
How To: Program in Context Free
In my free time, I like to program in an image programming language called Context Free. You can download it at www.contextfreeart.org for free.


In my free time, I like to program in an image programming language called Context Free. You can download it at www.contextfreeart.org for free.

In this two part episode, Aharon Rabinowitz shows you how to use audio to control time. You'll learn how to make your video automatically move forward in time to the beat of the music - a technique used in tons of music videos and commercials.

This is a two part video tutorial. Be sure to click on Chapters 2 as well to get the full tutorial. Taking a look at the popular technique of designing lower thirds and the process it takes to design these using Photoshop. Photoshop is the perfect solution for this task with the ability to mix text, texture, graphics and logos to create compelling titles for your show or video.

This is my list of programs that I must have on my PC, but I think you can also use them, so here is the list:

If you need to know how to create a compound path in Illustrator, the quickest way is to go to the object tab in Illustrator. This gives you with the click of a button an easy way to create a compound path.
If you need to know how to apply clipping mask in Illustrator, the quickest way is to go to the object tab in Illustrator. This gives you with the click of a button an easy way to apply a clipping mask.
Many people think that learning to use Regular Expressions is difficult, but if you stick to the basics it is actually quite easy. This screencast and cheatsheet will give you a gentle introduction and allow you to gradually expand your knowledge into advanced usage.
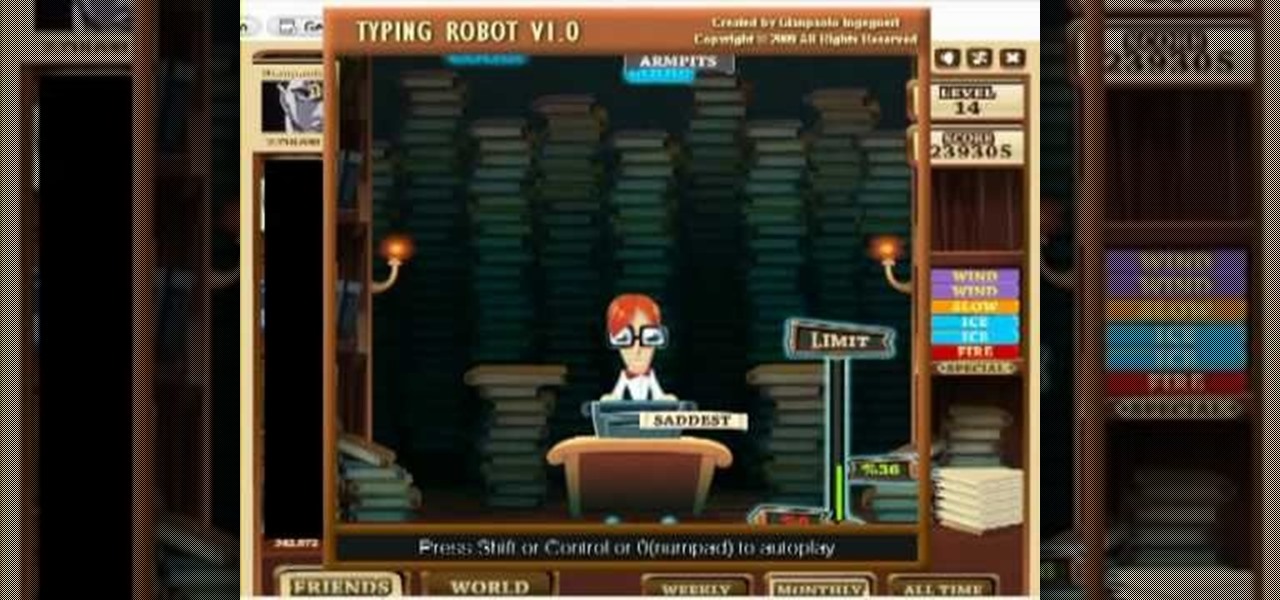
http://www.texturemind.com/post463/ TypingRobot is an artificial intelligence studied to increase your points record with the Typing Maniac game on Facebook. It can recognize several labels because it uses a powerfull OCR system (tesseract) and some principle of word correction. With this program you can make millions of points without problems (my personal record is about 2.700.000 points).

