This video gives instructions on how to cite sources when giving a speech. When giving a speech, you want to appear persuasive and credible to the audience. In order to do this, you must cite the sources of your speech's content. Prior to giving your speech, research materials relevant to your topic. In the course of giving the speech, mention where you got your data. In this case, the speech is about Emotional Intelligence in the Workplace. While making your first main point, mention that "a...

Is your blog booming or just plain boring? IMaybe it's not boring, but you probably aren't getting much traffic, at least, not the amount you want. If you want to learn how to increase your traffic to your blog or website, this video has information pertaining to quick traffic.

All you science and astronomy nuts out there, pay attention, this detailed video tutorial series will tell you everything you need to know about using the Meade EXT Premier Telescope to ogle the universe.

All you science and astronomy nuts out there, pay attention, this detailed video tutorial series will tell you everything you need to know about using the Meade EXT-80-TC Telescope to ogle the universe.

With the growing popularity of buying local, many people are rediscovering the benefits of preserving fruit at home. Concerns over food origin, additives and preservatives are driving this trend and in just 20 minutes you can enjoy fresh produce all year long. Watch this how to video to learn more about picking fresh food and the preservation process.

This next tutorial is a classic prank that is easy to perform and will trick everyone around your car. It involves leaving a bag full of groceries, items, goods, whatever on top of your car and driving around with it on there.

Changing your iPhone ringtone can be a pain, even in iTunes. Other ways to change your ringtone include downloading software that takes up hard drive space and clogs your applications folder. There is another way, and it's a website called Audiko. It's a website for free ringtones for mobile phones and the iPhone. You just need to follow the instructions on the site and you'll have a new ringtone on your cell phone in no time.

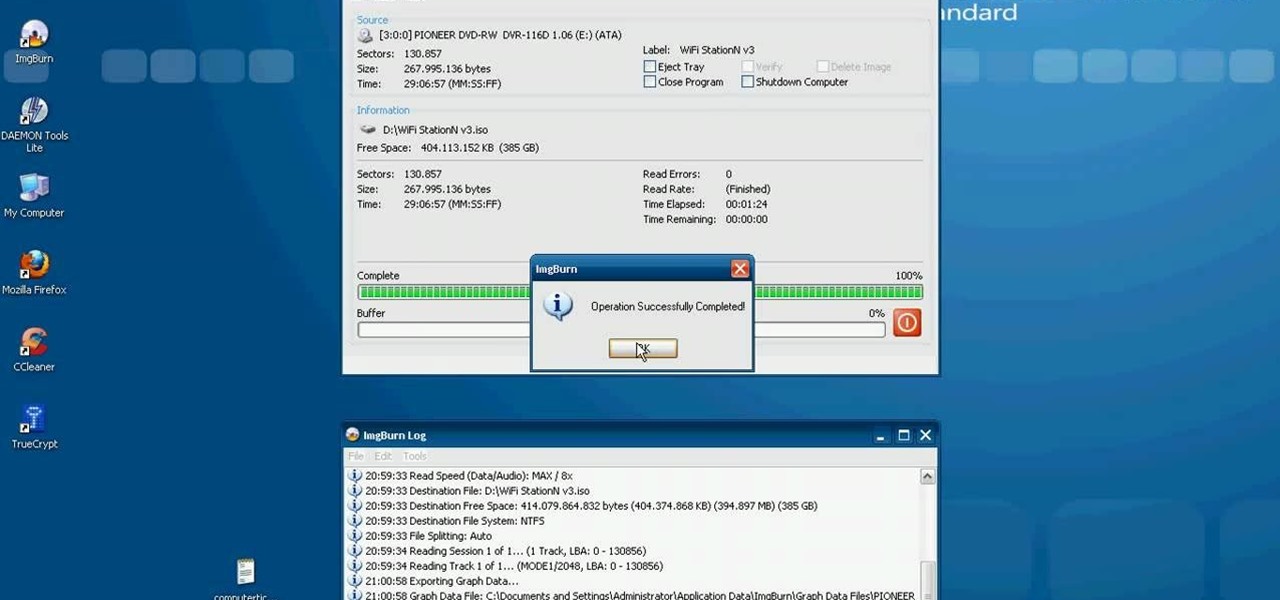
This video tutorial from computerticket shows how to use Daemon tools and Img Burn applications. First, install Daemon Tools and ImgBurn programs. Both can be easily found using internet search engine.

