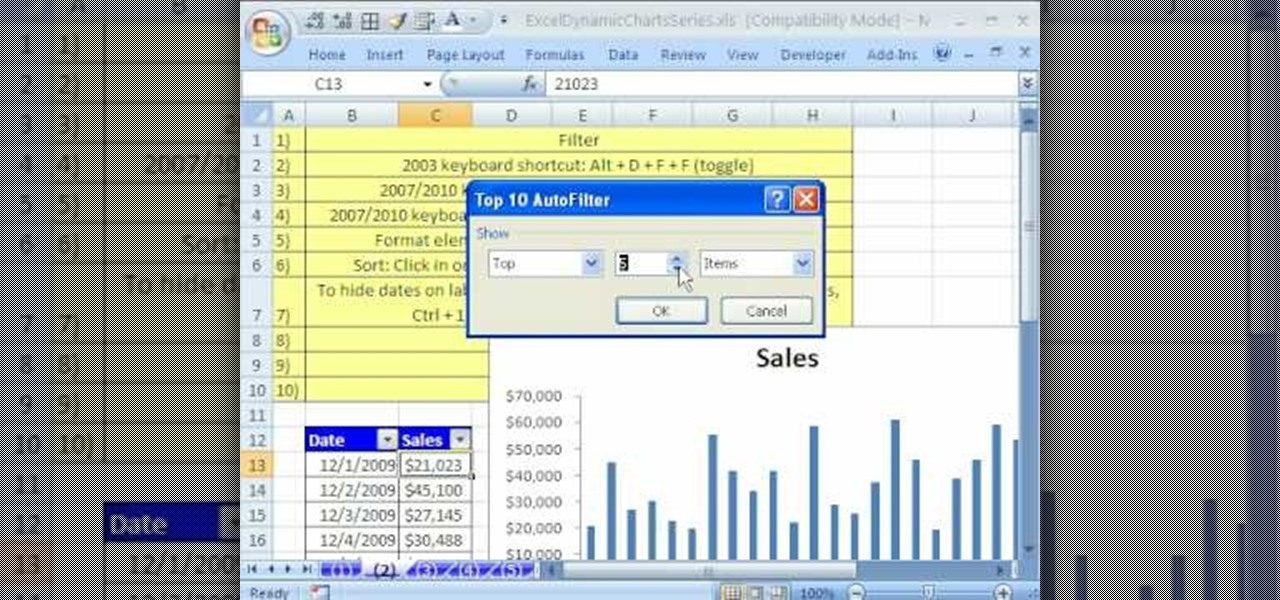
In this Software video tutorial you will learn how to use the filter & sort feature in Excel. First create a column chart on an excel sheet. In this example, it is a date and sales chart. Click alt+F1 and the chart is displayed. Then click and delete the legend and the horizontal lines. Now go back to the data set, click on a cell and click ctrl+shift+L and that will add the auto filter. ctrl+shift+L is for Excel 07. For earlier versions, see the commands listed in the video. This is a toggle...
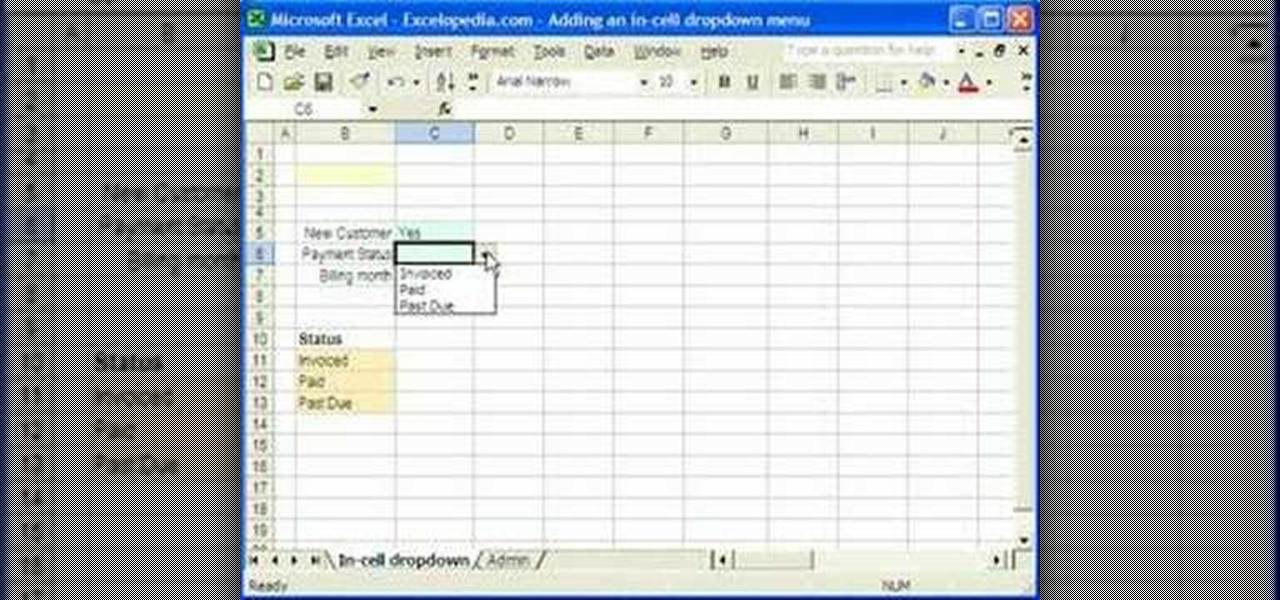
1. Select the cell for which the dropdown menu is to be applied. 2. once the cell is selected goto DATA menu select VALIDATION.Data validation dialog box will be displayed.

