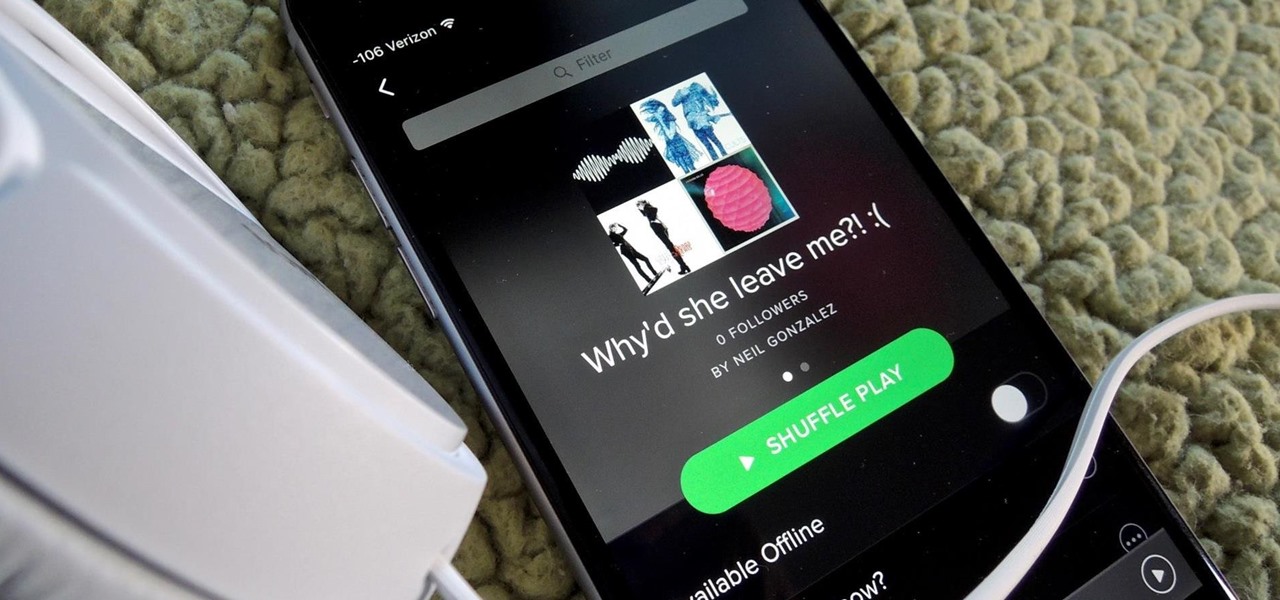
How To: Recover Deleted Spotify Playlists
Playlists are more than just a list of songs that you enjoy listening to while in traffic or hosting a party—they're stories that illustrate who you are or your frame of mind at a certain point in your life.


Playlists are more than just a list of songs that you enjoy listening to while in traffic or hosting a party—they're stories that illustrate who you are or your frame of mind at a certain point in your life.
Jem and the Holograms was one of the hottest cartoon series on TV back in the mid-'80s (though only for a brief time), and was recently given the big screen treatment with the feature film of the same name. While the film bombed at the box office (with good reason), your Halloween costume doesn't have to.

If you don't have the time or patience to build a complete Ant-Man suit from scratch, there's another way to make a Ant-Man costume for Halloween. If you're more skilled with brushes and makeup rather than drills and cardboard, this is the Halloween DIY for you—especially if you're a fan of the Marvel universe.

For a number of years, I have had a vortex cannon on the top of my list of projects to attempt. Creating a sturdy cone for the barrel has always been a hurdle in the design, one I finally found a solution for in this video.

Straight out of the box, the Nexus 5 is an awesome device, but even it can be faster with better battery life. Luckily, one of the things that makes it so awesome is that there are tons of developers creating mods for it, since it runs stock Android by default. When it comes to gaining speed and better battery life, flashing a custom kernel is the way to go.

