These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

When it comes to smartphones, the biggest complaint voiced by most users is battery life. Sure, it's unrealistic to expect your Android device to run for weeks without a recharge, but many folks struggle to even make it through the day without having to top off their battery.

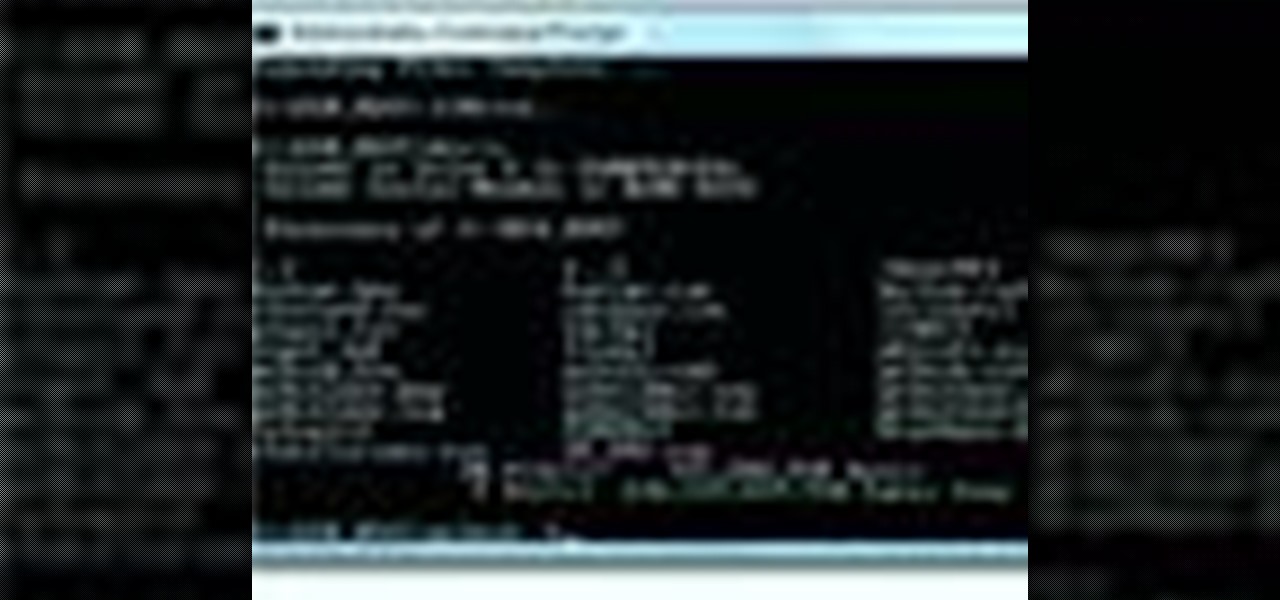
In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

Deciding what to remove from your iPhone in order to free up space isn't the easiest thing in the world. You've got to decide which apps, videos, and photos are worth keeping, even though in a perfect world, you couldn't have to part with any of them.

One of the more talked-about features of Google's new flagship device is the fact that all of the data on the Nexus 6 is encrypted by default. At face value, this certainly seems like an added bonus for the 6-inch phablet, especially in this day and age with growing security concerns abound. It's definitely something that the FBI is none too pleased about.

If you've ever owned an HTC device or anything in the Nexus line, odds are, you have typed the word "fastboot" into your command line at one time or another. That said, odds are, you have only just barely scratched the surface of what this handy little Android tool can do. Let's take a deeper look.

HTC has made it their mission to get updates out to its devices as quickly as possible, with new builds slated for release 90-days after Google finalizes a build—this is dubbed HTC Advantage.