MMS is disabled on some iPhones. To enable it go to settings, and go into the general settings. From the menu select network and select cellular data in the network menu. In the Cellular Data settings go down to MMS options. Now set the APN as wap:voicestream.com, MMSC as http://mms.MSG.eng.t-mobile.com, and MMS Proxy as 216.155.165.50:8080. Once you do these settings go to the message settings and make sure that the MMS messaging is turned on. Now go to messages and create a new message. Add...

In this Know Your PC video the instructors show how to perform a recovery on your computer by demonstrating it on the HP TouchSmart PC. This recovery process will work on any HP desktops, HP Pavilions, Compaq Presarios. Your PC might get corrupted if you recently made any changes to it or installed software that contained viruses and many other reasons. In such cases the best thing to do is perform a system recovery. Recovery will help you take your computer right back to the way it was out o...
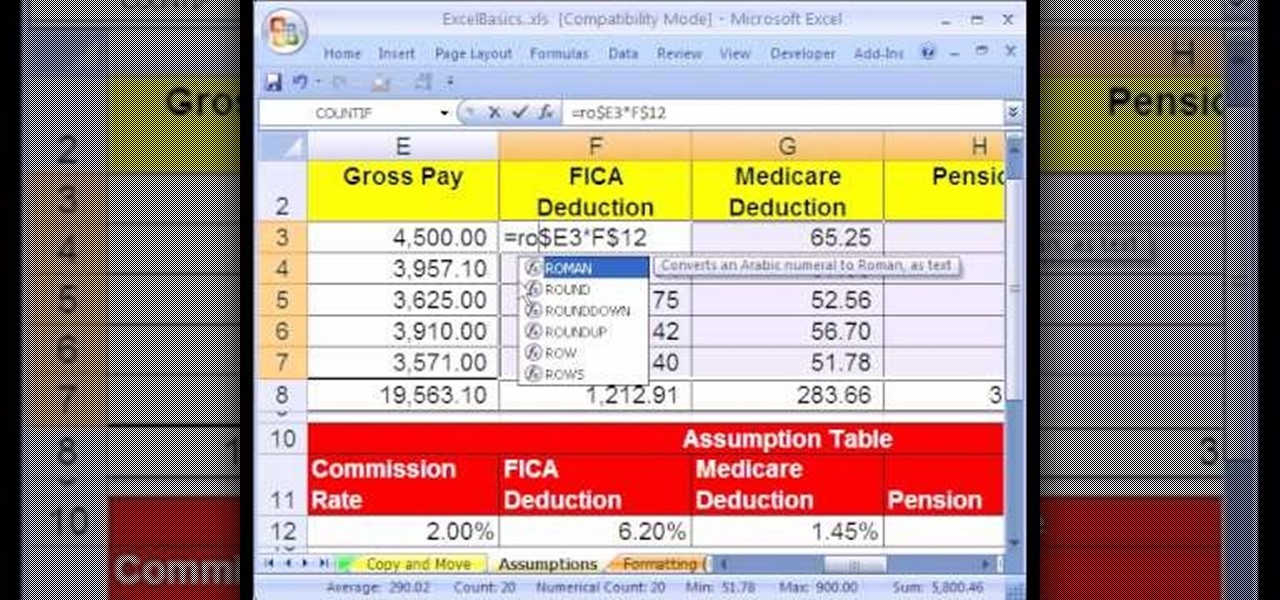
In this video the instructor shows how to use the Round function and also format numbers in Microsoft Excel. Normally while calculating formulas in Excel, the formatting of numbers can get you into a lot of trouble and to get around this problem you need to use the Round function. To do this take some sample data in a Excel work book and apply any formula that you want on the data to arrive at some calculation. Now because of this formatting some times you can arrive at a wrong result as show...
In this first demo of a 4-part series, learn how to set up labels for mass mailings using the Mail Merge feature in Word 2007.

