
How To: Make Gorgeous Drunken Pasta with This Key Ingredient
It's hard to argue with the notion that wine and pasta are a winning combination. I mean, millions of Italians can't be wrong.


It's hard to argue with the notion that wine and pasta are a winning combination. I mean, millions of Italians can't be wrong.

Microsoft's HoloLens comes with helpful features for capturing video and photos, but sharing whatever you record isn't as straightforward as you might expect. So here are the many ways to get your media off the device to share with the world.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

Google I/O is right around the corner, and everyone's expecting new virtual and augmented reality news. Here's what to expect from this week's announcements.

Obviously this is just a teaser, and who knows how soon we'll see something like this in real life, but just go ahead and watch the video first before you continue reading.

To serve as a framework for the "Nexus Imprint" feature in their new Nexus 5X and Nexus 6P smartphones, Google added native fingerprint scanner support to Android 6.0. Sure, Android devices have had fingerprint scanners in the past, but this is a unified, system-wide implementation that all devices can use—meaning that in the near future, we may finally start to see apps that let you log in to your account with your fingerprint instead of a password.

It should come as no surprise that, according to Details Magazine, nearly half of all people who make New Year's resolutions pledge to lose weight, eat healthier, and/or get fit. There are innumerable companies out there that are ready and willing to take advantage of this momentum: from those hocking "magic bullet" pills that will increase your energy or reduce your belly fat to the myriad shake- and juice-based diets that put you at a near-starvation calorie input—and will probably have you...

This is my first How-To on Null-Byte, so I hope it's not too complicated written, because I am not a native english speaker. I don't use pictures, but this Tutorial is a good supplement for my updated Tutorial here.

The morning started out like most of them do: I was hungry, and it was time to chow down on some breakfast. However, this particular morning had me craving something besides the usual milk and cereal.

If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streaming services don't work on your Chromecast or Chromecast 2.

Any other person can make plain pancakes... but only the most awesome of cooks can make stuffed pancakes. Luckily, this isn't a tough technique—in fact, it's so easy that you'll find yourself getting bored of the run-of-the-mill pancakes and dreaming of all the things you can stuff pancakes with, instead.
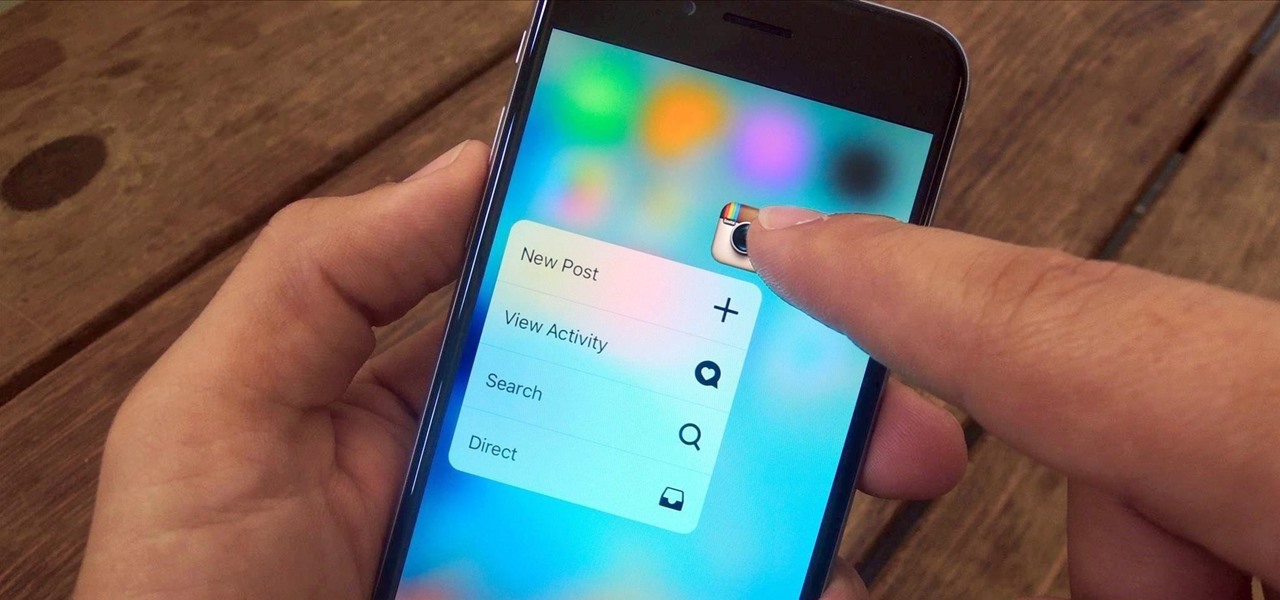
3D Touch is a new feature on the iPhone 6S and 6S Plus that's reinventing the way we interact with our smartphones. With just a little bit of added pressure when tapping on the display, you can perform Quick Actions from an app's home screen icon, "Peek" at emails, stories, and photos in-app, as well as perform other app-specific gestures. Since 3D Touch is such a new concept, here are some of the apps that currently support it, along with the shortcuts you can use.

