Living in Los Angeles so long has perhaps spoiled me a bit. The only time I check my weather apps is to send screenshots of my 70 degree Decembers to my friends in Chicago and New York. So for these bragging occasions, I like to have a good looking app.

Just days after news spread that Snapchat could be exploited by spammers, an anonymous group of hackers have released the private information of over 4 million users of the popular photo-sharing application.
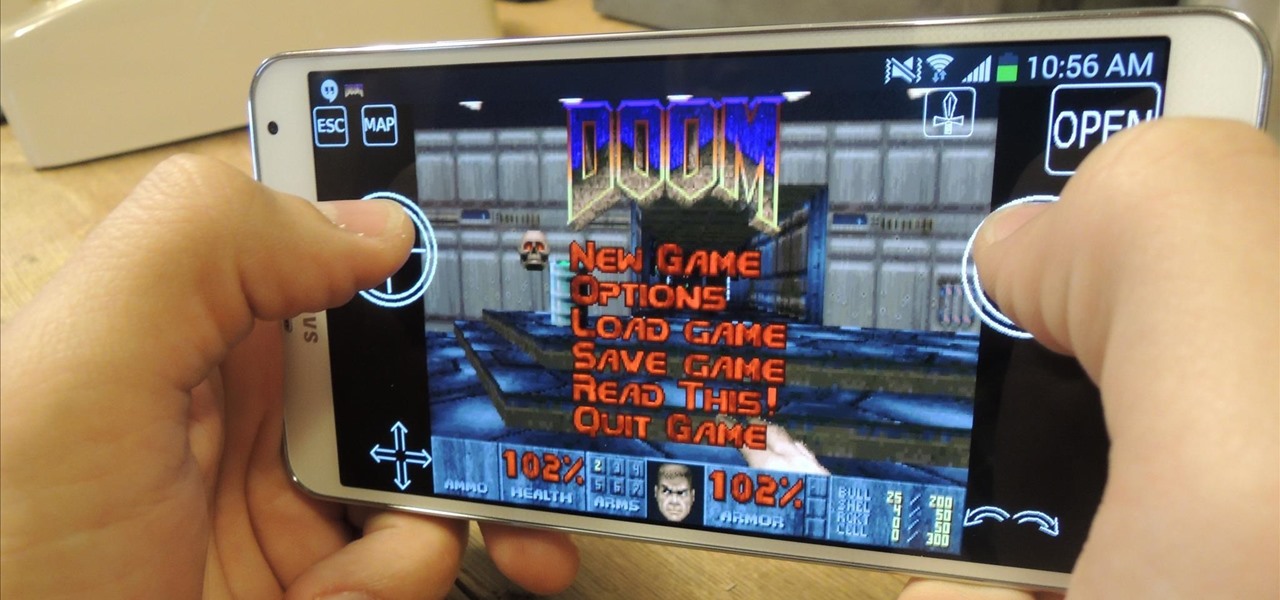
In the wake of its 20th anniversary, the folks over at Eltechs have released Original DOOM, a full shareware version of the revolutionary first-person shooter DOOM for Android, available for free on the Google Play Store. It's unmodded and unaltered from the original FPS classic.

The internet was ablaze this week after it was found out that evasi0n's newest jailbreak for iOS 7 secretly came bundled with a highly obfuscated Chinese app store. The application, called Taig, was filled with pirated software and was rumored to have permissions capable of tracking your information and sending it elsewhere. It was reported that the team at evad3rs financially benefited from this move, netting them a very high six-figure number close to a million dollars. The controversy incr...