In this article, I'll be explaining the basics of how microcontrollers work, physically and virtually. First off, microcontrollers are no simple thing, so don't be discouraged if you find it mind-boggling! The world of microcontrollers is fascinating, engaging, and an awesome hobby; it never gets boring. I'll be focusing more on I/O and analog based microcontrollers, such as those running Arduino, and using Atmel chips as examples (these are most commonly available, and easy to program).

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...

Sometimes you come across problems and glitches when you're playing FarmVille, FrontierVille, any of your facebook games, or even just using the internet for ordinary purposes! It might just be getting really slow, or you might start losing data or in-game items. As the Zynga customer support article will tell you, you sometimes need to clear you browser and flash cache! Here are some simple steps to do just that!

Losing your important data can be more painful than losing the hardware the data was stored on. Precious memories, files you don't often access but always want to have, there's so much you store on impermanent devices that you can't live without. Backing up your information to a secure, cloud-based location is the best way to stave off disaster here. Polar Backup Unlimited Cloud Backup Storage will give you an unlimited amount of cloud storage while making the process super easy.

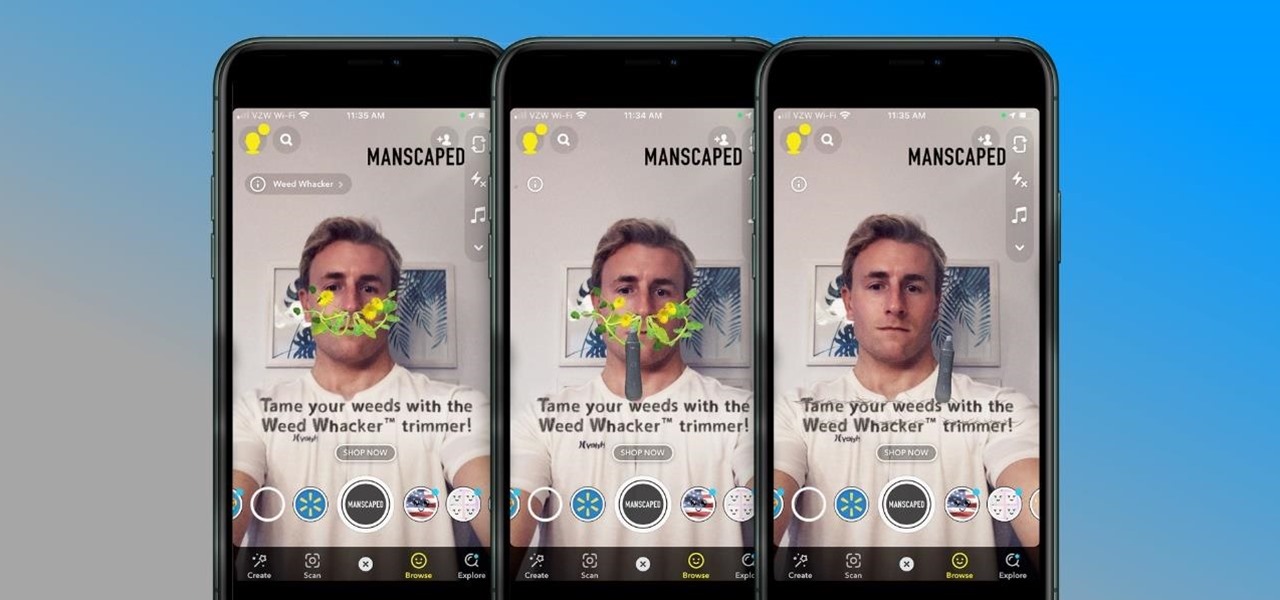
If you're a man and subscribe to podcasts or YouTube channels that cater to masculine interests, then you've almost certainly encountered sponsorships from Manscaped. And that means I don't have to explain what the company is selling you (for the uninitiated, it's a company dedicated to helping you trim your body hair—most notably, your nether regions, in addition to other areas).

