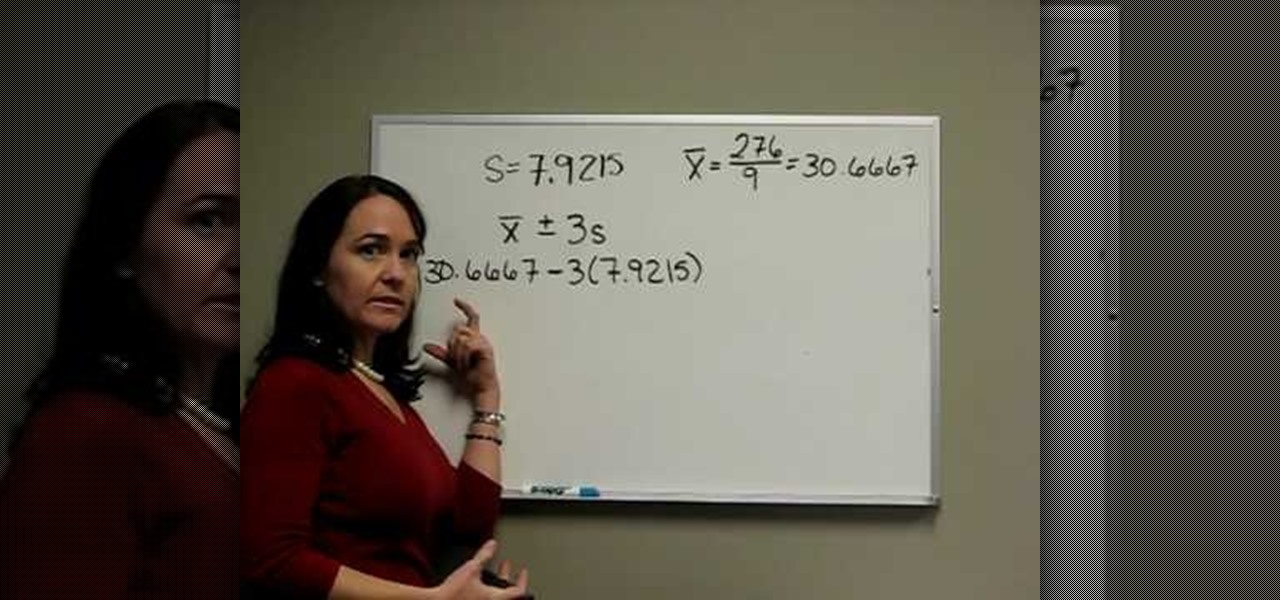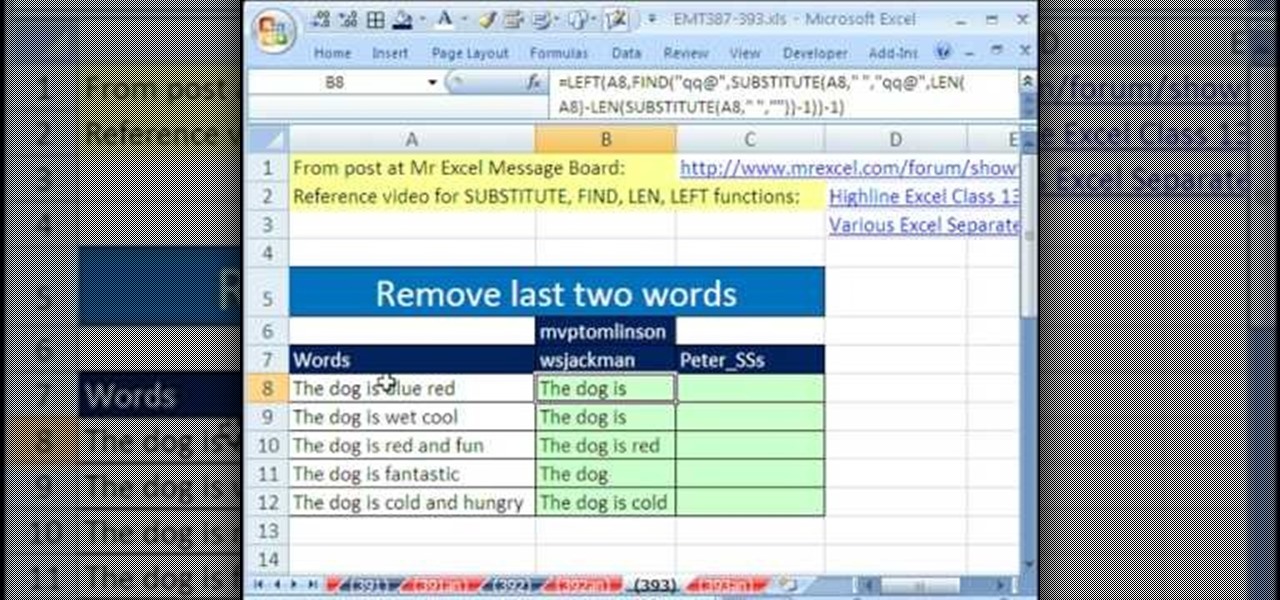
New to Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. With this video tutorial from ExcelIsFun, the 393rd installment in their series of digital spreadsheet video tutorials, you'll learn how to remove the last two words from column of data with the LEN, SUBSTITUTE, FIND, REPT, RIGHT and TRIM functions.

