Ever a hacker can have their own business that goes beyond cashing in on profitable bug bounties. With the right skill set and certifications, an ethical hacker could build a cybersecurity firm, become a penetration testing for hire, or even just consult on preventive measures to defend against black hats. But learning how to start and grow a business is rarely easy.

After leveraging the well-known intellectual property of Rovio's Angry Birds for its first game for the Magic Leap One, Resolution Games is singing a new song with a familiar refrain for its next game for the augmented reality headset.

The Force was awakened in many a household on Christmas morning this year, as evidenced by numerous recipients of newly unwrapped Star Wars: Jedi Challenges systems sharing their first lightsaber battles in augmented reality on social media.

In this tutorial, we see how to whistle loudly by putting your fingers in your mouth. First, place your two fingers from each hand into your mouth. You will use the middle and pointing fingers from each hand. Place your fingers underneath your tongue and hold the tongue back while you whistle. Push the tongue to the back of your mouth making a seal around your lips. Push air out of your mouth going out into the middle. This is the easiest way to make a loud whistle sound while just using a si...
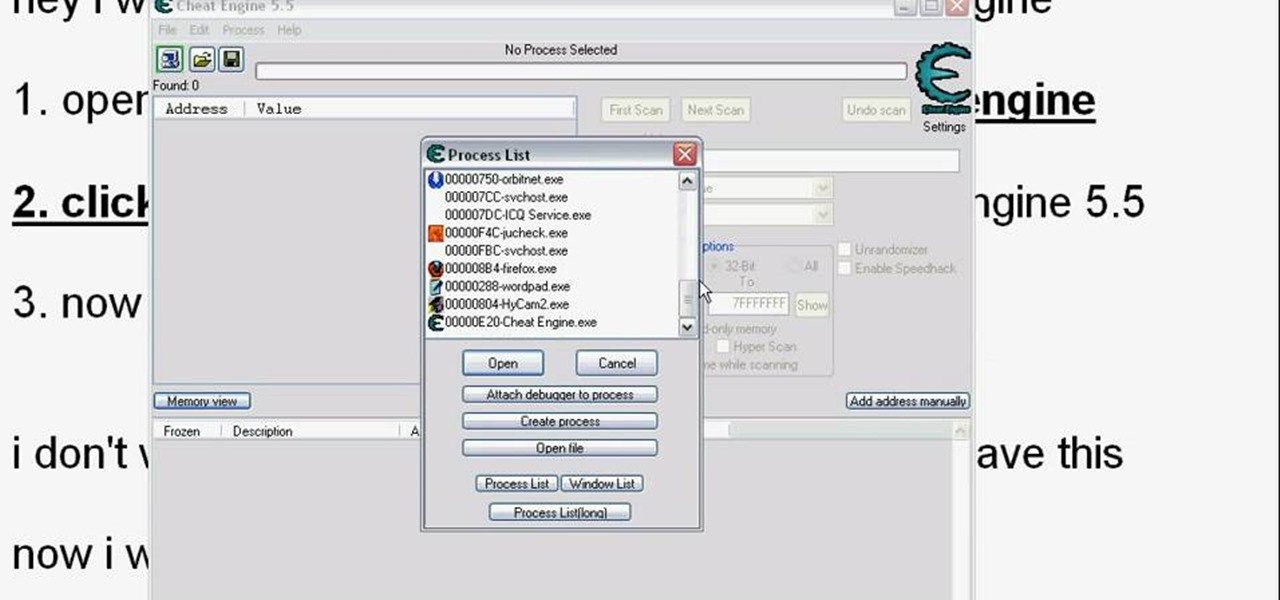
You're one step away from hacking your favorite flash game on the web. You're almost ready to start cheating Facebook games. You're just about ready to call yourself a hacker… but wait… where in the heck do you get this so-called hack app at? Cheat Engine. It's the mother of all hack programs. And the easiest way to find it is to Google it. It's the first result at the top. You just need to go to http://www.cheatengine.org or directly to the downloads section to download Cheat Engine 5.5 for ...

Chibi Itachi is quite the character. If you want to learn how to draw this "little" Chibi Itachi character, it's really quite simple. DragoArt has this video tutorial on how to draw Chibi Itachi. Get more detailed instructions on the step-by-step cartoon drawing here.

