EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

When Stardew Valley launched back in 2016 on Steam for PC, it was instantly deemed a success for steering the RPG farming simulator genre back on the right track. Before its release, we hadn't seen too much in this particular field of games that caught the eye of the general public. Since then, the mega-hit Stardew Valley has made its way to the mobile world of Android and iOS.

When someone sends you a funny video, image, tweet, what have you, often the first thing you want to do is share it with someone else. Instead of copying the link and jumping over to another chat to do so, WhatsApp makes it easy to share content right from the thread you received it in, via the forward feature.
For some reason, the Slack app on Android and iOS is a little less customizable than Slack on other platforms, so you can't adjust the sidebar theme to different colors directly inside the app. But that doesn't mean you can't customize the look of your mobile app at all. It's just a little less convenient.

During the keynote at WWDC earlier this year, Apple introduced the latest iteration of its mobile operating system, iOS 12. Despite a thorough demo on stage, Apple glossed over new eye tracking features that use ARKit 2. Developers can now use the TrueDepth camera on the iPhone X, XS, XS Max, and XR to determine where your eyes are looking, opening up incredible new possibilities for new apps.
In the battle for best stock Android flagships, there are really only two choices: Google Pixel phones and OnePlus phones. Although the latter isn't true stock Android, it is impressively close and usually paired with more impressive hardware than the Pixel lineup. The latest is the OnePlus 6T, which will be a bit controversial for fans this year.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

Although the Essential PH-1 got off to a rocky start, thanks to steady updates, it has slowly become one of the best Android phones to come out in recent years. For $499, the Essential Phone is a cheaper Pixel, receiving updates almost as soon as the Pixel lineup does. What's more, you get a phone with an easily unlockable bootloader, which is the first step to rooting.

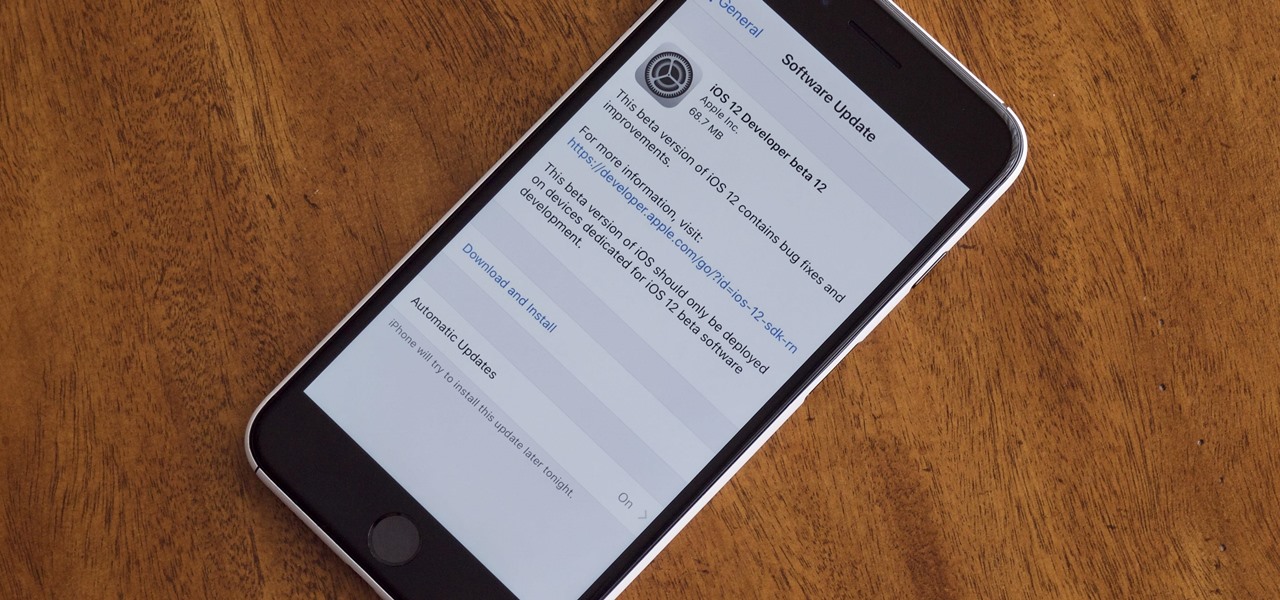
Right before the Labor Day weekend, Apple issued iOS 12 developer beta 12, which comes four days after dev beta 11 and public beta 9, and just one day after announcing the Sept. 12 event. This update primarily fixes a bug where you would be continuously prompted to install a new iOS update even when none existed.

