
TypoGuy Explaining Anonymity: Secure Browsing Habits
to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?


to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?
Apple makes it easy to access your favorite and most recently used applications and documents in Mac OS X. You can simply add your favorite apps and folders to the dock, and you can always visit the Apple menu from the menu bar to see a list of your most recently used apps and docs.

Welcome back! In the last iteration of how to train your python, we talked about functions, and we even made our own! We're going to move on to more types of data arrays (much like lists) in today's discussion.

Windows 10 definitely has a sleek and modern look to it, but some of these visual changes have been made at the expense of functionality. For instance, the slider that appears when you click the volume icon in your notification tray now sports a completely minimalist look that lacks the quick link to the full volume mixer from past Windows versions.

In an article published in early-2015 by Peninsula Press, it was reported that the demand and the salaries for cyber security professionals are exploding! They cite that 209,000 cyber security jobs were unfilled last year, and that job postings have increased over 74% in the last 5 years. Job opening are expected to grow by another 53% over the next 3 years. You are definitely in the right field, my tenderfoot hackers! Some researchers are expecting information security jobs to continue to gr...

Hello, fellow hackers. I'm sure we've all seen it somewhere: the undying question of "How do I hack the game so-and-so?" And the answer usually is, "Come back when you actually know how to hack!" But how does one even go about "hacking" a game? What could that even mean?

Welcome Back !! TheGeeks. SQL Injection (SQLI) Part-1

Android Marshmallow was recently released, and as we've grown to expect, a root method was quickly made available to devices running the brand new operating system. Legendary root developer Chainfire has stated that he's working his way towards retiring from the scene, but he still had enough left in the tank to quickly publish an update to his popular SuperSU root method.

If you're entirely new to smartphones, Android's share menu can seem like a foreign concept at first glance. In reality, it's one of Android's most central and unique features, and with a little experience, it can make your smartphone a lot easier to use.
Uninstalling programs in Windows is not the nicest procedure. Some programs bundle a nice uninstaller with them which helps to ease the process. Other programs, mainly those that utilize the Windows Installer technology, begin the uninstall process right away. This can potentially be problematic for users who are trigger-happy with the mouse.
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.

Welcome back, my fledgling hackers! In this series, I am trying to develop your knowledge of digital forensics, which is valuable whether you're choosing a career in it or just want to know how your hacker activity can be traced. Few professional digital forensic investigators have a hacking background, but the best ones do.

People like to cite the iPhone as the device that started the smartphone craze, but the truth is, smartphones had existed for years by the time Apple got into the game. The real groundbreaking feature that this device brought to the table was a multi-touch screen to go along with its "smart" functionality, and this is still the main method we use to interact with our devices today.

Flashing people in an oversized trench coat is both old-fashioned and exhausting (and also very illegal). But like the evolution from school-yard bullying to cyber-bullying, it seems as if the new trend is "cyber-flashing" (it's even has an official hashtag). In the U.K., police are now investigating what they are calling the first cyber-flashing case.
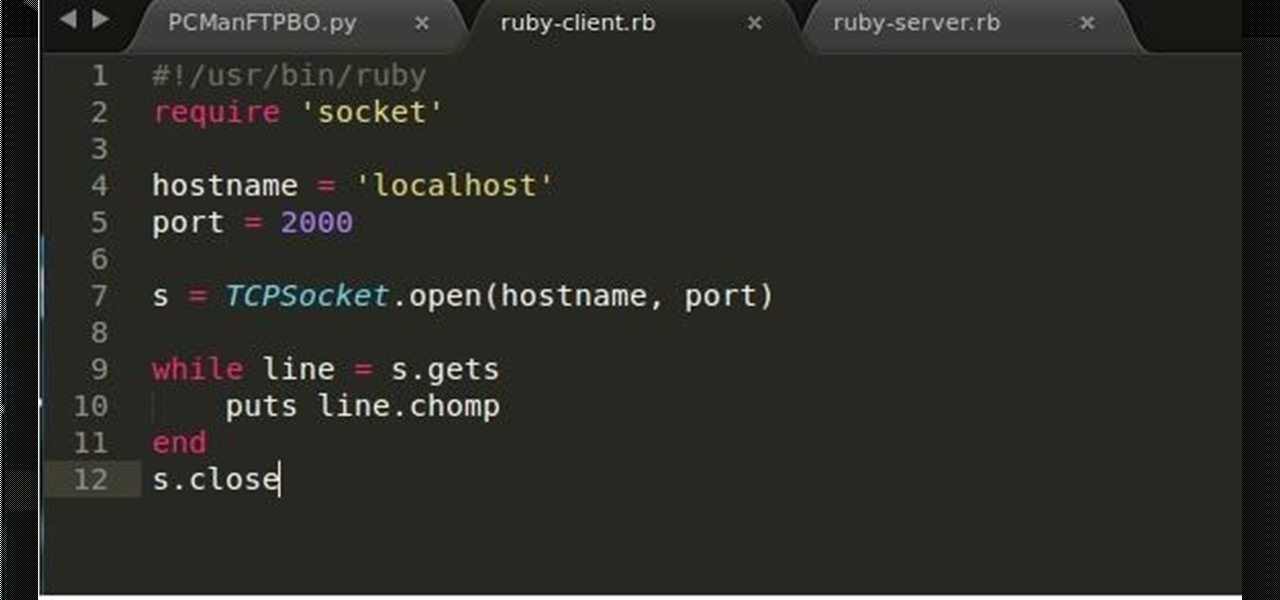
Recently, I've been learning Ruby as a second scripting language. But one topic I never covered with the many lessons online were sockets. So I did some research and came up with a very simple client/server connection that sends a string over the socket.