Learn how you can achieve this sexy black smokey eye look with this how to video. This makeup tutorial uses the following products: a matte black base (Blacktrack fluidline), a matte black powder eyeshadow (Carbon eyeshadow), a matte highlight that's similar to your skintone (Performance eyeshadow), another matte highlight that's similar to your skintone, but darker than the one before (Malt eyeshadow), a black eye kohl (Graphblack technakohl, Blacktrack fluidline) and [optionally] a shimmery...

With Adobe Photoshop on your computer, it's super easy to change or adjust the skin tone of somebody in a digital photo. The process uses some basic selection and color adjustment tools, and it's a fun way to make a friend's face nauseously green or lessen the effects of overly strong, sometimes even orange, makeup.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

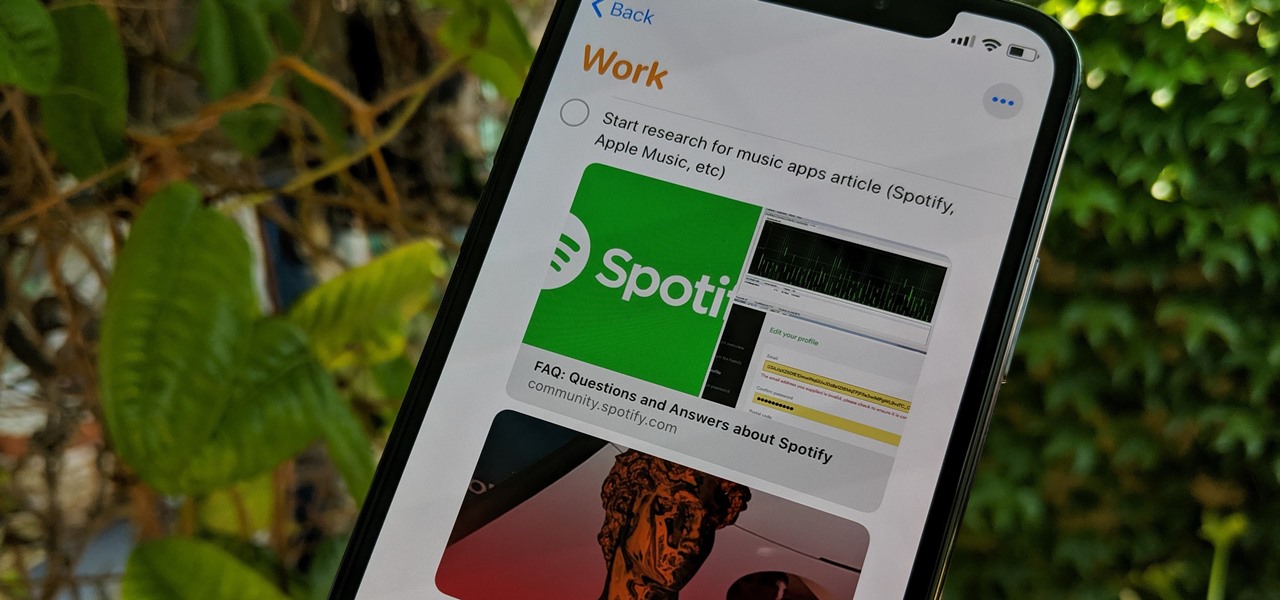
Apple's Reminders app has always been an underrated yet useful productivity tool for iPhone. It's not as powerful as many third-party to-do apps, but it makes it easy to keep track of a few basic tasks, and it's integrated deeply with iOS, macOS, and watchOS. In iOS 13, it's even better since you can now add attachments to your reminders, such as photos, documents, and webpages.

While the Galaxy S10 is a beautiful phone, its software isn't for everyone. One UI makes huge strides toward undoing the mess known as TouchWiz, but for purists, it's still not quite on par with stock Android. Fortunately, the beauty of Android is you can change this with a few apps.

The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

When flashing files through TWRP, ADB, or Fastboot, there's a slight chance for things to go wrong. Whether it's user error related or something else entirely, it's always good to have a backup plan. In most cases, you'll be dealing with a semi-brick or soft-brick, which can usually be solved by wiping the data of the device using TWRP. However, it can be more severe than that in some cases.