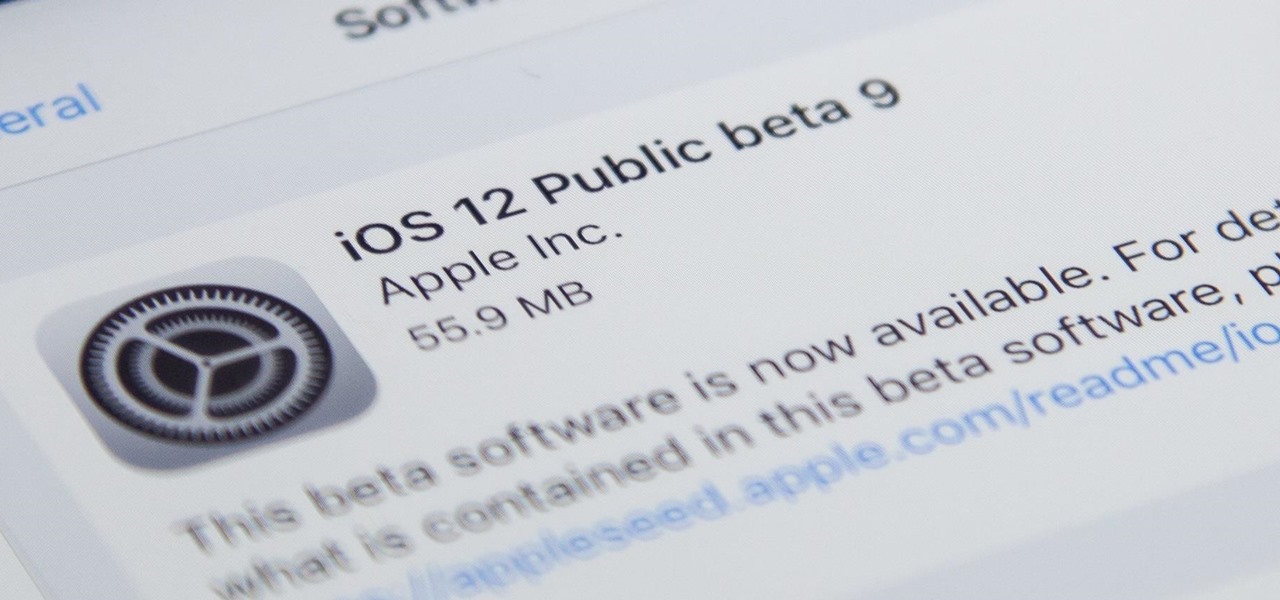
Apple released iOS 12 beta 9 to public beta testers on Monday, Aug. 27. The update comes at the same time as the release of dev beta 11. This is surprising, as Apple typically releases developer betas at least a few hours before the public version. Then again, everything Apple is doing with its iOS 12 beta as of late is surprising.

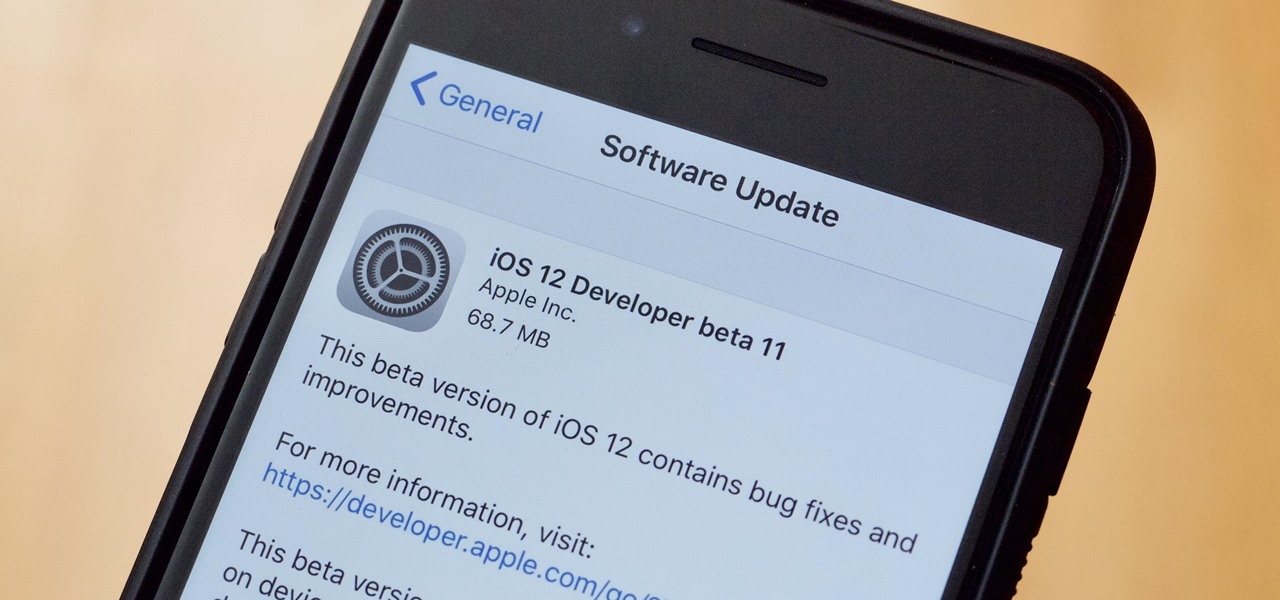
Apple released the eleventh developer beta for iOS 12 to registered software testers on Monday, Aug. 27, only four days after the company unexpectedly released both dev beta 10 and public beta 8. Apple has ramped up its beta release schedule as of late, offering minor updates twice a week in the lead-up to iOS 12's official debut in a few weeks.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