If you're marginally inclined towards computers, you've probably been approached at some point by a family member who wants you to "fix" their system during a visit home. With the holidays coming up, these opportunities (or ambushes) are even more likely.
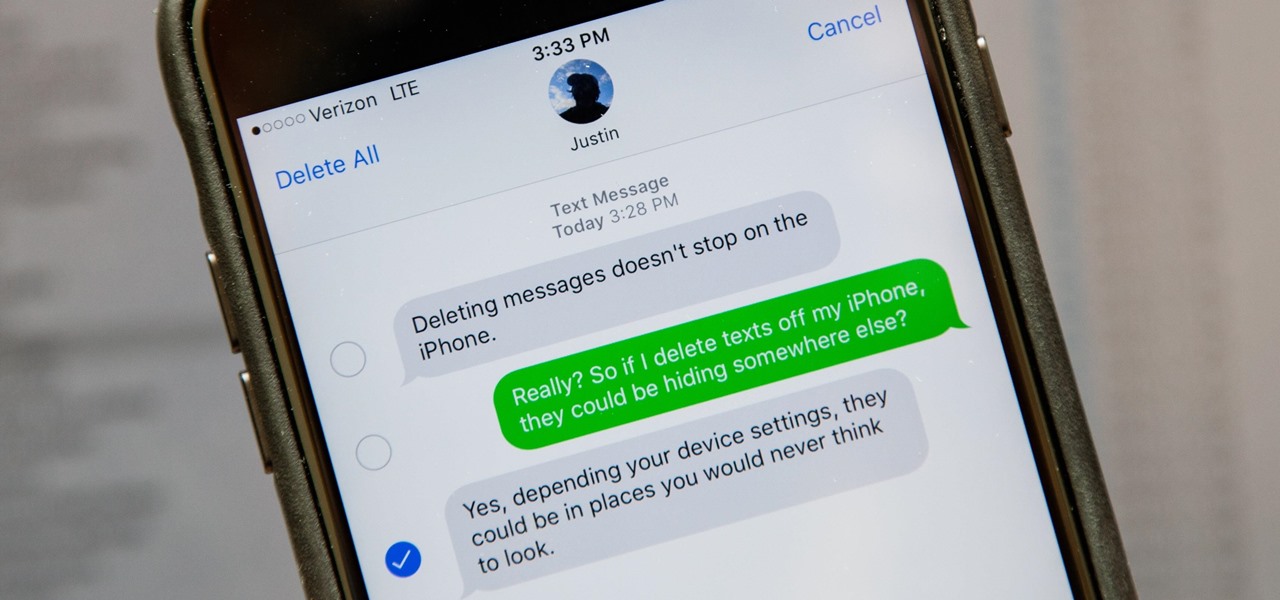
Deleting text messages on your iPhone may seem like a pretty simple task, but it's those really simple tasks that usually end up causing headaches later on. Data can stick around, even if you asked it not to, so there's always a slight chance that embarrassing and incriminating texts you supposedly deleted may end up in the wrong hands one day.

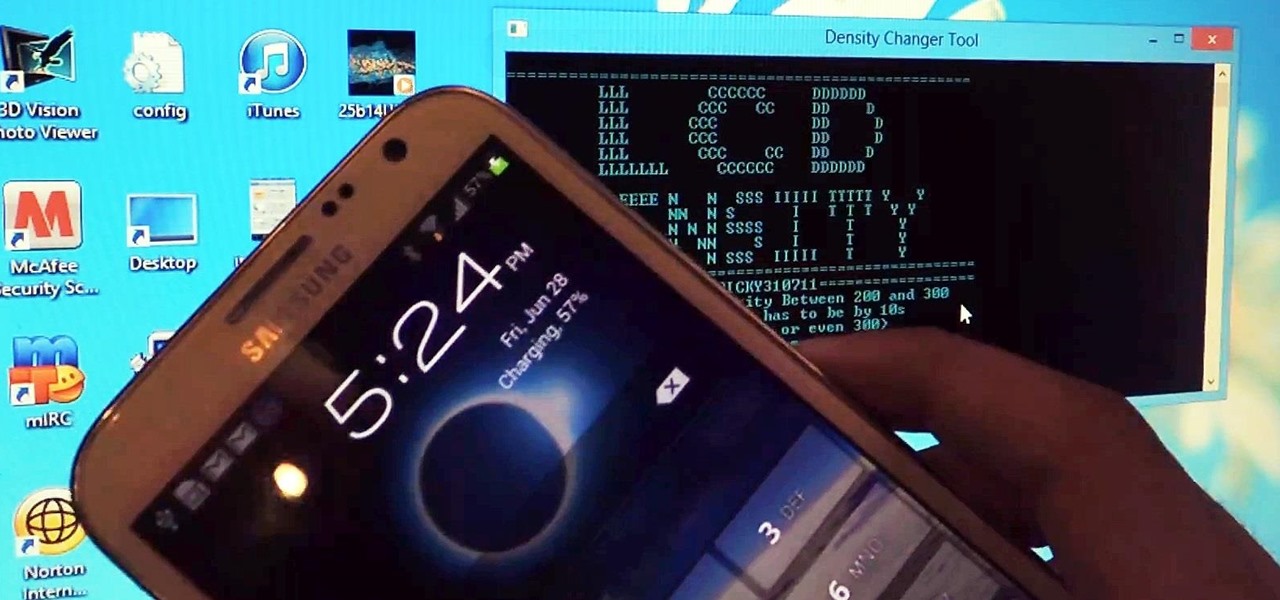
There are a ton of cool features available on your Samsung Galaxy Note 2, but if you're a softModder, you can make your phone do just about anything.
There has been much talk about how unsecure the cloud is because of PRISM’s newfound ability to demand all of your data without any resistance. This has spin doctors in the Cloud Storage industry losing their mind. They suddenly went from a central hub for 10GB of your files, to an easy window for Big Brother to track you through. Centralized cloud storage is no longer a safe way to keep your files, but we still need a way to access our files anywhere we go.

