Yes, there's already a way to jailbreak iOS 9 on your iPad, iPhone, or iPod touch, but given the fact that it's only been out for about a week means that not all developers have had a chance to make their tweaks fully compatible yet. That doesn't mean they won't work, but that they might not be as smooth as they should be.

Hello my fellow hackers, it's been a while since my last post, I can't get the time now-a-days for the posts but can manage to tend to comments.

Have you ever been using your computer when a friend randomly decides it's time to start up a text message conversation? You usually have to stop what you're doing on the desktop, then go pick up your smartphone and respond to the text. Then, if your buddy replies with another message, you have to juggle back and forth between your mouse and keyboard and your handheld device.

Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.

All of Apple's products are praised for being extremely easy to use. So much so, that your grandma can pick one up and be a "pro" within a few hours. However, this isn't necessarily a good thing for us real power users who want more granular control of our devices.

Amazon makes it exceptionally easy to purchase anything you want in just a few minutes. From textbooks for school to live ladybugs, its more surprising when you can't have something delivered to your doorstep in a few day's time.

After you have registered to this site,sign in then to start missions. Basic Missions

Facebook essentially strong-armed us all into installing their standalone Messenger app for mobile devices, but the recent initiative that allows third-party development on the platform definitely makes it worth your time.

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

When it comes to getting your computer and smartphone to work well together, there's no service more robust and capable than AirDroid. For years, it's been the go-to tool for users looking to transfer files between their devices or access contact lists and call logs from their computer.

Third-party keyboards have been available for iPhone ever since iOS 8, but which ones are worth checking out? There have been many options over the years, and if you want keyboard features like swipe-typing and themes, you're going to have to put Apple's stock QuickType keyboard on the backburner and try out these top hits.

When it comes to dictating what happens when the Galaxy Note 3's S Pen is detached, the stock settings that Samsung provides are severely lacking. There are only two measly options: launching Samsung's own Action Memo app, or displaying the Air Command menu.

Keeping data private is vital in the days of smartphones and the free-floating information they carry. Justin wrote a guide on many of the deeply hidden and sometimes concerning privacy settings in iOS 7. Now we're back to cover some of the new (and old) privacy settings in iOS 8 that you need to address right now.

Voicemails are like chores for me. I have to listen to them, but never really feel like doing it. When I finally do, most of them get deleted right away, but every so often they'll be one I save and listen to over and over again, whether it's a cute birthday wish from grandma or a hilarious joke from my friend.

Loaded with a gorgeous display and a powerful processor, the Kindle Fire HDX is an impressive all-around tablet, especially when it's used for what Amazon Kindles were built for—reading electronic versions of novels, textbooks, and other printed works.

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

When it comes to theming your Android device, it's the little touches that count the most. That's why developer SArnab created the Android Theme Engine, an Xposed Module to theme those hard-to-reach corners of the Android System that often go untouched with other themes.

Facebook will let you do pretty much anything via a text message, but unless you still have a flip phone, it's more of a novelty than actually useful.

The camera situation on the all new HTC One is a little daunting. The M8 has not one, not two, but three camera lenses built in. First, there's the 5 megapixel selfie machine up front, then around back, there's the new Duo Camera with a refined UltraPixel sensor. HTC has done things differently here, and the UltraPixels and dual lenses means that the M8 doesn't necessarily take pictures like you'd expect—and that's not a bad thing. With a little guidance and some easy tricks, you can use all ...

Welcome back, my aspiring hackers! In previous tutorials, I have shown you how to scan the globe for vulnerable servers and write simple scripts in BASH and Perl to perform other reconnaissance tasks. In a very recent guide, I taught how to scan vulnerable servers for Heartbleed.

After many beta builds, Apple has finally released iOS 7.1 to the public. It includes bug fixes for the old iOS 7.0.6, along with UI enhancements and even some new features.

The new Google Now Launcher has hotword detection and one-swipe access to Google Now, but personally, it's not enough to convert me away from other launchers like Apex or Nova. Just because it's Google's official launcher for stock Android doesn't make it better than all the rest.