Have you noticed the many utility ARKit apps on the App Store that allow you to measure the sizes of horizontal planes in the world? Guess what? After this tutorial, you'll be able to do this yourself!

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

Google Lens is a fantastic addition to Google Photos for Android and iOS that allows your smartphone to identify a number of things in your pictures, like landmarks and contact info. Using this power, you can even find out how to buy almost any product you've taken a photo of — you don't even need the barcode.

In case you missed it, you don't have to chat one-on-one anymore in Snapchat. The company added group chats back in 2016, and they are increasingly gaining new features such as video and audio chats, so communicating Snapchat-style with all your friends at once is better than it's ever been.

TouchWiz might not be the Android skin of choice for hardcore aficionados, but the Galaxy's OS still has a ton of great features up its sleeve that help provide one of the most enjoyable smartphone experiences out there. Many of these are relatively hidden and overlooked features that you may not be aware of.

No matter your reasons, you might need a second phone number that's a little more disposable than your primary number — a "burner" number, so to speak. If you create this burner number using Google Voice, you'll get new functionality like call forwarding and voicemail transcripts, and best of all, it's completely free.

IFTTT is an application that allows you to automate certain tasks on your iPhone or Android. It can communicate with a myriad of apps and services on your phone by creating applets that perform actions automatically — actions you'd normally have to do manually. Finding those applets, however, can be a little difficult.

Gboard is one of the best third-party keyboards available for iPhones, but you probably don't know everything you need to know about it to become a real Gboard pro and stop using Apple's stock keyboard for good.

When you have an idea you want to jot down or a quick list to make, the Notes app on your iPhone is a great place to do it. However, by default, Notes use a blank canvas, which doesn't match the physical lined notebooks we're used to. If you've always use unlined or gridless sheets of paper, a blank canvas is probably fine, but you can actually customize your digital stationary with lines or grids.

For almost a decade, projector phones have tried to entice consumers with their convenience as media machines. While these devices are alluring, they've never really taken off with mainstream success. The latest effort, Moviphone, sounds tempting if you watch a lot of films and TV on your smartphone, but is it good enough to be your daily driver?

So, your grandmother finally wants to ditch her flip phone for a shiny new smartphone? Congratulations. But helping her get used to her new device, even when it's an iPhone, is no small task. Grandma mastered checking her email in late-2012 and just recently learned there's a thing called "Facebook." But we love grandma, and thanks to this guide, we can definitely make this happen for her.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

One thing that makes Signal Private Messenger better on Android over iOS is that you can better secure the app with a password or passphrase. Best of all, you don't need to install an app locker to get this working — you can do it right from inside Signal.

Well, well, well. Uber, we knew you were investing a ton of money into creating self-driving taxis and flying cars, but what we didn't know is that you were already testing out your driverless vehicles on the streets of New York City.

For some of us, winter puts the brakes on apps like Pokémon GO since smartphone screens usually only respond to bare fingers. Nobody wants to be that guy who caught frostbite chasing a Sneasel. When you use normal gloves, the display's sensor simple doesn't activate, so that doesn't help any. Fortunately, several options for touchscreen-friendly capacitive gloves are on the market to help you through this last blast of winter.

A few months ago, LlabTooFeR leaked a full system dump from Google's then-unreleased Pixel and Pixel XL smartphones. That may not seem like a big deal at first glance, but the system dump contained all of the preinstalled apps and services from Google's new flagships—including the much-anticipated Google Assistant.

Thanks to the Edge variants, Samsung's Galaxy S phones are just a few millimeters off in body size when compared to the Note series, and just 0.2 inches smaller when it comes to displays. Now that the two flagship models are almost identical in size—with matching curved displays—there's really only one thing that separates the Note7 from the Galaxy S7 Edge: The S Pen.

