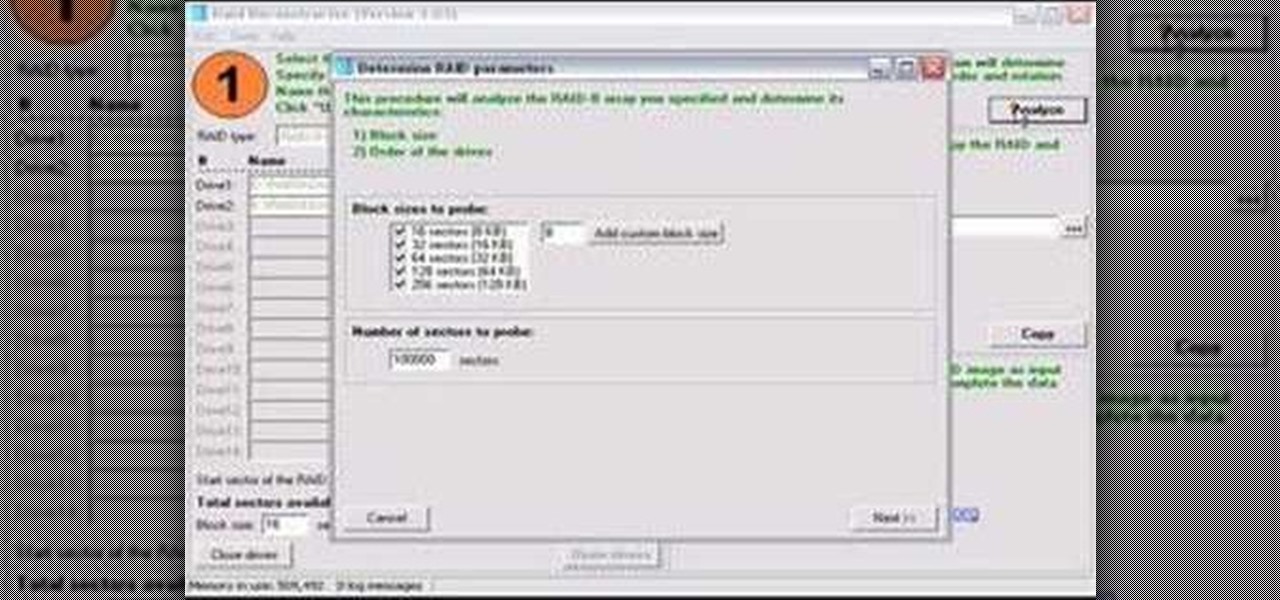
Check out this video tutorial on how to use the Runtime RAID Reconstructor software to create a destriped image with a two drive RAID 0. So, get your data back with this copy of your RAID to have recovery options for your computer. This program will collect, sector by sector.

A tutorial on how to "break in" to your Windows machine after you have lost the password. This works in Windows NT, 2000, and XP machines without an encrypted file system. I then show you how to wipe a hard disk to assure no one can gain access to your data once the drive is sold or discarded.
This is a very basic introductory video that teaches you how to successfully install Quartz Composer on your MAC OSX 10.5 Leopard. Quartz Composer is a node-based graphical data software that uses visual programming language. Built exclusively for use on the MAC OSX, it's a handy software for graphic designers.
In this episode I show you a few of the innumerable uses of Quicksilver. Quicksilver is an unified, extensible interface for working with applications, contacts, music, and other data. The possibilities are endless. These are just a few of the ways that I use Quicksilver on a daily basis.

How to change the alignment of headings in Open Office Calc to fit all your data onto one page.

Larry Jordan explains the advantages and trade-offs of various external drive solutions, compares data rates or FireWire drives vs. SATA drives, what solutions work the best and how to avoid clogging your Final Cut Pro workflow.

Cells in Numbers '08 are the same as in Excel. Basically, they are where you store your data. This tutorial will show you how to use the different functions of cells.

A spreadsheet software wouldn't be much good if you couldn't use formulas and functions on your data. This tutorial goes over how to use them in Numbers '08.

