
How To: Fix the E74 error on your Xbox 360
This video demonstrates a method of fixing the E 74 Xbox 360 error. In order to do this, you first must disassemble your XBox, which will void your warranty, so this is at your own risk.


This video demonstrates a method of fixing the E 74 Xbox 360 error. In order to do this, you first must disassemble your XBox, which will void your warranty, so this is at your own risk.

Bud Brown explains how to know when to use a voltage adapter in the Philippines. The United States and the Philippines have different voltage systems. In the United States 110 volts are used, and in the Philippines 220 volts are used. If you plug something from one system into the other system, it will not work correctly and may ruin your equipment. Consider that computers and phone chargers are equipped to handle both systems. Check the labels on your electrical equipment to determine if it ...

Ballinguy556 shows you how to put iPod video on an XBox 360. First, you need to take your USB wire that goes with your iPod. Plug the USB wire into the front USB port of you XBox Rest your XBox on top of your XBox 360. Your iPod is now on top and therefore on your 360. You can also place it on your 360 controller by placing it on your controller. That is how you get your iPod on your 360.
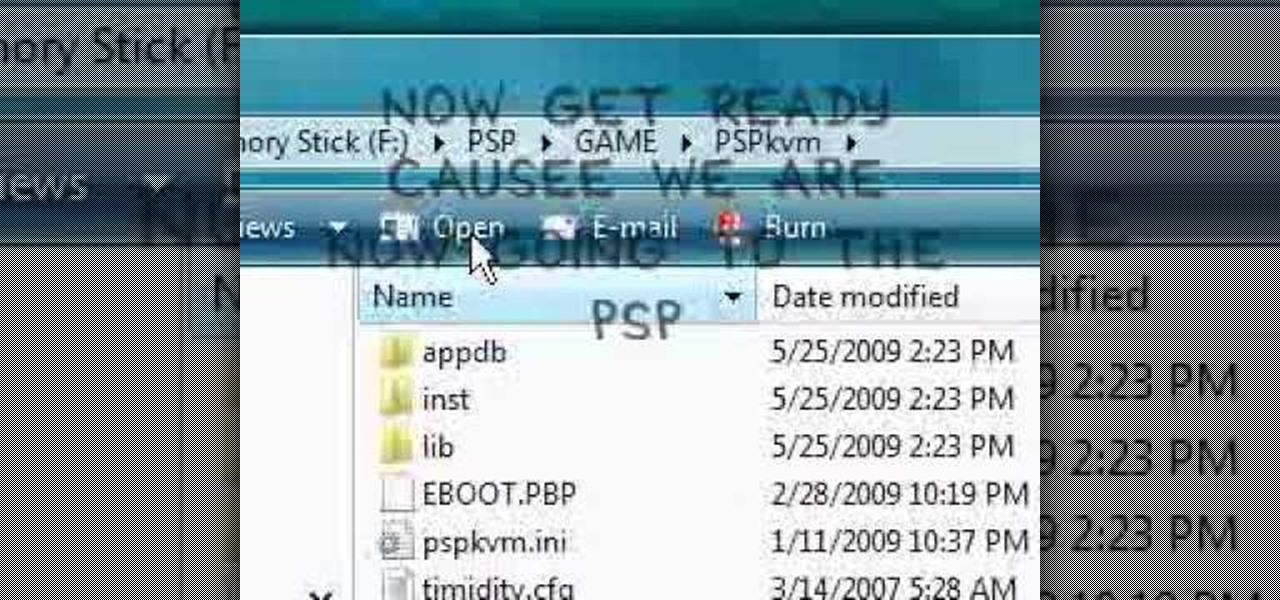
In this video the instructor shows how to play java games on your PSP. To play java games on your PSP you will have to download and install the PSPkvm. Now plug in your PSP and go to my computer and put the downloaded folder in the PSP/Game folder. Now download any free java game from the Internet. Now open your PSP and choose the game by looking for the PSPKVM. Now open that file and it prompts to install it. Install it using install from memory stick option. Now open that application and ch...