More information is available to us now than ever before. We simply cannot make sense of so much data on our own. Thankfully, we have programs to do the heavy lifting for us.

Do you believe you just don't have an intuitive sense of math? Sadly, this is the case for many people. The reality is that math is learned with practice. No one is born with a math gene making them more intuitive than others.

We've become accustomed to new models of learning over the past generation. What once required classrooms and chalkboards now only needs a laptop and an internet connection. At this moment, with much of the population staying inside, eLearning has never been more necessary than now.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

Last week, Apple released the first iOS 13.4 beta with fun and useful new features, such as new Memoji, an upgrade Mail toolbar, and the ability to control your NFC-compatible car via CarKey. To add to that, Apple just released iOS 13.4 developer beta 2, but does the update have any more new changes to be excited about?

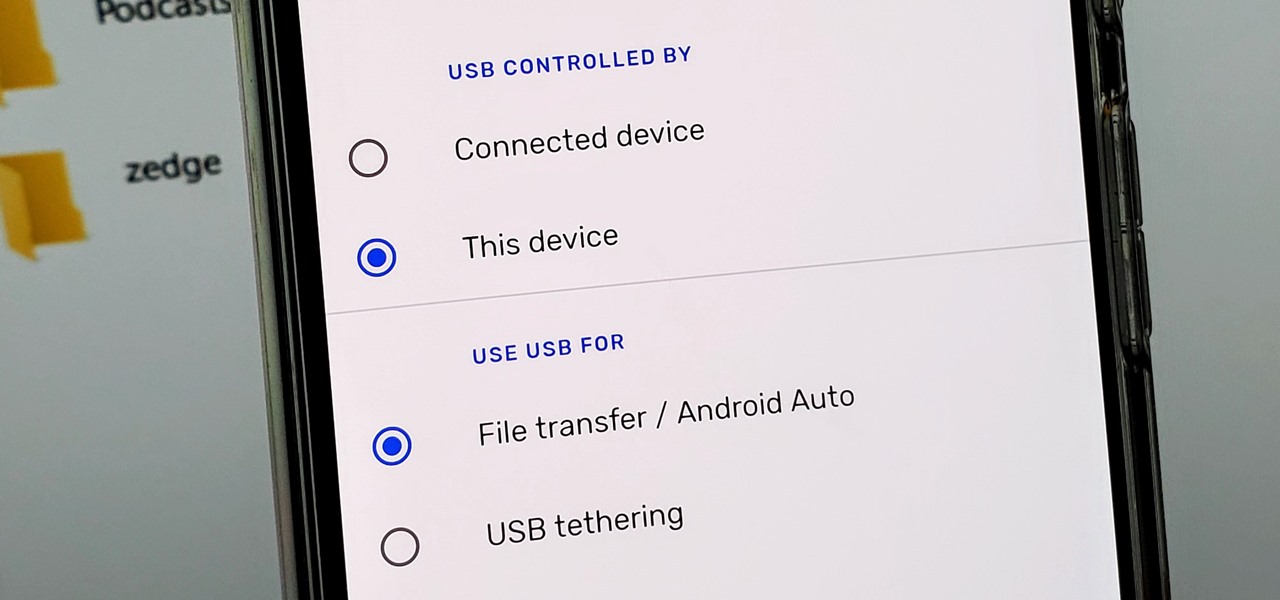
Back in the earlier days of Android, you were able to connect your phone to a computer, and it would mount automatically. This meant once the USB connection was made, your internal storage would pop up on the computer and you could go about your business. But recent versions of Android changed that to help increase security.

