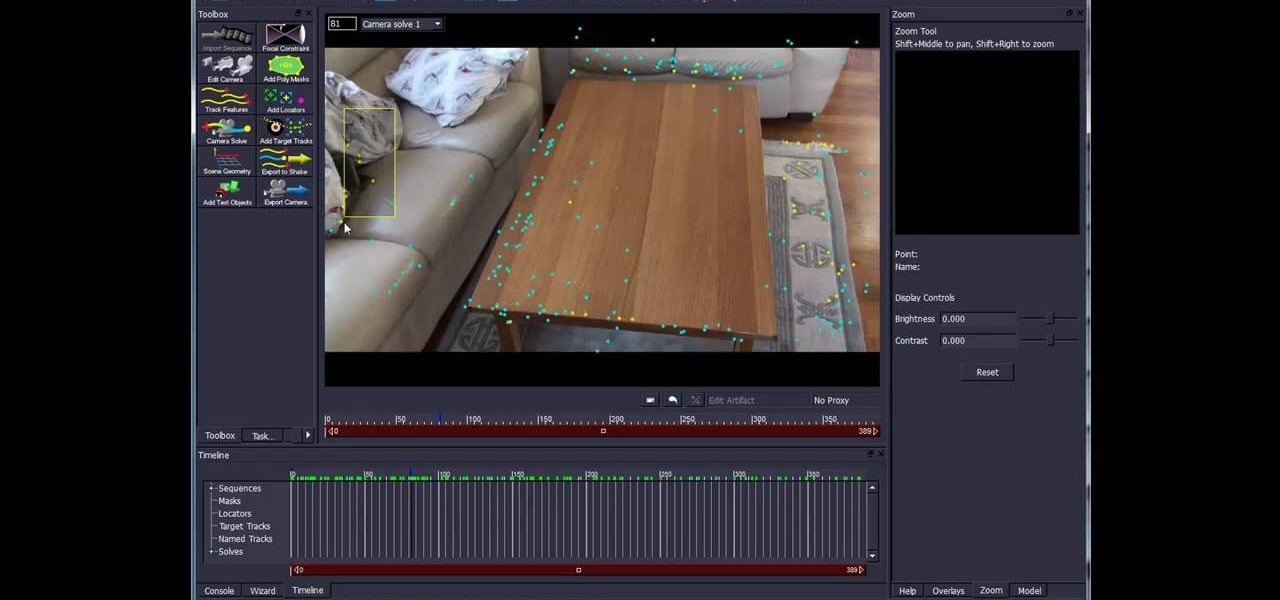
Creating movie-quality 3D images takes more than just 3DS Max. It takes a village of graphics programs to really make it look professional. This nine-part video tutorial will teach you how to create a hole in a coffee table using a combination of 3DS Max, After Effects, and the matchmoving software Boujou. This is high-level stuff, but the instructions are great and this video should have you compositing 3D images in no time!

This 2 part video will show you to make a classic Victoria sandwich sponge cake. Follow along as this sweet afternoon tea snack is put together. Fans of raspberry jam will be delighted to get a nice sweet filling. It's a lot easier than it looks! Just follow the recipe and the video!

Beautiful cabinets really make the kitchen, don't they? Not only are cabinets handy storage, they also lend a certain level of elegance to the room depending on their craftmanship. If you would like to perform a kitchen makeover but don't want to hire someone else to do it for you, check out this eight part tutorial on how to build custom kitchen cabinets on your own.

Kim Perrin a certified mechanic shows how to do your own oil change. To accomplish this, you'll need oil, an oil filter, an oil filter wrench, and a ratchet.

Do you like adding garlic to every recipe you make. We'll you are definitely not alone. Learning how to mince garlic will take your love for garlic to the next level. This homemade solution will keep you away from the store bought variety, and will show how to create the perfect minced garlic effortlessly.

Three point lighting is the key to MAKING videos look professional. Tom Skowronski, the associate editor of Videomaker, guides us through the process of three point lighting. Three point lighting involves the use of three types of light to create a professional appearance when video taping. First, a key light is used to provide bright illumination of the subject. Then, a fill light cleans up the dark areas on the face. Lastly, a backlight fills serves to separate the subject from the background.

Everybody loves dogs, but not everybody can own one. Although… everyone can own and enjoy a painted dog. And if you want to learn how to paint a puppy dog yourself, this is the video tutorial for you. Make sure to pause the video after each step and look at the screen every few seconds while you are drawing.

Is your hatchet in need of a quick tuning? Doesn't quite get the job done anymore? It's time to sharpen it. This also applies to sharpening an axe.

Box Seats! Put the art back in party furniture with collapsible tables and stools.

It's Christmastime, so what better of a game to play than the winterized Icy Tower? And what better game to hack with Cheat Engine?

Watch this tutorial to learn how to glaze artwork (painting with transparency). Make sure to pause the video after each step and look at the screen every few seconds while you are drawing.

Watch this fine art video tutorial to learn how to draw the differences between male and female faces. Make sure to pause the video after each step and look at the screen every few seconds while you are drawing.