When you post something online, it pretty much stays there. So it's no surprise that Snapchat, the self-destructive photo-sharing app, became such a huge hit, boasting an estimated 50 million users. Its ephemeral nature has proven popular, especially with teenagers—who are now well aware of the burden that permanence on the internet has.

WhatsApp is one of the most well-known and most utilized cross-platform chat applications available today. It's free for one year, and only $0.99 a year after, which is chump change when you realize there are no hidden costs like international charges. Basically, it creates an easy to use forum for you and your friends to chat, regardless if they're an Android or iPhone user.

With all of the new features and third-party apps out there making Android better and faster every day, it's quite frustrating to me that keyboard advancements remain relatively static.

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

My favorite color is blue, but if everyone I knew said the same thing, I'd probably switch to red—there's nothing cool about uniformity. One place I'm guaranteed to see plenty of my favorite hue is on Facebook. The social network has gone through many redesigns, but its signature color scheme has never changed. While Facebook introduced cover photos, which allows for a little more creativity on your Facebook page, everything else is pretty much the same across all one billion plus profiles. B...

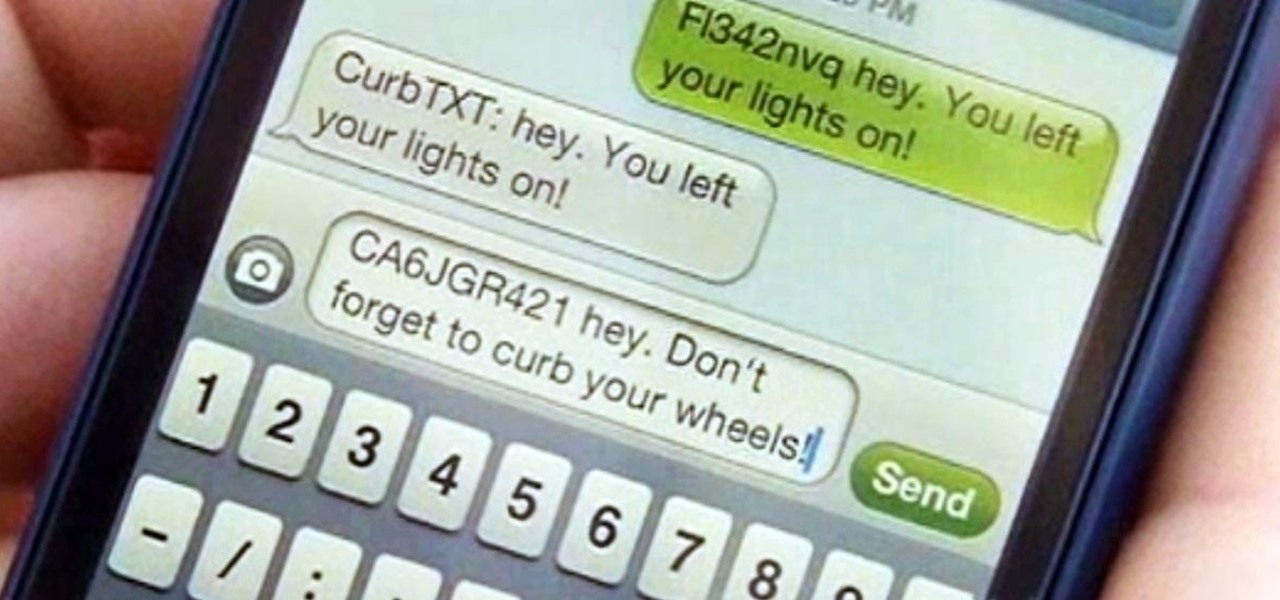
Parking. Ugh. Parking is about as fun as running through a swarm of bees while being chased by a pack of wolves from The Grey.

Every Windows system includes command prompt; and while a lot of people on Null Byte and WonderHowTo in general know how to use it, some people don't know anything about it, even how to access it.