A good prank requires decent effort, creativity, and impeccable timing. If you're in the office, there are plenty of hilarious pranks to play on coworkers, and for your family and friends, there's everything from toothpaste-filled Oreos, to solid milk, to impossible-to-solve Rubik's Cubes and smartphone-friendly pranks.

Ever wonder what your brain looks like while you're singing? No? Neither had I, but as this music video for the song "Better Man Than He" by SiVU (aka James Page) will show you, the answer is "pretty cool."

The International Space Station is a habitable man-made satellite currently in orbit around the Earth. Launched in 1998, the ISS is used mainly as a microgravity and space environment research laboratory where astronauts perform experiments in large variety of fields, including biology and physics. In order to be hospitable for crew members and scientists, the ISS needs energy. To do this, the station uses its solar panels to capture rays of sun and power the station up. In order to garner th...

At one time or another, we've all enjoyed the visualizations that came stock in Windows Media Player. I remember spending hours listening to my favorite album, putting the graphic equalizer on full screen, and getting lost in the flurry of colors that would dance across the screen. Well, now thanks to the imaginative mind of Instructables user yardleydobon, you can now recreate this rainbow-colored music visualizer right on top of your freaking head—with these trippy EL wire headphones, which...

Hello! This post will be about the special care your dwarf rabbit needs during hot weather. There are many ways to keep your pet happy. Step 1: Choose the Environment

November 29th marks the day of Nissan's triumph, not only as an automaker, but as an eco-friendly automaker. The new Nissan LEAF has won the 2011 European Car of the Year award, the first all-electric vehicle to be chosen for the award.
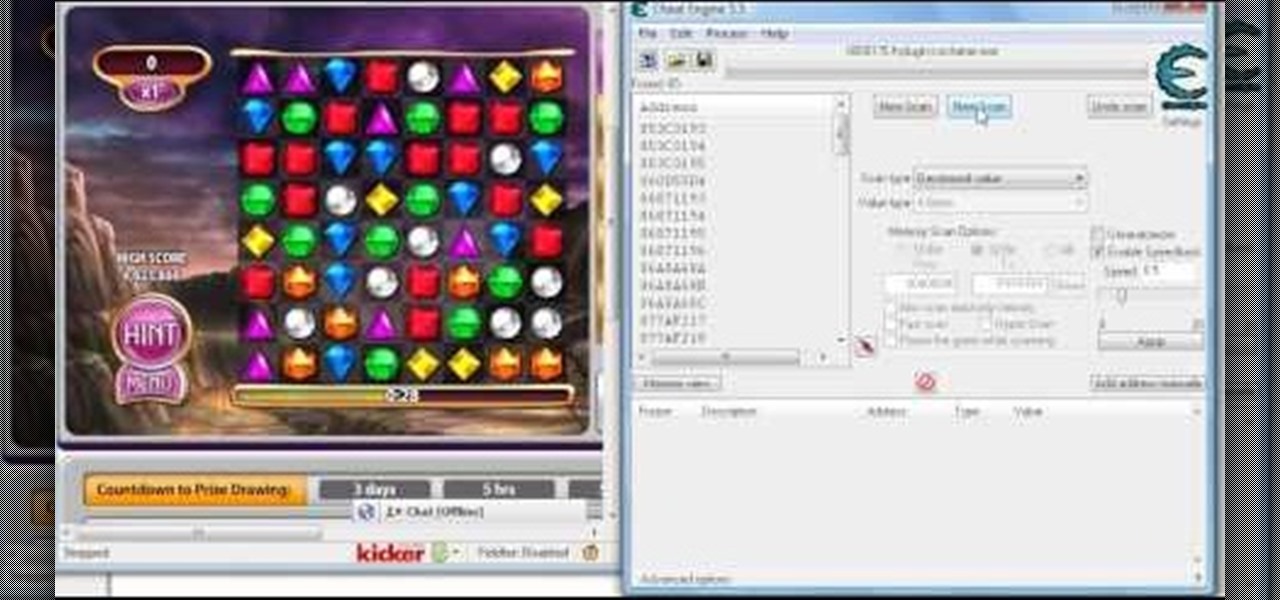
Don't let Bejeweled Blitz get the best of you. Show it who's boss and get the highest score possible. Of course, you'll need Cheat Engine to overpower the game, so make sure you have Cheat Engine 5.5 or higher and check out this video for the hacking Bejeweled Blitz (10/09/10).