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

While the phenomena of viral videos and internet celebrities are relatively new, it seems like there's a new one every other day. Sometimes they're funny, other times they have a social mission, like Kony 2012, and sometimes they're just videos of cats jumping in boxes.

These days, there is hardly a place in America that doesn't have access to the internet. But with web usage fees and ridiculous cell phone provider contracts, sometimes it's still necessary to go a little DIY when it comes to staying connected.

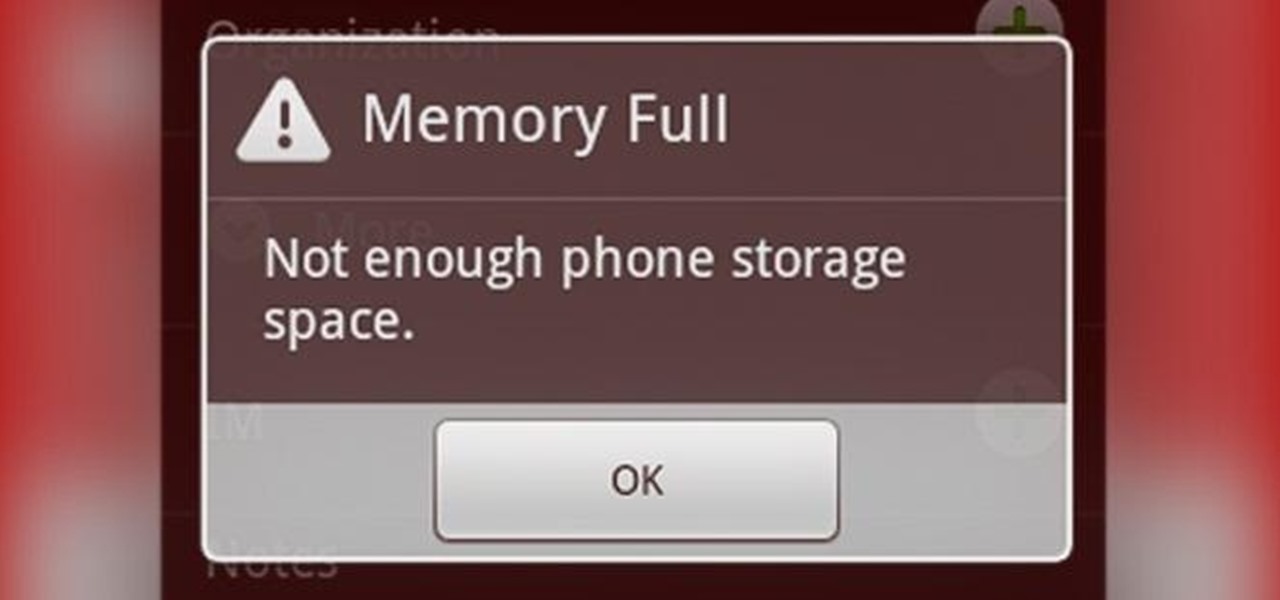
There is no such thing as too much space when it comes to our smartphones. Space is the great equalizer of all things. No matter how many awesome features a device has, the amount of storage space available will always be a determining factor. Be it music, apps or photos, it's easy to fill up your phone's memory fast.