Before you sell your Blackberry on eBay you may want to erase all personal data on the device. This video will show you exactly how to reset your Blackberry and erase all personal information.

A lag switch allows you to cheat in online games or on XBOX LIVE by disabling the flow of data to your console or PC. We will show you how to build one.
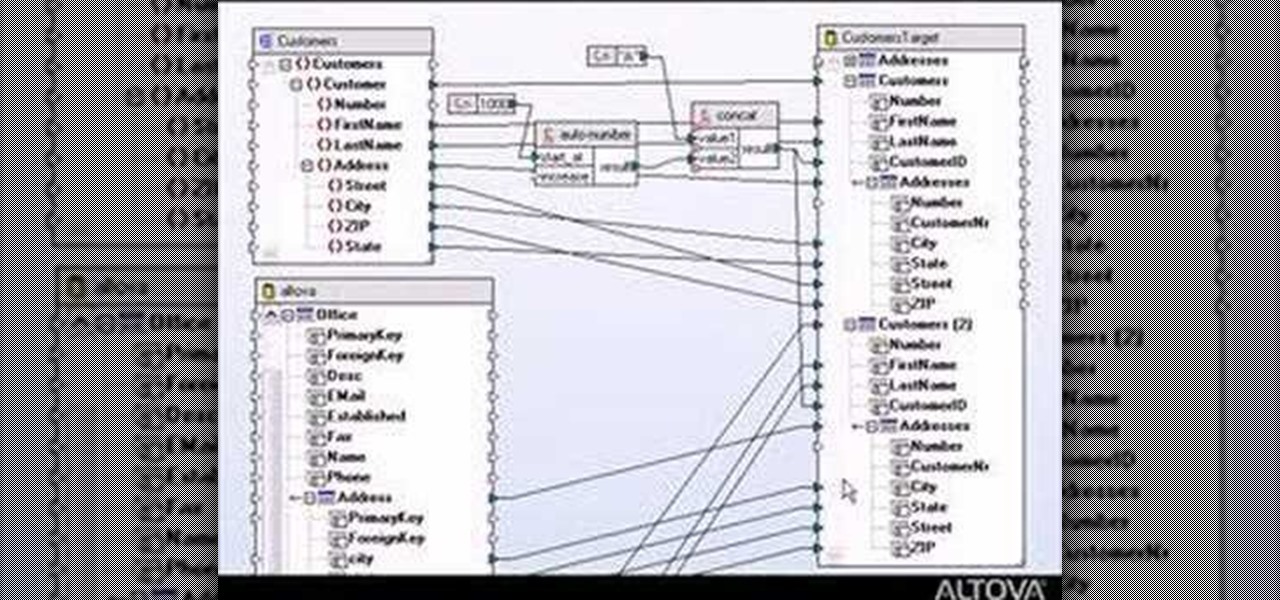
Designing a data mapping project in MapForce? The output functions in MapForce let you preview textual or XML output, save it to disk, or look at SQL statements for database output before committing them to the database server. Learn how in this tutorial.
While you cannot directly open a Microsoft Access database file in OpenOffice Base, it is possible to connect Base to an Access database, and manipulate the data contained within it.
Databases allow you to store data in a systematic and organized format, making it easy for you to search, sort and edit.