From day to day, it can be difficult to remember everything that's required of you. I tend to forget exactly where it is I'm supposed to be during my busiest moments, and it's even easier to delete each day's events out of your brain when there's so much else that dominates your mind. Yet taking the time to remember exactly what it is that happens during each of our days can be a vital part of our memory—and with nothing more than 15 minutes, we can strengthen our brains and remember more tha...

SET is great when you have a short space of time at hand, however sometimes you want to know whats actually going on under the hood or have found a site you can't clone with SET.
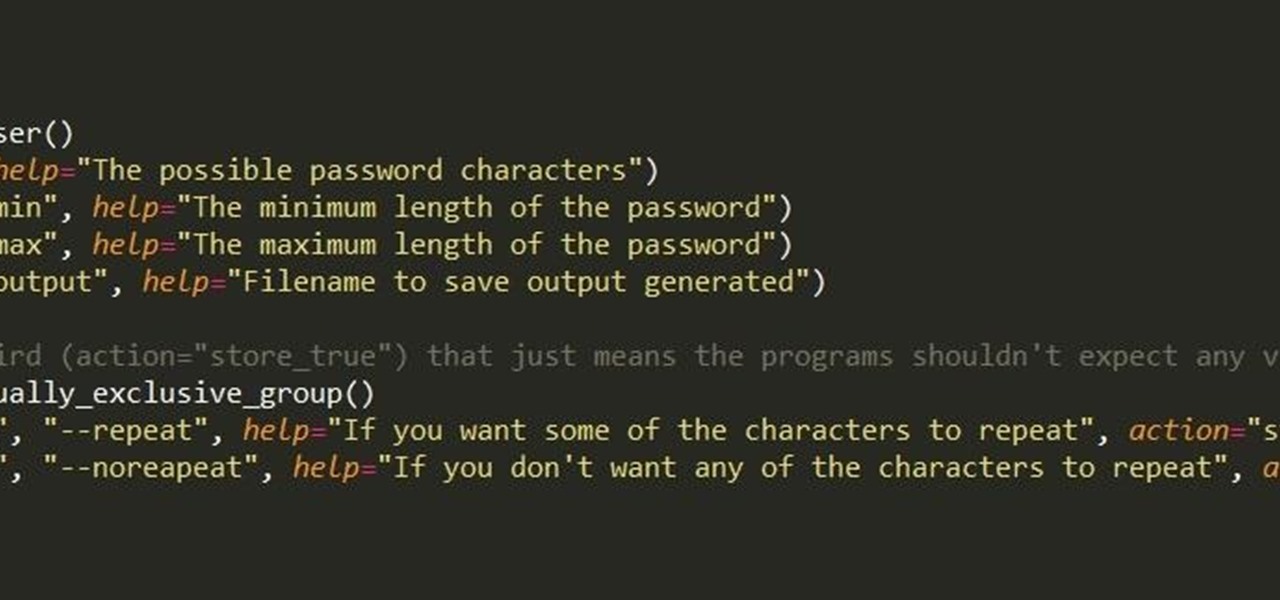
First of all, I hope the title makes sense. :D Well, this is basically creating a program that can help with dictionary attacks. Generate possible passwords. It pretty much lies in you knowing the person you want to hack.

Last year, Apple debuted a feature that allows families to share iTunes and App Store purchases across their various accounts. Us Android users, on the other hand, have to buy separate copies of apps for each of our accounts—well, at least from an official standpoint.
Welcome back, my hacking friends. We use our smartphones every day, for business, socialization, and leisure. The number of iPhone users is increasing in dozens of millions every year, with a whopping 63.2 million users in 2014 alone. That's a lot of users.