Access your computer's BIOS settings

How to install custom themes in your PSP gaming unit. First go to Google and search "Free PSP themes" and then click first link.

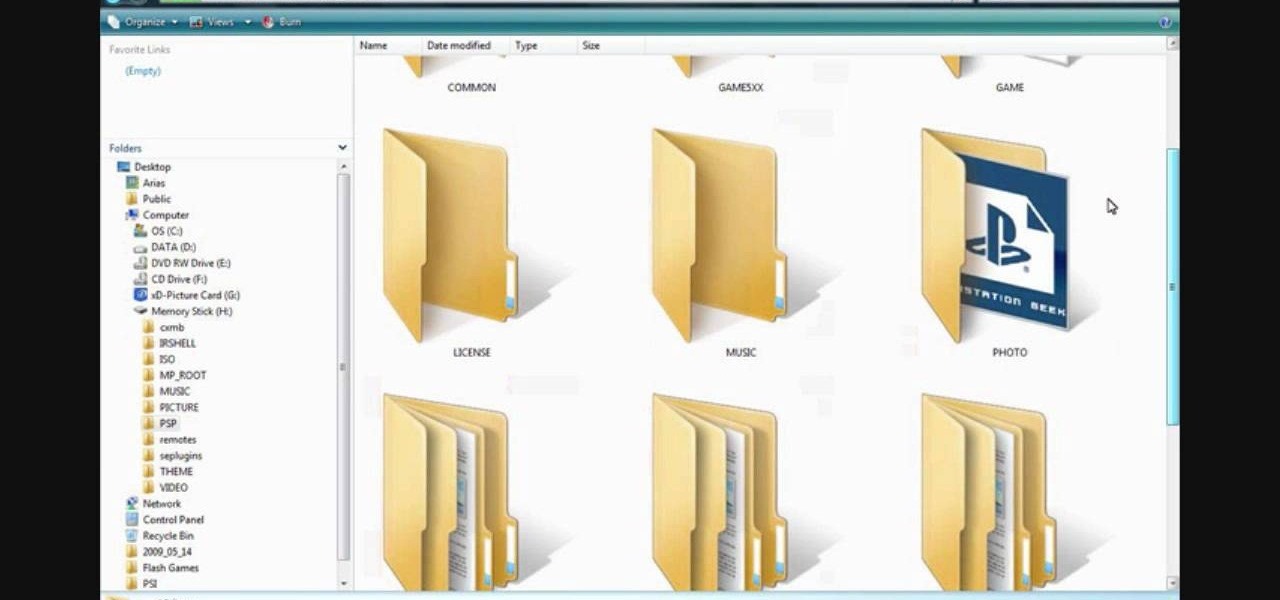
In this video the instructor shows how to install a program or a game which is in ISO format. The first thing you will need is the ISO file that contains the game or program. Next you will need a program that can open the ISO file. Use the daemon tools for this purpose. Right click on the daemon tools icon in the notification area. From the menu choose the mount image option and point to the virtual disk. Now browser and select the ISO file that you want to open. This mounts the image to the ...

In this video tutorial, viewers learn how to recover and restore deleted files using Recover. Recover is a freeware data recovery program. Recover recovers files deleted from your Windows computer, Recycle Bin, digital camera card, or MP3 player. Start by selecting the type of file. Continue by inputting the information. It will then take an hour to scan the drive for the deleted files. Once finished, it will display all the deleted files. The green files are recoverable and the red files are...