Eventually, we plan on doing some root the box competitions here at Null Byte, but we're still looking for a server to play on. Anyone want to donate one? You won't regret it. Root the box is like 'king of the hill', except you have to hack a server and maintain access. Each server will have numerous known security holes, but until then, let's get back to the regular weekly coding sessions and realistic hacking missions on HackThisSite.

We'd like this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with (anyone want to donate one?), we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But for now, back to the normal flow of things...

In this article I'll show you how to make a simple IP address notifier. The program will text you your new IP address, in the event that it changes. For those of you with dynamic IPs, this is very useful. I'm constantly frustrated when my IP changes, and it's handy to be notified via text when it happens. To use the program, you'll need Python 2.7 or later, urllib2, and a program called "text" (see this article here to get it).

We're aiming for this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with, we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But, for now, back to the normal flow of things...

The community tore up the first realistic mission last week. You've applied the techniques learned in the basic missions to a real scenario, so I'm pretty content. The realistic missions are where the learning gets intense and where we can apply real knowledge to extremely realistic situations. We will also be continuing the normal Python coding and hacking sessions. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, f...

In this article, I'll show you how to create a simplistic AES python based text encryptor. You'll need python 2.7 and PyCrypto (found here). The code is fairly simple, a user enters an encryption key (which basically tells the program how to scramble the text, using an algorithm), then the text to be encrypted. The program takes the key and text and inputs it into the "cryptograph" or code-based algorithm from PyCrypto. PyCrypto can use 16, 24, or 36 character encryption keys, but for the sak...

This is Part II in the Lockdown: The InfoSecurity Guide To Securing Your Computer series. Before beginning, check out Part I. This article will cover using alternate software to increase your security and will provide you with some information about websites and programs that test a computer's security. It will also guide you to software you can install or follow so you know what programs need to be updated on the computer. Lastly, I will talk about some features that should be disabled when ...

Community byters, it's time to get serious. We are finally moving on to the realistic missions in HackThisSite. This is where the learning gets intense and where we can apply real knowledge to extremely realistic situations. We will also be continuing the normal Python coding and hacking sessions. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the 10th Community Byte session for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

If you've ever heard software piracy terminology being discussed, I'm sure the term KeyGens came up. KeyGens is short for key generator, which is a program that exploits algorithmic faults in software by generating software license keys that appear to be genuine. Normally used as a technique to protect the source code software and prevent piracy, a key generator exploits the key algorithm to effectively nullify the need for any software licenses. For example, we must try to find patterns in t...

Null Byte is looking for forum moderators! Welcome to the ninth Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to the eighth Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