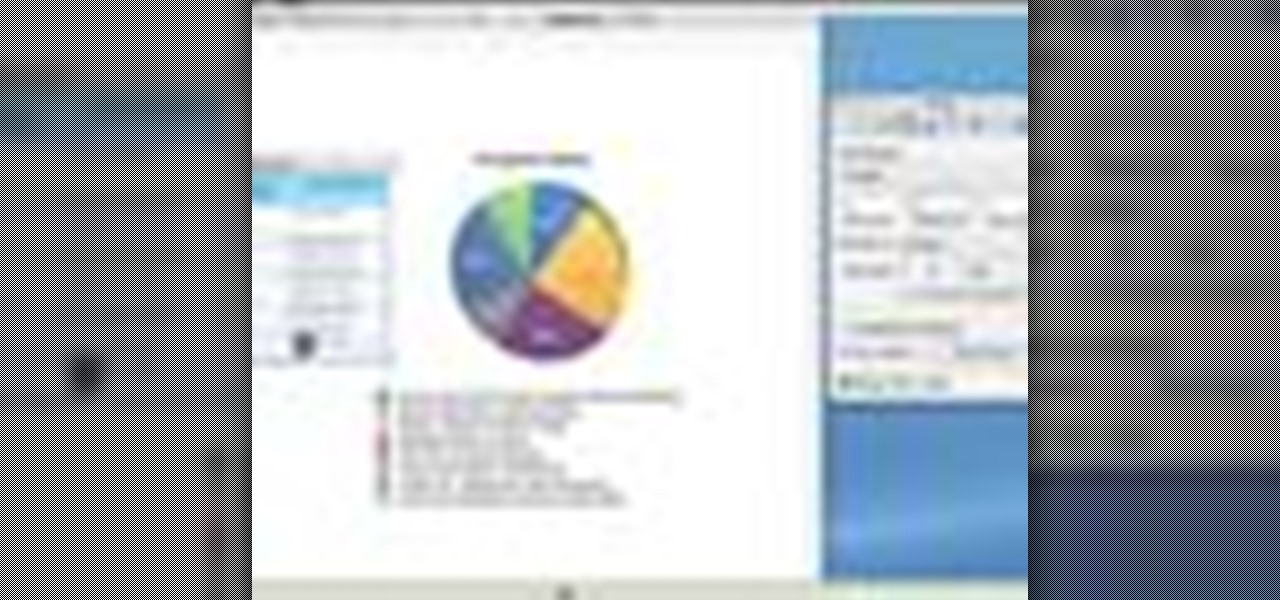
It's often best to use a graphical representation of the data you've assembled or calculated. This tutorial shows you how to create charts to visually show your results.

In Numbers '08 you can enter data dynamically with interactive buttons and sliders known as cell controls. This tutorial goes over using check boxes and sliders.

If you can't access your iCloud data such as emails, contacts, calendars, photos, notes, reminders, files, and other documents via a web browser on untrusted devices, like one at a library or friend's house, there's an easy way to regain access.

Even with the convenience of online storage like iCloud and Google Drive, data management can be a constant struggle on your iPhone. If you continuously find yourself having to delete messages, photos, videos, and other files to make room for other things, know that there's an easy way to free up space without erasing anything important or having to dig through documents and data yourself.

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.

Every single photo you take carries with it a considerable amount of seemingly "invisible" yet important information known as metadata. Although metadata is usually helpful to sort your photographs by location and date, that same information could potentially be used against you, especially if the pictures are taken during a precarious situation.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

Since we wouldn't have Android without Google, everyone has come to realize that the Pixel smartphones are a prime example of what an Android smartphone should be. With so many unique software related features, no wonder people want that Pixel experience.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

