So you recycle your newspapers and plastics. Big deal. “Freegans” are trying to save the environment by living exclusively on stuff in your trash. Here’s how to join them. You will need a willingness to get dirty, a tolerance for eating food from the garbage, and a commitment never to buy anything new. Watch this video tutorial and learn how to dumpster dive and live like a freegan.

What is a freegan? It's an anti-consumer movement, and a way of getting free food by dumpster diving. Get a crash course in dumpster diving with an accomplished Biology professor who demonstrates the lifestyle of a freegan. Watch this video ecology tutorial and learn how to dumpster dive.

In this episode of Halo 3 Tricks Stoned, Shane, and Smoogerz show you how to fly around in a dumpster on the campaign level, The Storm.
There is no discount like free. And if you are not afraid to get your hands and clothes dirty foraging through dumpster bins, trash cans and the back alleys of department stores or restaurants to score perfectly usable items and perfectly edible food without paying a single cent, then dumpster diving might be right up your alley.

Skip Conversions = guerilla art + recycling + creative urban upcycling. My three favorites below (particularly the pool, which literally interprets the term "dumpster diving").

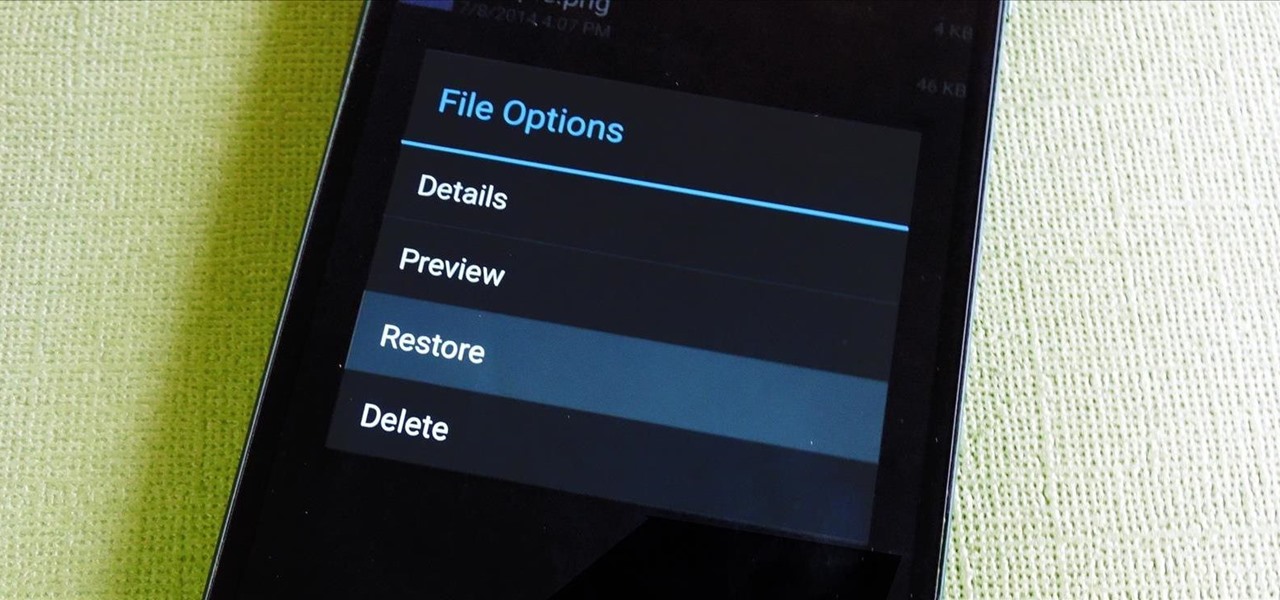
Do you ever wonder if the files you're trashing on your Mac are actually trash? Let's say there are 80 million computer owners running Mac OS. If each user trashes at least 10 files each day, that's 800 million deleted files that cease to exist every 24 hours. If that doesn't sound like a lot to you, a month would equal 24 billion junked files, a year—nearly 1 trillion.

Dumpsters make great swimming pools and skateboard ramps, but when they're full of trash, they're pretty valuable, too. You can get a surprising amount of free booty dumpster diving. If you're a penny pincher who values low cost (re: free) functionality, check out Apartment Therapy's guide to mastering the craft. Below, my three favorite insider tips.

If you've ever used a computer, you're surely familiar with the concept of a Recycle Bin (Windows) or Trash Can (Mac). To sum it up, files that you've deleted are not actually gone from your storage, they've just been moved to a different location. You can then restore the files if need be, or empty them, permanently deleting them forever to free up space.

Identity theft typically occurs when someone uses your personal information such as social security numbers, credit card numbers or account information to perform various misdeeds, and you are left to clean up the mess.