There are few things that make me smile more than ice cream… or bread! So why not combine them for double the happiness? We've discussed the art of making ice cream bread before, but not everyone has the time (or, let's face it—the patience) to bake bread in the oven, no matter how few ingredients the recipe may take.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

You can beef up the security on your Mac all you want, but all the firewalls and antivirus apps in the world mean nothing when that can of soda tips over on your Macbook, destroying your laptop and all its data forever.

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

Heads up! We've done a new, more thorough review of the best Android file-sharing apps. You can check that out here. Our old file-sharing app roundup can still be viewed below for posterity.

So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.

Indoor electric grills are nothing new; George Foreman grills have been around for over 20 years now, providing healthy, smokeless grilling options for indoor use. Yet as nifty and fun as George Foreman grills are, indoor grills have never been considered a hot item for passionate and avid home cooks.

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

A landmark bill finally went into action this week that will allow American cellular customers to unlock their smartphones for free. The process of unlocking may vary between mobile service providers, but you can rest assured that you are now entitled, by law, to carrier-unlock your smartphone.

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.

Welcome back, my budding hackers!
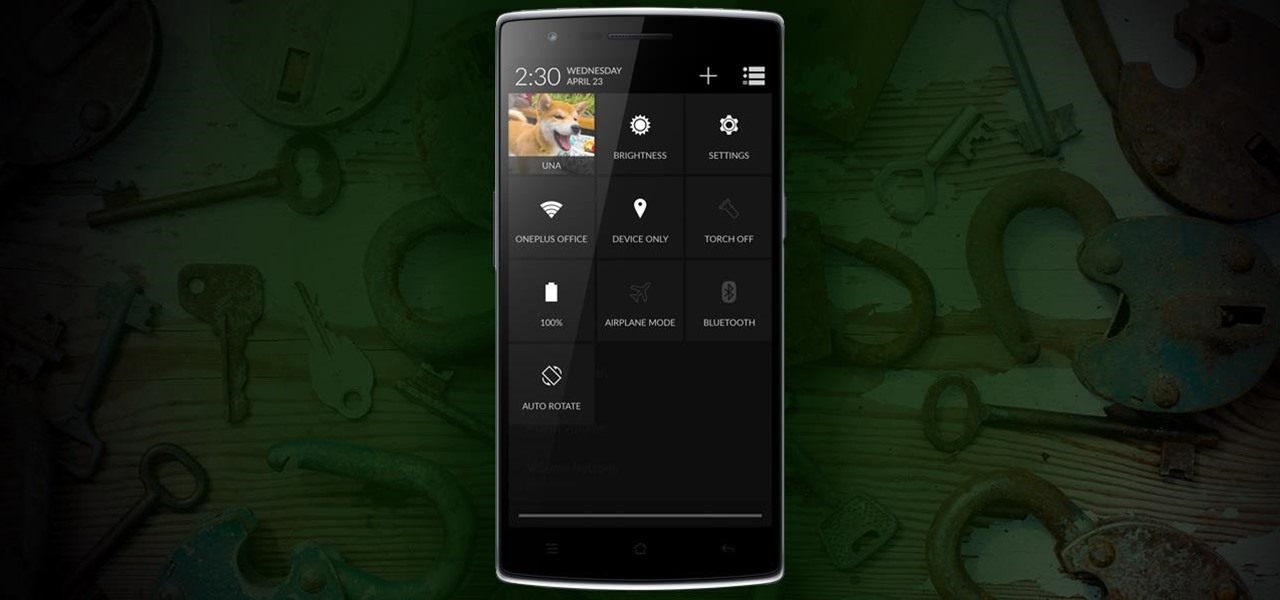
Due to its constant delays and lack of public invites, the OnePlus One is the equivalent of a unicorn in the Android community. I was lucky enough to win an invite in the OnePlus Storm of Invites promotion and have loved every minute with my new Nexus Killer since receiving it.