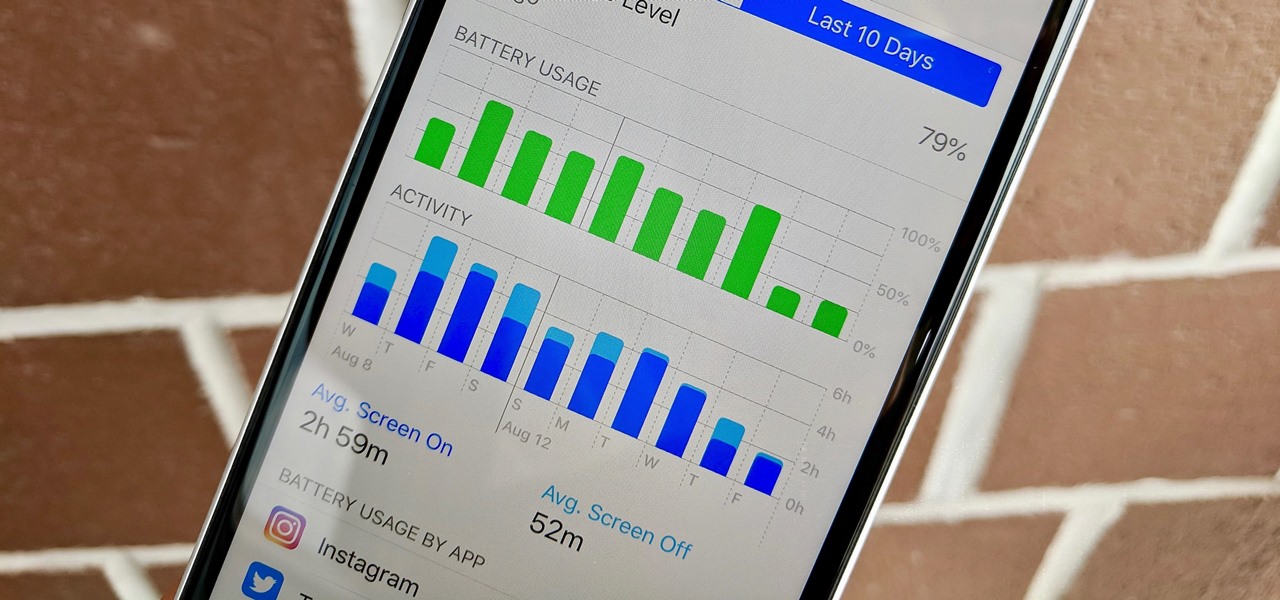
Performance and stability improvements, as well as new features, are just some reasons to install iOS 12, but new changes mean new battery health challenges. It can be difficult to boost battery life while taking advantage of everything this update has to offer. Luckily, there are plenty of ways to avoid unnecessary battery drain when using iOS 12 on your iPhone.

With iOS 12, Apple is making up for mistakes from the past, with iPhone batteries being no exception. The new update builds upon both battery health and performance throttling tools introduced in iOS 11.3 by offering users more information about your iPhone's battery usage than ever before.

The gig economy is thriving, and if you aren't already making money with your phone, you could be missing out on easy residual income. Some people just want extra cash, and some even manage to completely ditch the 9–5, enabling them to work at their own pace and set their own hours.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

As you may have heard, Verizon has jumped on the "giving up users' data to whomever will pay" bandwagon with its new AppFlash spyware app that's all set to be pre-installed on at least one of the Android phones they sell.

The newest version of Apple's mobile operating system, iOS 10, has been out for about a month now. But like every year beforehand, some of you who updated will not be happy with the latest and "greatest" iOS version.

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I suggest doing so unless you are familiar with basic assembly programming and system calls. This is by no means rocket science, so therefore I will simply repeat my TL;DR from last time before we get started, so that the a...

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

If you're anything like me, you started down the Android-modding path for two distinct reasons; to run cutting-edge software and squeeze every bit of performance out of your hardware. Utilizing the new F2FS file system on your rooted Nexus 4 or 5 fulfills both of those desires at the same time.

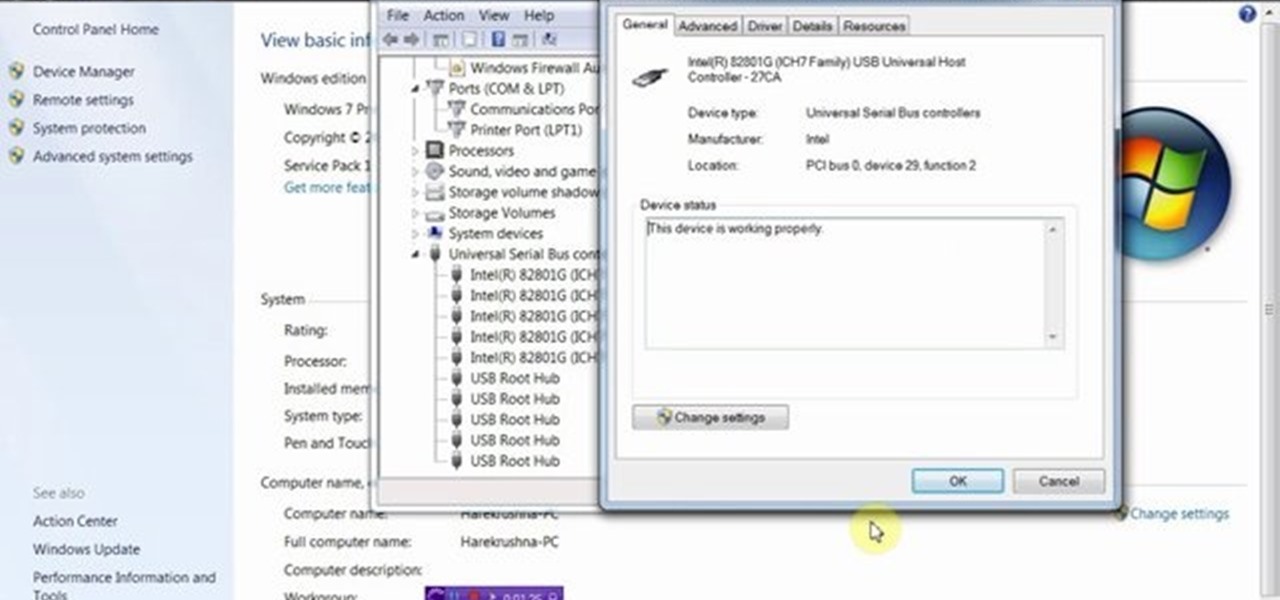
This video will show you how to enable or disable USB port in your PC. If you disable USB port nobody could insert a USB device on your computer and could not copy your data. You could enable the port whenever you needed. Watch the video and follow all the steps.

