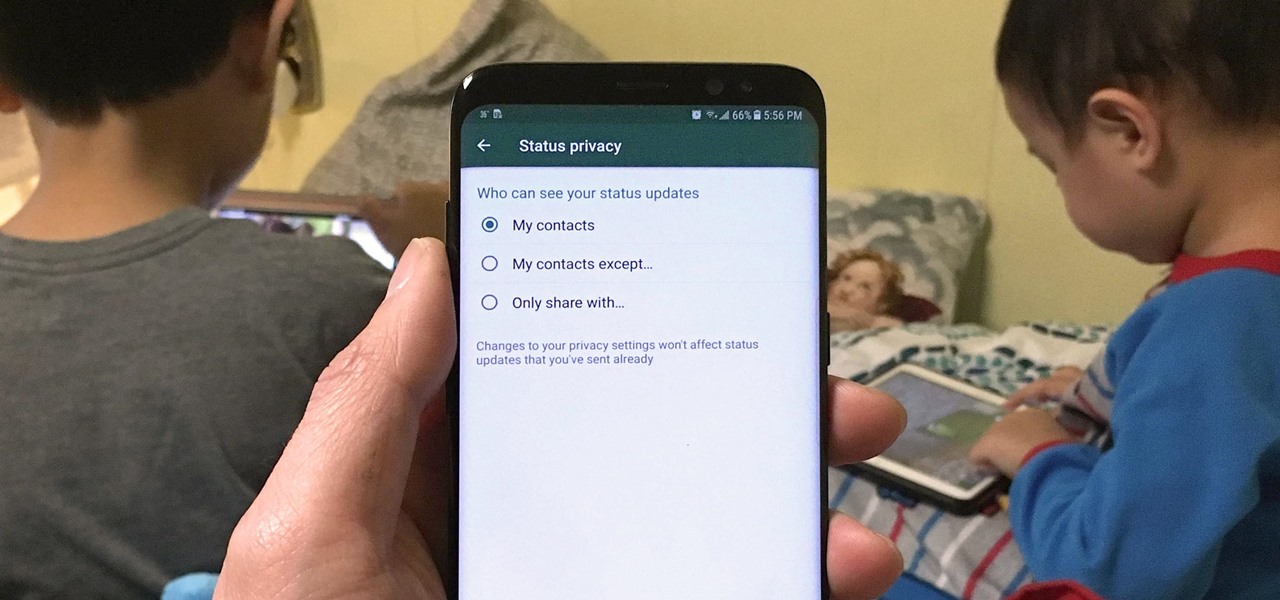
Sharing Stories via WhatsApp Status grants your friends access to your daily adventures in the form of GIFs, photos, videos, or simple texts. Like Snapchat, stories you share with your contacts disappear after 24 hours, giving you an extra layer of privacy since anything you post will not be permanent. And if you want to limit who can see your private stories, WhatsApp also has you covered.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

Volunteer project Standard Ebooks strives to enhance some of the work available from Project Gutenberg and other public domain text sources, making them easier on the eyes.

Music is definitely more immersive when it's accompanied by a bit of visual stimuli, which is why CyanogenMod and other custom ROMs have started integrating music visualizers into elements of the Android system UI. It's a great effect, but it's not necessarily something that's worth replacing your stock firmware over.
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account?

Sideloading apps on Android is incredibly easy—you just have to enable "Unknown sources" in your device's Security settings, then you're free to run an APK installer file to get the app installed.

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

I rarely receive spam mail, but every now and then I’ll get an email from Cat Fancy Magazine. I’ve never read an issue of Cat Fancy Magazine or been to their website. Actually, I’m allergic to cats. So how did they manage to get my information?

Incorporating features such as CarPlay, UI enhancements such as the new call screen, and several bug fixes, iOS 7.1 was the first major update to Apple's operating system since iOS 7 was released in June of last year.

