Play Along: At the start of the mission, you simply need to follow the leader through the city. Do your best not to bump into anyone, as Ezio will drop the chest if you do. Eventually, you read the end of the trail and a cut scene takes over.

Cheaters Never Prosper: But they do get quite a reputation. This is a simple mission. You need to just fight off the opponents that come at you using your bare hands. Even though you've no weapon equipped, you can still use the typical counter ability. Though you won't always KO an opponent with the first counter, repeatedly make use of the technique and you'll eventually drop the opponent.
Ace Up My Sleeve: It's not a playing card though. Talk to Paola again and she'll give you the hookup with a cool weapon. Problem is, it doesn't work yet. You need to bring it to Leonardo da Vinci, who's just across town. Make your way to him and knock on his door for a lengthy cut scene.

Boys Will Be Boys: This is the very first problem for you to solve in the video game. You're dropped into your first mission, which requires you beat up a lot of dudes. Be sure to lock onto an enemy, which allows you to throw up your guard and block incoming attacks. You've got access to a counter move that's incredibly useful if you can get the timing down. Just hold up your guard and press the attack button as an enemy swings on you to put him down instantly. For more info, watch the whole ...

Pull off this easy prank, and – without causing any permanent damage – watch your coworker squirm with frustration.
New to Windows? No problem... here's a beginner's video tutorial that will teach you how to prevent cut, paste, copy, and delete on Windows files.

Homemade chicken and dumplings will bring warmth and comfort to your family. You Will Need

Learn how to reduce your risk of allergies. Transform your home into a sanctuary for your eyes, nose, and throat by reducing the risk of allergies.

Learn how to style a fro-hawk with Petrilude. Petrilude (aka Josh) is a guy that does makeup. You may think taking makeup tips from a guy is strange, but Petrilude is a talented makeup artist. If you are looking for party makeup looks, great for going out to the club, check out Petrilude's makeup tutorials. Search Petrilude on WonderHowTo for more amazing beauty looks: party makeup, club makeup, drag queen makeup, halloween makeup, goth makeup, costume makeup, and more.

Check out this bar trick of super sonic hearing. It is the trick that fooled Einstein by Brian Brushwood and Revision3's Scam School. Watch Brian scam Olympic gold medalist Jonny Moseley with a few coins, and some algebra!

Don’t squeeze that blackhead! There’s a gentler way to get rid of it, and several steps you can take to prevent new ones from forming.

Strengthen the calves with calf raises. Learn about dumbbell exercises for stronger, more flexible calf muscles in this fitness video. Take action: use one foot or add dumbbell to increase difficulty, keep body straight and tall, and drop heel as low as possible. Michelle is a personal trainer at a gym in NC and has been a personal trainer for several years. She is certified through ACE and is a certified aerobics instructor as well. Her Specialty is weight lifting and she enjoys training asp...