Quick Look, first introduced in 2007, is an instant preview feature on the Mac operating system that lets you view files and folders without opening them up. Just highlight a file, like a picture or text document, then press the spacebar on your keyboard to get a speedy preview of it.

Prior to this year's WWDC, there were lots of rumors that Apple might finally be making a version of iMessage for Android. While that never came to fruition, a few big updates to a very useful app have now ensured that we can seamlessly send and receive Android texts in Apple Messages on our Macs.
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

This is the second installment of the short series on how to remove user passwords in Windows. Once again this has only been tested on Windows 7. If I can find some time between two jobs and school I'll test all the ways on Windows 10 and Windows 8/8.1.

Near Field Communication, or NFC for short, is a feature that allows our smartphones to wirelessly communicate with other devices over a short distance while using almost no power at all. Think of it like a slimmed-down version of Wi-Fi or Bluetooth that can send a small burst of data two inches away without having any measurable impact on your battery life.

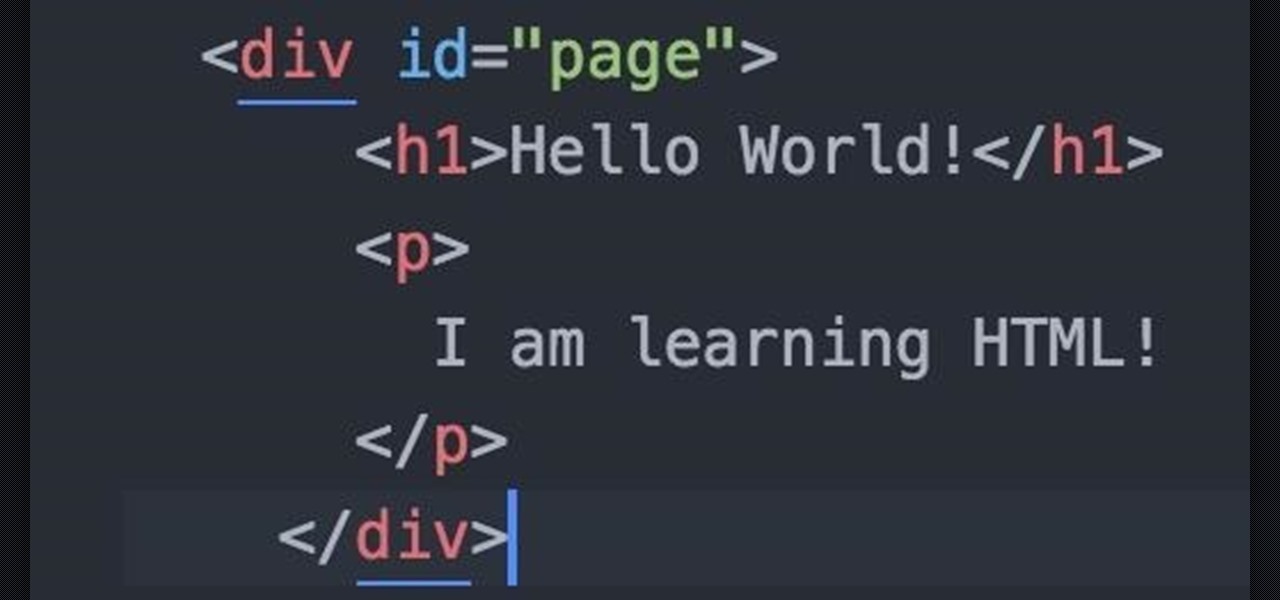
Welcome fellow Null-Byters! Sorry for the delay, this time of the year can be hectic for all of us. Hopefully this will not happen again. In this "tutorial" we will go over more styling and make our page look even better!

Hello there, reader! If you've clicked on this How-to then it means you are interested in learning some C programming or just generally curious about what this page has to offer. And so I welcome you warmly to the first of many C tutorials!

Smartphone cameras are so good nowadays that there's almost no reason to own a point and shoot. Once the megapixel spec race was finally settled (hint: more isn't always better), manufacturers started focusing on the quality of their camera sensors, which has led to a huge jump in color accuracy, dynamic range, and image clarity.

In the recent hit movie Furious 7, the storyline revolves around the acquisition of a hacking system known as "God's Eye" that is capable of finding and tracking anyone in real time. Both the U.S. spy agencies and an adversarial spy agency (it's not clear who the adversary is, but the location is "beyond the Caucasus mountains," which could imply Russia?) desperately want their hands on this system.