
How To: Use a hammer or nail gun correctly
Tim Carter demonstrates how to install a finish nail using a hammer and nail set. Tim also shows how to do it the fast way with a powered nail gun!


Tim Carter demonstrates how to install a finish nail using a hammer and nail set. Tim also shows how to do it the fast way with a powered nail gun!

As you test out the new Quick Settings media controls in Android 11 and form an opinion, you'll notice one of the changes they made to the player besides the new location. For example, when you swipe away the mini version of these controls, the music keeps playing and the player still appears in the expanded view.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.
Now that the dust has finally settled on Microsoft's big HoloLens 2 announcement, the company is circling back to offer more granular detail on some aspects of the device we still don't know about.

While the technology companies continue to drive forward with autonomous vehicles, Nissan's vision of the future of self-driving automobiles lies in a cooperative experience between human and machine, facilitated by augmented reality.

Whichever web browser you use, each comes with a way to surf the net "secretly." While nothing on the internet is truly anonymous, private browsing modes can help keep your movements hidden from those who might have access to your data. The "secret mode" for the Samsung Internet app goes a step further on Android, by locking your private browsing behind a unique password.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.
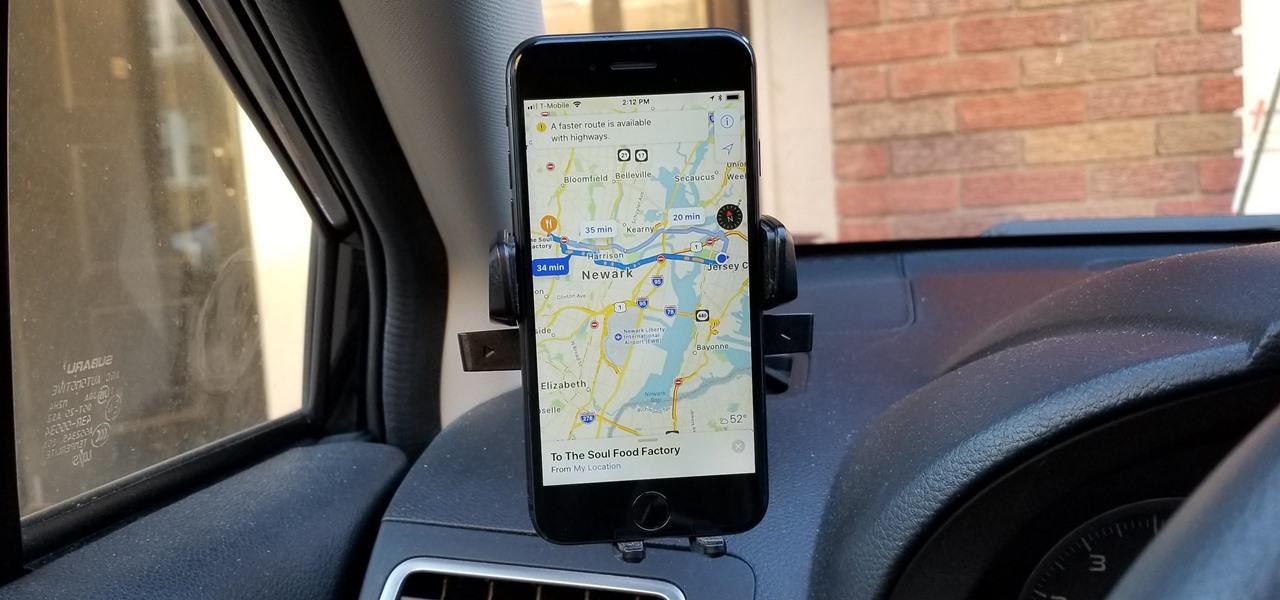
Highways are among the most efficient routes of driving from one place to another. Unfortunately, however, they're also the most used route taken by everyone else resulting in migraine-inducing congestion, especially during rush hour. Thankfully, Apple Maps has a feature that will direct you along lesser known routes that could be faster and/or safer.

