Here is the answer to the question that a lot of people have asked lately, "How does one install Linux Ubuntu on Windows without causing any modifications in the original boot record of the PC?" Software wiz-kid Matt Hartley walks the viewer through a step-by-step process of installing Ubuntu on a Windows-driven computer. The secret is to download Ubuntu to a CD instead of downloading and installing it directly on the hard drive of one's PC. This also ensures that the Ubuntu is easy to delete...
In this video, viewers learn how to install Wiiflow. Viewers will need to install cIOS 249 and 222 / 223. Wiiflow is USB Loader that you can use on a Wii that have modified or hacked. Wiiflow enables you to play your "legal ISO backup" by using any USB storage device like a thumb drive or a more substantial external hard drive. This video demonstrates how to do this in a way that is easy to follow.

Looking to expand the storage capacity for your PS3? Look no further. This video will show you how to upgrade your Playstation 3 harddrive. So, if your Playstation 3 is starting to run out of space, it is time for an upgrade. Follow along with this step by step tutorial and learn how to install more room on your gaming system.

Slow down? What!?! You've got to love the simplicity when it comes to long drive tips from long drive competitors. The long hitting Jamie Sadlowski shares his simple tip for more power, and it's not what you might think. See how to slow your golf swing down for more power.

Geoff walks us through getting the "Chain Reaction" Achievement in GTAIV.

Here's a new handle system for the RED ONE Camera. Allows multiple mounting points as well as an isolation plate for RED DRIVES. It's extremely robust, versatile, and inexpensive.

John Jacobs' Golf Schools present Quick Tips: Putting. Director of Instruction Tom Perkins helps you limit your strokes on the green.

How to fool your friends in some time ! You can delete or move away the icons ! Using Paint or any other screenshot or photo editing program swap out the desktop with one covered in images of the icons, rather than actual and clickable program icons. Delete all the icons on the desktop and this is sure to drive yoru friends crazy. Perfect office prank.

This Weekend Project is the USBattery from MAKE Magazine Volume 16. Conceal a flash drive in a AA battery! This is a way cool USB battery mod or hack project. It makes a cool secret storage space for your spy projects. Wear gloves, safety goggles and a non alkaline battery.

Is a constantly running toilet driving you mad? Don’t call the plumber until you try these simple adjustments. Don't waste your money just yet- watch this instructional video on how to fix a running toilet. You will need a faulty toilet and some food coloring.

You may have lost your files but you needn't loose hope, too. In this episode of Lab Rats TV, Andy and Sean show you how to recover your deleted data (and your marriage!) using oranges. For detailed instructions on recovering your own lost data, take a look at this tech how-to.

Want to mix and scratch like a professional DJ? To be a good DJ you need to understand the concepts of mixing tracks, adding cool effects, and of course you need a good sense of rhythm to line up the beats. This how to video explains how you can set up the American Audio TT-Record Turntable. This is a Belt Drive turntable that can record your vinyl with a press of a button. All you need to do is plug in your memory stick and off you go. This unit does not need to be used as a direct drive sin...

This video tutorial shows you how to scan an image in the Runtime GetDataBack software for NTFS. The image was made in the tutorial for RAID Reconstructor when recreating a RAID 0. Why do you need to scan an image? For data recovery that you recreated with RAID Reconstructor. An image is the exact same thing as a hard drive, except that it's in a file format. So, backup your computer's drive, with this video to help, using GetDataBack.

Just because you don't drive a BMW that comes with these cool headlights stock, doesn't mean you can't have them. This video shows you how to wire angel eye (halo) headlights in a 99-04 Mustang.

In this ShowMeDo, Jeff Winkler demonstrates using pyWinAuto (v0.3.4) to control Windows Notepad. pyWinAuto is a series of Python modules that uses a very intuitive dot syntax to drive any Windows application.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