Facebook and its Oculus subsidiary have been open about their intentions to bring AR wearables into the mainstream for some time now.

Apple's latest updates to its operating systems add another security feature to its Find My service, so you have an even better chance at locating your lost iPhone, iPad, or Mac should it ever happen. As long as you have the option enabled, you can leverage other Apple users' devices to find yours on the map.

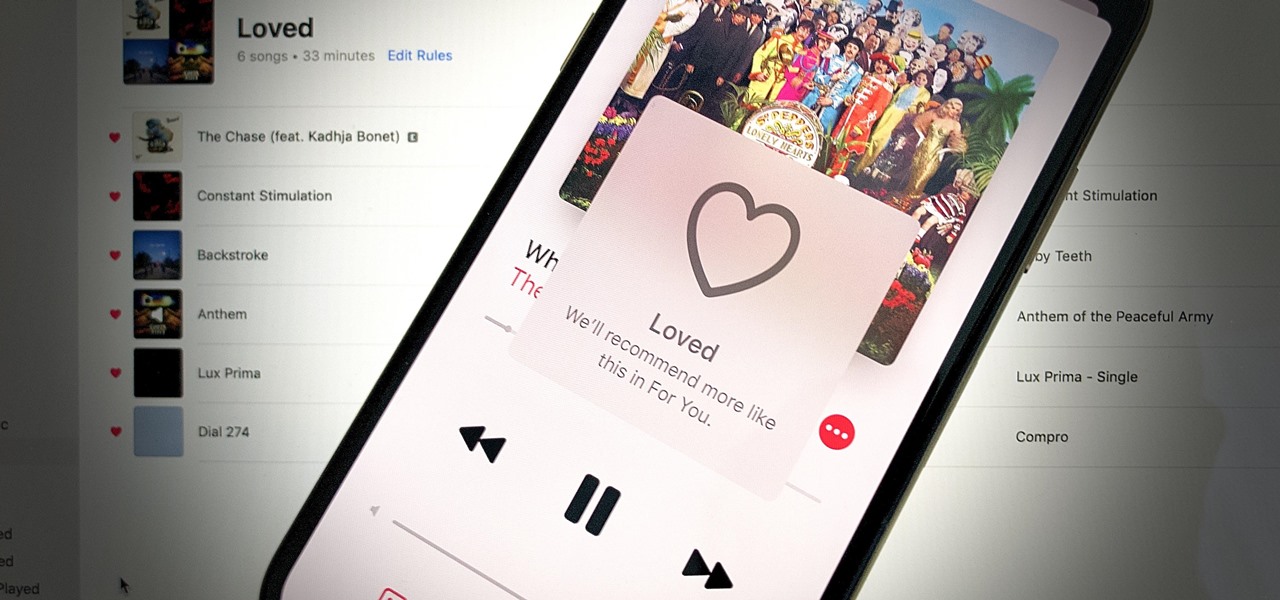
In Apple Music, loving and disliking songs is a great way to teach Apple's subscription service what type of tunes you like and which you don't. While it also seems like it should be an excellent way to keep track of songs you enjoy in the wild, there's no clear way to view all of your loved tracks in one convenient list. There is a way, however, but easy it is not.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

When it comes to customizing Android, there's no better way to make it your own than by installing a custom ROM. You gain new features that were not accessible on the stock firmware that came with the phone, and you get complete control over how your system looks and feels. But there's definitely a learning curve.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