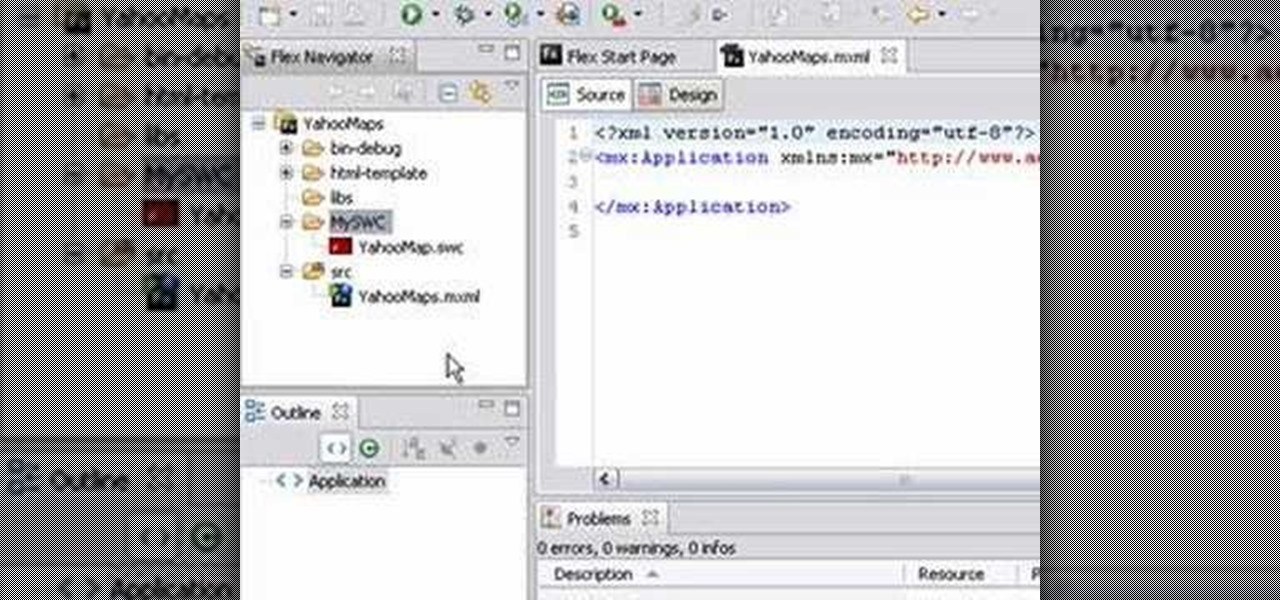
This video tutorial series shows you how to use the Yahoo Maps AS3 API in Adobe Flex 3. This new API gives you the ability to place Yahoo maps directly into Adobe Flex 3. Mike Lively Director of Instructional Design at Northern Kentucky University will be taking you through this tutorial.

Learn how to do single palm-up inverted pull ups on a Smith machine. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do step back lunges with a plate twist. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do stability ball push ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do landmines with a barbell. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do alternate front lunge holds with quick alternate dumbbell rows. Presented by Real Jock Gay Fitness Health & Life.

As we move toward the end of the year, the wheels of the augmented reality space continue to shift in major ways.

The big day for Snap that resulted in the debut of brand new augmented reality Spectacles smartglasses is turning into a big week.

Apple has a sterling reputation when it comes to managing its supply chain; it's where CEO Tim Cook proved his mettle to succeed Steve Jobs. Now, the company has made a strategic investment with a supplier that will be crucial to its future plans for AR wearables.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the outstanding feat of "magic" presented, we nevertheless hold fast to our survival-based grip on the truth: we just saw simply "can't be real."

XDA recently reported on a leaked version of the upcoming Pixel 4's camera app. By testing the app, they were able to find upcoming Pixel 4 features like a new Night Sight mode that can photograph stars. Well that leaked version has leaked itself, so now you can install it on your own Pixel phone.