The fourth thing that every high-level tennis player does when hitting a backhand is follow through. Extend out in the direction you are hitting the ball, then smoothly bend the elbows and wrap the racket up over your shoulder.

This series of ping pong / table tennis videos demonstrate how to master the table tennis serve. Jim Clegg, a Level 4 Coach with the English Table Tennis Association and Head Coach of the Preston Table Tennis Association, explains and demonstrates how to do a table tennis serve correctly. Serving today is an extremely complicated topic. These are 9 in depth thought processes for a table tennis serve.

Learn how to do speed tube shoulder presses. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do dumbbell step-up with shoulder press. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do single-leg flat bench standups and sculpt your body without weights! Presented by Real Jock Gay Fitness Health & Life.

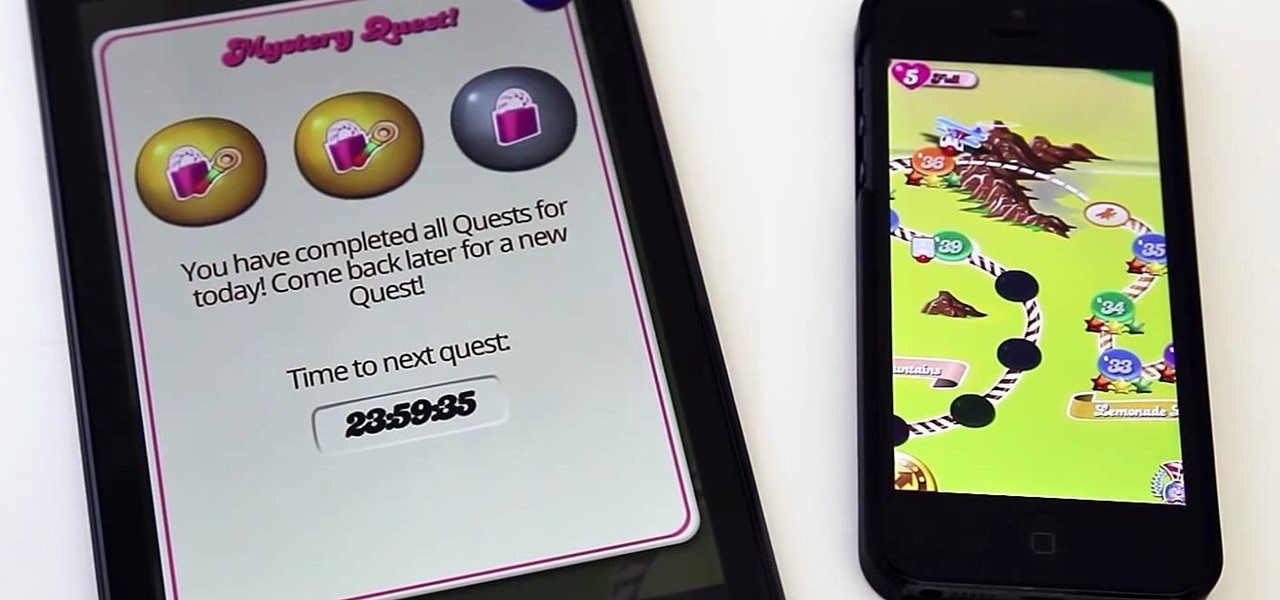
There's an easy time hack available for Candy Crush Saga that let's you bypass the time restrictions to you can play more games faster, and this video guide from KiboshGaming will walk you through it on both Android and iOS devices.

If you love the ocean and love swimming, it's time you step up to the next level… snorkeling. Snorkeling is one of the best ways to explore the underwater life, without fancy equipment or expensive training. And all you need is a snorkel. If you want a better look at what’s underwater, all you have to do is snorkel.

Check out this video to learn how to level the bad audio off a cheap digital camera preventing extreme highs and lows. In this episode of How In The Hell, Nick Allain shows how to level the audio from video taken with a digital camera at a live concert using a free program called Audacity.

One of the greatest trends to emerge from this period of home isolation is the live concert broadcast from bedrooms and living rooms across the planet. Though public gatherings are on hold, you can still impact people with your music and mixes. In fact, it's helping many people get through this confusing time.

Augmented reality already seemed like the ideal technology to advertise for a movie based on the premise of being sucked into a video game world the first time around. For the sequel, how about two times the immersion?

The landscape of augmented reality marketing is growing by leaps and bounds nearly every month, with Hollywood and the cosmetics industry leading the way.

Look Around in Apple Maps gives you a high-resolution 3D view of roads, buildings, and other imagery in an interactive 360-degree layout. We haven't had anything like this in Apple Maps since iOS 5 when Google's Street View was incorporated. Now, in iOS 13, seven years later, we have street-level views again, only better. But Look Around isn't available everywhere yet.

It's been proven that hackers can manipulate your screen with fake taps through specific exploits, so they can potentially hit the "Grant" button when you get a superuser request. This is the last thing you'd want to happen since the malicious app from that point forward has full system privileges. Luckily, using a fingerprint to lock your superuser requests can prevent this.

There's something extremely satisfying about hunting down your online adversaries and knocking them out with a well-placed shot, which probably explains why shooting games are still one some of the most popular time killers for iOS and Android.

