
In my first few articles, we focused on operating system hacks. These hacks have been primarily on older operating systems such as Windows XP, Windows Vista, and Windows Server 2003.

Kiatsu for head and neck pain uses a series of pressure points along the lines of the body. Learn how to administer this alternative medicine with expert tips in this free healing arts video series.

While there's an art to surviving the all-nighter, there's also an art to staying awake throughout the day when you're operating on little to no sleep. In 1964, the record for sleep deprivation was set by 17-year-old Randy Gardner, who stayed awake for an incredible 264 hours and 12 minutes. Now while we're not out to challenge Randy for his title, we can certainly look to him for inspiration in beating back our own fatigue.

Kiatsu massage for head and neck pain uses a series of pressure points along the lines of the body. Watch how to administer this alternative medicine with tips from an experienced masseuse in this free healing arts video series.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.
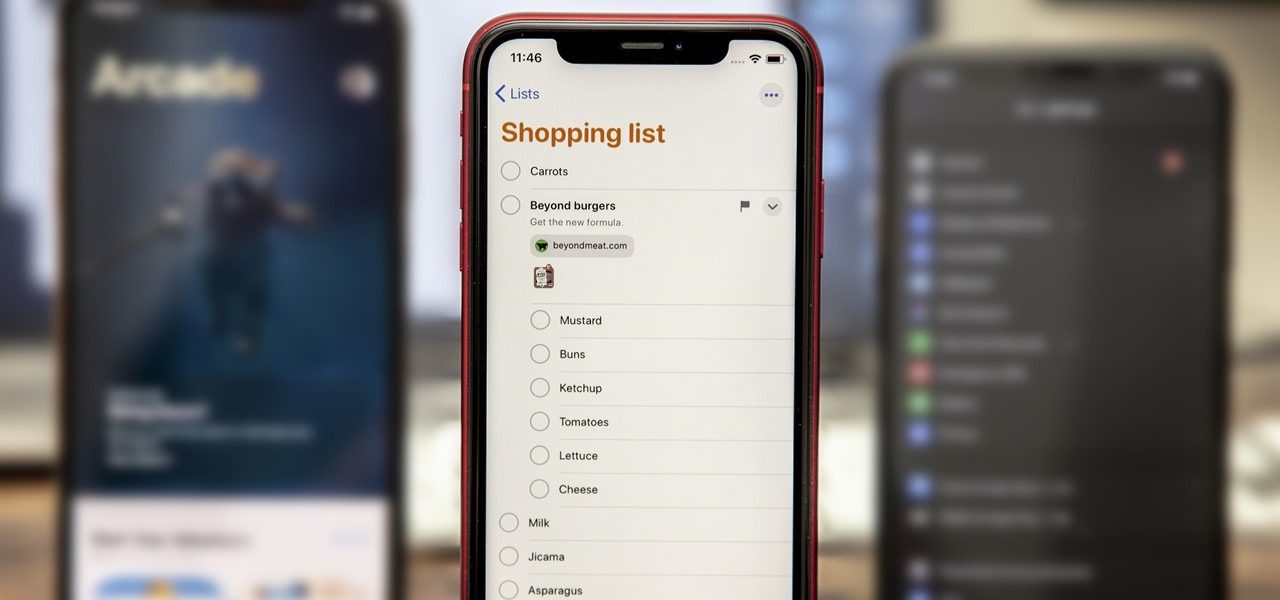
While the Reminders app has been largely ignored by Apple for years, iOS 13 finally makes it a force to be reckoned with. The app has been completely redesigned with easier navigation and more useful features that can compete with other task managers. After giving the new Reminders a shot, you may want to ditch that third-party to-do app you've been using.

With iOS 13, Apple included some major updates to the Reminders app for iPhone. Among them is the ability to add web links to individual reminders, including a rich preview of the link that can be minimized if necessary. So now you can add an Amazon link in a reminder to buy a present or a webpage for a recipe in your grocery list, to name just a few examples.

Apple's Reminders app has never been particularly sexy or appealing, but that changes in iOS 13. Although the productivity tool has always been useful for quick to-dos, it now has an overhauled user interface with several new features, including grouping lists together for improved organization.

While a viable version of consumer-grade smartglasses has yet to find mainstream success, two more contenders emerged this week, as Vuzix confirmed that a leak of a fashion-forward design is legitmate and Vivo introduced tethered smartglasses designed to pair with its new 5G smartphone.

The Apple rumor mill is getting its first real workout of 2019, and this time the whispers are more exciting than usual.