Welcome to another Community Byte announcement! In the past two sessions, we have coded an IRC bot in Python capable of issuing commands. Since it can issue commands and most of you are new to programming, that project will stay idle for a while. Other commands such as voice and half-op can be easily hacked in via common sense, even if you weren't there for that session.
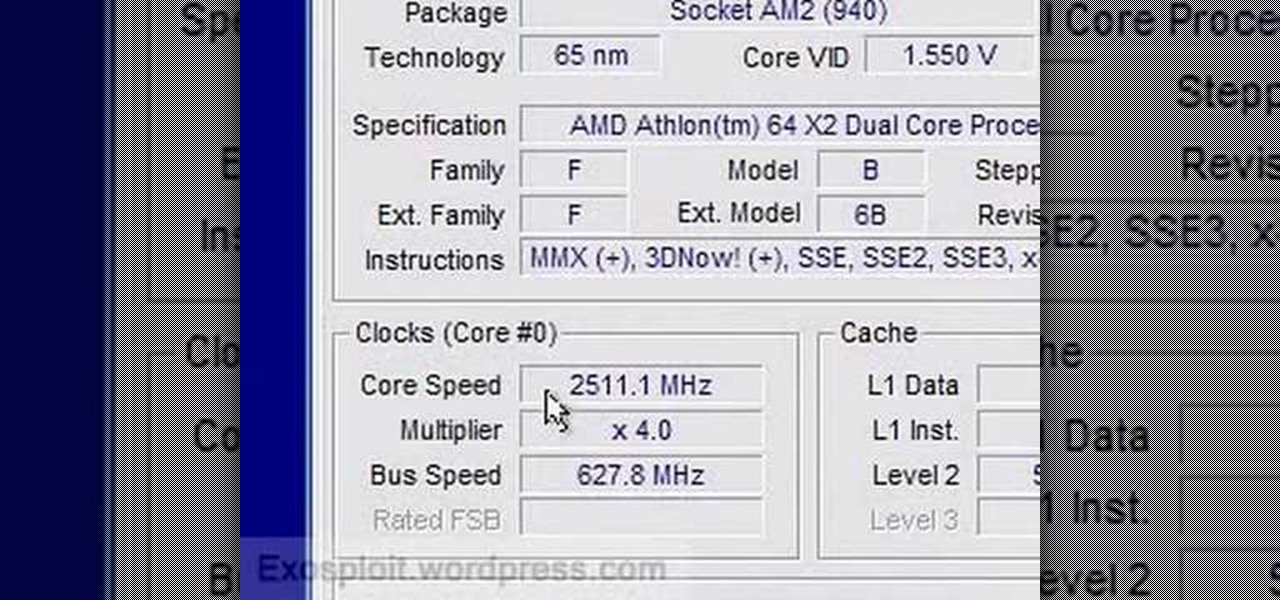
In this video from exosploit we learn how to find your system specs in Windows XP. If someone is trying to help your computer, you might need this information. Right click My Computer, and click Properties. Here you'll see your operating system, service pack, and how much RAM you have. Also google cpuz. Go to the first link and download it. Extract it and click the main file. Here it will tell you your processor, mother board, what bios version you have, how much RAM you have, and it will tel...

In this tutorial, we learn how to clear the ARP cache. First, go the command prompt on your computer and type in "C:/>netsh interface ip delete arpcache Ok". Press 'enter' on your keyboard and then it should be cleared out. If you want to view your ARP cache, type in the command "C:/>arp -a". If this fails, then you will need to use Microsoft Windows to repair the network connection. If this doesn't work, talk to the person that manages your connection. If successful, this will help make your...
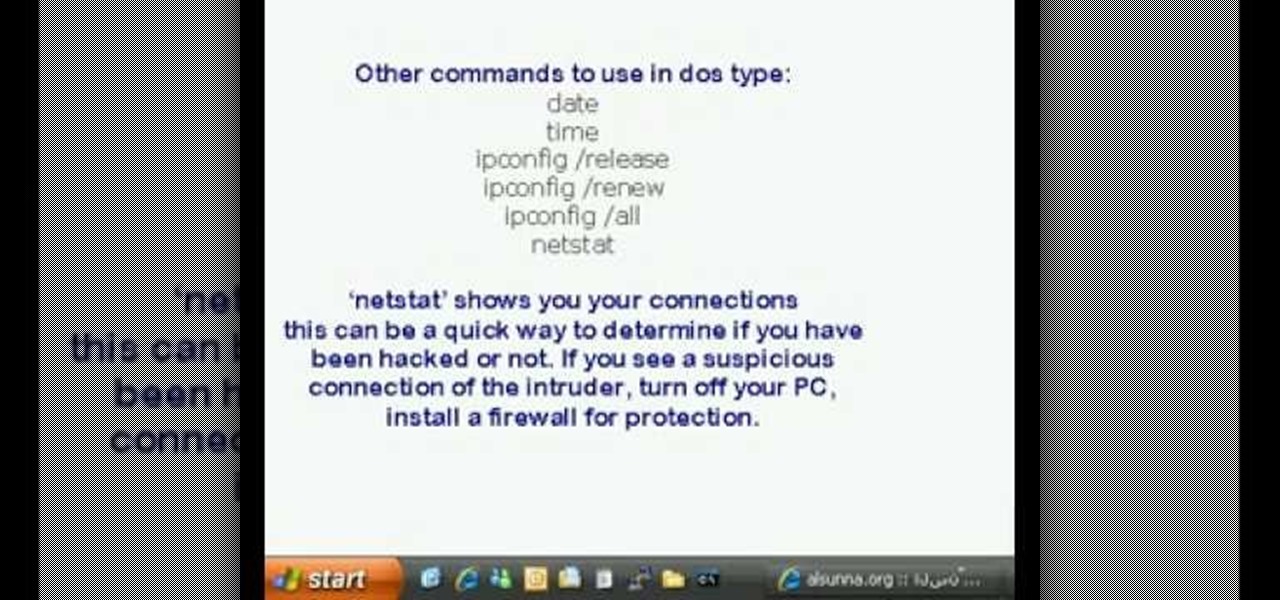
This is a video tutorial in the Computers & Programming category where you are going to learn how to find and ping your IP address. Go to start > run and type in "cmd" to get the DOS window. Here type in "ipconfig" and hit enter. If you are online, your IP address will be displayed. If you are offline, go online and try again. Then in DOS type in "ping yahoo.com". This is to see if you can connect to Yahoo. If you are online, the site will reply 4 times. If you type in "netstat", it shows yo...