Tired of squinting over your laptop? There are several ways to turn a big-screen TV into your new computer monitor and enjoy video games, web content, and photos like never before.

Does your kitchen smell like a landfill? Try these simple steps to clean out the culprit. This video will show you how to safely clean a garbage disposal.

Learn how to crash a wedding. If you have a free Saturday, we have a way for you to score free food, free cocktails, free dancing—and maybe even a hook-up.

Hotels are anonymous and while this is a great thing, you should also be careful about the nameless folks who've used your room before you. Follow this tutorial to make the most of your hotel and ensure a great vacation experience.

If your not sure how to steam your media files to your Playstation3 this video will explain three different ways to achieve just this. Your options will include using a thumb drive, a personal web server or get the appropriate software.
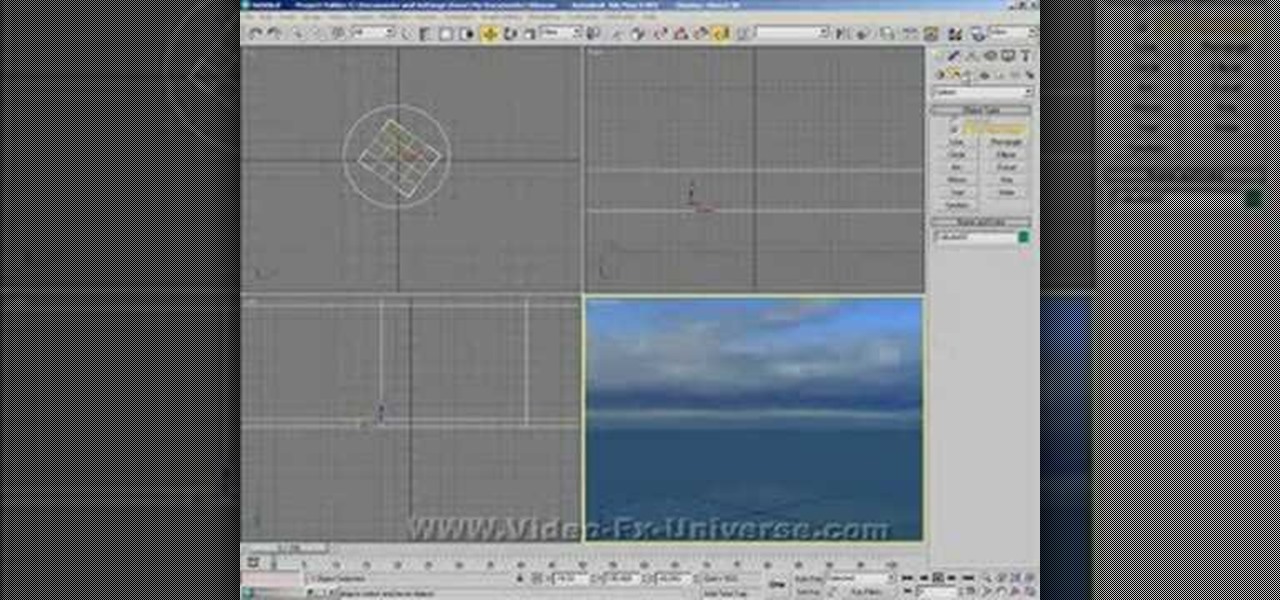
how to create an Ocean in 3DS Max

Watch this video tutorial to learn how to calculate your carbon footprint. A carbon footprint is an equation that estimates just how much you, personally, are contributing to global warming—and all you have to do is plug some info into an online calculator. Figuring out how to make your footprint smaller, of course, is another matter.