You can't be a couch potato without a couch. So stop squatting around and listen to these hints to learn how to furnish your apartment with practically no money.

Bob Harris of decorative concrete institute explains how you can remove your tiled or carpeted flooring for a concrete substitute. He suggests when your removing carpeting that it can be very heavy and advises you to hire someone who can lift and carry it out, or rent a dumpster for easy take away. He states that after the carpet is removed you'll need to remove the adhesive from the floor. You can do this by stripping or grinding, and at other times the use of harsh chemicals may be needed. ...

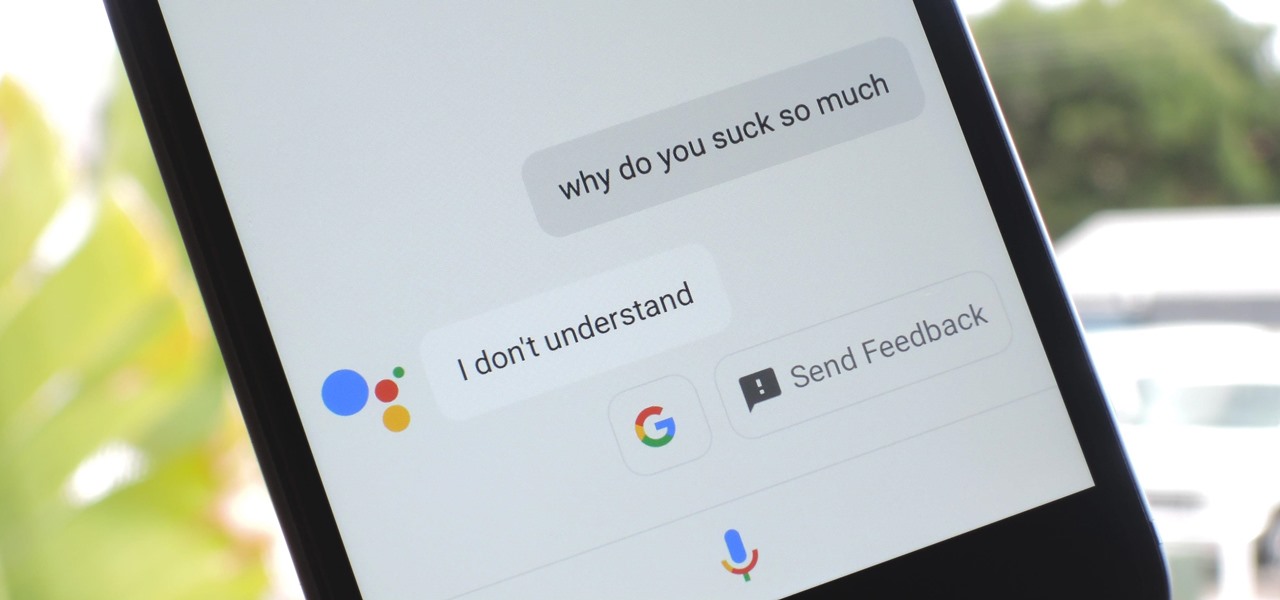
Google Assistant was just released for iOS today. You may know it as the AI-powered assistant that makes Google Home tick, or perhaps you've heard from one of many review sites about how much better it is than Siri. Well, before you run off to the App Store to install Google Assistant, let me save you some time: It sucks.

The other day I was doing the math on roughly how many eggs I eat each year. I estimated about 500. That's a lot of eggs. And, subsequently, that's a lot of eggshells to throw in the trash.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

You might think your photo is amazing, but in the midst of editing it and getting ready to post it on social media, you notice something in the background. Maybe it's an unwelcome stranger or a wide-open dumpster, or it's the entire backdrop, but suddenly you realize that it's bad. Although you look good in it, the background just doesn't work — which is why you can always get rid of it.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.
Welcome back Hackers\Newbies!

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.

Check out this video to see how to make pneumatic power with stuff from your dumpster. Take one empty Tekapur (polyurethane foam) spray can, and one hand air pump, and watch the instructions. Soon, with a wee buit of time and effort, you'll have some cool pneumatic power at your fingertips.

The resourceful fisherman of Holy Island (Lindisfarne, Northumberland, UK) are upcycling beautiful old fishing vessels into storage sheds. Flip it upside down, add a door, and the result is striking.

As Popsci says, these DIY snow vehicles show winter who's boss. The Snow Chopper

Despite the tremendous increase in recycling programs across the states, 136 million tons of municipal solid waste still ends up in landfills. So, the next time you throw away something, conjure up your DIY spirit and ask that trash, "Are you really trash, or just the beginning of my next ingenious project?"

Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information you want to keep private, private, should be important to you.

QI and ZA. QI n pl. -S the vital force that in Chinese thought is inherent in all things