It took many months of cries from all around the internet—and a particularly large groan from an ex-Lifehacker editor-in-chief—but Apple has not only acknowledged the existence of its iMessage problem, it's promising a fix.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.
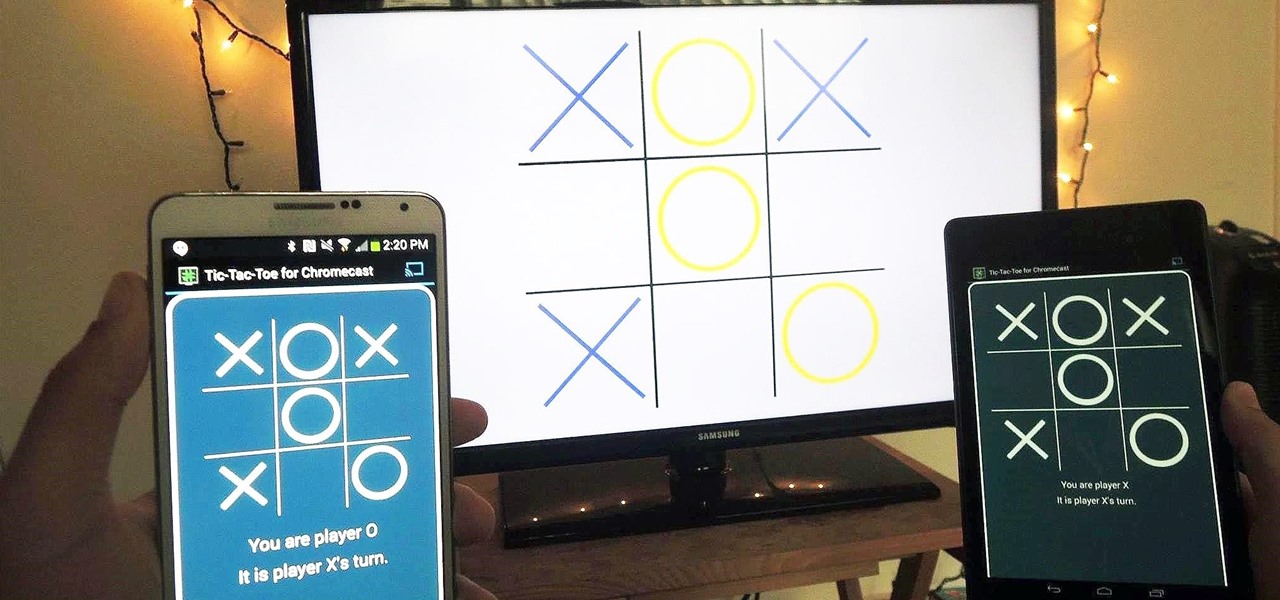
With the emergence of rumors that Amazon, Google, and Samsung are all making their foray into the gaming console market, it's a possibility that our Android-powered mobile devices might become tools that play a central role.