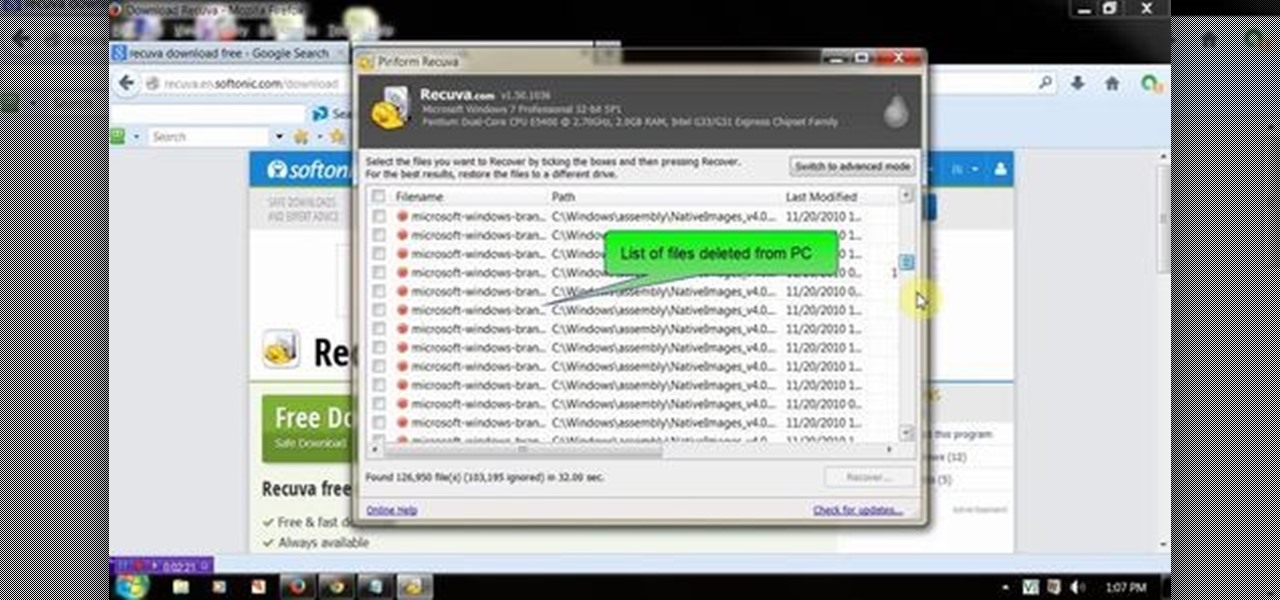
This video will show you how to recover permanently deleted file which you have deleted from recycle bin. But if any new file allocated to those positions then the files could not be recovered with this tool. Watch the video from the installation to execution of the tool to recover deleted data.

This video will provide an idea how to disable or enable the USB port on your PC. By disabling USB port will restrict people from copying your files into USB devices. This is a very effective trick to save your data. Watch the video and follow all the steps.

