Since its inception in 2007, the Pwn2Own computer hacking contest has been challenging the vulnerability of mobile phones and web-related software. In 2010, the fruit of two full days of hacking came down to the exploitation of the following web browsers: Safari 4 on Mac OS X, Internet Explorer 8 on Windows 7, and Firefox 3.6 on Windows 7. The winners walked away with the successfully hacked computer, plus a cash prize, but they left one Godly browser intact: Google Chrome. Even the savviest ...

Life has always been complex and challenging. The challenges today are just different than what they were in the past. Nowadays instead of hunting and scavaging for food and living in the elements we’re bombarded with suggestions and demands from our highly sophisticated societies. How is it possible to find harmony amidst what are often contradictory messages?!

West LA Seido Karate-do embeds its personal protection program into its on-going classes. Private instruction in this aspect of Seido can also be arranged with Kyoshi on an individual basis.
Cheating ruins everything. Cheating makes game play unfair for others who may be truly competitive and strategic. Cheating makes others disrespect and un-friend you. There can be unforeseen consequences, like getting viruses, trojans or your account hacked from downloading a cheat/bot program. And you will get banned from the game for violating terms of service.

In order to complete this 3D spinning cube using OpenGL and GLUT for C++ programming, you need to know the basics of C++ programming. This video lesson covers everything you should already know. Check out the other videos to get the full gist:

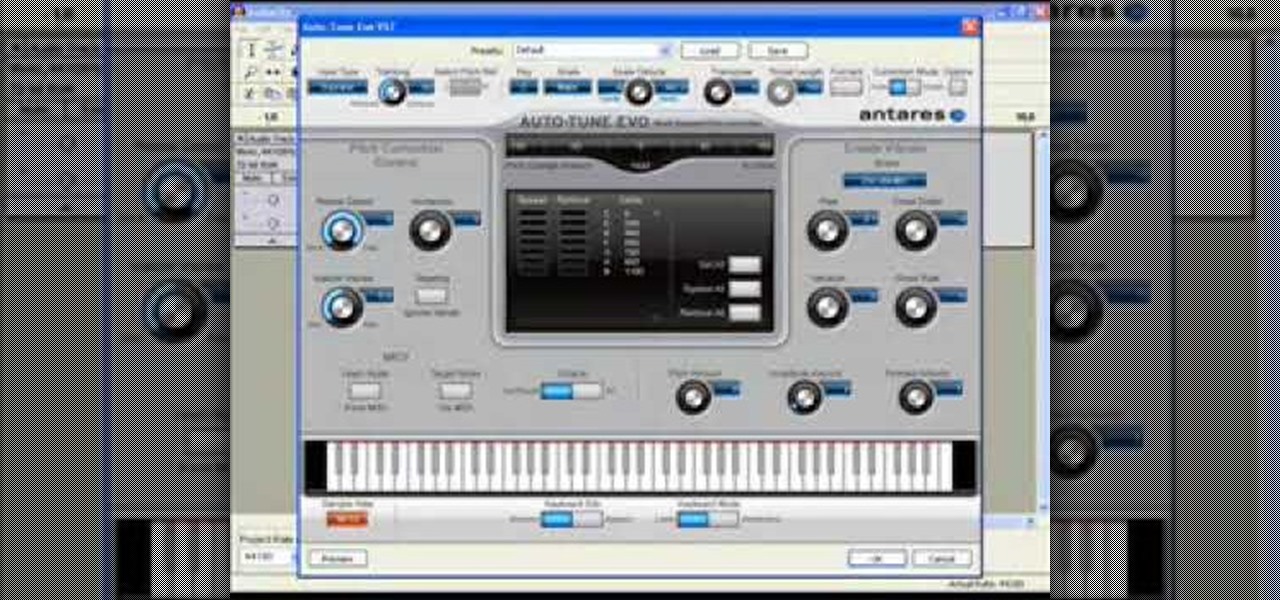
In this video tutorial, learn how to get auto-tune into Audacity. This video shows you how to receive a ten day free trial. The success rate of this video is questionable, so if you have trouble: Go into edit/preferences/effects, and make sure all three VST settings are checked. Also make sure that "rescan" is checked. Restart Audacity, and it should work. This video is demonstrated on a PC, and should work for Vista users.

