SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).
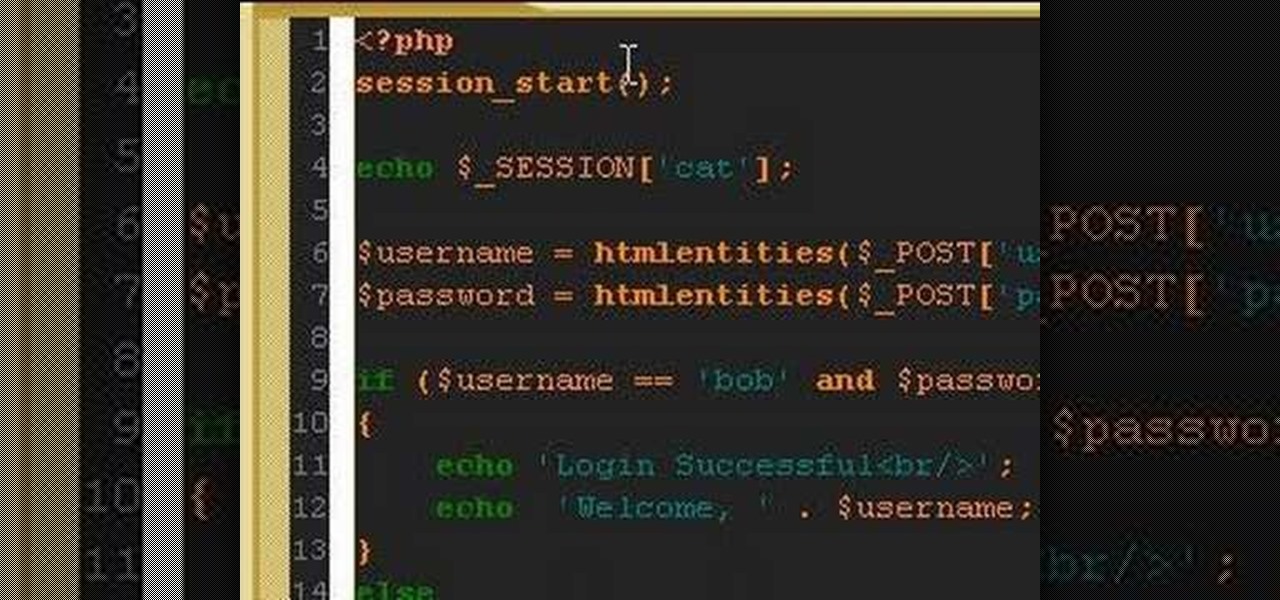
A PHP programming tutorial on creating login sessions to keep users logged in.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

Interested in making Firefox save your browser state more frequently to protect against crashes and outages? This clip will show you how it's done. It's easy! So easy, in fact, that this handy home-computing how-to from the folks at Tekzilla can present a complete overview of the process in about two minutes' time. For more information, including detailed, step-by-step instructions, take a look.

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...

In order to get add-ons and plug-ins for Google Chrome, you to go to Chrome Plugins. Type the address into your browser. Then, press Enter. Scroll down the list. Choose and add-on that you want: for example, Click & Clean. Click on the one that you would like to choose. Find "Download Latest Version" and click on it. Wait for it to download and click on it. There are lots of options. Click & Clean allows you to clean your browser with only one click. Session Save allows you to save the sessio...

In Blender, you can build up a library of Actions, Poses, and IK Target motion based on real-world motion capture sessions. These session files are freely available and cover hundreds of everyday motion. Use these libraries to study and augment your hand-animation skills, or use directly to animate your character. Whether you're new to the Blender Foundation's popular 3D modeling program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're s...

Take advantage of this unique opportunity to prepare for the Advanced Certification exam in an interactive day long, live session with an Advanced Certified Pro advisor! Get a jump start on becoming a QuickBooks Advanced Certified Pro Advisor. Learn how advanced certification can help you grow your business and continue to improve your skills. You will understand what advanced certification is, why it is important to your practice and how it can benefit you and your clients. Learn how to effi...