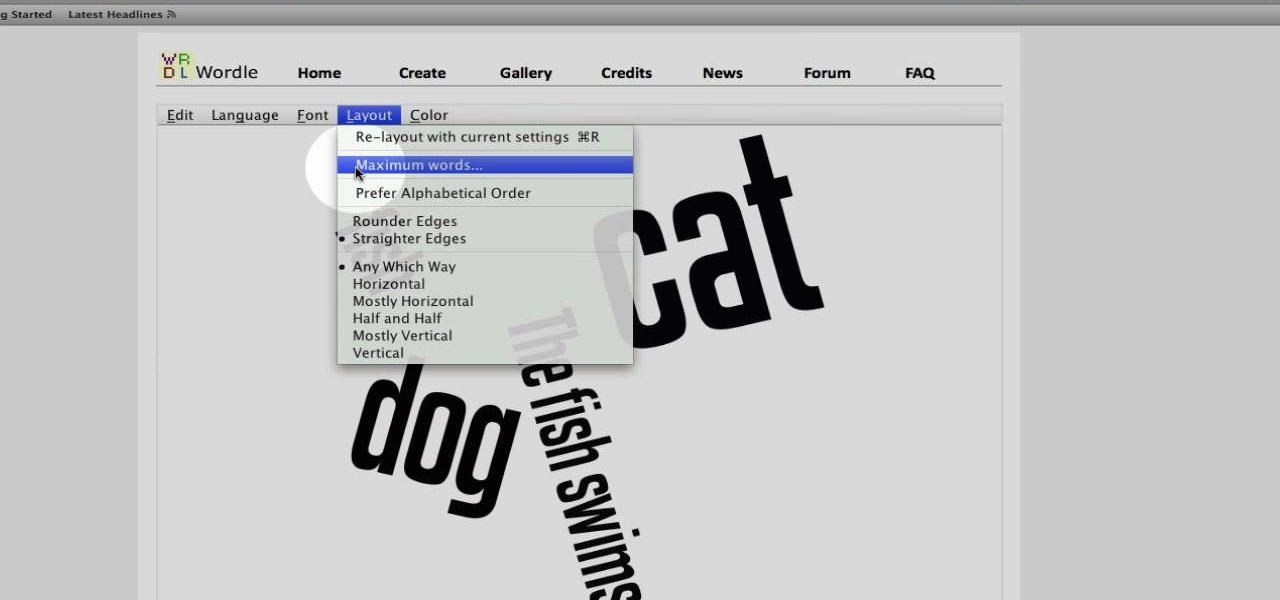
This video tutorial belongs to the Computers & Programming category which is going to show you how to use Wordle to create word clouds. Go to Wordle and click on the 'create your own' link. In the first box, type in your text, and in the second box enter the URL of any blog, blog feed or any other web page that has an Atom or RSS feed. In the 3rd box enter your del.icio.us username, if you have one. After typing in, hit 'go' and you get your Wordle file with the words written in different sty...

The pen doesn't have to stop on the paper. Your art masterpiece doesn't have to stay on the canvas. You can share your favorite drawings with everyone, right on your own chest. Wear your art designs with pride by using a scanner/printer, a photo editing application, an iron, and Avery iron-on Dark Fabric Transfer paper. And don't forget your tee shirt.