Although the Essential PH-1 got off to a rocky start, thanks to steady updates, it has slowly become one of the best Android phones to come out in recent years. For $499, the Essential Phone is a cheaper Pixel, receiving updates almost as soon as the Pixel lineup does. What's more, you get a phone with an easily unlockable bootloader, which is the first step to rooting.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

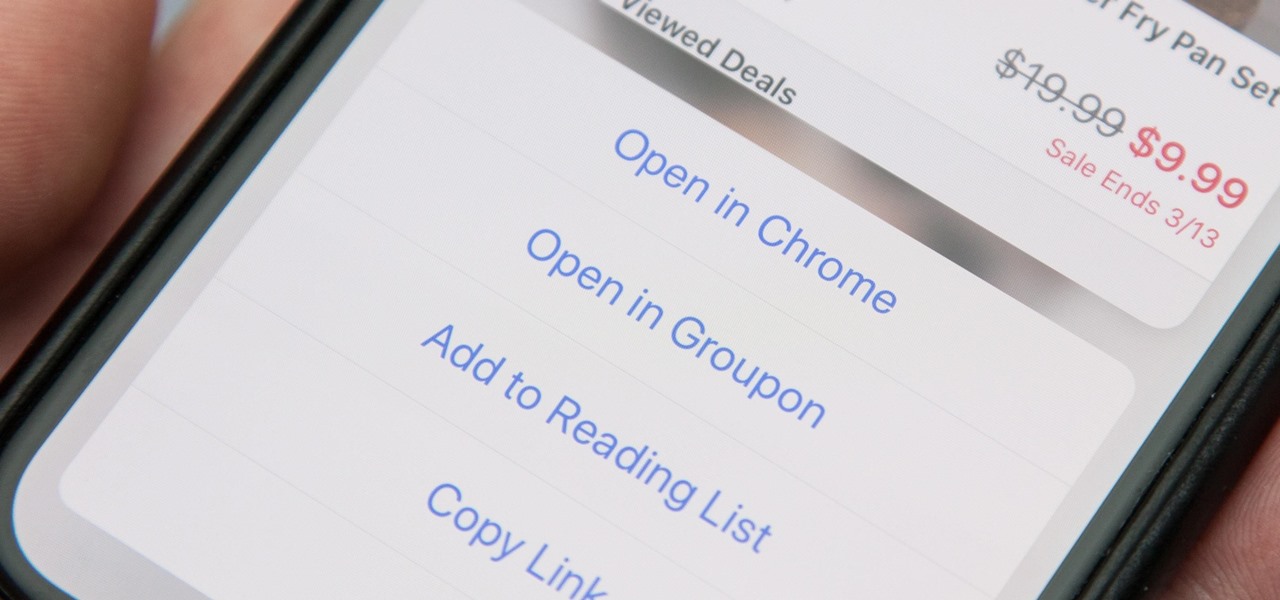
When you tap on a URL link in a text, email, or wherever, your iPhone's default reaction will be to open it up in Safari, and there's no way to change this in the settings. However, there is a way you can work around this to open up links in Chrome instead. Even if you accidentally open a link in Safari, there's a quick way to jump the tab right into Chrome.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

Ah, butter—the (literally) heart-stopping star of the dairy world. Everything tastes better with it, from pie crusts and cookies to veggies and steaks. Hell, you can even fry things in butter if you want the best-tasting fried foods of your (short) life.

With Passover soon upon us, many Jews are dreading a week (or eight days for Conservative and Orthodox Jews) of making matzo, the staple of their diet. Matzo is also known as "the bread of affliction," and I'm pretty sure it's because by day three or so you're convinced that matzo is the 11th plague.

Hands down, chips and dip are the best entertainment foods to ever exist. This fact can be confirmed in an instant by any grocery shopper strolling down the chip isle on Super Bowl Sunday or New Year's Eve. However, you may want to hold off on buying those standard salsas or dips at the store—especially if you own a food processor.

If you've spent any time at all recently on social media, then you've probably seen pictures of fairy bread. This magical creation comes to us courtesy of Australia, so we have yet another thing to thank those clever folks Down Under for... along with shrimp on the barbie, Vegemite (the Aussie cousin of Marmite), and Hugh Jackman.

I've never had a problem with veggies—we've always been the best of friends—but I do have a lot of other people in my life that have been less than enamored with this basic food group in the past. Some cite the bitter flavor associated with veggies like Brussels sprouts, while others dislike the various consistencies that come with boiling or steaming vegetables such as broccoli or eggplant.