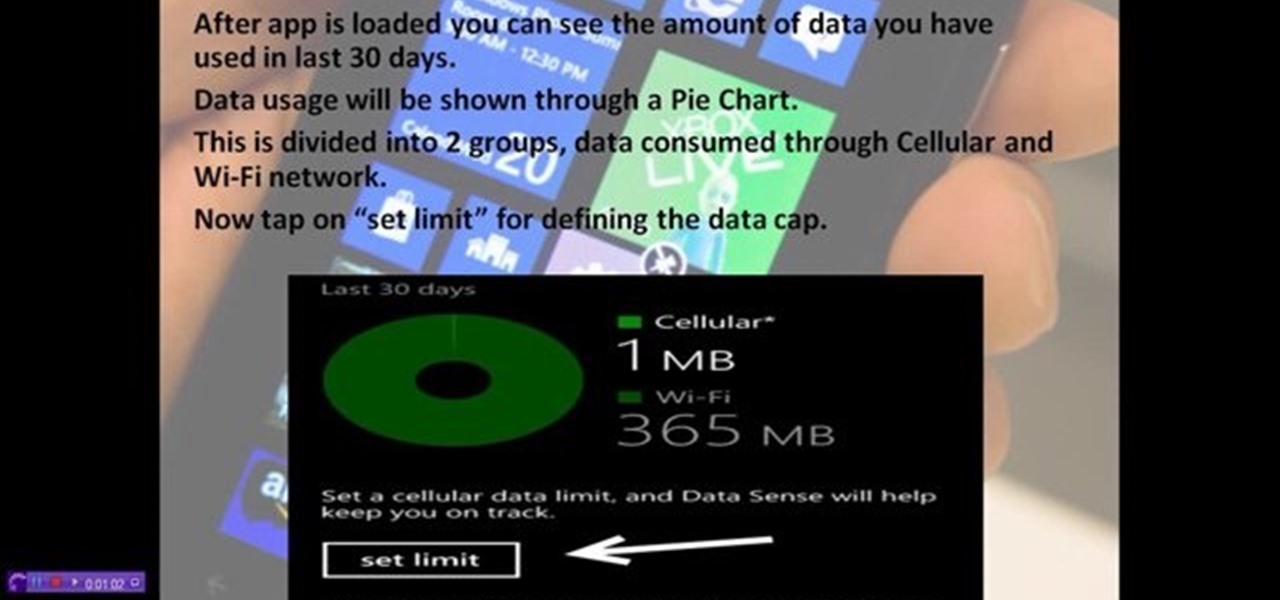
How to control and limit your internet usage in your windows 8 phone? You may want to restrict your internet usage and want to set limit for apps also. If you set your usage limit internet will stop automatically after reaching the limit. Follow the video to employ in your own phone.

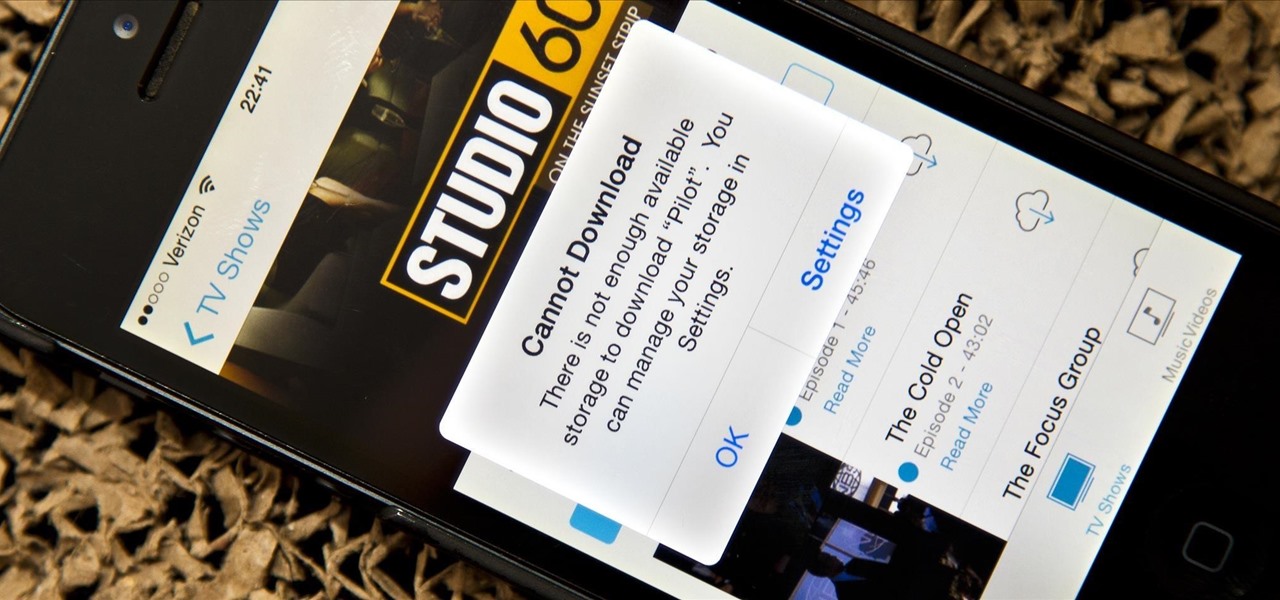
Running out of storage space on your iPhone is annoying, but trying to free some up is downright aggravating. Until they figure out a way to throw a terabyte of flash memory in there, you're going to have to do some spring cleaning every now and then, especially if you're trying to update to iOS 8.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