Greek yogurt just sounds like a fancy version of regular yogurt, but it's so much more than that if you're trying to lose weight. Greek yogurt has twice to three times the amount of protein of regular yogurt, which means you'll stay satisfied and full longer. It's also thicker and creamier, rather than than slippery and watery like regular yogurt.
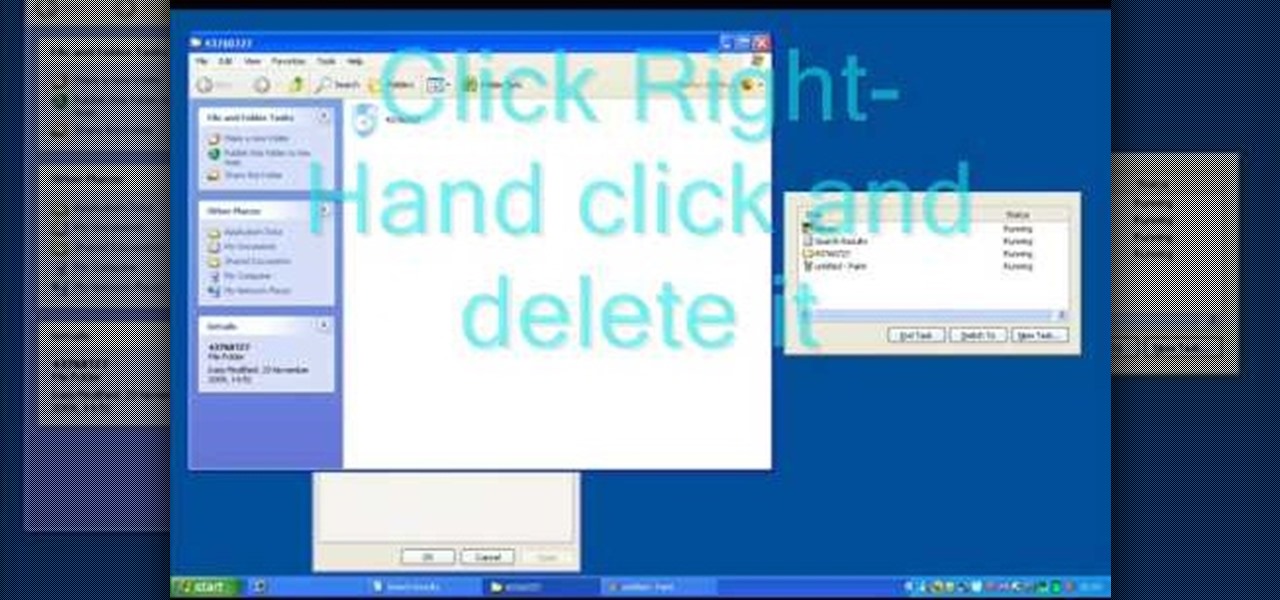
In this tutorial, we learn how to remove security tool in less than one minute. First, restart your computer, then press "ctrl+alt+del" when your new window starts up. After this, wait for a few seconds, then if you see the security tools pop up, end the task for it. Then, go to the start menu, then all programs, then look for any security tools. Right click, on "find target" then delete it! After this, your security tools will be deleted and will stop annoying you. You will be able to delete...
In this video, we learn how to remove Security Tool the simple way. Most ways will not remove this from your computer, but this way will. To start, you will need to restart your computer. After this, press ctrl+alt+del the moment Windows shows up. Then, go to the Task Manager and look through the programs that are open. When your security tool opens, press the same buttons to get the mouse free. Then close the security tool from the Task Manager. Now, go to your desktop and press on the icon ...