While the increasing superiority of smartphone cameras is great, they can be a double-edged sword. Sure, we get great images that are crystal clear, but at what price? Storage space on your devices ends up paying the price for this luxury, filling up quickly due to the high-quality images and their grotesquely large size. Not only that, but most photo editing applications only make it worse. Adding a few filters, changing the hue/saturation, or adding some text across the picture can all incr...

When we think of search it's usually in regards to the internet. But when you are using a smartphone, searching your device itself can be just as important and useful.

If you don't have a car, or just prefer to take public transit to work, you know that an unexpected change in the weather can quickly...er, dampen your day. If you're not expecting it, rain or snow can turn your trip into a long, hellish ordeal—especially if you bike.

For the majority of my math classes in middle and high school, a graphing calculator was a must. While the calculators were very useful to have, they were quite steep in the price column. After losing the TI-83 graphing calculator my parents bought me in high school, I had to save up my own money to buy the next one.

I love YouTube for listening to music I don't already have on my phone or in my iTunes library, but there is one very simple thing that you think they would've figured out by now—the ability to have your video continue to play outside of the app!

A lot of people text nonstop, but there are situations where it's either not allowed or considered rude to use your phone. Let's say you're in class or in a meeting at work, band you're expecting an important message or phone call. Rather than trying to check your phone discreetly, wouldn't it be better if you could just see your calls and messages on your computer?

A few weeks ago, Twitter announced that they would be creating an archive feature for its members, which they've been slowly rolling out to select users. After signing in today, I noticed the feature was finally available for my account, so I went to test it out.

Some people hate cold weather, but there are also plenty of things to look forward to in the wintertime. The holidays, building awesome snow sculptures (or igloos), and hot chocolate, to name a few. But with all the good also comes one gigantic downside—more people get sick during the winter than any other time of year.

Facebook has been revamping its Messenger apps these past few months, trying to lure in more users. Competing in an already crowded market of third-party messaging applications, Facebook Messenger just upped the ante, by introducing voice messaging.

I use Google Chrome every day for my browsing needs, and I had no idea they were hiding something from me. So, I was pretty surprised to see that Chrome has an entire hidden experimental add-ons section. There are add-ons that work for Mac, Windows, Linux, and Chrome OS, so there's something for everybody.

In the Windows 8 Enterprise edition, you can use the Windows to Go feature to travel with Windows 8 OS, personal files, documents, settings and many more. All you need is an external hard drive or USB drive of 32 GB space or more and USB 3.0 support or more for fast Windows 8 booting. We need the storage media of above specification to create bootable USB to access the data anytime by plugging the media into different PC running latest version of Windows 8 PRO or Windows 7.

The Samsung Galaxy S III is undoubtedly a great phone, but still has some minor issues to work out.

There is nothing worst then having to wait for something you really want. It doesn't matter how old you are or what the item is, the fact that you have to wait for it makes you want it even more. It's the love-hate relationship I have with Amazon and anything I order, and when that anticipation is for a new smartphone, it's amplified by about a thousand. The LG Nexus 4 has received great reviews and is one of the most sought after phones this holiday season, but it's a hard one to get a hold ...

A few weeks ago, Facebook published a blog post called "Proposed Updates to our Governing Documents," which outlines a few changes in their policies and user voting system. These changes would essentially take away users' right to vote on future changes to Facebook's data use policy while also taking away Facebook's responsibility to alert users of those changes. If the new policy is enacted, the vote will be replaced with "a system that leads to more meaningful feedback and engagement," what...