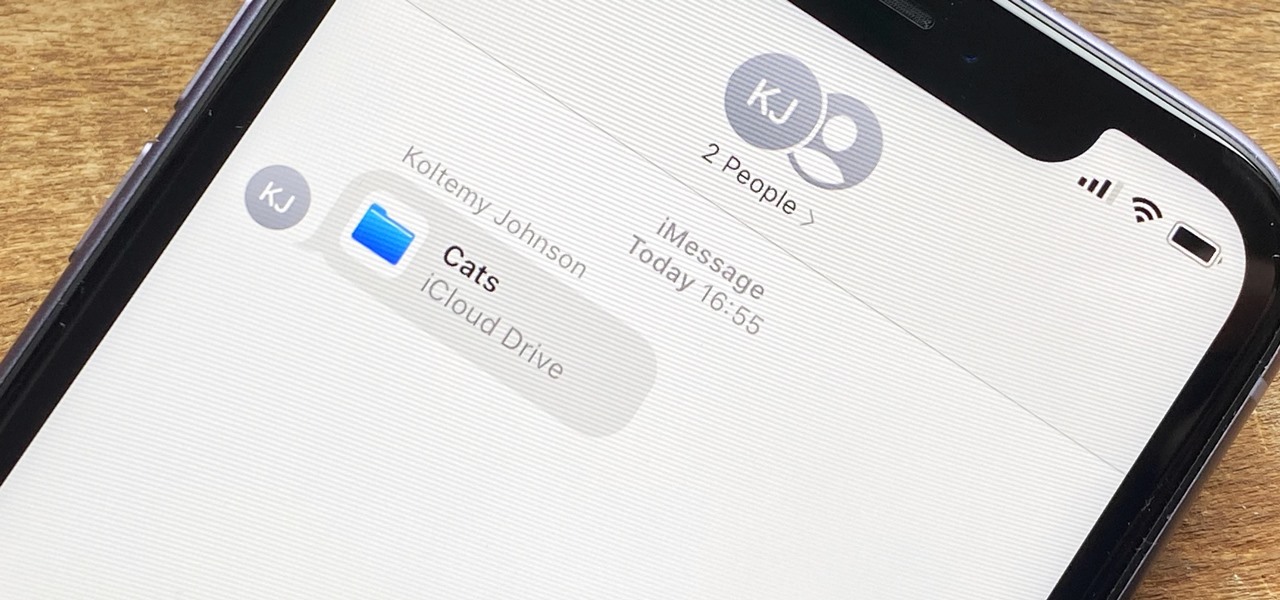
In the iOS 13.4 update, Apple added folder-sharing capabilities in the Files app. That means you can share multiple documents at the same time instead of doing it one by one. But that's not all — you can share folders with numerous contacts and even enforce access and permission settings.

Facebook has announced the cancelation of its annual F8 developer conference, citing concerns around the developing coronavirus health crisis.

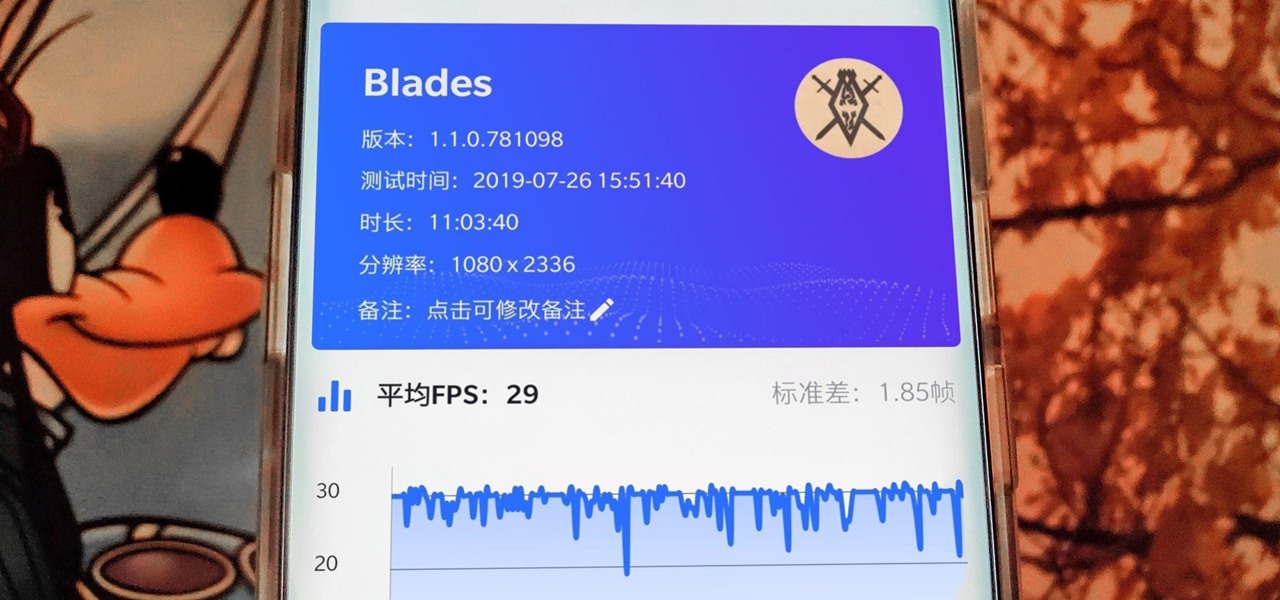
When you're gaming on your Android phone, does it sometimes feel "slow" and you can't figure out why? That means a drop in performance, which is when the frame rate dips, causing some noticeable stutters and lag. There's not really a way to know what's wrong unless you made the game yourself. But on the bright side, you can check any game's FPS with a simple tool.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

Yesterday, I talked about what I think is the most immediately mainstream-friendly app on the Magic Leap One is (Screens), and now we'll touch upon the runner-up: Helio.