With a fresh infusion of $9.7 Million in funding on its ledger, enterprise augmented reality company Scope AR has now expanded the functionality of its WorkLink platform.

Already a dominant force at the box office, Marvel Studios appears intent on establishing itself as the ruler of augmented reality media as well.

The Federal Communications Commission (FCC) has cleared a path for Google to move forward with hand-tracking technology that could pose a major threat to Leap Motion.

On Tuesday, Blue Vision Labs, one of three Google-backed companies working on AR Cloud platforms, announced its acquisition by ride-sharing company Lyft.

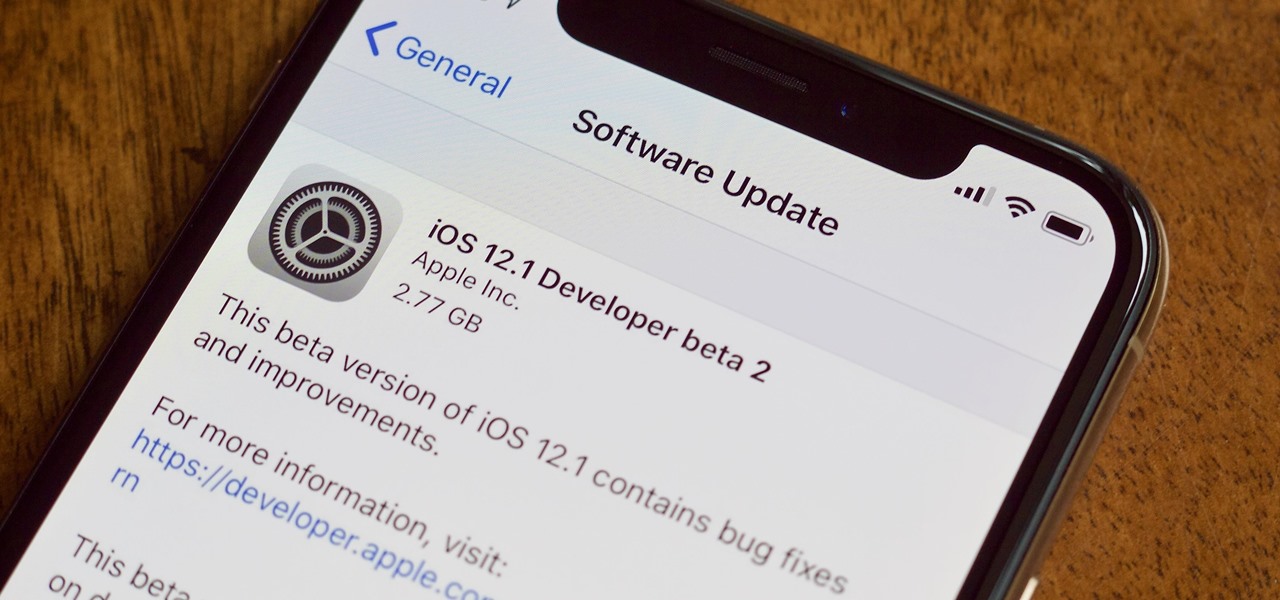
Public beta testers will be pleased to know that the second iOS 12.1 beta has just become available for iPhones. The Tuesday, Oct. 2 update features an impressive 70+ new emoji for testers to enjoy, including bald emoji, emoji with red hair, gray hair, and curly hair, among many others, as well as a patch for iPhone XS and XS Max devices suffering from charging issues.

Apple released the second developer beta for iOS 12.1 to testers on Tuesday, Oct. 2. The new update features over 70 new emoji, including emoji with red hair, gray hair and curly hair, and an emoji for bald people, among many others. It also introduces a fix for iPhone XS and XS Max suffering from charging issues, that some have dubbed "Chargegate."

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

The HoloLens team is finally beginning to realize that to truly engage the mainstream, augmented reality needs to make its way out of the lab or factory floor and onto the streets.

For years, Magic Leap has promised to deliver stunning augmented reality experiences that will outperform any other competitor, and a newly revealed partnership hints that the company may be able to deliver on those promises.

If you're looking for your gaming fix and nothing on the App Store is piquing your interest, you should give soft-launched games a try. These are games that haven't been released in the US yet because they're getting tested in smaller markets first. Using a simple workaround, you can install them on your iPhone in any country.

Taking a cue from the smash hit Super Mario Maker, Bandai Namco has soft launched PAC-MAN Maker in Canada ahead of a worldwide release. This is welcome news for mobile gamers, as you won't need a console to enjoy this classic arcade game when it finally touches down stateside. But if you want to give PAC-MAN Maker a shot right now, we've got you covered.

Assassin's Creed Rebellion is a welcome addition to the popular gaming franchise, garnering great reviews so far. Unfortunately, the game has been stuck in soft-launch limbo for almost a year, with no firm release date in sight. With a little legwork, however, you can try the game out for yourself right now.

Apple has been in hot water ever since the news that the company slows down iPhones with older batteries. The iPhone maker is now in damage control, offering customers a large, $50 discount on battery replacements. The question for you, though, is does your iPhone need a battery replacement in the first place?

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.