Apple has finally given us a decent file manager in iOS 11. The new "Files" app replaces the not-very-old iCloud Drive app that appeared in iOS 9, but you can still access your iCloud Drive files in the new Files app, as well as files from third-party cloud services. A nice improvement, right?

The Audi A8 may be short on the wow factor as the industry's first Level 3 car, but Audi has revealed some interesting details about one stand-out feature underneath the hood: the car's ability to self-pilot itself at stop signs and lights.

The fatal crash of Air France Flight 447 is one of the most tragic accidents in avionic history — while it also serves as a stark reminder of what can go wrong when humans rely too much on driverless vehicles.

Drive.ai (a startup founded by Stanford University graduates), Waymo, General Motors, and serial entrepreneur and author Vivek Wadhwa are featured in today's top news.

Tesla has confirmed the EV carmaker has begun to upload videos from models equipped with its latest flavor of Autopilot, as Tesla seeks to "fleet source" data to help improve its cars' machine learning capabilities.

Nissan began to offer Level 2 driving capacities in a mainstream model when it debuted its ProPilot self-drive option for its Serena minivan in Japan last year.

The next-generation Audi A8 to launch in July is expected to be the world's first Level 3-capable production car to go on sale in retail channels.

Intel launched their Advanced Vehicle Lab in Silicon Valley this week, and the tech giant is now on the hunt for potential partners.

In the driverless race, technological advances can sometimes just add more tension to an already heated competition, if Waymo suing Uber over their allegedly stolen LiDAR technology is any indication. Now, Sony is offering a new camera sensor, one that should help self-driving cars "see" the road with much more accuracy than any other camera sensors available for vehicles currently.
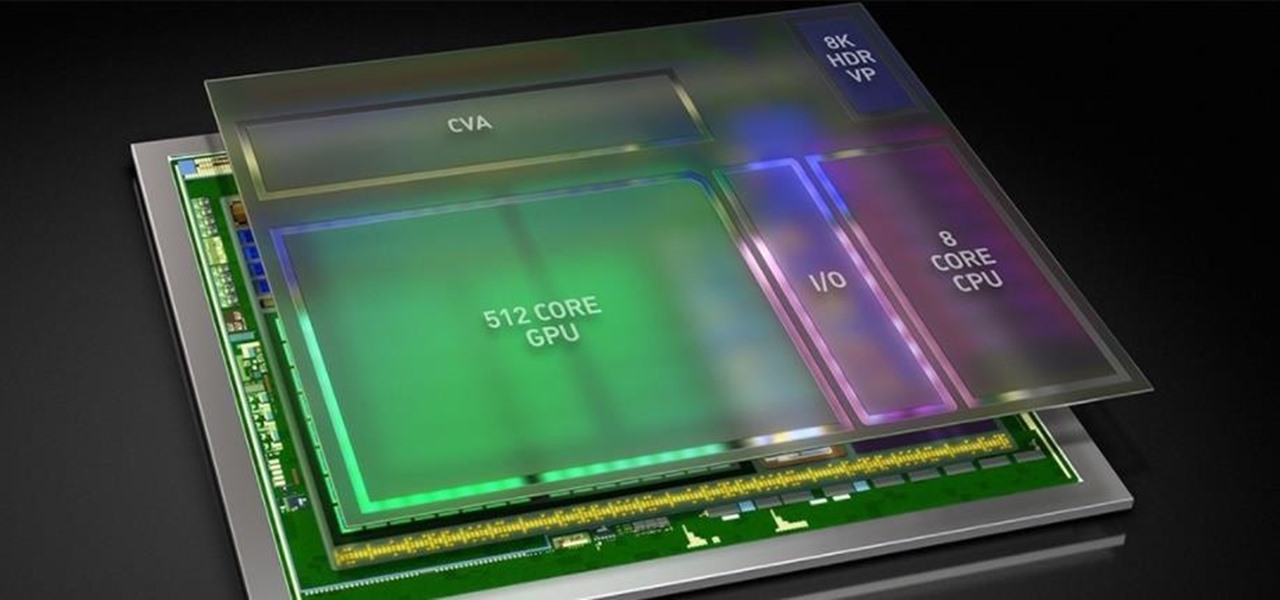
As Intel steps up their investment in driverless technology with a $15 billion acquisition of Mobileye, so have automotive supplier Bosch and NVIDIA teamed up to manufacturer driverless car systems with the much-awaited Xavier chip.