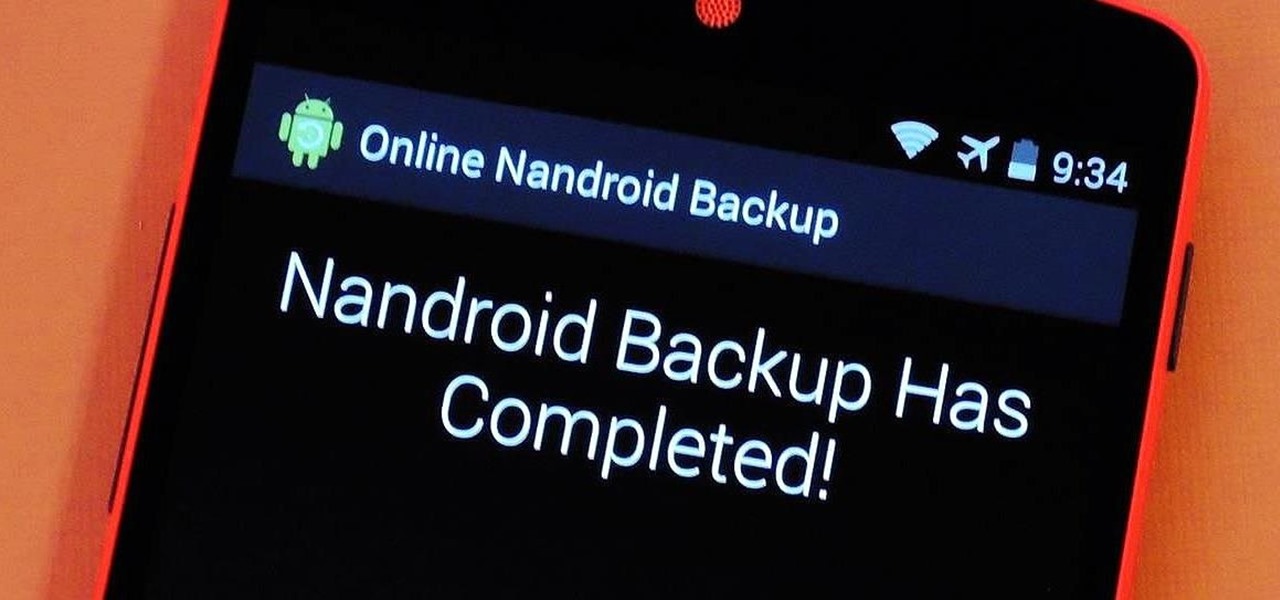
If you have a custom recovery installed on your Android device, the first thing you should have done as soon as you finished installing it was to create a Nandroid backup. But if you didn't, I'm not here to judge—I'm here to show you a much easier way.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

Sometimes, stock just doesn't cut it. When you're sick of the limitations in Sense on your HTC One, a new ROM can be a ray of sunshine. By installing a custom ROM, you can add or unlock new features in Sense, or you can get a pure Android experience instead. It's all up to you.

Whether you have the original Nexus 7, or the 2013 Nexus 7 tablet, rooting it will give you access to tomorrow's features, today.

KitKats? Toast? Sorry if that headline made you hungry, but no I'm not talking about Nestlé's chocolatey wafer treat, nor the crunchy slices of bread you have with your eggs in the morning.

When you post something online, it pretty much stays there. So it's no surprise that Snapchat, the self-destructive photo-sharing app, became such a huge hit, boasting an estimated 50 million users. Its ephemeral nature has proven popular, especially with teenagers—who are now well aware of the burden that permanence on the internet has.

The creation of private browsing was brought upon by the backlash against ad tracking and other ways that sites and agencies take away users' privacy online. People were tired of getting spammed with ads for Vitamin C pills simply because they visited WebMD. Private browsing is now built into all of the major browsers and is used frequently. While private browsing is more infamously known as the "Porn Portal," and does prove to be a great way of keeping racy content out of the sight of others...

What if you could have a secret hard drive connected to your computer that only you could activate? You can! Samimy shows you how to hack a remote controlled toy car and make a super secret hard disk drive in your computer, accessed via a secret activation key. This hidden emergency HDD can only be controlled by your key, regardless of how many people use your computer.

So you've watched this video, done your research, and decided that you want to flash the firmware on your XBox 360 with a LiteOn DG-16D2S rev. 7485 disc drive. Good for you! This video will walk you through the whole process. Be very careful, as messing up in small ways at any point can ruin the results which, when done properly, are really awesome.

In this tutorial, learn how to jailbreak your new iOS 4 on your iPhone or iPod. This jailbreak will let you take advantage of cool new features including the huge app superstore: Cydia. Enjoy!