We spend over 30 percent of our lifetimes sleeping—yet it never seems like enough, does it? Distractions ranging from work issues to personal relationships keep our minds racing well after they should be shutting down for the night, and the onset of smartphones has only added to this problem with the instant information and easy entertainment that they offer.

Downloading YouTube videos for offline use to watch later has always been a problematic endeavor. Dedicated third-party apps don't last long in the App Store, web-based converters aren't very functional on mobile, and rogue apps outside the App Store are tricky to sideload and open up the possibility of vulnerabilities. But that doesn't mean you still don't have a few good options.

Unruly customers. Crazy exes. Horrible bosses. When you need proof of insanity or just want it for your records, recording a phone call is a must. Problem is, it's not the easiest thing to do on an iPhone — but it's completely possible.

Whether you're just getting your first Android, or are already on your fifth annual cycle of picking up the latest flagship, there is always the question of what to do after booting up your device for the first time.
As a hacker or an aspiring one, You need to be careful and anonymous if your doing anything illegal. But you slipped up. Now someone is tracking you! Well luckily you read this post ahead of time and have a backup plan!

Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, online, Wi-Fi, Linux, and even SNMP passwords. This series is intended to help you hone your skills in each of these areas and expand into some, as yet, untouched areas.

With a root bounty of over $18,000 up for the taking, developers were highly motivated to get the AT&T and Verizon Wireless variants of the Samsung Galaxy S5 rooted. Legendary hacker George Hotz, aka Geohot, has won the race and can now step up to claim his prize.

Just because you have a Mac doesn't mean you can't root your Nexus 7 tablet. In fact, rooting Android 4.4 KitKat on both the 2013 and original 2012 N7 models is easy, if not easier than rooting it using a Windows PC.

It's officially the holiday season, which means everyone will soon be traveling home to spend time with loved ones. And anyone who has any knowledge whatsoever of computers knows what else that means—family members left and right asking you to fix their various technical woes.

There are definitely some great things about iOS 7, but like any good piece of software, it's got some things to kink out—and how wallpapers work seems to be one of the biggest issues, since it's so much different than in previous iOS versions.

Roses make a nice garnish for any pastry - cakes, cupcakes, pies.. Check out this video and learn how to make a rose from scratch using buttercream. This video shows you three different ways to make these delicious flowers. Watch the tutorial and decide which method is easiest for you. And don't worry if you can't get it on the first try..the mistakes are just as yummy to clean up as the successes!

There is a reason why this little gadget is called a powerball. It gets its name because it exercises your wrist, fingers, and forearm.

There is a reason why this little gadget is called a powerball. It gets its name because it exercises your wrist, fingers, and forearm.

By now you're probably already an expert at creating cover images for your Facebook Timeline, especially if you've taken advantage of those free Facebook cards that were (and still are) being offered. But just in case you need some help making eye-grabbing cover images, there's a few tools you can try out to streamline the process.

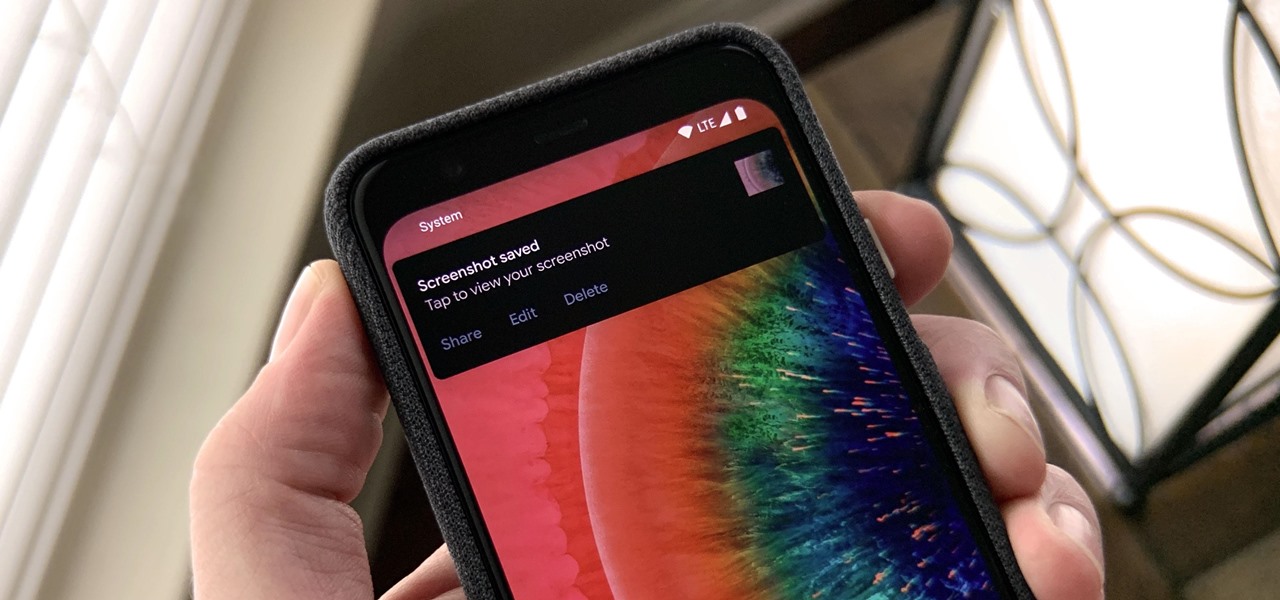
On stock Android 9 and 10, it is easier than ever to take a screenshot and quickly edit the captured image. However, the downside to that convenience has manifested itself in a heads-up notification that can also get in the way.