Watch this video from This Old House to learn how to choose exterior paint schemes. Steps:

In the coming years, artificial intelligence (AI) will revolutionize every facet of technology and business. AI researchers are in high demand. Salaries in this field are regularly in the hundreds of thousands of dollars.

Before the internet, acquiring enough data to analyze was challenging. Now we have the opposite problem: a deluge of data makes trying to sort through it nearly impossible. That's where data science comes in.

Since its release back in 1988, Microsoft Office has been the top client and server software suite for businesses around the world. Office's domination is thanks to both Microsoft's extraordinary foresight and their continual updates and innovations to ensure that companies always get what they need.

There is so much information in the world that trying to make sense of it all can be daunting. That's where data analytics comes in. By learning how to inspect and model data, you can take large data sets and transform them into highly valuable information that can take any business further.

Being stuck inside for the near future is less than ideal, but at least you have the world of eLearning to sharpen your skills while you kick back on your couch. Case in point, The 2020 Premium Learn To Code Certification Bundle has all the training you need to start coding like a pro right at home, and it'll only cost you $39 today.

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

While Magic Leap World gets its share of fun apps for playing with Porgs, watching TV, and exploring the ocean's depths, developers are making a strong business case for the Magic Leap One as well.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

In an effort to raise awareness regarding the impact of emissions on the environment, Snap has partnered with the United Nations Environment Programme to use augmented reality to show how much ocean levels will rise over the next 80 years.

Thanks to leaks that let us try out the latest Android Pie beta on the Galaxy S9, we already have a good idea of what the update has in store for Samsung's flagships moving forward. As we've come to expect, Android 9.0 brings a slew of notable updates, such as the addition of a system-wide dark theme and an all-new TouchWiz replacement called "One UI."

This week, saw two companies leaning on AR to prop up their financial futures. On one hand, Apple made quite a bit of AR-related news ahead of its quarterly earnings report next week. On the other hand, Vuzix launched a pre-order program for its Blade smartglasses and closed the largest financing deal in the company's history to fuel its ongoing headset production.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

A top executive from Baidu's telematics division believes the company will become the word leader in driverless by 2020, according to a report in today's South China Morning Post.

Cruise Automation follows Waymo's and Uber's lead with its debut of a beta version of an app-based driverless ride-hailing service for its employees in San Francisco, ahead of a possible launch of a full-fledged commercial offering within four years.

Four million Americans misused prescription opioid painkillers in 2014. Those who do are 40 times more likely to inject heroin or other drugs than other people. Now, the Centers for Disease Control and Prevention (CDC) are blaming that misuse for a 12-fold increase in endocarditis, an infection of the heart valves.

The Chinese government's tight restrictions on gathering data by foreign firms for 3D mapping, the lifeblood of machine-taught driverless systems, could at least slow down access to the market by Waymo, Tesla, General Motors (GM), Ford, and other players hoping to make inroads there.

Ok, I have to admit, I drop my phone around 2–4 times a week. I'm horrible at protecting it and I've gone through my fair share of cracked phones. Most of the time, once the phone is cracked it's just easier to get an entirely new phone, rather than have to fight your phone provider for a fix.

Uber and Waymo's lawsuit is starting to pan out. Following a ruling on Monday, May 15, Judge Alsup, who called Waymo's patent infringement claims "meritless," ordered Uber to perform a series of actions and duties for Waymo. Without further ado, here's what Uber must do to begin to put this lawsuit behind them (well, maybe):

Uber's year is going from bad to worse, and they may be subject to a potential criminal probe in the ongoing Waymo legal battle.

User interfaces for computers have evolved over the years, from the introduction of the keyboard and mouse on the personal computer, to touchscreens on mobile devices, to natural voice recognition. However, the same cannot be said for robots or drones—until now.

Crayon, a free 3D drawing application by the mysteriously named arkalian, showed up in the Windows Store recently, so I gave it a try like I do all new apps for Windows Holographic. Truthfully, I loaded it up not expecting much, but wow, was I wrong. It's a simple idea, but it's executed well enough to make it a truly great experience on the HoloLens.