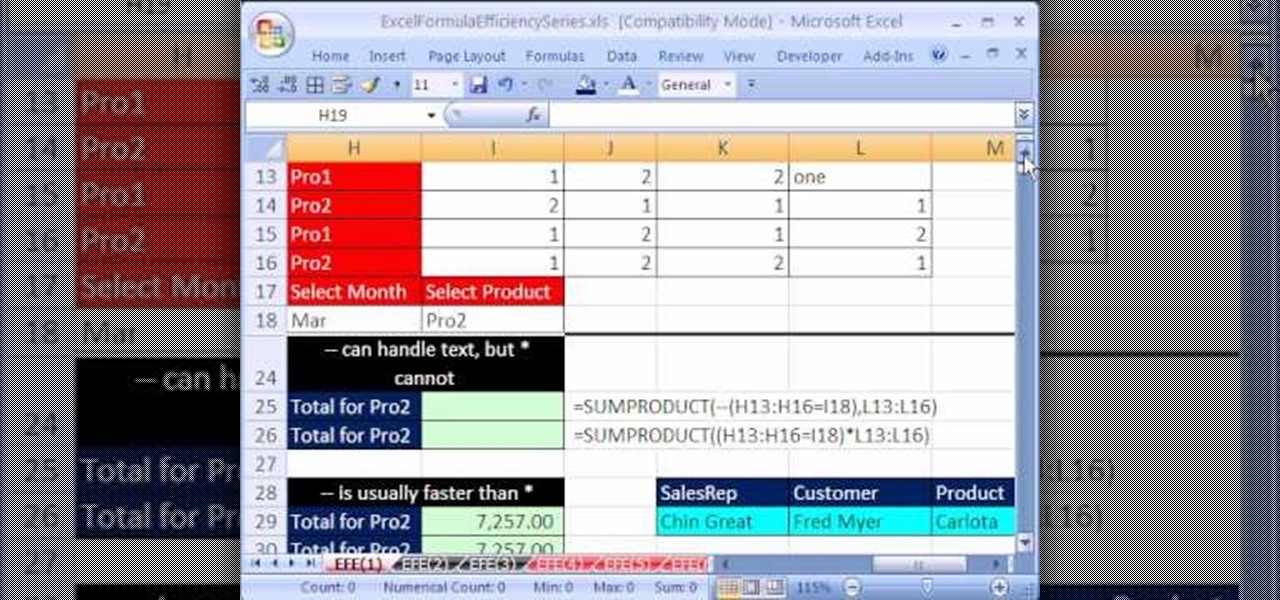
Are you looking for a way to make your Microsoft Excel formulas more efficient? If so, you're in the right place. With this free video lesson from everyone's favorite digital spreadsheet guru, YouTube's ExcelsFun, the very first installment in his "Excel Formula Efficiency" series, you'll learn about the basics of Excel's SUMPRODUCT function — why some people use double negative and why other use times one.

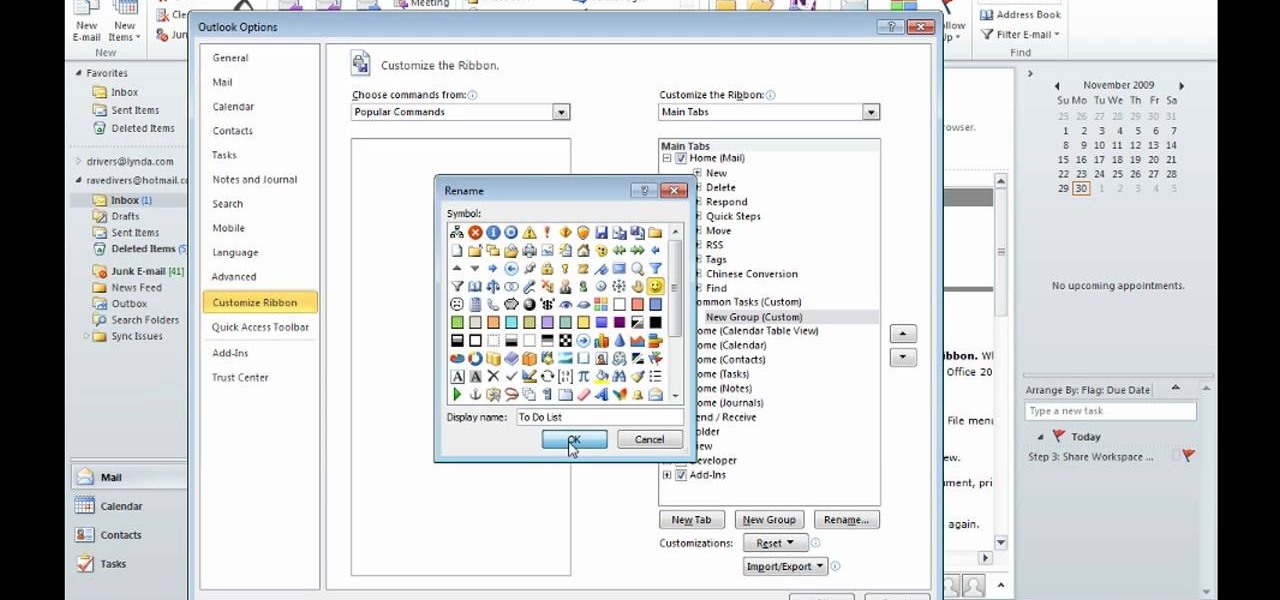
After you launch Outlook 2010 in your computer, you will see the Ribbon strip immediately in the main window. The button for writing a new e-mail is separated from a button for creating new items in the calendar, contact list or task manager. An independent Quick Steps section offers functions allowing you to move a message into different folders, to save it into a calendar as a meeting reminder, to quickly forward it to a chosen person or to more people and to forward it with a FYI note. If ...