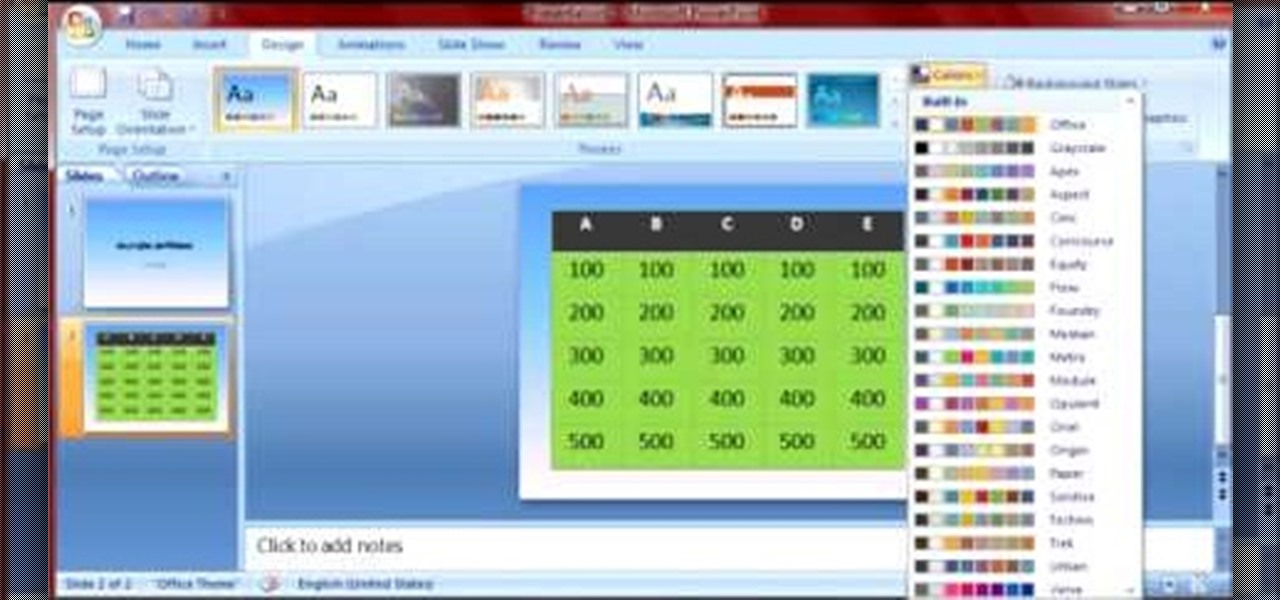
Microsoft PowerPoint is a powerful software to make presentations. It can also be used to make a Jeopardy board. To do this open a new PowerPoint presentation. Start with a title layout. Now add a gradient to its background. To do it right click on it and select the fill option from the menu. Select the color of you choice and fill the background. Now add the title in the layout with suitable fonts. Now add a new slide and insert a 5 X 6 table to it. Format the table with colors of your choic...

1. This video shows how to use getURL in Flash ActionScript. 2. Create a new flash application and draw a circle with blue color using tools. 3. Place a text box over the circle and enter the text inside the text box. 4. Then make that circle and text box a button object using the "convert to symbol" menu. 5. Then open the action script window. 6. Create a variable named "url" with string value named Wen Arene. 7. Then create UrlRequest object. 8. Then add a button click event listener for th...

Shown here is another video tutorial made possible through TutVid. In this video, you are learning the basics of Action Scripting in Flash. This lesson is titled "Action Scripting:101." Action scripting is one of the coolest thing about flash. The thing that makes flash special is the ability to make simple actions interactive. Flash possibilities are endless!

Drawing an eye can be tough. Drawing a female eye can be even tougher, because it needs a delicate touch. Drawing a female eye from a profile view is yet, even harder. But it doesn't have to be. Watch this tutorial to learn how to draw the female eye from a side profile. Make sure to pause the video after each step and look at the screen every few seconds while you are drawing.

Long-time packeteer Bob Bruninga, WB4APR, developed the Automatic Packet Reporting System (APRS), which allows packet radio to track real-time events. It deviates markedly from the usual message- and text-transfer activity. Instead, APRS concentrates on the graphic display of station and object locations and movements.

Why make a flip book? Because all animation – even stick-figure Flash animation and multilayered, highly technical 3-D effects – is built on, and can benefit from, the basics of the craft first developed by artists working at the beginning of the last century. And while fancy computer programs are nice, you can teach yourself these basics using nothing more than a pad of paper and a pen, and replay them over and over without any extra technology needed.

Want to watch Hulu on your iPhone? Maybe Netflix on your iPod Touch? YouTube videos? The best way to watch these hits is with a brand new… and FREE… paperclip iPhone stand.

Use Adobe Acrobat to edit your PDF files. With handy software like this you will be able create the perfect version of whatever project you are working on. Text, photos and images can all be changed with this handy advice.