Now that iOS 7 has rolled out to the general public, with an overwhelming fit of mass hysteria, it's only custom for people to start bitching about battery drain—and I don't blame them. I was experiencing some rapid battery drain after first updating my iPhone 5, as well.

Want to breathe some life into your Macbook Pro? Get an SSD! But how to swap your data over? Here's how!

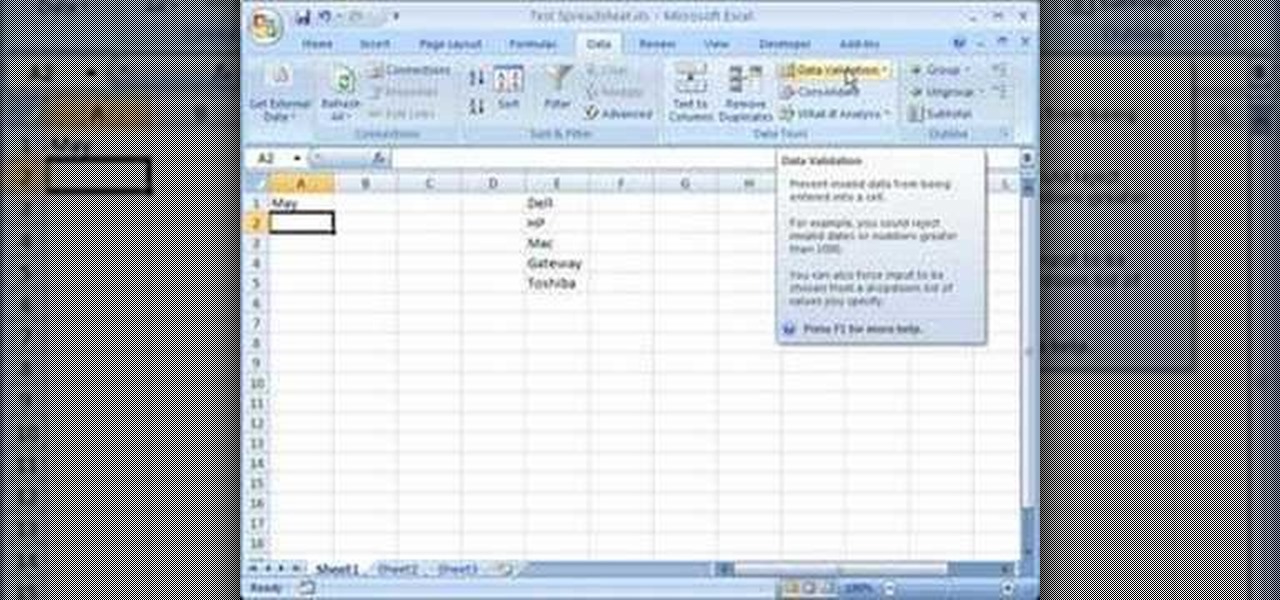
This video is a tutorial on how to create drop-down menus in Excel 2007. Select a cell on your spreadsheet and click on the “Data” tab. Go to the “Data Tools” section and select “Data Validation”. In the window that opens select "Allow" and choose "List". You will create a list of the values you want to allow. Type in the values, separated by commas, and click OK. Now you will see your selected cell has an icon to right that indicates there is a drop-down menu containing the value...

First of all launch the program "Nero 7". Now click on "cd" and then click on "cd-rom boot'. From the new screen choose ' image file' and then click on 'browse'.Now go to the 'drive d' and select 'windowsxp-boot image' folder and then select 'boot.ima' file. Now click on 'open'. Now click on 'advanced' and then click on 'no emulation'. Select the ‘number of loaded sectors' and increase it to '4'. Now click on 'ISO' and then make sure that all the data is same as that on the tutorial.