Long-time packeteer Bob Bruninga, WB4APR, developed the Automatic Packet Reporting System (APRS), which allows packet radio to track real-time events. It deviates markedly from the usual message- and text-transfer activity. Instead, APRS concentrates on the graphic display of station and object locations and movements.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

One of the coolest feature of the 3G iPhone is the high speed, always on, Internet connection. Having a constant connection to the Internet is pretty much a must have for any dot com mogul. The main problem with the iPhone is the screen is too small to do any serious Web surfing. Yes, it’s great for Twitter or checking up on emails but blogging from it is an exercise in frustration. Fortunately, there is a way to extend that 3G connection onto your laptop by turning your iPhone into a wireles...

This is an intensive one-day overview video tutorial of the fundamental concepts of the Ruby on Rails Web programming framework, presented by the UC Berkeley RAD Lab. The overview consists of six sections of approximately one hour each. Click through the video chapters to go through the Ruby on Rails programming course.

Just got the new Android-powered Samsung Galaxy Tab? A little confused by all of those cables that came with it? No problem. This video will show you how to connect the AC charger and the PC data cable that came with your Galaxy Tab. But really, it's one of the easiest things you can do on this new mobile device.

Want to activate your G1 but don't have a data plan? It's easy! So easy, in fact, that this mobile phone hacker's guide can present a complete overview of the process in about six minutes. For more information, including detailed, step-by-step instructions, take a look!

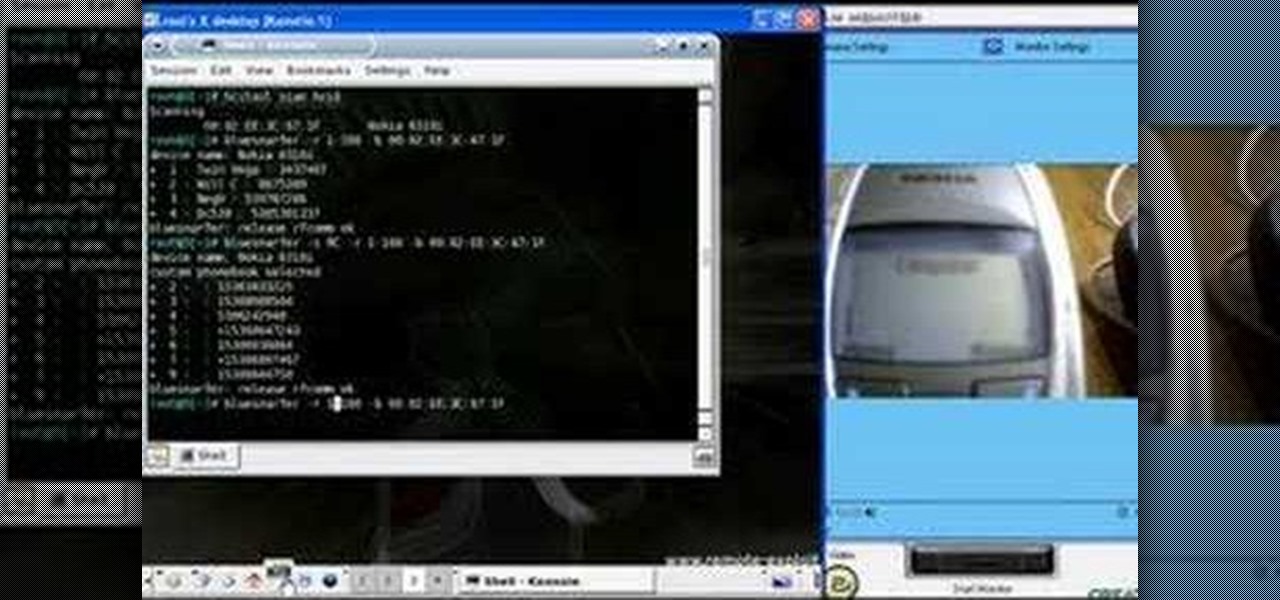
Check out this video tutorial to see how to bluesnarf a Nokia 6310i handset (cell phone). What is Bluesnarfing exactly?