In this video, we learn how to make a scary hip-hop beat. Start with a normal beat and then make a high pitched sound followed by a deeper sound. Use a deep treble as you continue to play the song and then add in creepy tones that you find in the different areas of the program. Explore the different types of scary beats that they have available then start to put them all together. Once you get all the different beats together, you will be able to add more bass or treble. When finished, you ca...

In this video, we learn how to use Spotify without any ads. First, you will need to download the program from: naspotify. Once you have this installed on your computer, open it up and open up Spotify. Now, when you are on Spotify and you see an ad come up, you just need to press Alt+F9 and the ads will be gone from your page! This is a very easy way to get rid of the ads without having to go to a lot of trouble. This doesn't require any additional downloads, so if you are using a free version...

In this tutorial, we learn how to remove pop up screens when Avira Antivirus updates. First, locate the installation folder for Avira, this should be in your computer programs. After this, locate the file "avnotify.exe". Next, right click this and go to the preferences option. Now, go to security, then edit, then click on the system option. Click "deny" on all the boxes in the bottom section, then save these. Now, the next time your Avira updates, you will not get a pop up box that tells you ...

This video tutorial is in the Computers & Programming category where you will learn how to secure your wireless internet connection. If you don't secure your wireless internet connection you are allowing others to enter in to your network. Open the set up CD and first change the network name from the default name to anything that you like. For this go to step 3 of 'naming your network', type in your network name and click 'next'. Then you enable security on the network by choosing 'WPA2'. Nex...
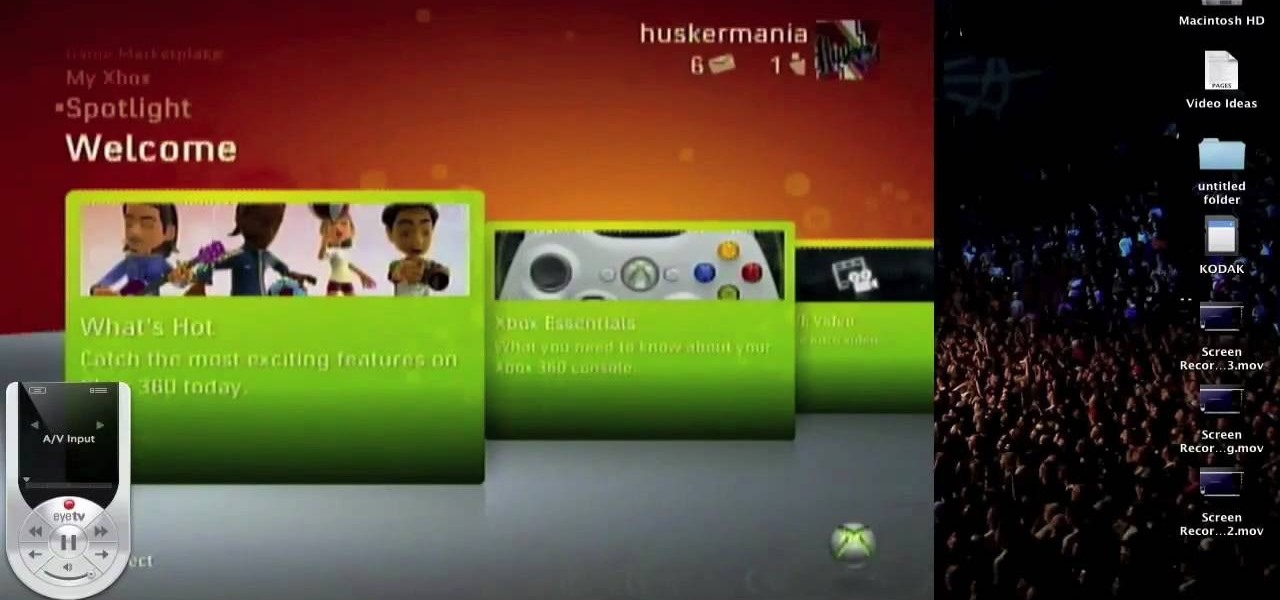
In this tutorial, we learn how to use your Mac screen as a gaming display. First, you will need to plug a USB cable into your computer that also has a source to place in a cable to your television. After you have connected these, the program will start automatically. To change this to view on your computer, change the controls to go onto your computer instead of the television. Now, turn on your game console and you will hear the start up noise on your computer, then see the game load onto yo...