These days, there is no shortage of ways to exchange files to and from friends and family: text messages, email, Bluetooth transfer, and cloud services are just a tiny sliver of what you can use to share music, photos, videos, and more.

Before I start this tutorial, no, this is not that "Effective. Power." text that is going around. With that being said, let's talk about this attack.

On Thursday morning, May 28th, Google announced an upcoming version of Android—and within a few hours, a preview build of this so-called "Android M" release was made available to select Nexus devices.

Google's Chrome browser is evolving into a very powerful platform. Not only can it be used to view your favorite website or mirror tabs to your Chromecast, but now that it has an App Engine, more powerful tools can be run within Chrome.

As the developer behind the most popular root methods for hundreds of Android devices, Chainfire knows the ins and outs of Android root procedures. But this doesn't mean he's infallible—occasionally, some of his root utilities can cause minor bugs.

Customization helps your device stand out from the rest, and that sentiment is no different when it comes to the Apple Watch. Unlike every other Apple device before it, the Watch allows you to customize the information that appears on the UI—without the need for any jailbreaking.

They might be a little late to the party, but the Cyanogen team has finally released their newest ROM for the OnePlus One, Cyanogen OS 12. The launch had to be pushed back a few times due to some technical issues, but now we finally get to see what the Cyanogen team has cooked up for Android Lollipop.

Video: . IF function

Sideloading apps on Android is incredibly easy—you just have to enable "Unknown sources" in your device's Security settings, then you're free to run an APK installer file to get the app installed.

With troves of sensitive information, like receipts and password reminders, hiding in your email, your inbox can become a sort of Holy Grail for hackers—or anyone with your password. Although my crazy ex-girlfriend had no hacking experience, using my email login, she was able to find a lot of account information with just a general search for "password" in my inbox.

What Is IPython? IPython is a richly featured replacement for the standard python interpreter. It offers a wider range of functionality, that the standard

Today we are pleased to announce the end to the Apple vs. Android war. About a year ago, our Gadget Hacks team started working on a top-secret project to dual-boot both Android and iOS on the same phone—and we couldn't be more proud to announce that we've finally succeeded! Your phone can now run both iOS and Android—whenever you want. Right now.