If you're new to DreamCoder for MySQL, one of the first things you may want to know how to accomplish is how to import data to a remote MySQL database. Happily, this tutorial will walk you, step by step, through the process. Take a look!

In this screencast, Tubemogul's very own Mark Rotblat explains to us how to export your data on the web.

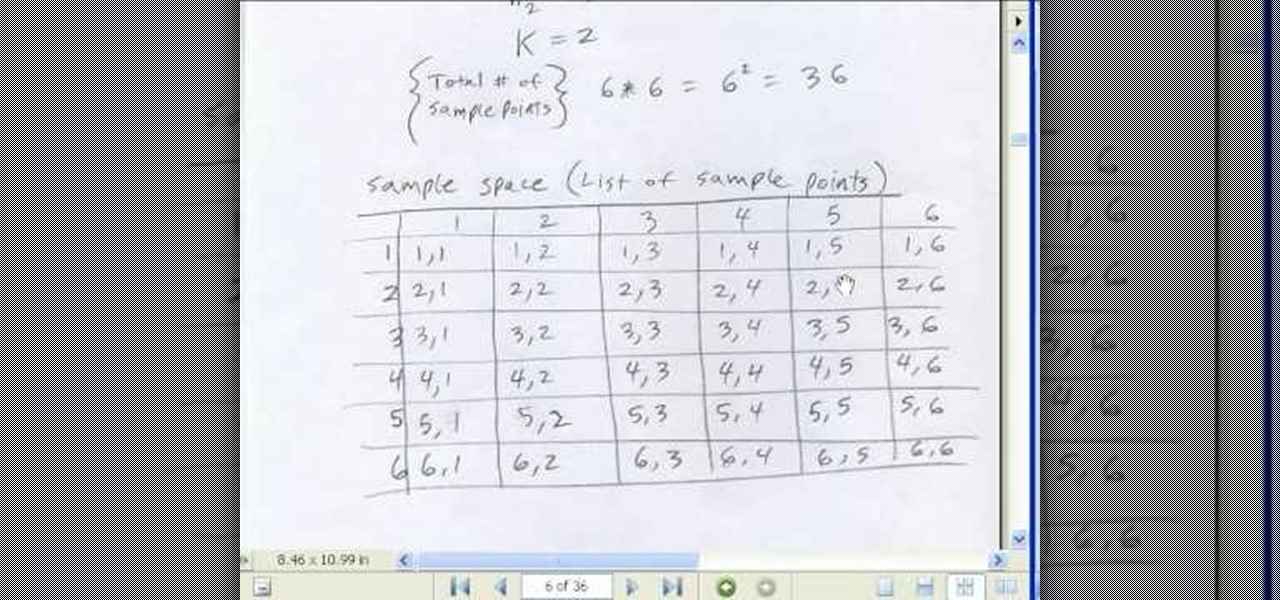
If you use Microsoft Excel on a regular basis, odds are you work with numbers. Put those numbers to work. Statistical analysis allows you to find patterns, trends and probabilities within your data. In this MS Excel tutorial from everyone's favorite Excel guru, YouTube's ExcelsFun, the 50th installment in his "Excel Statistics" series of free video lessons, you'll learn the basics of probability:

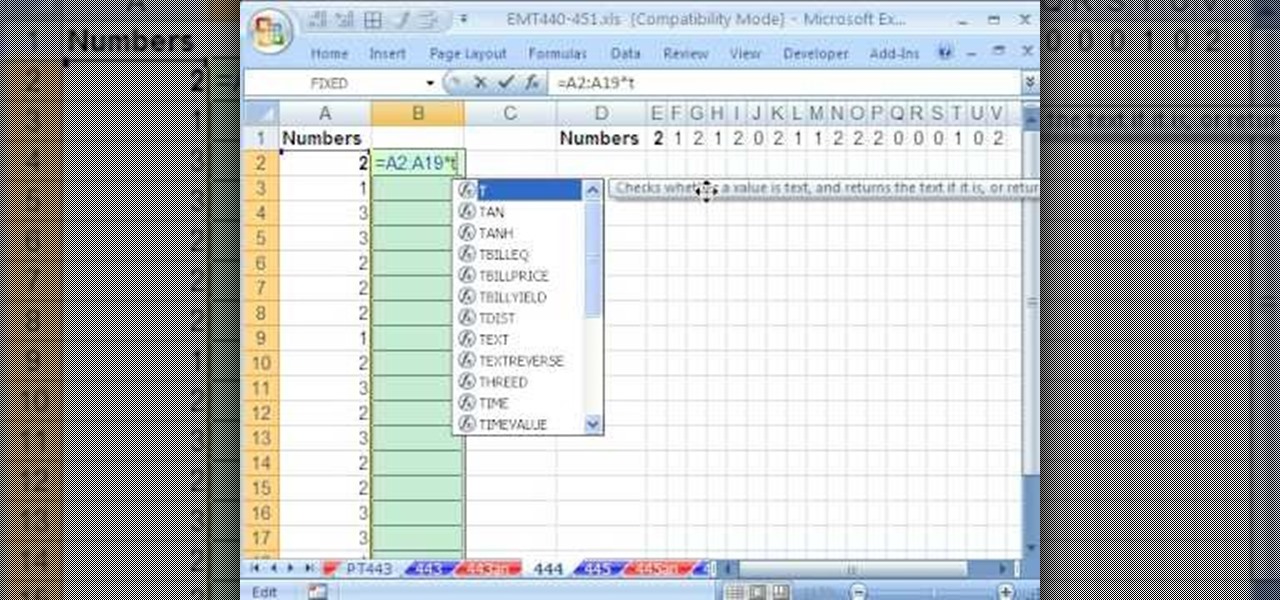
Description Of Excel Magic Trick 444-> to understand this you can also download it from EMT 440-451.