Google's former Self-Driving Car project, now graduated from Alphabet's X division as Waymo, has found a collaborator and potential new partner in Honda. This is an interesting turn of events given traditional automakers' reluctance to work with driverless-car startups over the years.

Last week it was announced that Waymo, the former Google Self-Driving Car project, had graduated from Alphabet's X innovation center. This graduation had been in the cards for many months with senior members of the project team and X hinting that it would be soon.

While it hasn't gotten as much attention as iOS 10, Apple's big 10.12 update to their Mac operating system is finally out for all to enjoy—and you can download it for free from the Mac App Store right now.

Welcome back! Sorry for the dry spell, but I've been rather busy setting up some side projects! If you remember back to a few training sessions ago, we covered basic file I/O. This is a very important step in making our scripts applicable in a real life scenario, and today we're going to further these concepts.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Google is rolling out an update for Google Drive that streamlines the online file storage/sharing app, and finally gives you access to the Trash folder that had only been available on the desktop version.
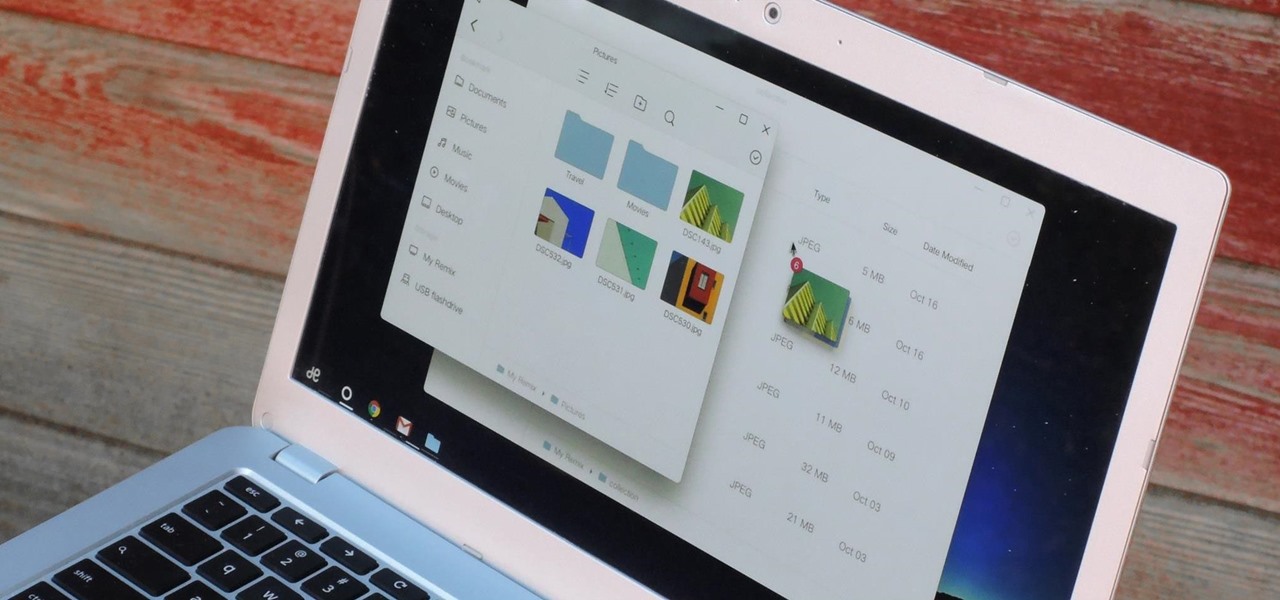
If you read the reviews on Google's Pixel C, you'll notice one big complaint about the tablet/laptop—most reviewers feel that Android simply isn't ready to be used as a desktop OS. The developers at Jide felt the same way, so they set out to make a custom version of Android with proper multitasking support and a UI optimized for the mouse and keyboard.

Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other and the constant search for knowledge that inhabits this subdomain is a driving motivator for me to join in. I'm glad I arrived at the right time. Anyway, wipes tears (not really)...

Hello, everyone! Many of you don't even know about my existence here on Null Byte, so I thought of contributing something rather interesting. Recently, someone asked how to make your own "Bad USB," and I promised to make a how-to on this topic. In addition, it would be nice to have something related on our WonderHowTo world. So here it is!

Technology has progressed by leaps and bounds and has blessed people in a number of ways, but at the same time, it has troubled them also. Computers are now used in every aspect of life. No matter if you are a businessman, an employee, a student, or even a housewife, a computer can assist you in your routine work. You save your personal information, documents, and other similar sensitive stuff on your computer that can hurt you if they get compromised.

When it's most important for me to browse the web incognito, I always seem to forget to enable private browsing. If that sounds like you, it's time you stop making that mistake for good. Manually deleting the cache and browser history is a thing of the past, and as it turns out, so is manually switching to incognito mode.

Yesterday, I wanted to remove BackTrack from my system and install Kali, and at the same time didn't want to damage my Windows 7 or my hard drive. I searched a lot of articles, but almost all of them wanted me to have a backup Windows 7 CD, which I don't possess.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.
Welcome back My sleepless army of young hackers, Everyone uses internet, right? So for this tutorial, i'll start with the basics and slowly we'll get to the UPD Protocol.

Last month, Alexander Heit drifted into oncoming traffic after being distracted from the road. His sudden correction forced his vehicle to roll and flip over. He was pronounced dead at a local hospital shortly thereafter. All because of a freaking text message. He was only 22 years old.

With the release of Windows 8 right around the corner, if you plan on buying it (or just want to see what it's all about), it's a good idea to take advantage of the free trial before you shell out any money. If you're an Apple user who doesn't have a deep-seated disdain for Microsoft products, this tutorial will show you how to install the Windows 8 preview to try it out on your MacBook. First things first, you'll want to download the Release Preview on Microsoft's website (make sure to save ...