Thanks to the strenuous efforts of our Gadget Hacks development team here at WonderHowTo, the fortified barrier segregating Android from iOS has finally fallen down.
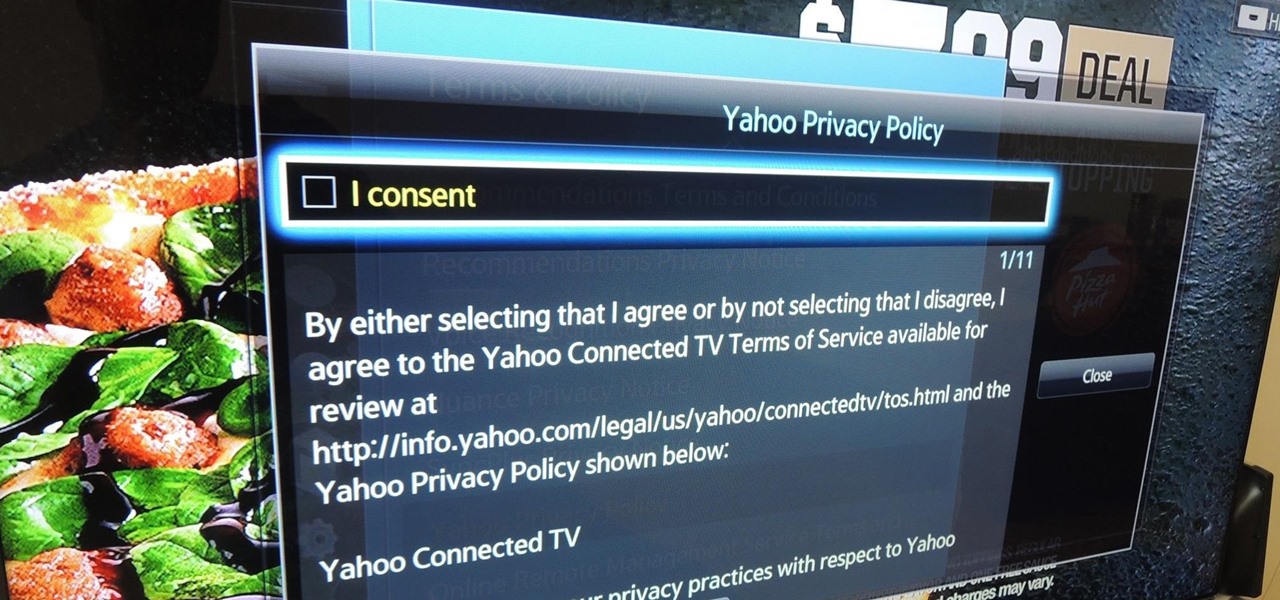
Televisions used to be great for just one thing—watching TV. But a more connected world brought with it Smart TVs, devices that can access the web, stream Netflix, and even mirror your smartphone's display. And with this level of connectivity, OEMs like Samsung saw it fit to place targeted and interactive ads on your screen.
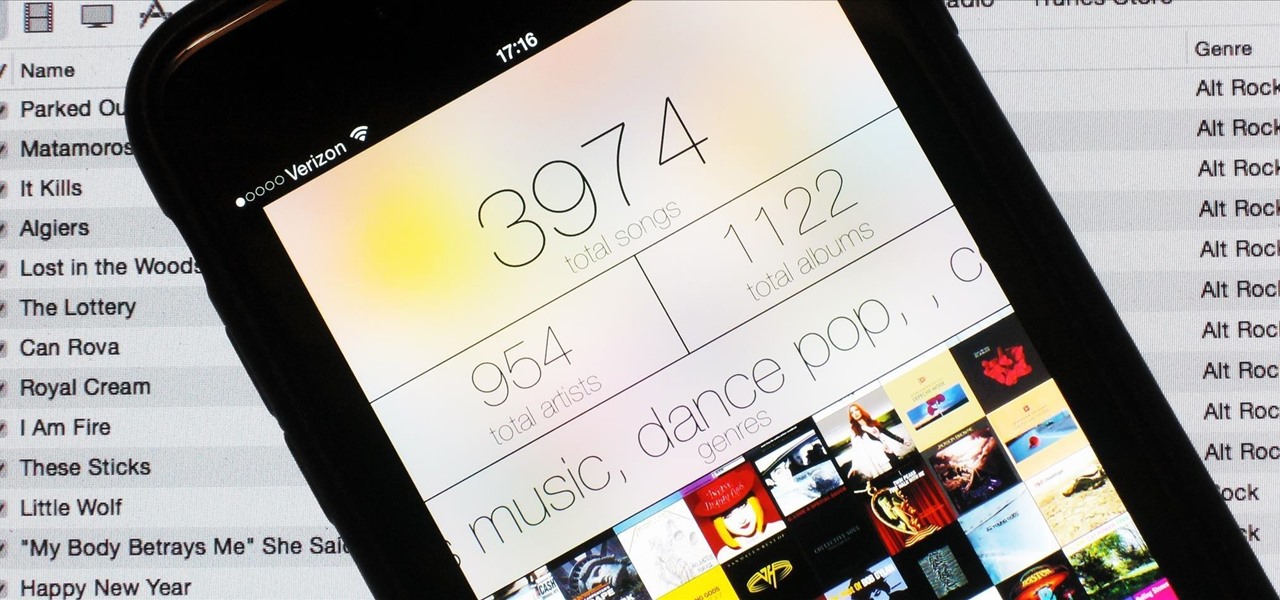
There are songs that we love, songs that make us sad, and songs that change the way we view the world—and that's something that Steve Jobs knew all too well.
Normally, if you want to close all of the open apps on your Mac, you'd have to either quit them all one by one or restart, shut down, or log out while making sure to deselect “Reopen windows when logging back in." The latter option is great, but it doesn't always work in Mac OS X, and what if you don't want to restart, shut down, or log out?

Super Bowl Sunday is just around the corner. With 111.5 million viewers tuning in last year (112.6 if you count streaming), which broke another record that it previously set for the most-watched television event in U.S. history, it's safe to say that most of us will be watching Super Bowl XLIX on February 1st, 2015, whether via TV, web, or mobile.

In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new users from across the world. Last year, we covered Sicher, a German app that lets you send and receive encrypted self-destructing messages on your smartphone.
Android Lollipop promises tons of new features and functionality when it comes to a device near you, but as we wait, it's almost painful to see the screenshots and demo videos from Nexus devices and how downright pretty the new operating system looks.

OnePlus changed the way we think about high-end phones. Their "Never Settle" motto led me to ditch my high-cost smartphone for their flagship One, which not only packs some pretty impressive hardware, but won't break the bank. Now that OnePlus has made a name for themselves with the One, they're trying their hands at ROMs, too.