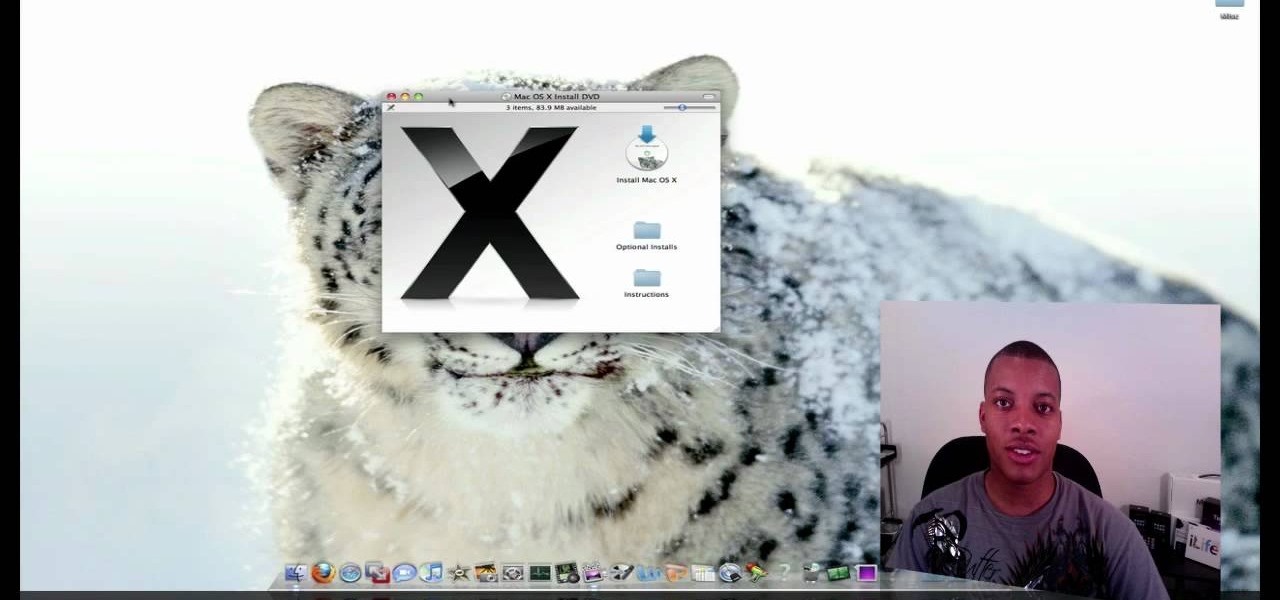
This video tutorial from SoldierKnowsBest presents how to install Snow Leopard operating system on your Mac computer.

This video demonstrates how to stain a white sheet of paper and make it look antique. You'll need two tea bags (an extra one if the other tears open. Place the paper to be stain on a tissue or newspaper to avoid a mess. Take half a tumbler of hot water and dip a tea bag until the color becomes dark orange. Take out the tea bag and gently wipe all over the sheet of paper and also dab gently on the applied parts for a darker stain in some regions to look natural. Repeat this process by turning ...