Gymnastics are impressive and exciting to watch. You’ll need strength, agility, flexibility and some definite practice to get to the point where you’re ready to try a front handspring but all the work will be worth it when you stick your landing.

You know your going to have to sleep outside and you don’t know how to stave off the chill of the night. With the right equipment, some layering techniques and a full belly you be sure to get a good nights sleep even if it’s cold out.

In this video Lowe's shows you how to make custom lampshades out of a plain old lampshade so that it looks great for the kids room or classy for any other room in the house. Decorate an old or plain lampshade using stencils, paint, decals, or in any way you can imagine. Then attach a wire plug and the light holder and hang the lampshade using an appropriate chain, as shown in the video. All accessories required for this job are available from any hardware store.

Learn how to wrap earbuds. Give your Apple iPod earbuds a little TLC by learning how to store them correctly.

This is a video showing the drilling of live rock from a saltwater reef tank. The 1/2" holes are used for mounting pegs made from acrylic rods or other types of pegs or frag plugs. The live coral are attached to the end of the peg and can easily be positioned in the tank. This process also facilitates moving the coral to another location at a later time, they can be removed from the holes somewhat easily. It also prevents coral from falling as once its pegged well, its pretty much going to st...
Print what you want, how you want. While browsing, choose the content you want then edit and print exactly what you see on your screen..

This video is a demonstration of tying the EZ Shape Sparkle Body Sand Eel Fly. EZ Shape Sparkle Body can be used to make a variety of baitfish, shrimp and crab flies. This sand eel fly is great for fly fishing for striped bass, bluefish, weakfish (sea trout), redfish/drum, fluke/flounder, tuna and many other saltwater flyfishing game fish. It can also be used a as teaser ahead of a plug, jig or other lure for casting.

Compared to Apple's products like the iPhone and iPad, Android phones and tablets are very flexible devices. For instance, you can set a new home screen, replace the lock screen, or even beam files using NFC — but that's just the software side of things, and the flexibility goes well beyond that.

In many urban areas, GPS doesn't work well. Buildings reflect GPS signals on themselves to create a confusing mess for phones to sort out. As a result, most modern devices determine their location using a blend of techniques, including nearby Wi-Fi networks. By using SkyLift to create fake networks known to be in other areas, we can manipulate where a device thinks it is with an ESP8266 microcontroller.
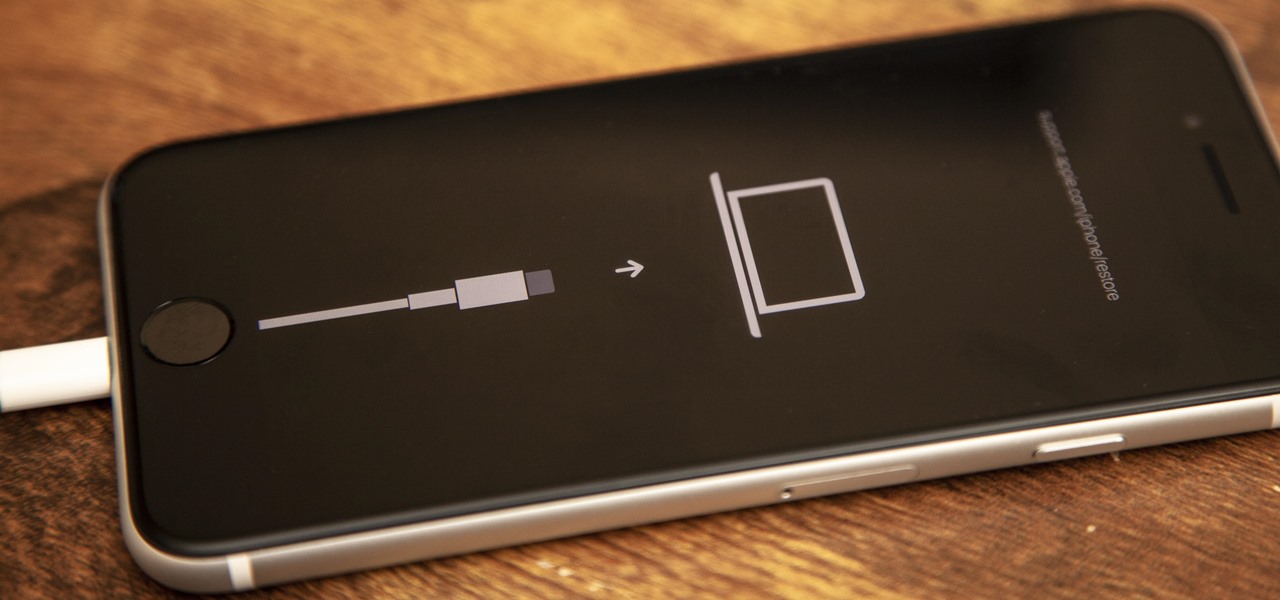
If your new 2020 iPhone SE is frozen, unresponsive, or won't load the system, and a standard power down and up procedure didn't work, there are few more things you can try. Force-restarting the device may do the trick, recovery mode is a last-ditch option, and DFU mode is your fail-safe.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