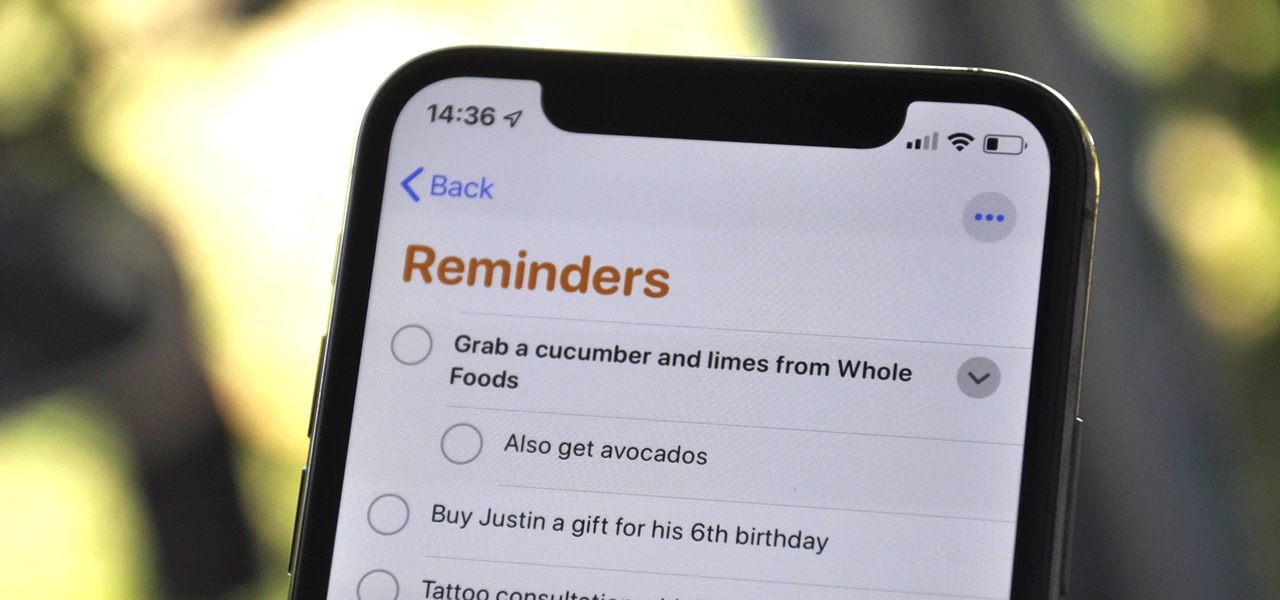
Things are a bit more organized in Apple Reminders, so the cluttered mess that it once was is no more in iOS 13. The slapped-together feel in older iOS versions was the main reason I never used it that much, but the updated version for iPhone has finally got me hooked.

Apple Card has generated quite the buzz since its March 2019 announcement. The iPhone maker's new credit card pairs with Apple Wallet on your device, is simple to sign up for, includes enhanced security over other cards, has zero fees, and provides daily rewards right to your Apple Cash account. And as good as that sounds, the fine print can complicate things real quick.

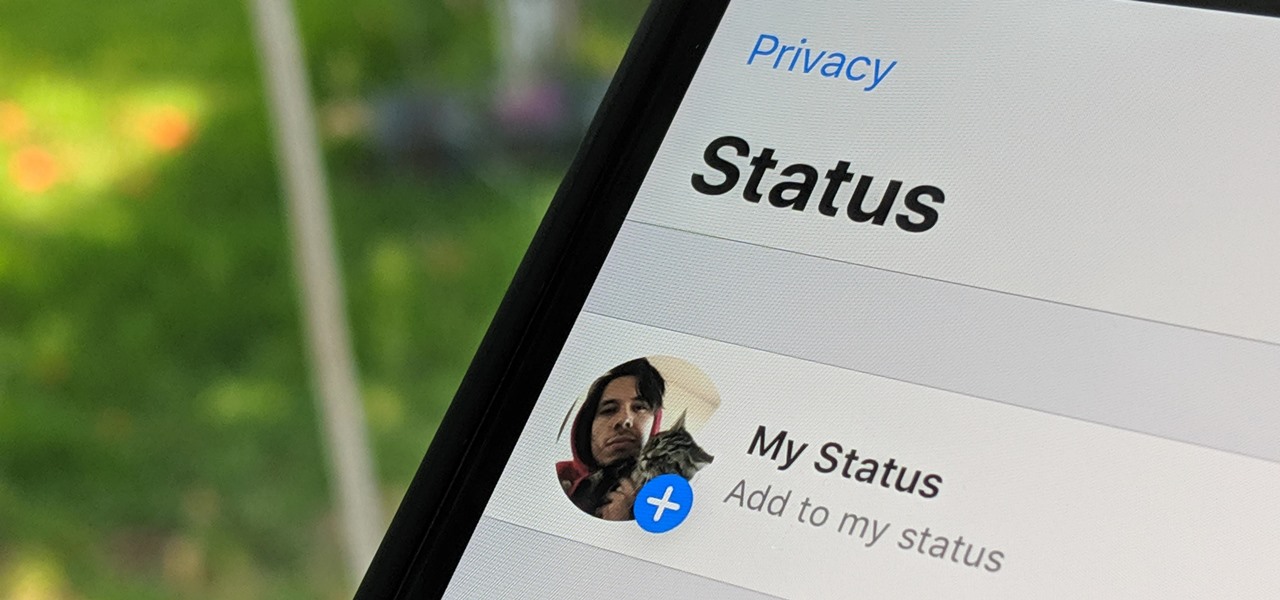
WhatsApp, the popular messaging app owned by Facebook, has several important privacy and security-related features, including end-to-end encryption, screen lock, read receipts, and two-step verification. If you're an avid WhatsApp user, you'll be happy to know there are more privacy features you might not know, such as hiding your profile photo from other users.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