Just got the new Android-powered Samsung Galaxy Tab? A little confused by all of those cables that came with it? No problem. This video will show you how to connect the AC charger and the PC data cable that came with your Galaxy Tab. But really, it's one of the easiest things you can do on this new mobile device.

Have a great movie stored on your iPod, and you really want to watch it on your TV? This tutorial shows you how! All you need is an RCA cable. Plug the red cable into the video slot and the yellow and white cables into the audio slots, and you'll be able to watch anything off your iPod on a televison set!

Learn how to setup the Verizon FiOS Router for multiplayer gaming. Most games and gaming consoles only require that UPnP (Universal Plug-n-Play) be turned on. The MI424WR Verizon FiOS Router that is manufactured by Actiontec ships with UPnP ON, as the default.

Checking the waveform on a car plug-in inverter, like the type you would use to power a laptop computer in a car. I used my NLS MS-215 Miniscope to view the waveform. As you can see it is much more like a squarewave than a sinewave, like a staircase waveform.

Every good illustrator knows the advantage of using a Wacom tablet with Adobe Illustrator. When you plug in a Wacom tablet it doesn't automatically set your tools to be pressure sensitive. Terry White will show you how to set your brushes to really take advantage of your new tablet.
I have owned quite the plethora of electronics in my life. A commonality between most of these devices' screens is frozen or dead pixels. This is probably the most annoying thing about buying new hardware—your LCD, or worse, LED display has one or more pixels that continues to stay lit. Most of the time, this will appear in the form of a brightly colored pixel that never changes, or a pixel that never displays the right color. Once you notice it's there, you just can't stop staring at it. It ...
The Na'vi don't have eyebrows. While you could just paint your makeup on over your brows if you don't have prosthetic appliances to cover them, a neat trick is to take a giant glue stick (or the spirit gum) and go over your eyebrows with it, rubbing the stick in the opposite direction of eyebrow growth. Let it dry and then do it one or two more times (depending on how thick your brows are). With your brows flat against your skin with a layer of "glue skin" over them, you can have a nice, flat...

Links of Love is showing you how to make origami heart shaped cuff-links. Start with a 20.5 cm square of paper. If you want to make a cuff link you can wear you should use a square the size of 4 to 5 cm. Fold a good crease and then unfold. Fold two corners in toward the middle and then unfold. Fold one side in toward the middle crease. Only crease up to the crease of the corner fold. Unfold and fold the side into the new crease just made. The creases are guidelines that will be used later on ...

When you first begin to drawing dogs, it can be difficult to know where to start. Usually, there are tricks that can get you started with ease, and the same is true in regards to drawing dogs. You don't have to be an expert artist to learn how to draw a dog; it's as simple as beginning with a 'cheat', or a few specific lines, and building a style from there. To draw a dog, you should begin by drawing the number 'six', followed by three lines, fairly close together. This will create the dog's ...

Working from home is going to be a reality for more people than ever. With Twitter CEO Jack Dorsey announcing that his employees will be working remotely for an extended period of time (and even permanently, in some cases), the workforce is rapidly changing. More companies are certain to follow suit.

While conducting an OSINT investigation, it's important to be able to pull in information based on any clue you uncover. In particular, license plate information can turn up everywhere, from photos to live data to on your own street. You could use that data to find the VIN, see if a Tinder date has hit anyone, find out who's blocking your driveway, and so on. Skiptracer can help get the ball rolling.

In a departure from Apple's newer iPhone models with Face ID technology, the 2020 iPhone SE goes back to the old days where the Home button ruled, and Touch ID was the biometrics method. But if you've never owned an older iPhone with a Home button, something as simple as shutting down and restarting the iPhone SE could elude you.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

Google recently released a new mesh router known as Nest Wifi. The updated and rebranded Google Wifi brought many improvements, such as faster processing power and an increased level of wireless security called WPA3. But while it's not enabled by default, you can still get the new WPA3 security on your original Google Wifi.