The long and slow road toward the actual release of the Magic Leap One appears to be accelerating, with a couple of new demonstrations of how the system works revealed in this week's creator's portal updates along with the company's developer documentation.

During its presentation at Unite Berlin, Magic Leap gave attendees a crash course in developing experiences for Magic Leap One (ML1), we found out quite a bit more about how the device works and what we can expect to experience with the device.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

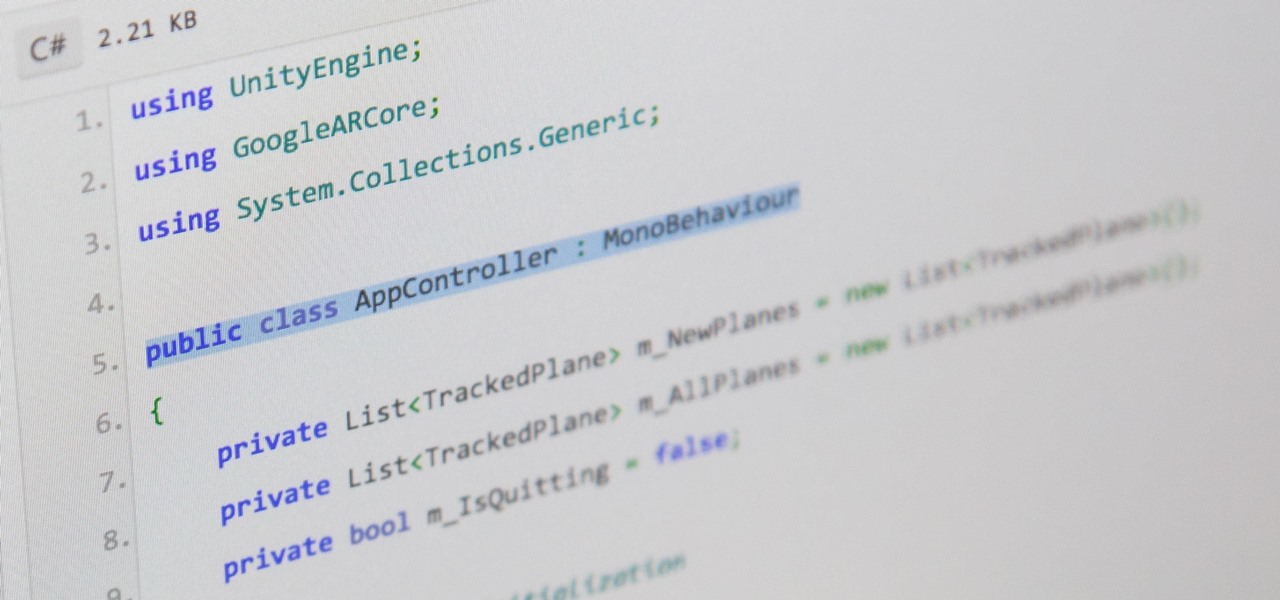
There are hundreds, if not thousands, of programming languages and variations of those languages that exist. Currently, in the augmented reality space, it seems the Microsoft-created C# has won out as the overall top language of choice. While there are other options like JavaScript and C++, to name a few, C# seems to be the most worthwhile place to invest one's time and effort.

All eyes will be on Tesla CEO and founder Elon Musk tonight to see if he is reveals details about the status of Tesla's challenged Autopilot at tonight's official Model 3 launch party.

Tesla's Autopilot self-drive interface in its new Model 3 signals the carmaker is already prepping its cars for Level 4 driving years ahead of the competition.

Volvo Cars' "all-electric" announcement last week was seen as a direct threat to Tesla's electric vehicle (EV) and driverless lead, but German auto giant Volkswagen (VW) says it is in a better position to challenge Tesla.

Most carmakers now agree with Waymo that piloting driverless cars is best left to the machine — with no meddling from the human.

The sun-drenched people of Phoenix can now sign up to ride in an automated car, for free, courtesy of Waymo. The Alphabet affiliate announced its "early ride program," which will (hopefully) demonstrate how self-driving cars will fit into people's everyday lives. Highlighting a challenge Nissan CEO Carlos Ghosn has spoken about that faces the driverless industry.

The technology driving the automated vehicle revolution relies on the car's ability to see and understand the world around it.

A couple weeks ago, GM's Cruise Automation released a remarkable self-driving video from the streets of San Fransisco that Driverless analyzed in detail. And now they've just released a new one giving more insight into their growing mastery of the complex roads in San Francisco, specifically, the Potrero Hill and Mission Dolores neighborhoods.

So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

When the Chromecast first came out about a year ago, developers were quick to find a way to root the streaming device. Google was almost as fast, however, in updating the Chromecast's firmware to close the loophole that this method used.

Mobile carriers have been the bane of my existence for as long as I've had a phone. First, they take away unlimited data, and then when you try and switch carriers, they hold your phone hostage for a up to a week before unlocking it from their network.