In 2018, augmented reality went from the vague promise of interesting things in the near future to tangible developments in software and hardware, proving that immersive computing is indeed the future.

Nearly a year to the day after the unveiling Magic Leap One, Magic Leap has dropped another update to the Lumin OS that runs the device.

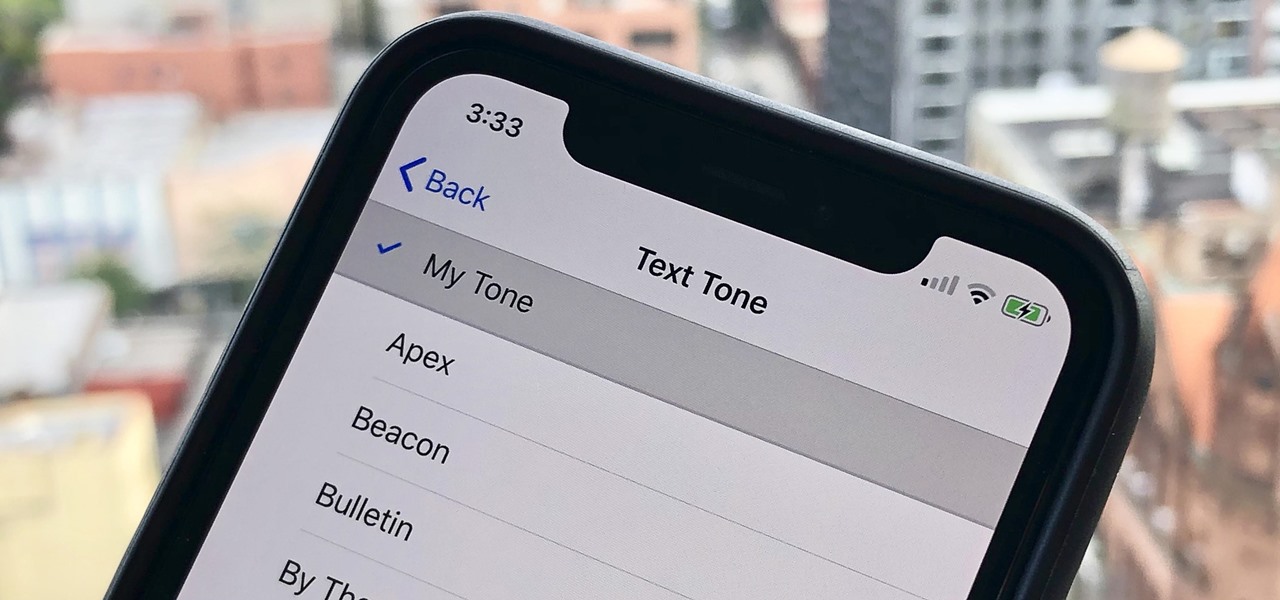
Your iPhone comes packed with a long list of excellent text tones to choose from. Bamboo anyone? Of course, for some of us, stock sounds from 2013 don't cut it anymore. We want customizability, something that's found more on Android than iOS. However, you can add your very own text tones to your iPhone right now, so long as you have a sound file in mind and a computer running iTunes.

You can never replace the skills and expertise of a professional graphic designer, but Canva comes pretty damn close. It's ridiculously easy to use the drag-and-drop design tool for both professionals and people like me who don't have the need (or knowledge required) to use more advanced graphic design software.