To use your iPod to move your music, you must sync your library to your iPod as data into a folder.

In this free video math tutorial, we learn how to use the Z-Score formula to find a data point (Xi) in statistics. With mathematics, as with anything else, not everyone progresses at the same rate. Stats is no exception. Happily, in the age of Internet video tutorials, this isn't a problem. Those who progress quickly can go beyond what's being taught them and those who are struggling likewise have all the time in the world to catch up. Whether you need help finishing your homework or studying...

A rough definition of standard deviation is that it is a measure of expressing the observed variations about the average in statistical data i.e. by how much do the observed values vary from the mean. This video continues from the previous solved example and demonstrates the mathematical interpretation of the standard deviation that was calculated. We begin with stating the mean and standard deviation values and then calculating the upper and lower bounds of the data based on the standard dev...

Go to Cydia and add a new source http://Cydia.xselize.com. Now search there for supreme preferences and install it.

Your Android phone is a computer not unlike a laptop or desktop PC and it shares the same vulnerabilities. This clip presents a quick overview of how to safeguard against viruses and data loss. With the Lookout app, it's easy! So easy, in fact, that this video guide can present a complete overview of the process in about two minutes. For more information, including step-by-step instructions on how to adjust your own Facebook tagging settings, take a look.

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 97th installment in their series of digital spreadsheet magic tricks, you'll learn how to use a data form in both Excel 2003 and 2007 as well as how to add a button to Excel's Quick Access toolbar.

This video from CNET Insider Secrets tells you how to recover deleted files from a data drive. If a disk is still readable by the computer, files may be recovered. Files may be recovered using the PhotoRec program, PC Inspector or other programs that may be available. An example is shown where mp3 files are deleted from a flash drive. We are then shown how files are recovered using the PhotoRec program, including how to select the correct file system. The mp3 files are recovered along with va...

Here, you'll be shown how to revert your Windows Vista computer back to its factory settings, if you get stuck with a bad virus or anything else like that. Make sure to back up all of your important data before you decide to go back to the original factory settings, as you don't want to lose that precious data. After a quick backup, we'll run through the options from start to finish. We will run through a few restarts of the system, and then show you the easy path to getting your system back ...

Do you want to know how to sync an iPod with the XBox 360? You must have an iPod and a XBox 360. Connect your iPod with your XBox with the USB cable. Transfer the files from the iPod to the XBox XBox helps play AAC format as well as MPEG movies. The iPod must be connected to the portable device section. This will help you share movies, music, pictures and other data and you can even copy the downloaded data to your iPod from the Xbox.

Get MMS working on iPhone 3G, iPhone 3GS, MMS on 3.1 for AT&T. Step 1 : First of all, you have to update to 3.1.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to back up and restore data easily on Ubuntu Linux.

In this screencast, we look at how changing the page style of each sheet in your spreadsheet can enable you to apply different formatting settings for each one.

When trying to get fit, something that can easily be overlooked is your overall sleep quality. Your body needs sleep to recharge and it helps to maintain a healthy lifestyle, there's no denying it. Luckily, Google Fit can help you track your sleeping habits without having to jump through any hoops along the way.

As far as HBO is concerned, it's not augmented reality — it's Snapchat. The premium cable network is leaning hard on Snapchat's AR magic tricks to promote yet another series, this time for the adaptation of Philip Pullman's His Dark Materials series of novels.

In the business world, it's sometimes said that "where there's smoke, there's fire." At Snapchat parent company Snap, Inc., it appears the equivalent of smoke is executive turnover.

All of the new iPhones from 2018 were released with dual-SIM support, but none of them were capable of actually using the eSIM in iOS 12, only the physical nano-SIM. But on iOS 12.1 and later, you can finally take advantage of eSIM so you can have, say, a business and personal plan on your iPhone XS, XS Max, or XR at the same time.

On Thursday, Snap released three new templates for its Lens Studio that will give creators access to augmented reality capabilities previously only available to Snap's own design team.

Location-based AR game Ghostbusters World is creeping closer to launch, and developer FourThirtyThree has released some new gameplay footage and a trailer to capture the interest of the living.