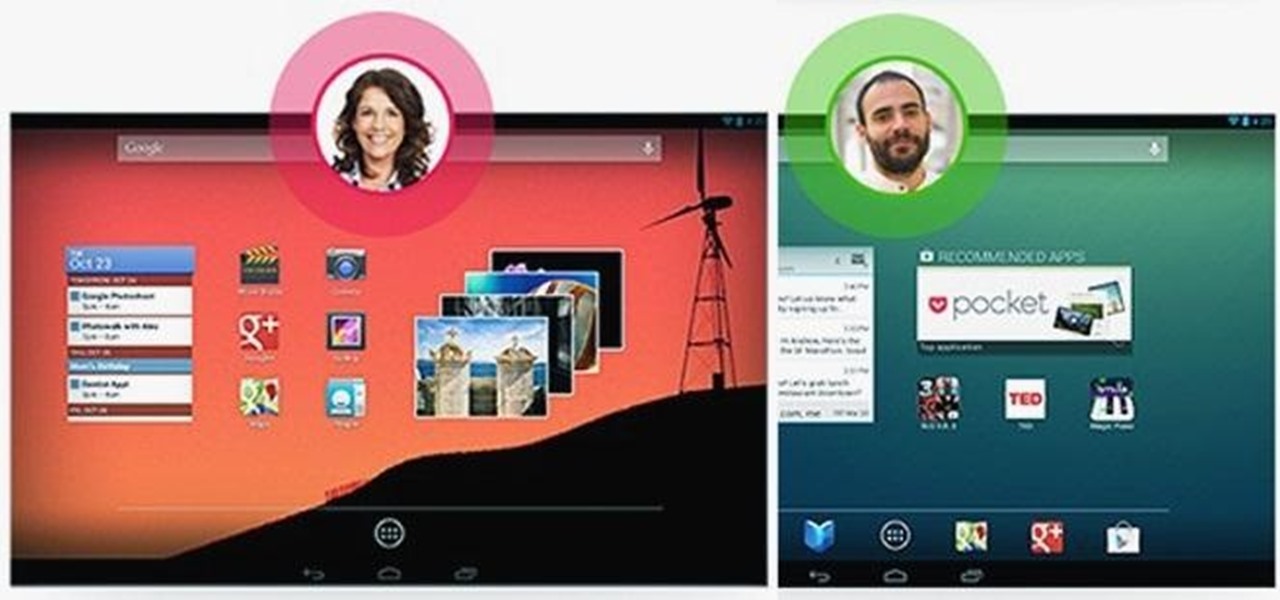
The most recent update for Android's Jelly Bean has some pretty cool new features, like better panoramic photos, gesture typing, and wireless sharing. From a security standpoint, though, the best new feature is the ability to add multiple users to one device. You can create up to 8 different accounts on Android tablets like the Nexus 7 or Nexus 10, so besides saving time hiding or protecting sensitive data, it could also save you some money. You can share a device with your family, kids, or s...

If you have the international version of the Samsung Galaxy S2 (I9100) and are sick and tired of waiting for the Jelly Bean update to hit your device, you're in luck—XDA-Developers member izap has leaked what appears to be the final version of Android 4.1.2 for the S2.

Whether it's forgetting your driver's license or misplacing your cell phone, forgetting things at home can be a pain in the butt. Car keys, wallet, purse, papers, sunglasses—the list can go on. Sometimes I even surprise myself at the important things I forget... Oops.

Have a super secret spy communication you'd like to send out, but don't have the funds to hire your own trusted operatives to deliver the message? Then stick to what you're used to—email it. SafeGmail is a browser extension that allows you to send encrypted emails right through your regular Gmail account. While this may seem a bit unnecessary for most messages, encrypting your email can definitely be useful.