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

You always wanted to make an undetected payload and make it look legit, Well this is what this tutorial is about, You're going to learn how to backdoor any (Unfortunately only 32-Bit) software, Let's get into it
Hello everyone. The red ring of death of Xbox 360 has been a huge problem since the beginning of Xbox 360. Many gamers like me have faced this problem and the red ring of death (RROD) is one of the biggest reason behind all the rant on Xbox 360 gaming console.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...

In order to become a good runner you must do more than just, well, run. Good running requires good form, which means that in addition to doing your daily job you must commit to completing drills designed to improve your running form (to reduce injury).

If you're just getting started with Final Cut Pro, you probably didn't know that you can also make slideshows with it. Crazy right? And it's actually easier than you think! In this video you'll learn how to start a session in Final Cut Pro to begin your slide show and walks you through the process of adding photos and effects, all the way to exporting the final product.

Audacity is an amazing editing tool, and why is it amazing? Because it's FREE! Yea, that's right, free! One awesome thing you can do with it is edit your mp3 files into whatever you need, heck, make your own ringtones with it! In this video you'll learn how to open a session in Audacity to edit your MP3 files in wave form!

Paul Jackson Jr. is one of the tastiest session musicians alive and has played with hundreds of artists over the span of his career including most of the guitar work on Michael Jackson's Thriller album! In this video he explains the secret to his style and how to pick apart chords and play the very basic components of each chord to create a more sonically sound rhythm guitar part that doesn't step on anybodies toes but is catchy enough to be noticed in the mix.

Want to know how to save and restore important tabs in Chrome? This clip will show you how it's done. With the Session Buddy addon, it's easy! So easy, in fact, that this handy home-computing how-to from the folks at Tekzilla can present a complete overview of the process in about two minutes' time. For more information, including detailed, step-by-step instructions, take a look.

Cardio intervals, circuit training, plate exercises...when it comes to fitness, it seems like there's always a fancy name for what are essentially really easy yet effective strength building, fat burning, and toning exercises.

This is a rugby tackle tutorial from RugbyDevelopment.com Video to prepare your players for a scrum session. The scrum is how play starts in rugby.

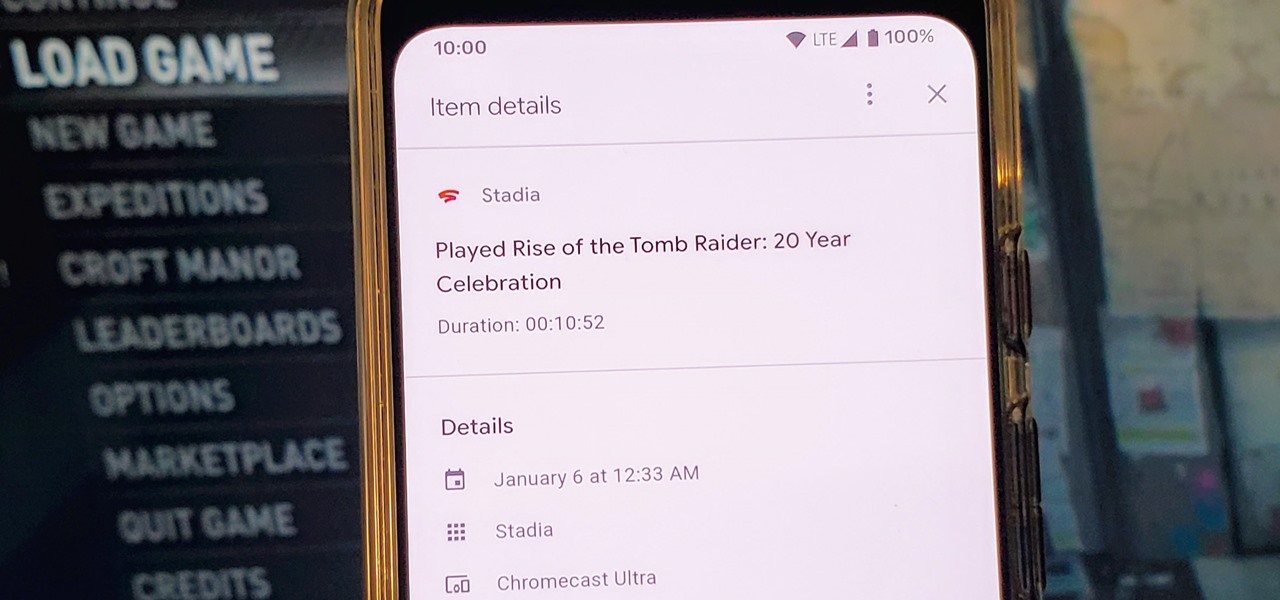
Since Stadia is an early access game streaming platform, Google is still working on bringing big things to the table. You can expect wireless Stadia controller support for many more devices, high-quality 4K gaming on all Chrome web browsers, and more Google Assistant features. They also managed to silently sneak in a way to keep track of your Stadia gaming sessions too, which is pretty handy.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