Reading the augmented reality news lately has felt a bit like reading a John Grisham novel, as the business side of things has dripped with legal drama.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

A core concept that has resonated through societies of the world over the course the last few hundred years is "knowledge is power." And understanding that concept gives us the drive to push further forward and learn as much as we can on a subject. At the moment, that subject for us at Next Reality is the recently released information about Magic Leap's upcoming Magic Leap One: Creator Edition.

The incidence of tuberculosis (TB) is dropping in the US, but the World Health Organization (WHO) considers it to be epidemic in the rest of the world — there were over 10 million new cases in 2016.

How can a drug used to treat cancer be effective against viruses, too? The answer lies in the drug's shared target — specifically, cellular components that control the activity of genes. A new research study showed that one such type of drug, histone methyltransferase inhibitors used in cancer clinical trials, has activity against herpes simplex virus, too.

Even though the Ebola virus was discovered as recently as 1976, over 30,000 people have been infected since, and half have died a horrible death. Since there's no way to cure the infection, the world desperately needs a way to prevent it — and the five similar viruses in its family, the ebolaviruses.

We've worked hard to reduce the flow of toxic chemicals into our waterways, which means no more DDT and other bad actors to pollute or destroy wildlife and our health. But one observation has been plaguing scientists for decades: Why are large quantities of one toxic chemical still found in the world's oceans?

The bacteria Klebsiella pneumoniae is a bad actor known for being antibiotic-resistant and causing a variety of serious infections in hospitals, including pneumonia, surgical site wounds, and meningitis. K. pneumoniae is something you do not want to encounter if you have a compromised immune system.

Bioluminescence — the ability of an organism to produce and emit light — is nature's light show. Plants, insects, fish, and bacteria do it, and scientists understand how. Until now, though, we didn't know how fungi glow.

Phase 2 of a Zika vaccine trial began in the United States this week, along with Central and South America.

A new study has found that up to half of people who think they have a penicillin "allergy" can still receive the drug, and other antibiotics with similar structures, without any negative reactions to the meds. Why? Because they're not really allergic, doctors say.

Arsenic occurs naturally in the environment, but it is also one of the most commonly found heavy metals in wastewater, deposited there by inappropriate disposal and arsenical pesticides, for example.

Marijuana is legal to use for medical purposes in 28 states and the District of Columbia, but the quick development of this new industry could have left some regulation issues in the lurch.

Although their effectiveness is waning, antibiotics remain a front-line defense against many infections. However, new science reveals using the wrong antibiotic for an infection could makes things much worse.

Ah, wine. The bouquet fills your nose. The rich finish fills your mouth with soft flavors of oak and raspberries. The wine warms your belly and soothes your mind. Yeast and their biochemical factory help create this feast for your senses. Thanks to a research group from France, we now have a little more information on how that process works and a little more appreciation for yeast's contribution.

Despite the availability of a vaccine against it, almost 50% of men aged 18-59 in the US are infected with the human papillomavirus (HPV). Why?

I'm sure I'm not the only one on here that has googled "Why am I always tired?"... and I'm definitely not alone when I say that all of the advice I've found so far is useless:

If you could save the world by eating a burger, would you? Two companies, Beyond Meat and Impossible Foods, are on a mission to redefine veggie burgers and eliminate all of the downsides of animal farming on our planet. With over five years of research and product testing, they've finally figured out how to make a plant-based burger look, feel, and taste just like real meat.

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

During my time living in dorm rooms and small apartments, I would find myself in need of many different appliances—a food processor for making hummus, a blender for vegetable smoothies, or even a mortar and pestle for muddling mojito-bound mint leaves. Luckily, there was one tiny, inconspicuous tool that solved all of these problems: the coffee grinder.

Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

I record close-cropped videos and take macro still shots with my smartphones on a daily basis, so as you would expect, I spend a lot of time cleaning these devices. Over the course of a couple years, I've fine-tuned my cleaning regimen, and at this point, it's down to a near-science.

Whites are the hardest color to keep looking bright and new after just a few months' time. Your sweat and oils quickly become stains, and colors from other clothes will eventually bleed into the fabric, discoloring your bright whites into something merely whitish. But before you reach for the bleach, the ultimate chemical cleaner, try some a few of these safer, less-toxic DIY solutions out instead.

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

By now, you've stuffed yourself with enough cranberry-soaked turkey to last you until next year. Still, there's a formidable amount of leftovers, and you're kidding yourself if you think you won't be craving them when you wake up tomorrow with a food coma/hangover.

The other day I was perusing my Instagram when I came upon a curious hashtag... #OnePotPasta. Intrigued, I investigated further and discovered a whole world that was previously unbeknownst to me.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Contrary to popular belief, taking someone's mind off their sadness and telling them to "cheer up" doesn't do much good. Misery loves company, and while it may be a tiresome cliché, there's actually some science behind it.








