The original Kit Kat was a mutton pie served at a political club in London during the 18th century, which is quite different than the chocolatey version we're familiar with today. Kit Kat bars have been around since 1911, are produced in 13 countries, and have been sold in over 200 flavors in Japan.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Although mowing is key to keeping your lawn healthy and good looking, it isn't anything worth jumping up and down for when it comes time to doing it. As it turned out, the first time I mowed my lawn wasn't nearly as fun or exciting as Hank Hill made it out to be. Maybe it was the beer.
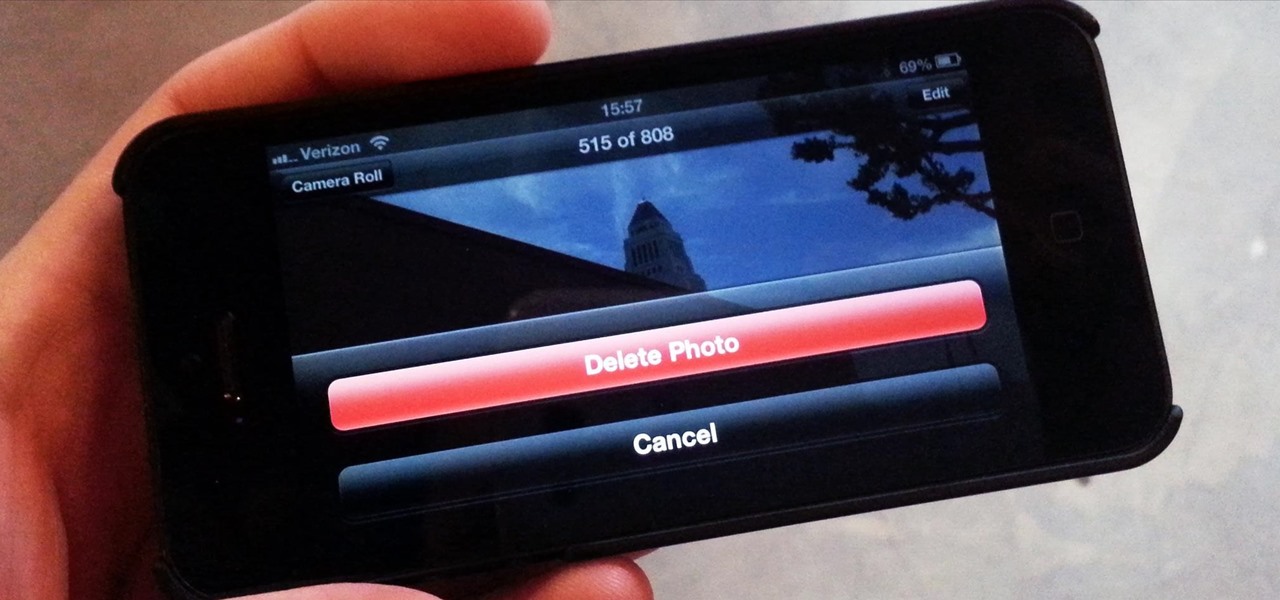
In one of Apple's newer ads, the company claims that "more photos are taken with the iPhone than any other camera." If this is in fact true, then it might also be appropriate to say that more photos are accidentally deleted on iPhones than any other camera.

If you thought humans were reading your résumé, think again. Robots do, and their one solitary objective is to systematically crush the hopes and dreams of those who don't make the cut. Instead of paying a few humans to read thousands of résumés over a couple weeks, many companies use computer programs that can do the job in less than an hour. In fact, at least 90 percent of Fortune 500 companies use what they call an applicant-tracking system, aka rejection machines.

Cinema is a matter of what's in the frame and what's out, according to director Martin Scorsese, who asserted that when describing his life's work. Getting the perfect shot can turn an otherwise ordinary scene into something great, both on and off screen.

Cross-dressing and gender-bending are nothing new, but the realm of Steampunk seems to be especially accepting of role-reversal in dress.

This post has been brought to you by the letter S. With the Christmas season fast approaching, it's time to ask one of the most important questions of our lifetime:

Timely costumes for Halloween are awesome—especially really obscure ones—because they're indicative of social awareness. In 2010, I remember seeing several Chilean Miner costumes, which I thought were great. 2012 brings new stories, new characters and more importantly...new Halloween costumes.

DarkStar One: Broken Alliance is an updated version of the space flight simulation video game DarkStar One (2006), and was made exclusively for the Xbox 360. It features updated graphics and presentation, making it the perfect space flight game for you wannabe astronauts.

Candy is not just for the kiddies. You’re wedding guests will feel like they’re in Candyland when they are presented with the whimsical wonderment of a candy buffet. You can easily match candy to your wedding’s color scheme and theme.

Want unlimited Tiki power on Island Paradise? Just use Cheat Engine to hack your way to more power. This is only for 1 use only.

If you can’t find the man of your dreams or maybe you’re looking for a new buddy, you can always stop looking and just draw him. After completing the basics your can style him and create whatever mood and features you like.