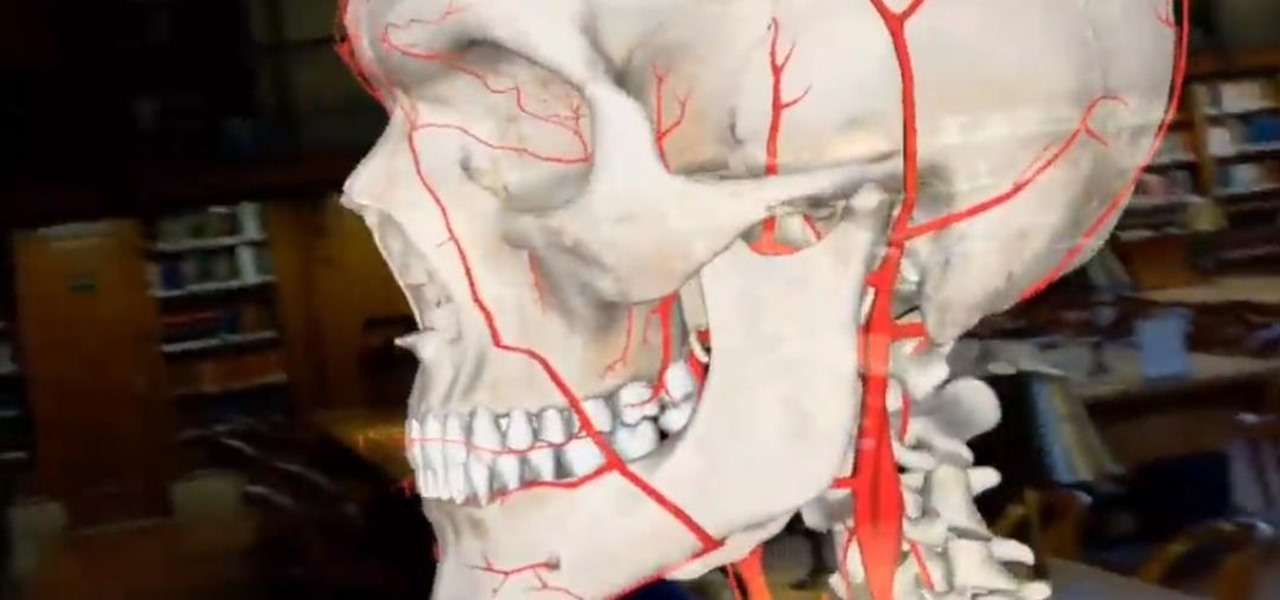
Not content to merely assist surgeons via the HoloLens, Medivis has expanded its augmented reality suite to Magic Leap One with an app for medical students.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Election Day is like the Super Bowl for network and cable TV news, so ABC News is breaking out the big guns with a new augmented reality experience to win over eyeballs of viewers.

All phones (yes, iPhones too) slow down over time. As your device gets bogged down by various apps and you begin to run out of storage, it's just an inevitability. That doesn't make it any less frustrating ... I mean, is there anything more annoying than a slow phone? My answer: No. Of course not. It's the single most annoying thing ever.

Having a dropped call can be incredibly frustrating, especially when you look down and see that your iPhone has full reception. While there's any number of issues that can cause this, one common and often overlooked issue is your iPhone failing to switch cell towers as appropriately needed.

As the official release of iOS 12 nears closer each day, Apple continues to update its betas. The company released the fourth beta of the upcoming software to developers Tuesday, July 17, exactly two weeks after the release of the third developer beta which came out just a few days before the second public beta.

Sometimes we need to share screenshots, but don't want to reveal the entire screen. This usually requires some editing that isn't typically easy to do on a smartphone. BlackBerry recognized this issue and created a tool called Redactor that makes it easy to hide your data before sharing.