Welcome back everyone! In the last training session we covered basic file input and output. We're going to leave this topic for a bit and start on something that will change the way we write scripts, classes.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

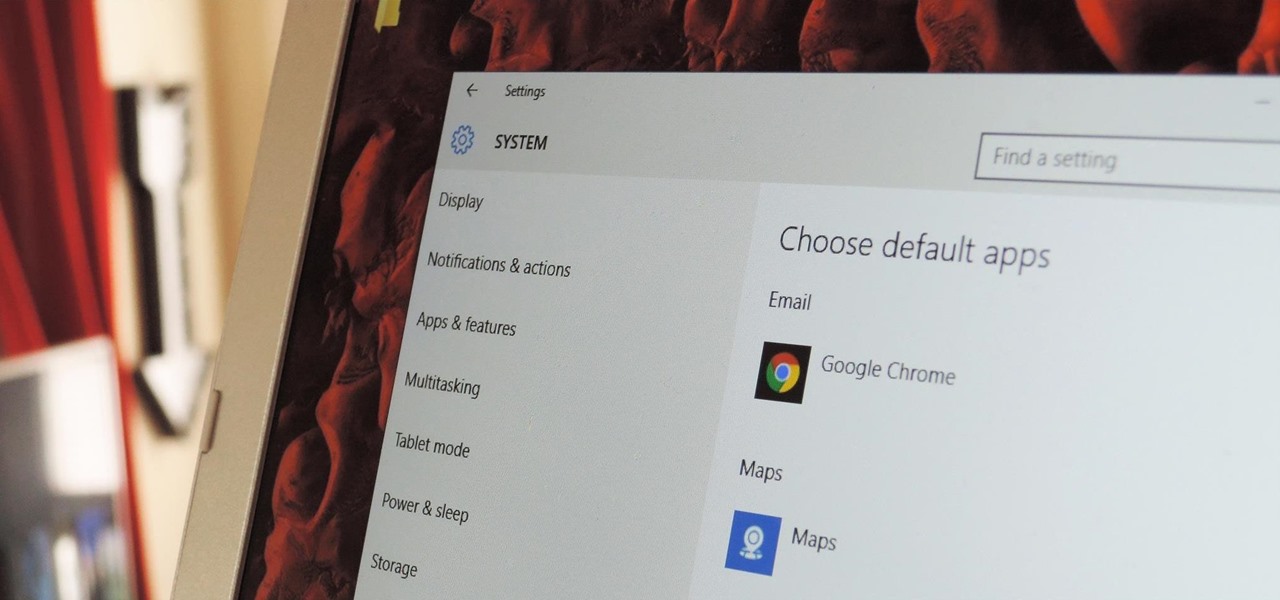
The first time you launch any type of file, Windows 10 will usually prompt you to select an app to open it with. Occasionally, though, this "Open with..." screen doesn't show up, and instead Windows will use a pre-installed system app to launch the file without ever giving you a choice in the matter.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

Hello, fellow grey hat hackers and aspiring coders. I'm back again with another python tutorial. Just that this one is gonna be a lot cooler ;-). We gonna make an encryption program, that well you know encrypts all the files on your pendrive or hdd or whatever you want....Also lots of thanks to DrapsTV. They have helped me a lot with Python and making awesome programs. The video is here:

If you've switched ROMs before or flashed quick mods on your Android device, you've probably used TWRP or another custom recovery to install them. But another great purpose for flashing through a recovery is to install your own custom .zip file filled with everything a fresh ROM needs—namely, all your apps.
Hello, Hackers/Viewers! My name is nullf0x, and I have 4 years of experience as a hacker. You might see everyday that one of your friends or acquaintances get a new virus in their computer. You might think, How cool would it be if I made a virus? or How cool would I be if i could remove viruses from others computers for money or free?

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Sideloading apps on Android is incredibly easy—you just have to enable "Unknown sources" in your device's Security settings, then you're free to run an APK installer file to get the app installed.