Best known for its mobile phones and television sets, South Korea's LG has had a quieter presence in the US compared to the country's homegrown efforts.

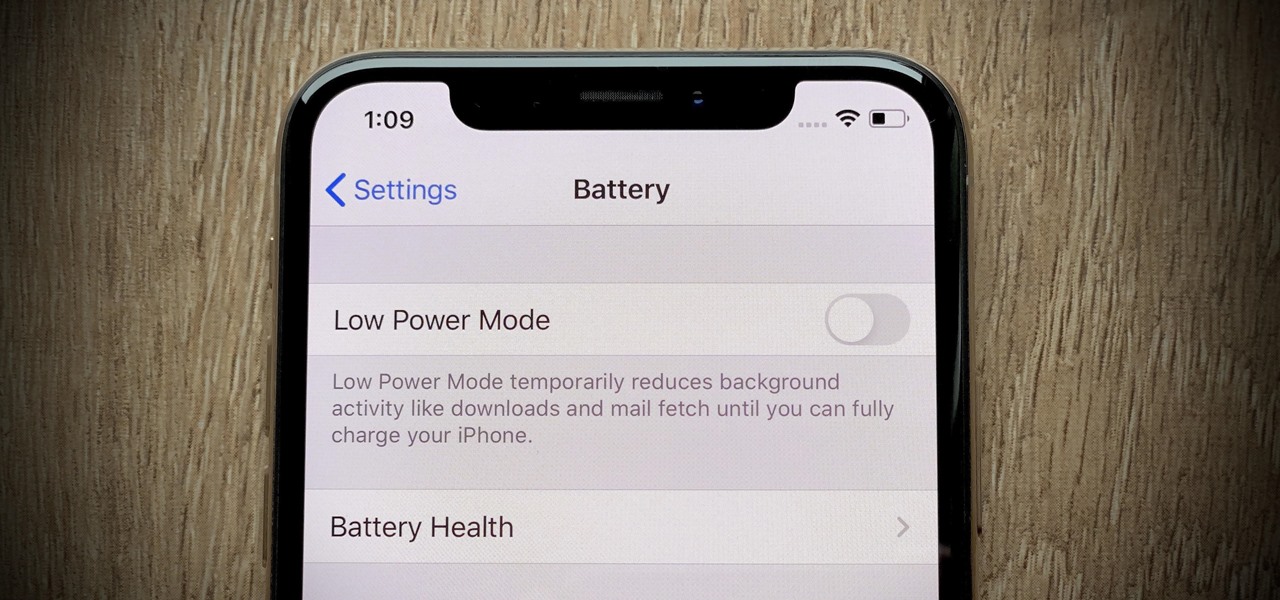
There are plenty of jokes out there about the battery indicator on iPhones. Some people complain about their iPhones dying randomly at 11%, while others see hours of use at the 1% mark. Despite its inconsistencies, that battery percentage is a useful tell for how desperate you need a charger. There's just one problem: the icon is hiding on your iPhone 11, 11 Pro, or 11 Pro Max.