Do you have an Alfa AWUS036NH Wi-Fi adapter that claims it can go to 2000 mWs, or some card that can supposedly transmit power over 1000 mW? If so, you may have run into problems setting your card's TXPOWER higher than 30 dBm, which is about 1000 mW. Well, I will show you how to break that barrier and go as high as you want!

You know those pretty twinkle light covers you can buy at Urban Outfitters or Home Goods? You can actually make them cheaply - i.e., with almost no money involved - at home.

Girls love bling, and little girls love it even more. Make your little lady as fashionable as can be by making these no-sew embellished headbands.

What's better— forking out the dough for a new headlight or simply restoring it to its original beauty? The latter is definitely the choice for penny-pinchers, and is easy to accomplish with a restoration kit from 3M. This video will show you how to use the 3M Headlight Lens Restoration System to restore your headlight's shine.

There is an easy way to make sure that dripping candles don't get wax all over the frosting of your next birthday cake. Simply place a hard candy like Life Saves around the bottom of each candle. Voila!

Blisters are a part of life for people with physical hobbies and professions. Many simply pop them and cover them up to treat them, but this is the wrong way to go about it. This video will teach you the proper way to treat blisters on your hands or feet.

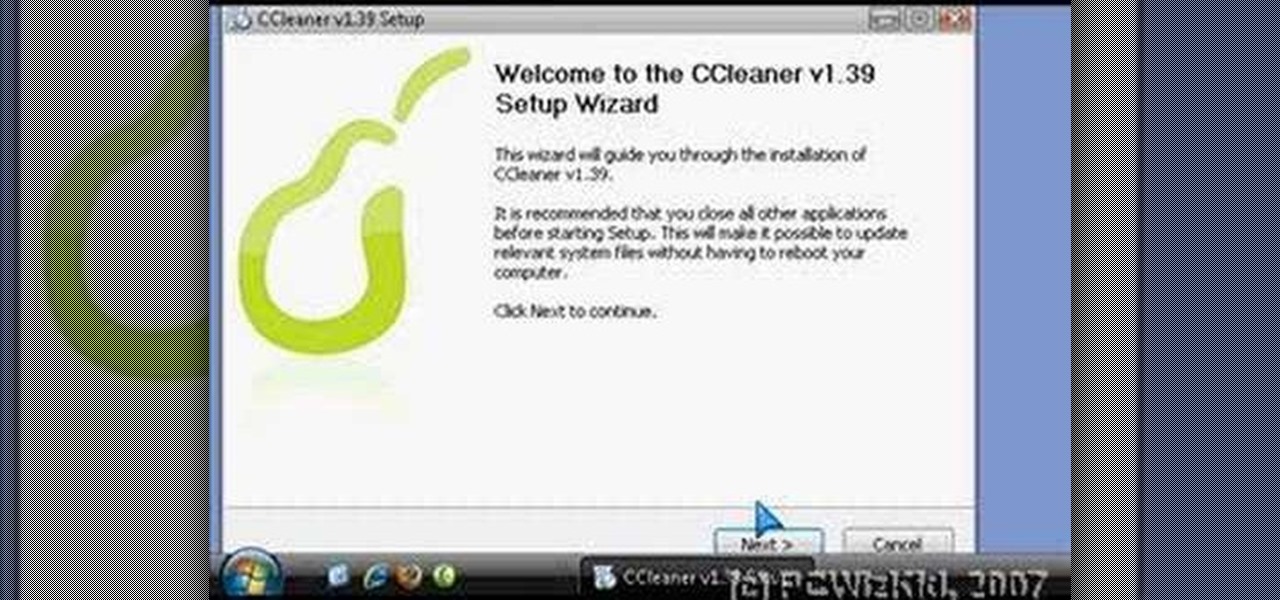
There is a built-in tool in Windows Vista that allows you to clean up your hard drive and system, and it could be found by simply searching for "disk cleanup" in the start menu. But this provides a really basic cleanup, so for all of you who want something more extensive, there are free alternatives available on the web. Once is called CCleaner, which is a lot better. It's the number-one tool for cleaning your Windows PC.