The holidays are here. From the week of Thanksgiving until the end of the year, retailers will be offering massive discounts on your favorite items. So if you're looking for smartphone accessories, this is the time to buy. From Walmart to Best Buy, there are deals everywhere on a host of items.

Many people don't realize much better audio can sound on their phones. While it's solid to begin with, Samsung has included several options in the Galaxy Note 10+ that will upgrade your listening experience to profound status.

My autistic son loves music. One afternoon, when he was nine, I downloaded GarageBand to his iPhone to help with the boredom of a long wait at a doctor's office. Instead of pacing or escalating into a meltdown, he spent the entire hour and a half practicing, learning, and composing. When we finally left that day, the rest of us exhausted and irritated, he shared his first composition with a big smile.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a simple cable. If you don't have a power source, you can also power your Linux distro over the cable at the same time.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

When it comes to busted smartphones, liquid damage ranks right up there with shattered screens as one of the most common issues owners have to deal with—as well as the most embarrassing. Thankfully, though, with the rise of waterproof phones such as the Samsung Galaxy S7 and even the iPhone 7, this is becoming less and less of a worry. But not everyone has a waterproof device.

We spend over 30 percent of our lifetimes sleeping—yet it never seems like enough, does it? Distractions ranging from work issues to personal relationships keep our minds racing well after they should be shutting down for the night, and the onset of smartphones has only added to this problem with the instant information and easy entertainment that they offer.

The video shows you in simple easy steps how to draw Snoopy from Charlie Brown. It starts with a single line drawing the ear and the head then adding the neck, nose and eye, adding shading. Then a simple triangular shape for the body, adding the hands. Simple circles are used for the feet, connecting them to the basic triangle shape and adding a tail. Removing the triangle shape then gives the body flow and then adding the collar and feet finally gives you the Snoopy character from Charlie Br...

The video describes the procedure of fixing the wiring harness on a Ninja 250R motorcycle. The person who owns the bike presents this video. He says that he got his bike back after getting the wire harness newly fitted. His signal blinker lights were not working. The next morning he wanted to make sure that it was fine. He plugged the wire and tried to switch it on, but it did not work. He also found that the horn was also not working. It was actually not working for a long time now. Then, he...

During the darkness of the winter months some bright and spirited holiday decorations can really add holiday cheer to a home. This Christmas, try making this festive tree and light table piece because you can never have too many decorations.

Are you having trouble with your animal drawings? Doodlekat1 shows us how to draw a cute cartoon tiger easily! You will need: blank piece of paper marker or pencil. For the head: Draw a big semi-circle and a small circle in the middle. Connect them using little curves then add the ears. For the nose: Draw a triangle on the top of the small circle then add the mouth, three dots and some whiskers. Draw two big shaded eyes. Draw stripes of varying sizes at the top and the sides of the head. Add ...

This instructional costume making video shows how to create a fur suit mask head base with foam. Just follow these three simple steps for your fur suit mask: make the base of the mask, make and attach the ears to the base, and make and attach the muzzle and jaw. Watch this fur suit costume making tutorial and you'll soon be ready to start roleplaying.