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Your email inbox is a treasure trove of personal data. The people you contact, your writing style, which messages you flag as spam — all of this information and more can be used to paint a clear picture of you. Google knows this as well as anybody, so they use this data to constantly improve your experience in Gmail.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

In hopes of strengthening its growing augmented reality team, Apple has reportedly hired Michael Abbott, an engineering and investment veteran with past ties to Twitter, Microsoft, Palm, and others.

Unlike many browsers, Firefox gives a lot of control to the user. By default, Firefox does a great job of balancing security and performance. However, within the app's settings, you can modify options to shift this balance in one direction or another. For those looking to shift it toward security, here are few suggestions.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

In the wake of reports of slow iPhone X sales and a possible early end to its shelf life, Apple CEO Tim Cook is on a public goodwill tour of sorts, espousing the virtues of Apple AR.

On Thursday, Snapchat opened up its walled garden of World Lenses to the masses of creators with the launch of Lens Studio.

Snapchat's popular AR lenses just got a lot more useful for businesses, as the company has now opened its Context Cards platform to sponsored content.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

Cruise Automation, General Motors' (GM) driverless car arm, has hired two hackers who were once seen by many as a safety threat to help find vulnerabilities in its self-drive car network.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

We have some bad news for BlackBerry fans: It looks like the upcoming KeyOne flagship won't be shipped in April after all.

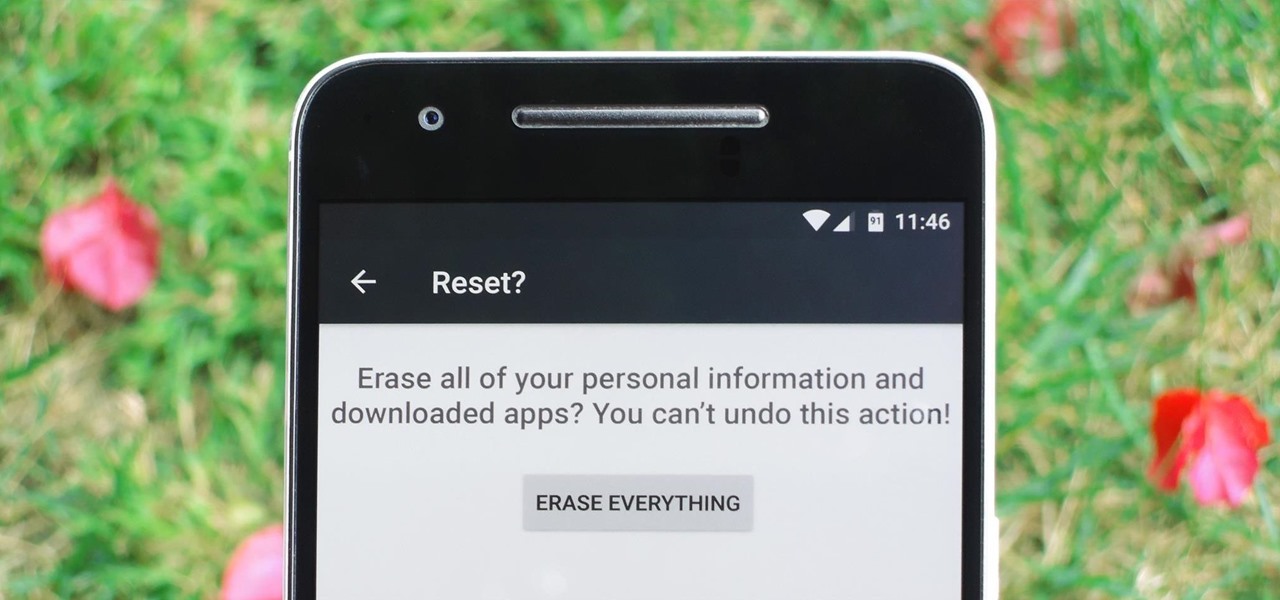
Whether you're performing a factory reset to get your device ready for sale or trade-in, or you're wiping your device in the hopes of fixing software issues, there's a right way and a wrong way to go about it. Sure, it seems like a simple task on the surface, but if you're not careful, you could end up wasting a lot of time or losing precious data.

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.