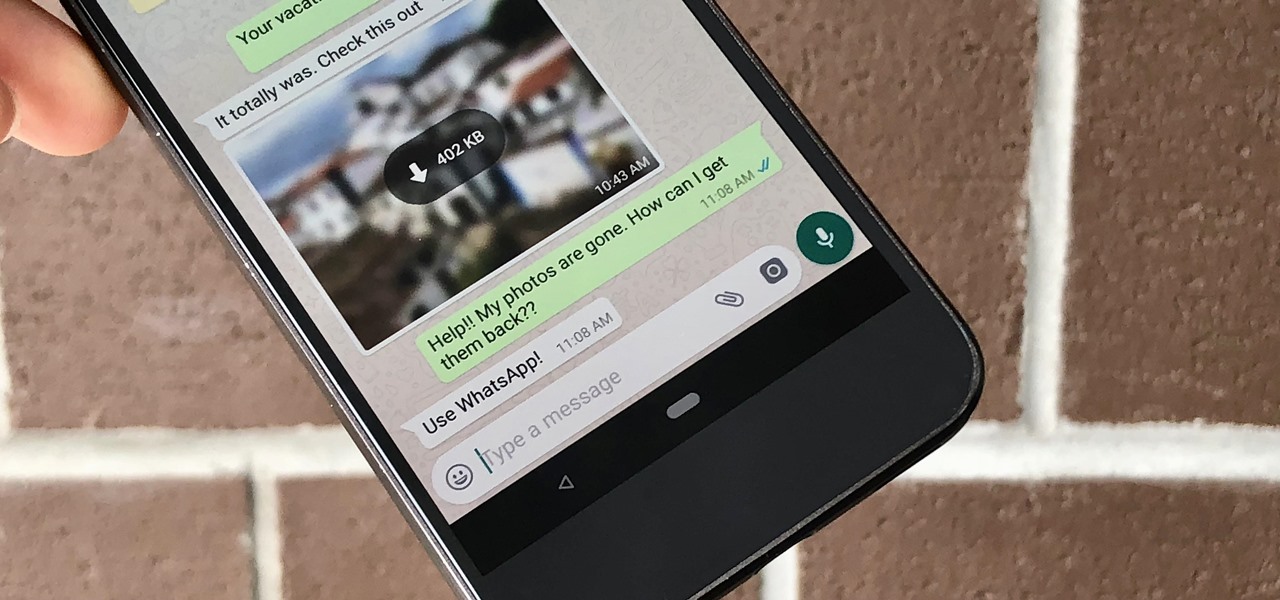
Thanks to cloud storage's increasing accessibility, permanently losing photos is becoming less and less common. Still, if you accidentally delete a picture from your smartphone without first making a backup of some sort, that data is pretty much toast — unless we're talking about photos from WhatsApp.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

Over the years, we've seen security breach after security breach, as well as high-profile data scandals where collected personal information was misused by companies. Apple makes customer privacy a priority, so there have been few issues to worry about when it comes to its services on your iPhone. However, there are still plenty of privacy settings to explore and change, especially within Safari.

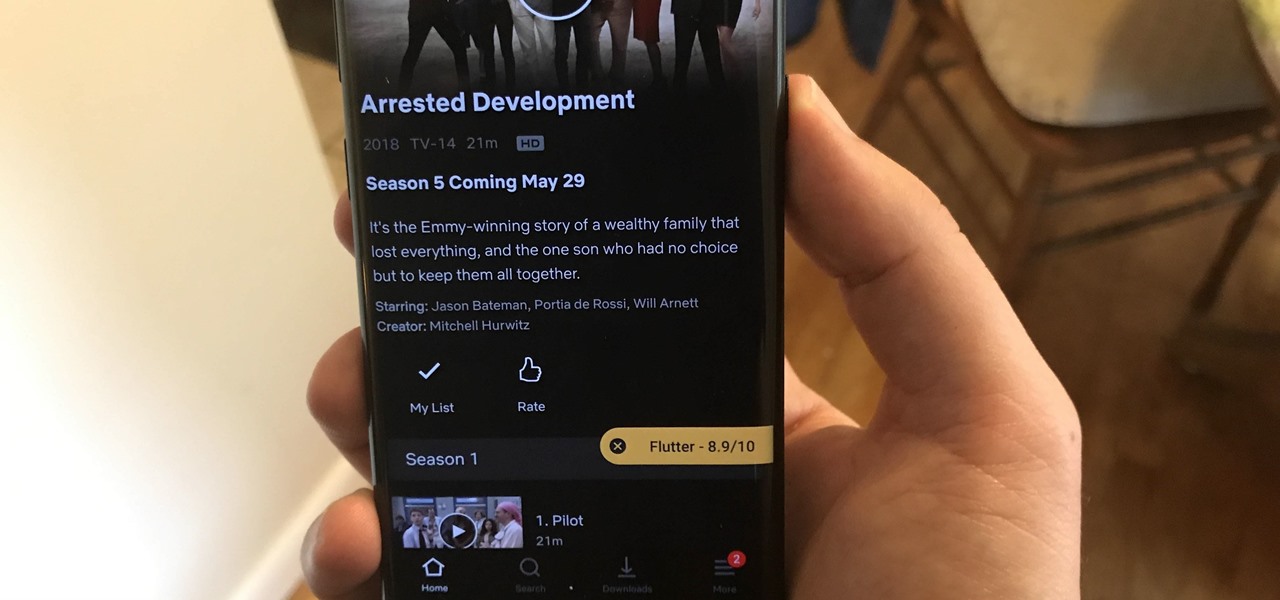
I don't need to remind you that Netflix is a holy bastion of both outsourced and original content. I probably also don't need to remind you that Netflix's rating system sucks. It suggests content based on how much you'd like it, as opposed to how highly it's rated. After all, Netflix wouldn't admit that some of their own material isn't good.