Carve the face of a wax sculpture with the professional artist in this free sculpting video, covering how to sculpt eyes, lips, ears, and the nose.

Learn how to sculpt a mask using 'slab construction' techniques. I use mixed studio clay from scrap. A small segment about ear placement and animal perception are included in the video.

Ever wanted to know what sea creatures sound like? This video will allow you to hear fish talk and whales sing by altering a kids toy called a spy ear!

Young boy shows us how to play the intro to Piano Man. Demonstrate step by step and note by note. Notation not available, but kid recounts seemingly by memory or ear.

Home cooks know firsthand what it takes to make delicious and amazing food for friends and family. One of the most effective ingredients to making foods as delicious as possible is herbs.
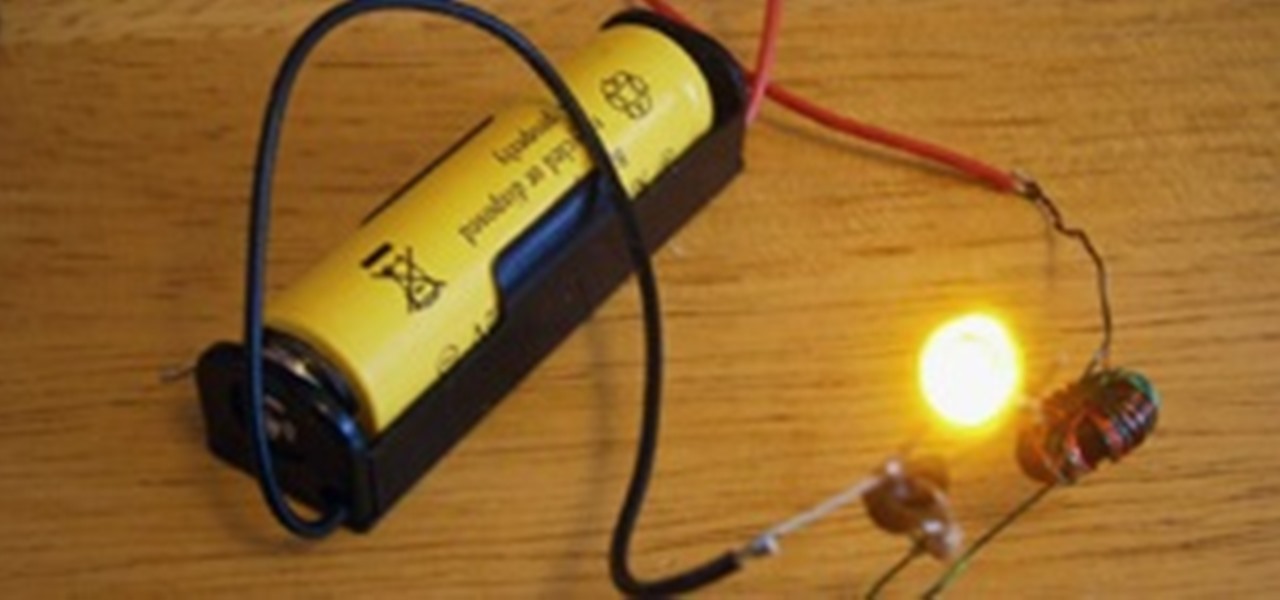
Just about every household gadget we own runs on 1.5 volt batteries of one size or another. Wouldn't it be great if you could reuse all of those dead AA, AAA, and D batteries after they've passed on? It turns out you can make a simple circuit called a "Joule Thief" to reanimate the undead flesh of your deceased batteries and create a zombie battery.

This video teaches us the method to train a horse to lower its head. You will need a horse with lead rope tied to it. Start the training by holding the lead rope. Apply pressure on the rope in the downward direction. Hold the rope in that position by resting one of your arm on it. Keep holding the rope until the horse comes down a little. Release the pressure on the rope when the horse comes down. Apply the pressure again when the horse goes up. You can also apply the pressure at the top of t...