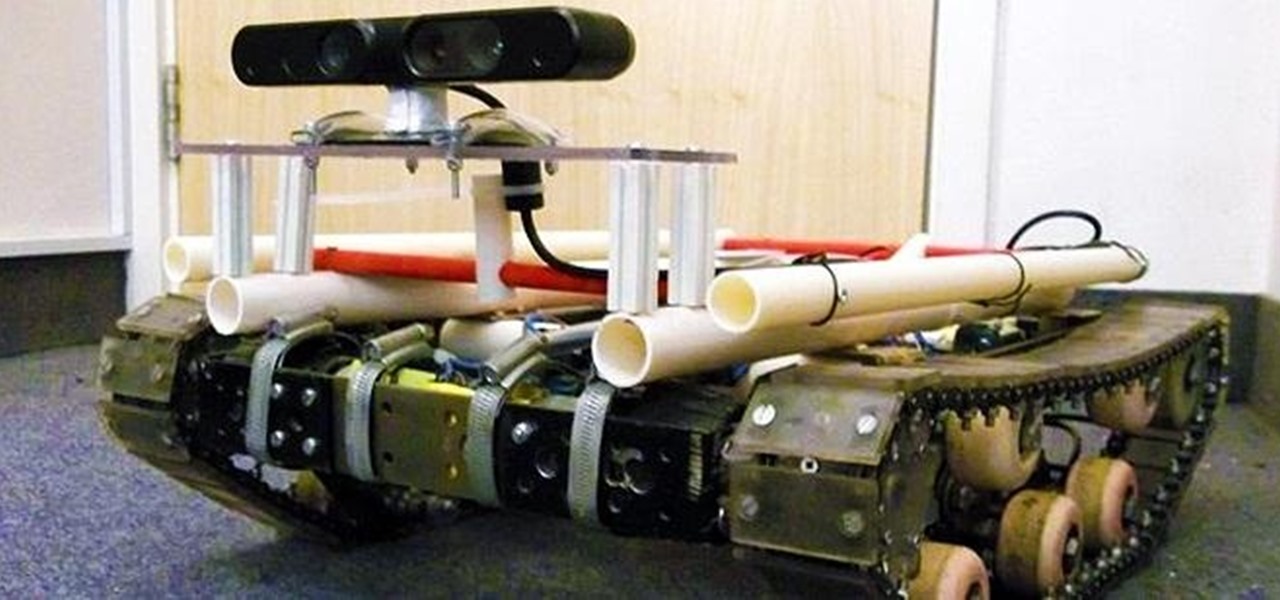
There are plenty of tank robots out there, but how many of them can recognize 3D objects and map their environment? Tanky, the tracked mobile robot, can do all that and more while rolling around on his bicycle chain treads. Created as a Master's thesis project, Tanky is made almost entirely of parts you can find at your local hardware store. It was built in two "layers" with the motors, electronics, and batteries on bottom and the processing unit, a laptop, on top. The motors came from cordle...

A hidden feature residing in Mac OS X Mountain Lion is the ability to view and also reply to your friend's tweets through the Contacts application, previously known as Address Book. The only way to do this, though, is to provide your Twitter account login data to the Contacts app. To integrate your Twitter, just go to System Preferences, then click on Mail, Contacts & Calendars and choose Twitter. Put in your Twitter login information and then click on Update Contacts. Twitter will use your e...

It seems like every other day there's a new security threat or data leak in the news. Whether it's your credit card PIN or your smartphone's apps leaking your email address, no one wants their personal information out there, especially passwords. And if you use the same email address and/or password for more than one site, the effects of someone getting hold of your credentials can be catastrophic.

Even though iOS 6 has only been out for a day, the folks over at iPhone Dev-Team have already released a Redsn0w jailbreak that works on the iPhone 4, iPhone 3GS, and iPod touch (fourth generation). As of right now, there's only a tethered jailbreak available, which means that you'll have to connect your device to your computer every time you power it up, but an untethered version that works on more devices is more than likely on the way. Until then, tethered is better than nothing, so here's...

Want to take advantage of your neighbor's super fast Wi-Fi connection? If they're smart, they probably have it password protected (otherwise you wouldn't be reading this, would you?). But if you have an Android phone, you can get back at them for always parking in your spot and slamming the door when they get home at 2 a.m.—by stealing...er, borrowing, their connection.

Windows users have been getting a lot of bad news about their security lately. First, we found out that passwords in Windows 7 and 8 can easily be exploited if password hints are enabled, and now, Russian password-cracking software developer Elcomsoft has found another huge vulnerability.

Since most devices these days are mobile and wireless, a lot of people have a bunch of old hardware from a decade or two ago sitting around unused, just wasting away in dusty boxes. Look familiar?

Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

As deeply as smartphones are integrated into our daily lives, it's no surprise that people are finding ways to use them to stay healthy. From detecting cancer and radiation to diagnosing STDs, phones have come a long way, baby.

Hello! I would like to share some data about the nests that rabbits and dwarf rabbits build. They represent good shelters for them and their babies.