There's nothing wrong with indulging in guilty pleasures on Spotify every once in a while — we all need a little Coldplay and Creed in our lives. The only problem is, all of your friends and family might be watching. Anyone that is following your Spotify account can potentially see what you're listening to, but there are several ways to hide this shameful and embarrassing activity from the world.

On Wednesday, in addition to uploading another batch of videos from its L.E.A.P. conference to its YouTube channel, Magic Leap also launched a new video series for developers called Spacebar.

Magic Leap's recent L.E.A.P. conference was free to all who registered in time, but if you weren't able to make the trip to Hollywood, the company just released video of some of the sessions that took place over the course of two days.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.

This video shows us how to burn files to a disc using Windows Vista. Insert the blank disc in your computer's recordable disk drive. Autoplay will automatically appear. Choose "Burn Files to disc using Windows". Click next when "Burn a disc" dialog box appears. Empty folder window appears. Choose files that you want to copy and drag them to the window. For example, if you want to copy a photo, click Start menu and open the Pictures folder. Select photos and drag them to the window. Photos are...

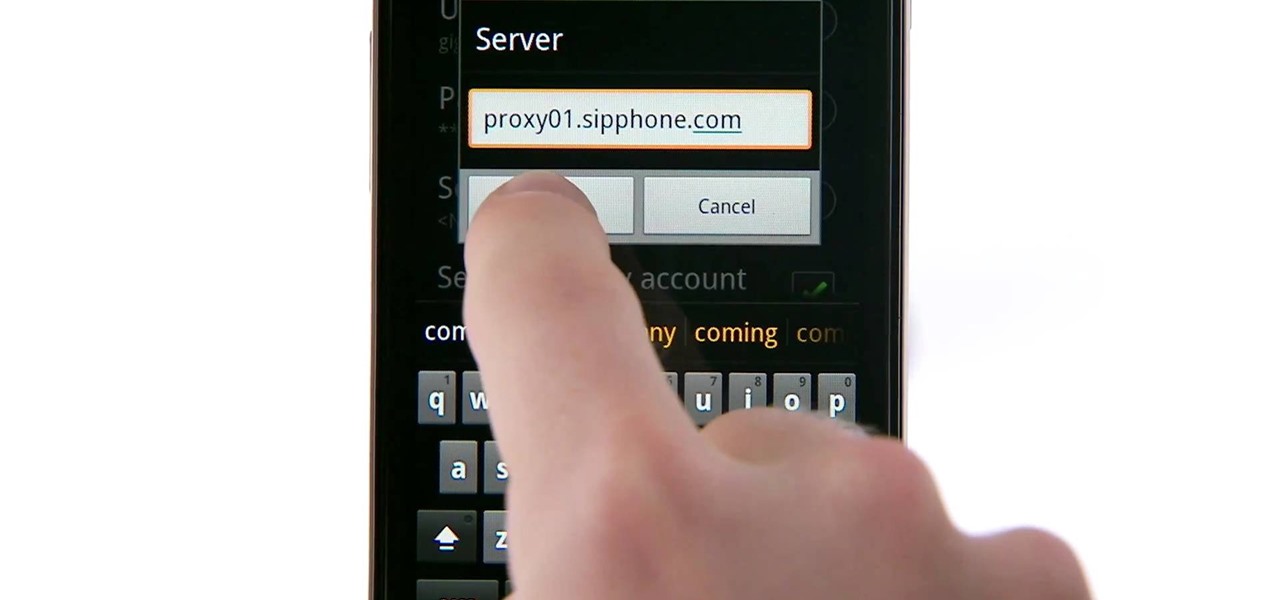
If you've got Android 2.3 Gingerbread running on your Google Nexus S smartphone, try out this cool feature. Set up a SIP (Session Initiation Protocol) account, and you'll be able to make Internet calls over Wi-Fi. You'll be able to talk to anyone with VoIP.