If you've got more than one computer, it can be a huge pain to switch form one to the other. Between files, settings and apps, it can take a while to transfer everything—and if you're running different operating systems, it's even worse. Image by Onion
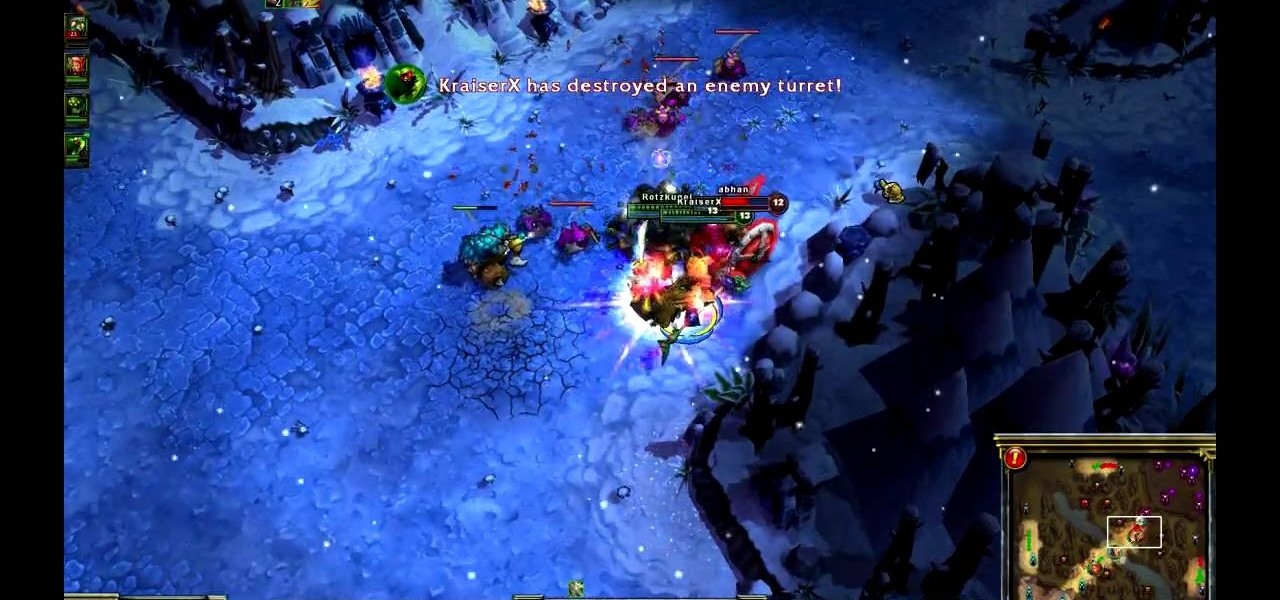
Ezreal is a champion you can bring onto the Fields of Justice. This video demonstrates what Ezreal, a strong ranged fighter, can do and the best ways to use him in combat. Here are a few good strategy tips when it comes to scaling his abilities, and a few ideas on how to fight certain opponents.
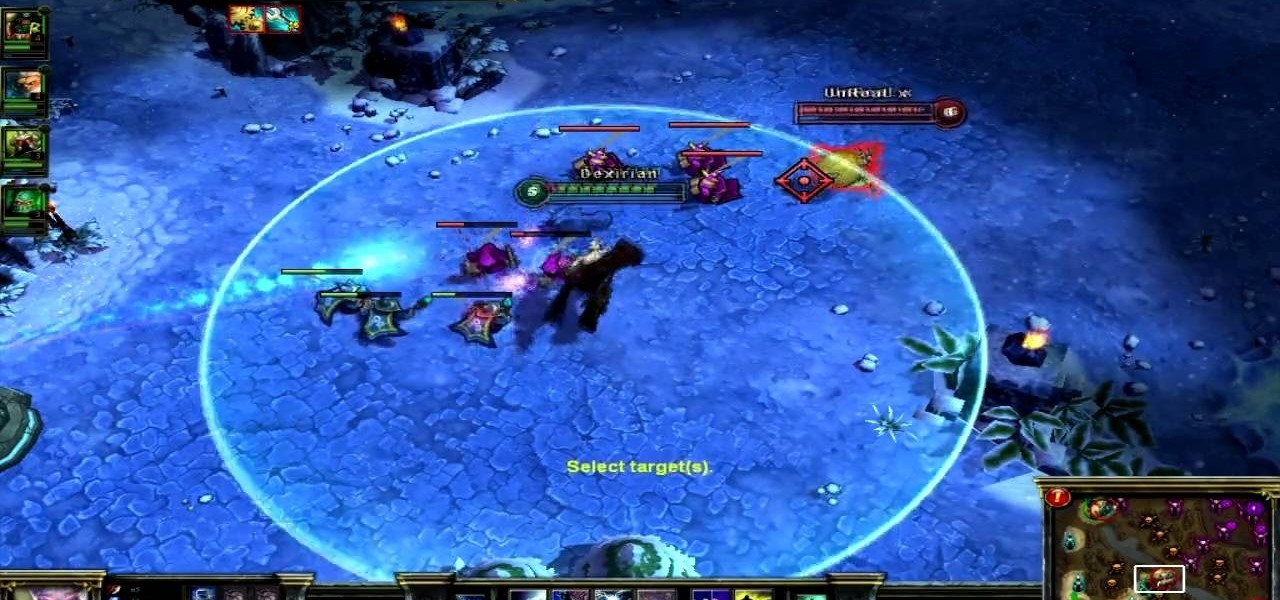
Start with Ryze as your champion at Level 1 and play him straight up through until Level 12. This tutorial shows you how to start his build and what spells, items and abilities to invest your points into so you can maximize his damage potential.

Malzahar can certainly be a viable champion to play on the Fields of Justice. This video shows you how to build up Malzahar by using the correct abilities, items and summoner spells to increase his strength in battle.

Vladimir the Crimson Reaper is the closest thing to a vampire you can bring onto the Fields of Justice. His abilities are focused on taking health from his enemies to build himself up, and this tutorial shows you the best build with spells, runes, abilities and items to take advantage of his unique talents.