If you are an active player of Pokémon GO, you may soon be capturing more than just virtual pocket monsters.

This week, we're beginning to see the wide ranging impacts of some of the early iterations of augmented reality hardware and software.

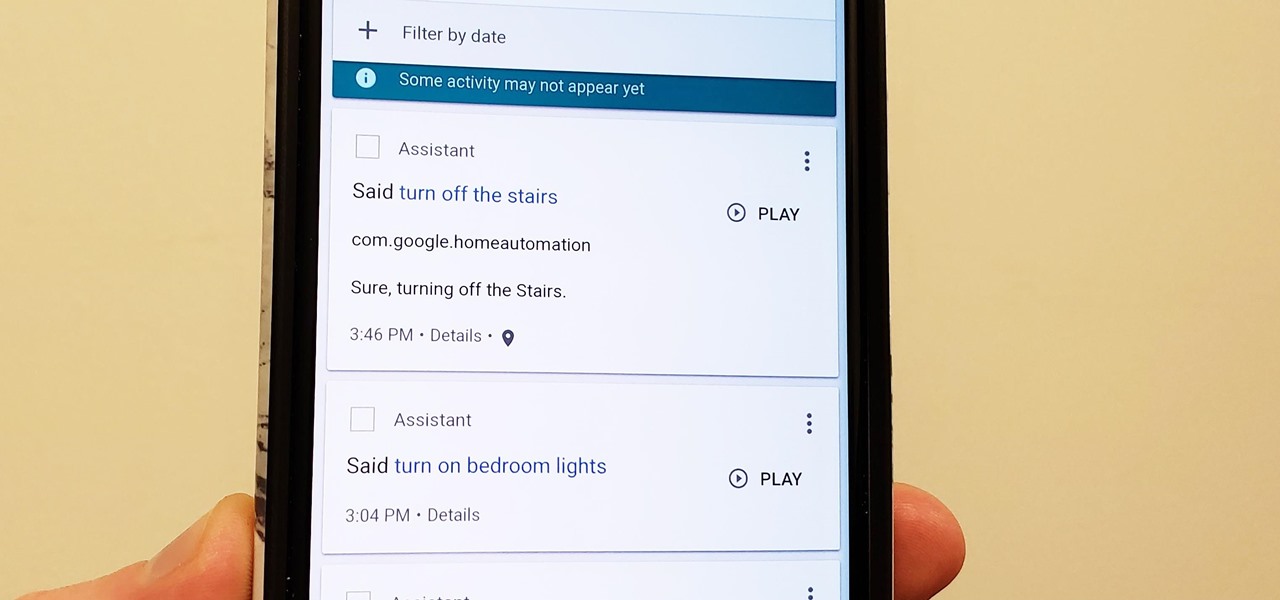
Privacy is a hot topic. In the wake of Facebook's data scandal, many want to safeguard their personal info. On the other hand, we all gain a certain amount of convenience by using services administered by huge companies like Google, Facebook, and Twitter. Google Assistant collects plenty of data, but you can easily check what is stored and delete items at will.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

Ever since the announcement of The Walking Dead: Our World game last fall, publisher AMC and developer Next Games have been quiet about the title. Almost too quiet.