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

When flashing files through TWRP, ADB, or Fastboot, there's a slight chance for things to go wrong. Whether it's user error related or something else entirely, it's always good to have a backup plan. In most cases, you'll be dealing with a semi-brick or soft-brick, which can usually be solved by wiping the data of the device using TWRP. However, it can be more severe than that in some cases.
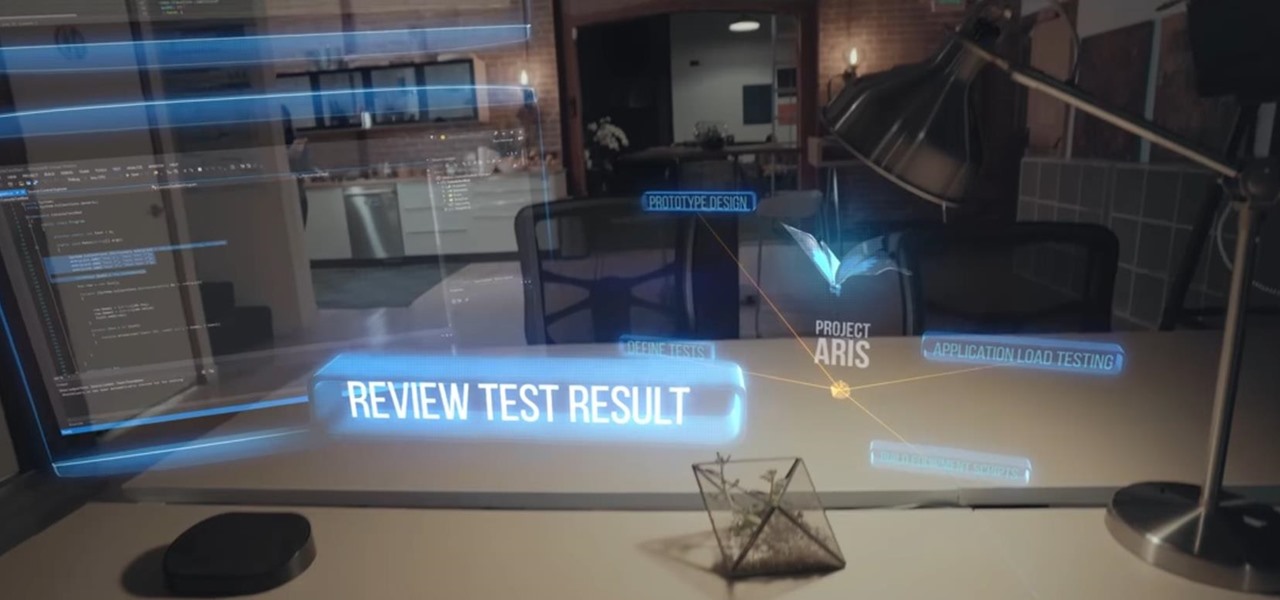
So after being teased last Christmas with an email promising that the Meta 2 was shipping, nearly a year later, we finally have one of the units that we ordered. Without a moment's hesitation, I tore the package open, set the device up, and started working with it.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

Brace yourselves, because Siri has a trick up its sleeve that iPhone users have wanted for some time. Yep, that's right, I'm talking about the ability to use Siri without having to talk out loud for the whole world to hear. It's great for privacy, Siri-ing on the down-low when you're not supposed to, or ... you know ... if you have a speech disorder.

We've heard the rumors for months, but it's finally official: The iPhone 7 will not include a traditional 3.5 mm headphone jack. Instead, you'll need to hook your favorite headphones up with a Lightning adapter (or use ones with a Lightning connector built-in) and connect to your phone using the same port that your charger occupies.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.