Kateikyoushi Hitman Reborn is a popular Japanese anime series that has yet to hit US televisions but is already insanely popular from being available on Crunchyroll. IN this video you'll learn how to play one of the series many beautiful songs "Tsuna Kakusei" on piano. It should get your psyched up for your next session of mob boss training.

Get those annoying wisps of hair out of your face in time for your afternoon pilates session while still looking put together by braiding your bangs into a hair headband.

Jared of the TechCentric crew gives you the lowdown on the basics of keeping your VoIP conversations secure and, on the other side of things, how to use the Cain VoIP sniffing application. For detailed instructions on keeping your VoIP conversations private, watch this hacking how-to.

This video demonstrates a Reiki session, the passing of Reiki energy into a patient. The video walks you through transmitting your Reiki energy into a person at important parts of the body.

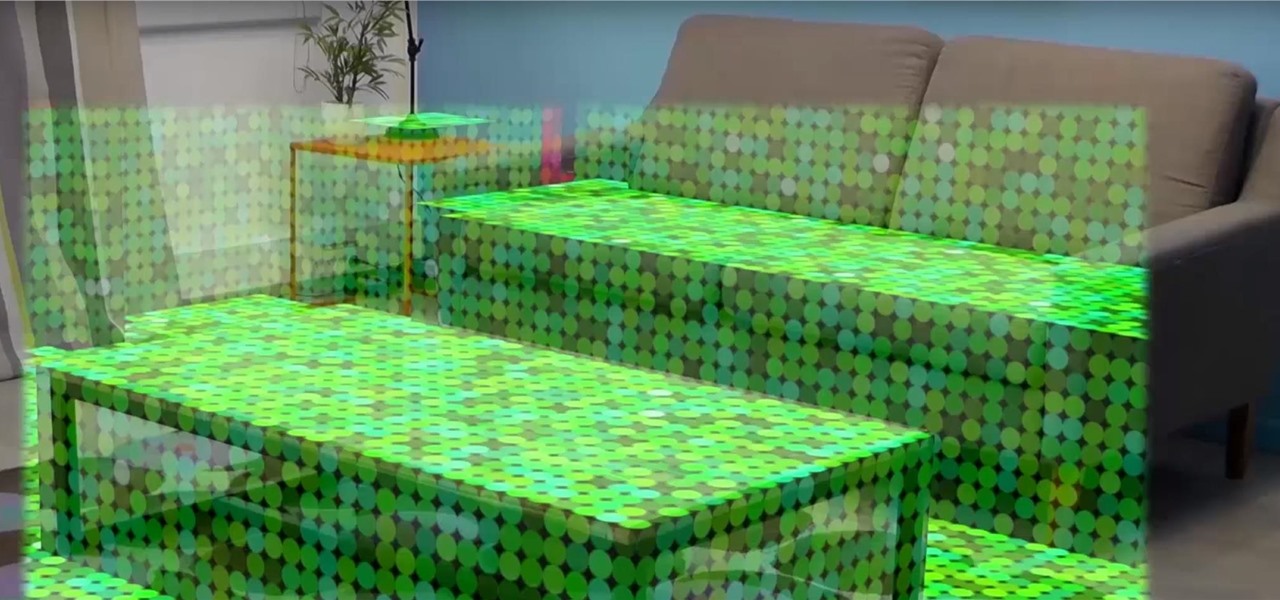
Once you've designed some holograms with HoloLens, you'll need to get them to interact with the environment. That's where Spatial Mapping comes in. There are five basic purposes for using HoloLens's Spatial Mapping with your app:

Gardening school is in session and Shirley is teaching the absolute basics, such as: what to wear, what tools to use, what is the difference between an annual, perennial, and biennial? What is a garden zone, and which one is yours? Class is in session, so spit out your gum and listen up. Time to learn Gardening 101.

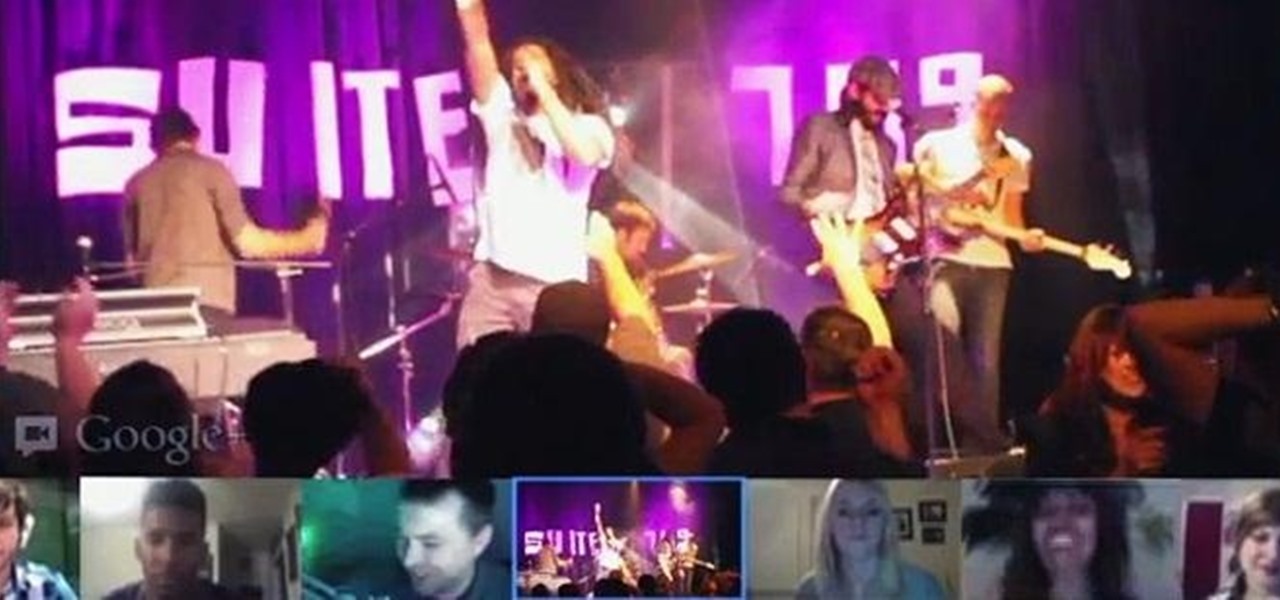
If you're a musician, Google wants you on Google+ Hangouts. In an effort to make it easier to stream your concerts, performances, and impromptu jam sessions, they've revealed their latest feature: Studio Mode. Enabling the new Studio Mode optimizes your Hangouts On Air for music, and the quality difference is massive.