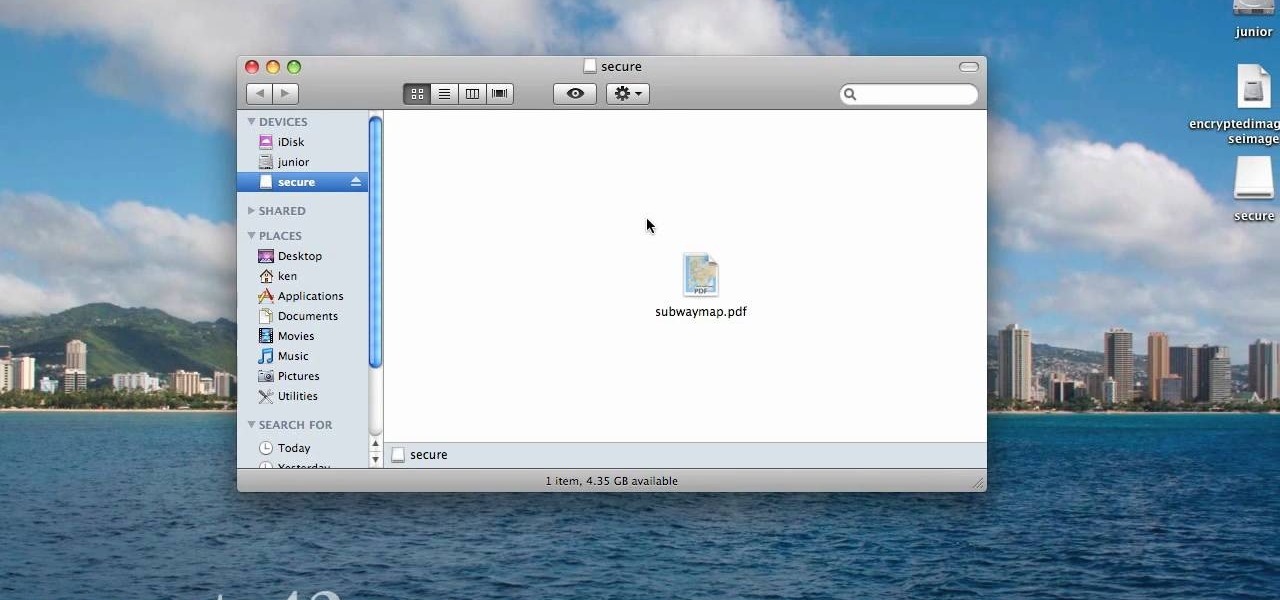
When you are sending any files over a network it is advised to encrypt it so that no can read it even if they get hold of it. You can encrypt files in Mac OS for this purpose. So first take any file or program that you want to encrypt. Open your hard disk and go to the applications. In the applications, under utilities open the Disk Utility program. Using this disk utility program you can create an encrypted disk image. Now this image will act as a disk image or other flash drive, but we can ...

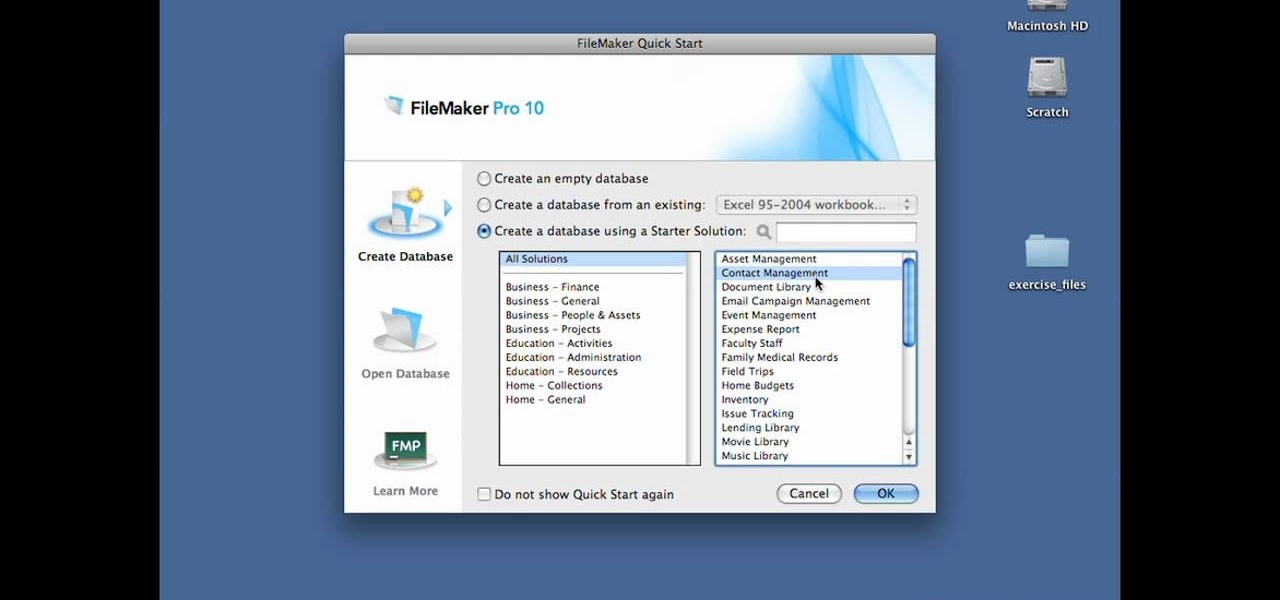
In this Lynda video tutorial, learn how to use FileMaker Pro 10 software to create databases with pre-made templates. FileMaker offers these templates in a package called Starter Solutions. To access these options, click open FileMaker. Then, go to New Database under the File menu. Click the option "Create a database using a Starter Solution." The templates are grouped according to the nature of their use. Some are for the home, while some are for business. All you do is open the template you...