Whether you like to go swimming or jump in a hot shower with your Apple Watch on, the chance is pretty high that you'll get water inside its speaker. If you're a big runner, even sweat can get inside there. While there is no way to prevent water from getting inside your Apple Watch's speaker, there is an easy way to get it out so that your muffled speaker sounds brand new again.

With the change to a glass back, many of us are concerned about the durability of OnePlus 6. While glass does offer some benefits such as lighter weight, without proper reinforcement, it can easily shatter in one drop. Now we have our our first look at its durability thanks to JerryRigEverything.

With the software installation out of the way, it's time to build the framework within which to work when building an augmented reality app for Android devices.

Not all microwaves are created equal, so when you use the recommended cooking time on any microwaveable meal, chances are you're actually cooking the food too much or not enough. And unless you're really good at mental math or have a virtual assistant that's smarter than Siri and Google, you have to do things the long way — but not with these helpful apps for iOS and Android.

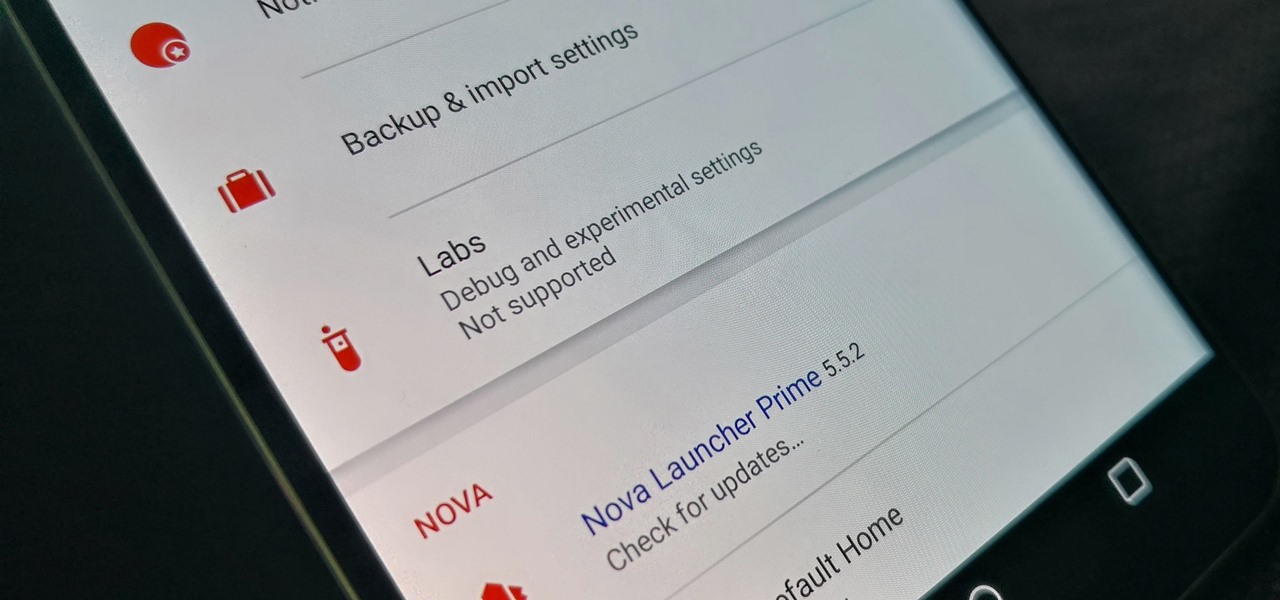
TeslaCoil's Nova Launcher is one of the best home screen apps on the Play Store. It's about as fast as it gets, and it's always among the first to add the latest Android features. However, it looks like Nova Launcher isn't showing users all of the customization options available — apparently, there's a secret menu, and it's pretty simple to unlock.

Amazon Web Services (AWS) opened its re:INVENT developers expo with a bang by launching Amazon Sumerian, a new tool that could become the dominant platform for building cross-platform augmented and virtual reality applications.

Mobile apps themselves are not always the end product or service for generating revenue. More often, they are deployed as tactics within a larger marketing or public relations strategy.