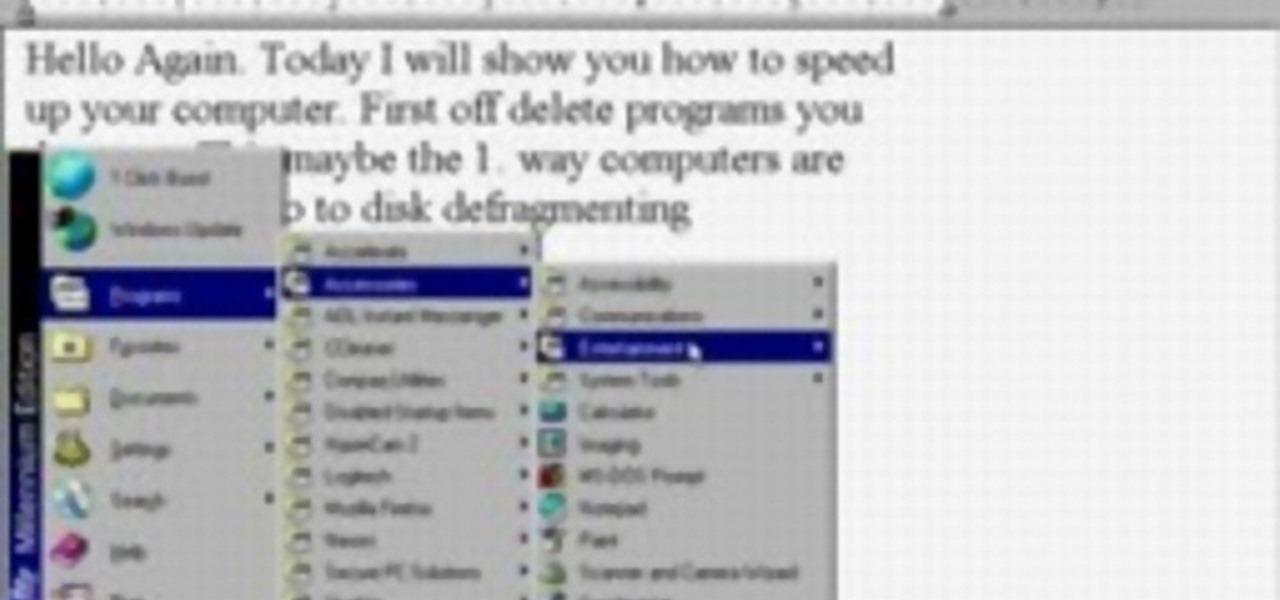
How to make your computer run faster is very easy to understand. The steps involved are as follows:

Do you want to change the login wallpaper on your Mac OS X? It is as simple as replacing an image in the file system.

Advanced defensive techniques are important in getting to balls that are hit into difficult positions. Whether the ball is hit low, to the side or high, the volleyball player must be prepared. Learn how to do advanced defensive techniques in this volleyball video tutorial.

Go ahead, but please, don't look for that car and especially don't drive it.Raspberry vodka, Malibu rum, Malibu pineapple rum, peach schnapps, strawberry liqueur, banana liqueur, raspberry liqueur, cranberry juice, orange juice, and pineapple juice make up the Where the Fuck Did I Park My Car? cocktail. Follow along with bartender Meghen as she gives step by step directions for how to mix up this fruity specialty drink. Watch this video beverage making tutorial and learn how to mix the Where ...

The HP 2710p business notebook has a number of innovative security tools to make sure your data stays where you want it.

It may not seem like a big deal, but sometimes when your filenames are being saved in the incorrect case, it is. If you save a file with uppercase letters in the name, your computer may change them to all lowercase. This occurs when downloading files form a host server to a local hard drive. But what if you want them back how you had them? Well, there's a small Windows tweak you can use to stop it from happening. Learn how!

In this series of computer hardware videos, our professional computer consultant and technology expert will demonstrate how to format a hard drive.

If you bought an iPhone or iPad equipped with USB-C but didn't max out the local storage, there are some great external storage solutions beyond iCloud and other cloud storage services. And now that the iPhone lineup comes with USB-C ports, you have better-performing external drives available to you than anything you could ever get for a Lightning-based model.

To play in the World Cup, soccer's ultimate tournament, you have to be among the best players on the planet. For the rest of us, Google has a hidden game to simulate the thrill of scoring goals for your favorite team.

Facebook Reality Labs just experienced its first major executive exit since the pandemic began. Hugo Barra has announced that he's stepping down from his position as vice president of VR at Facebook.

As the U.S. inches closer to herd immunity and reopening after the pandemic, it may become necessary to keep your COVID-19 vaccination cards on you at all times to gain access to places and events that are prone to spreading the coronavirus. You probably won't want to lose your card, so it may be wise to load a copy onto your smartphone for easy access.

The development of virtual reality at Facebook has been evolving lightspeed in the last few years. But while a relatively small group of VR enthusiasts and gamers are enjoying the social media giant's dedication to immersive headsets, it is the augmented reality space and its potential scale that truly has the tech market enthralled.

For the most part, new features for Google Maps, such as Live View augmented reality walking navigation, come to Android first.

If you've spotted an unintended Ethernet connection and wondered what you could do with all of the information coursing through those wires, there's an easy way to hack into it and find out.