This video tutorial instructs you on what a key logger is and how to make a key logger which records your computers key strokes for later review. There are software or hardware based key loggers that intercept the connection between the keyboard and computer. Hardware key loggers consists of a micro controller for data logging. Software key logger is a script that runs in the background then processes and saves the key strokes to a text file. To make a key logger you'll need to know a program...

New to Windows? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to protect Windows from viruses without an antivirus software.

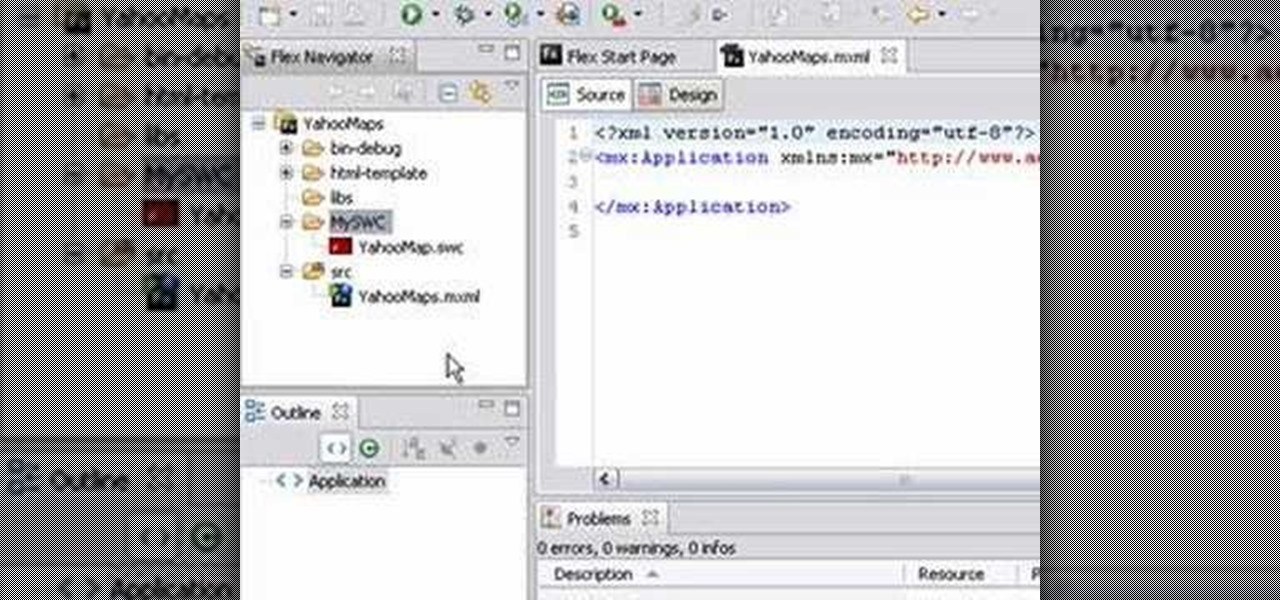
This video tutorial series shows you how to use the Yahoo Maps AS3 API in Adobe Flex 3. This new API gives you the ability to place Yahoo maps directly into Adobe Flex 3. Mike Lively Director of Instructional Design at Northern Kentucky University will be taking you through this tutorial.

This is a very simply process. Pick any app and press down on it. Soon an X will appear in the upper left hand corner. All Iphones have certain default apps, which cannot be removed. These apps will not get an X. The apps will start vibrating. Decide which apps you want to remove and touch the X. You will get a message saying that the certain app is being deleted, as is all of the apps data. The message will say "delete" or "cancel". Once you hit delete you will get a message, which will ask ...