In this Computers & Programming video tutorial you will learn how to make Google go crazy. This is a cool cheat that makes all the pictures in Google to fly around the page. First do a Google search for 'Google go crazy' and open the first link. Then in another tab search for anything with images, for example 'guitars '. Then remove everything from the address bar of the images page and copy and paste the java script from the 'Google go crazy' page in to the address bar. Click enter and all t...

In this Computers & Programming video tutorial you will learn how to create a zip file. You need to create a zip file in order to upload your website in to the digital dropbox in blackboard. Blackboard doesn't like folders with extra files in it. So you have to turn it into a zip file. You have created your 'my first website' inside which will have index files and image file. To get this onto blackboard in Mac, right click on the folder and select 'compress my first web site' option. Now you ...

In this Computers & Programming video tutorial you will learn how to use Stock.Xchng to access free stock images. The site is at SXC. Go to this site and you will find a large number of stock images that are free to use. And every day new photos are being added. You can search for an image by category by clicking on the search box and scrolling down to find your category. You can also type in the search box to find a photo of your liking. The image also tells you what is the screen size, prin...
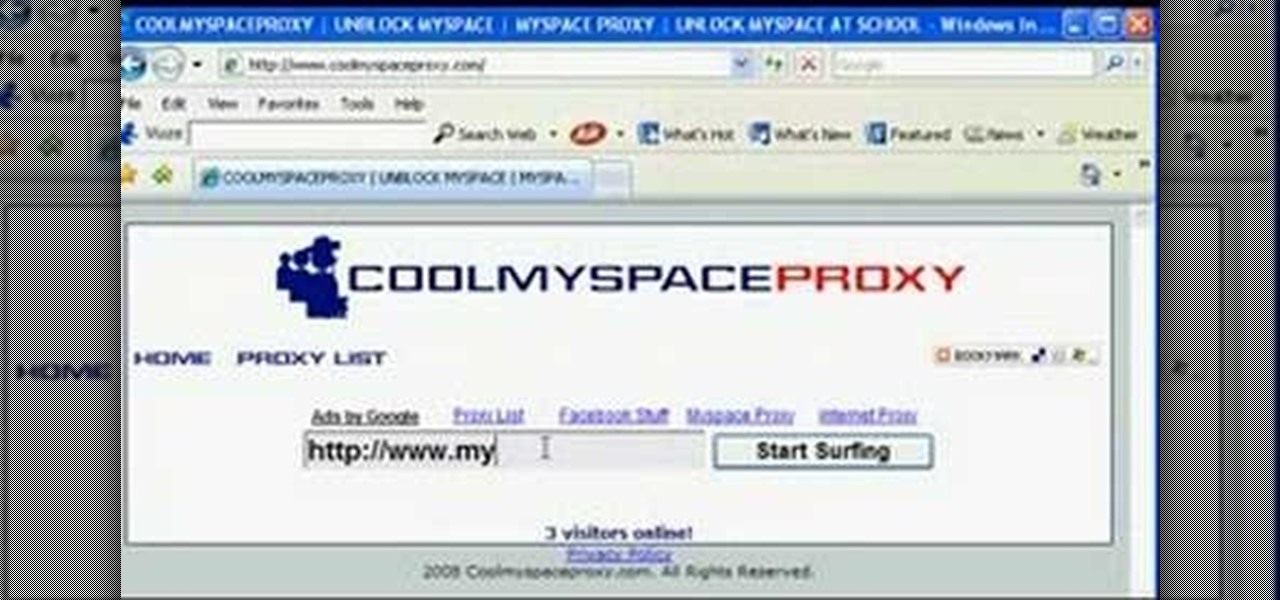
In this Computers & Programming video tutorial you will learn how to unblock MySpace (or any other site) at school or work or anywhere else. This is really very easy and simple to do and takes practically no time. It is like going directly to the original site. For this, you first go to the site Cool MySpace. Once on this site, simply type in the address of the website you want to go to in the surf box. For example, http://www.myspace.com and then click on 'start surfing'. That's it! You are ...
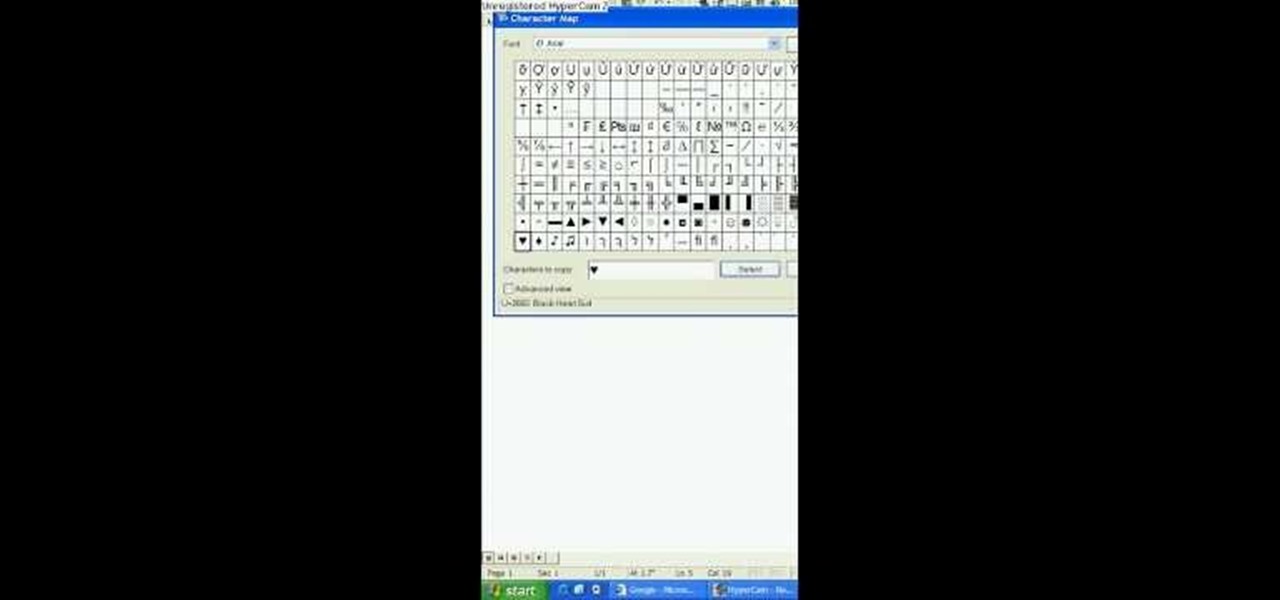
In this tutorial, we learn how to make a heart and other symbols on a computer. To make a heart, you will want to click on "run" and type in symbols inside of the white space. A new window will come up with a number of different symbols for you to choose from. You can choose the heart symbol on this, or you can choose any other symbol you would like to use. This isn't like clip art, it's just a simple symbol that anyone can use while they are in a word processing program and need a symbol tha...
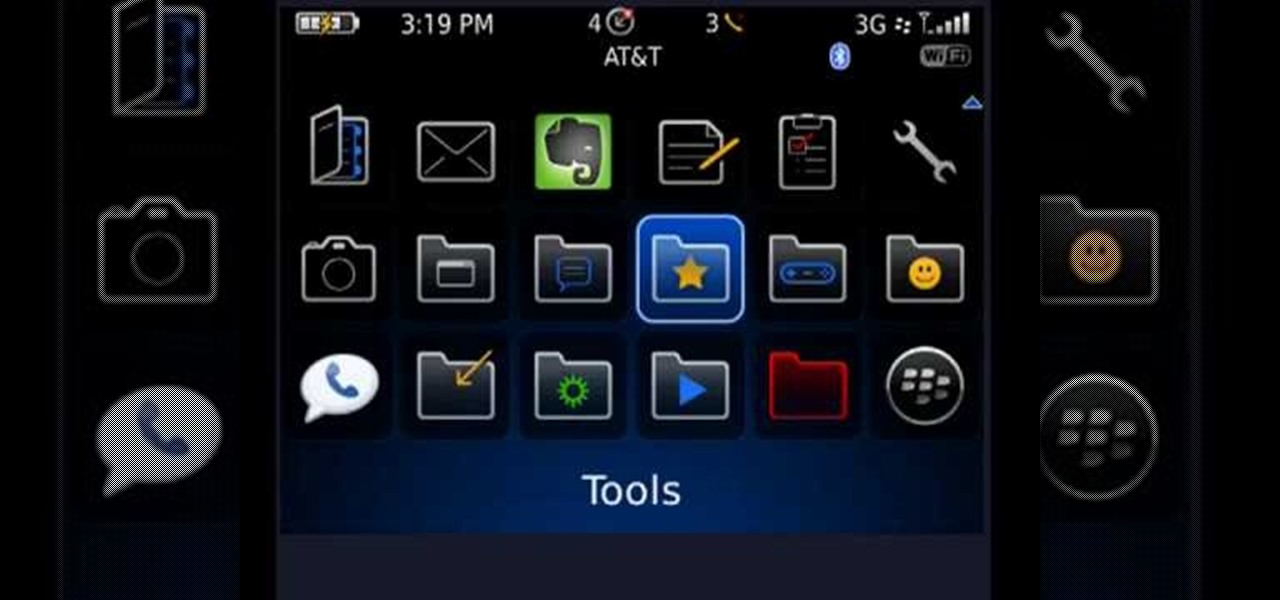
In this how-to video, you will learn how to shut down your Blackberry device quickly and easily. If you have uninstalled or installed a new program, this may be useful for you. You will have to find the power off tool in the display of your Blackberry. You can place this option in the tools section. Once you highlight it and press the track ball, it will begin the process of turning the device off. This allows you to shutdown all processes on the device and completely turn off. This video sho...

In this how-to video, you will learn how to free up disk space on your Windows Vista computer. First, go to my computer and right click the drive that you want to free up space on. Next, click on properties. Click disk cleanup on the new window. Select which files you want to delete by checking the appropriate boxes. Once this is done, click okay. You can also select clean up in the other tab to free even more space. The first section will allow you to remove programs you do not need, while t...

In this Software video tutorial you will learn how to mount an image using Daemon Tools Lite. This software takes many different types files and puts them on a virtual DVD drive. Go to www.daemon-tools.cc and download the Daemon Tools Lite program. You then install it. After that double click on the icon on your desktop and it will appear on the bottom right hand corner of the screen. It will say Daemon Tools and the version. Right click > virtual Cd/DVD ROM. To mount an image, click on ‘mo...