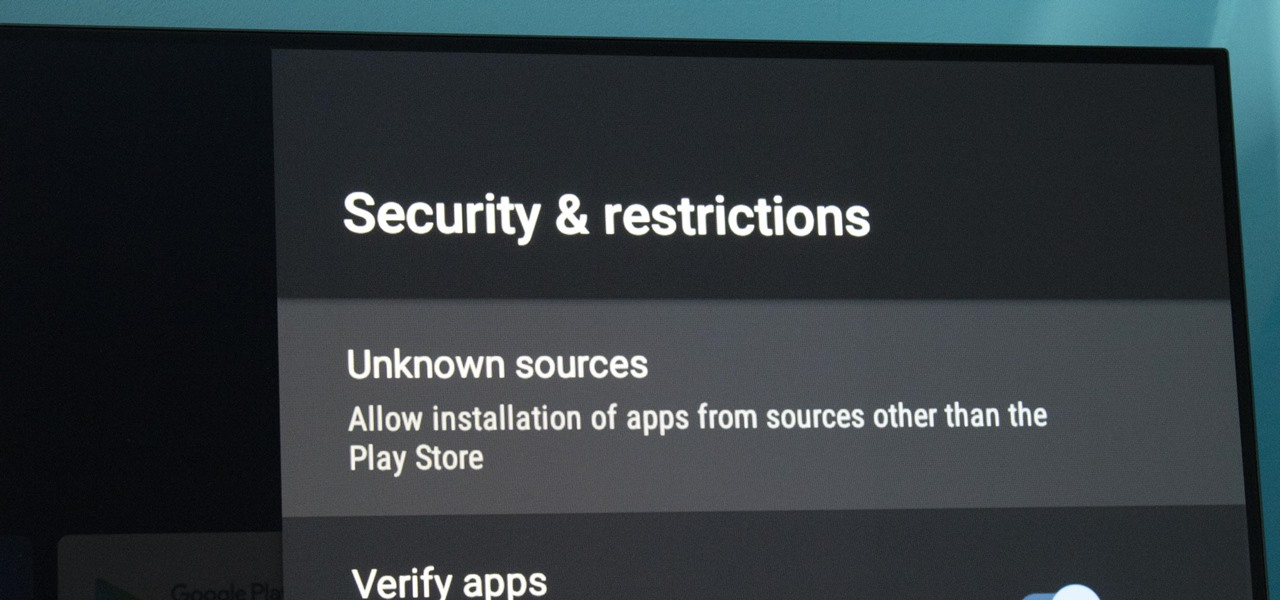
At its core, Android TV's software is the same as the OS running on 87% of all smartphones. But it doesn't always feel that way, with its version of the Play Store only having 5,000 apps (or 0.2% of all Android apps). To access the remaining 99.8% of apps, you will need to sideload them.

The year 2019 was filled with all the normal peaks and valleys of the tech business cycle, but this year was particularly important in a space as relatively young as the augmented reality industry.

It's finally out. After months of testing, iOS 13 is available to install on your iPhone, which means over 200+ new features you can use right now. The update, released on Sept. 19, can be installed over the air or from a restore image using iTunes in macOS Mojave and older or Finder in macOS Catalina. Ditto for the 13.1 update issued on Sept. 24.

We've already shown you our favorite new action games that have come out this year, but now it's time to share our all-time top ten list. These games are available for both Android and iPhone, they don't have intrusive ads or freemium schemes, and most importantly, they're all completely free to play.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Rooting usually means sacrifice. With most root methods, you lose access to apps like Netflix and Android Pay when SafetyNet gets tripped. More importantly, you lose the ability to accept OTA updates, forcing you to manually flash new Android versions. But there's a way around all of this if you root the right way.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

Windows 10 and macOS have poor reputations when it comes to customer privacy and user policies. Our hacking Windows 10 and hacking macOS articles might make it seem like a reasonably secure operating system doesn't exist. But I'm here to tell you that there is a viable alternative that could provide some sense of security and trust.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

With their first attempt at the mobile market, Razer introduced a device that looks at the smartphone differently. Instead of focusing on minimal bezels or an amazing camera, Razer decided to make a phone for gamers. So how could Razer target the growing mobile gaming market, which is projected to generate $40.6 billion in global revenue in 2017? It starts with the IGZO LCD Display.

In the previous section of this series on dynamic user interfaces for HoloLens, we learned about delegates and events. At the same time we used those delegates and events to not only attach our menu system to the users gaze, but also to enable and disable the menu based on certain conditions. Now let's take that knowledge and build on it to make our menu system a bit more comfortable.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.