Rascal Flatts are one of the biggest groups in country music, and their song "Bless the Broken Road" is a great uplifting ballad. Watch this video to learn how to play this relatively easy song on piano, then go out and play it. It'll probably bring some love you way.

Lots of designer purse companies, especially Coach and Kate Spade, LOVE attaching beaded charms to their purses and clutches. Sparkly little bits and pieces add extra pizazz to anything they're attached to.

Looking for an easy way to get around Kindle's sharing limitations? With the right technique, it's easy. So easy, in fact, that this how-to from the folks at CNET can present a complete overview of the process in just over a minute. For more information, including a complete demonstration detailed, step-by-step instructions, take a look.

Making fancy pool shots that send balls careening around the table may be impressive, but more often than not it's making short, easy shots consistently that will win you the game. This video will teach you an easy drill that you can use to improve your short-range cue control, which you can then use to set up combos and make sure you don't miss easy shots.
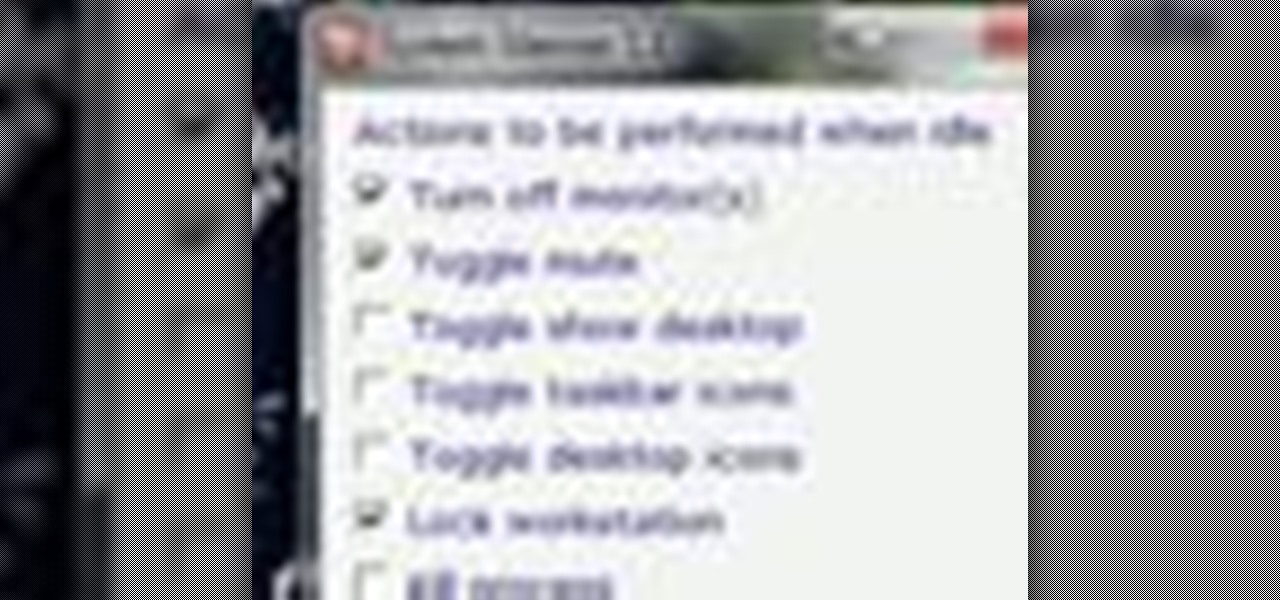
Wish there were an easy way to trigger a task when your computer goes idel? This clip will show you how it's done. It's easy! So easy, in fact, that this handy home-computing how-to from the folks at Tekzilla can present a complete overview of the process in about two minutes' time. For more information, including detailed, step-by-step instructions, take a look.

Looking for the perfect updo to wear to a formal event like a wedding or school dance? This video will show you how it's done! It's easy. So easy, in fact, that this clip can present a complete overview of the process in about ten minutes' time. For more information, including detailed, step-by-step instructions, take a look.

Livebearing fish consist of colorful little guys like guppies, mollies, platies, swordtails, and limias. These fish are great for children because they are easy to care for, can live in smaller tanks and have tons of easy to see babies.

Wish there were an easy way to protect one more browser cookies when sweeping out the rest? With the Selective Cookie Delete Firefox add-on it, it's easy! So easy, in fact, that this guide can present a complete overview of the extension and its various features in just over two minutes' time. Manage your cookies more effectively with this how-to.

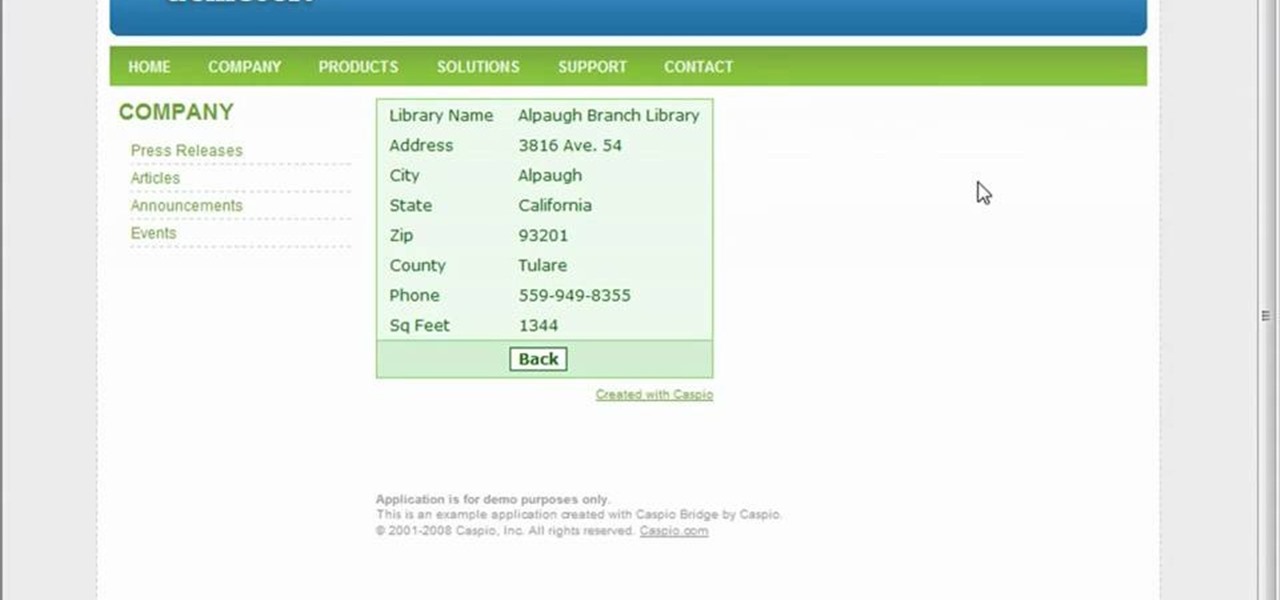
To start off the process of publishing your access database online we first look at a sample MS ACCESS database with typical formats and a online searchable application where users can search by library name or city and get details of the library. There are 3 steps to publish the database. The first step is importing data which can be done through clicking on the file menu and then click on import data through a Microsoft Access Database. Now select the file you want to import through the bro...

How to make simple and cute hairstyles; get professional tips and advice on methods, techniques, and products for doing your own hairstyling in this free beauty video series.

Sunny Anderson prepares tasty shrimp pot pie that's easy for anyone. Follow along for this easy to make real food shellfish recipe.

Want to play lead guitar in a rock band? Well first you have to learn techniques from the masters. This two part guitar lesson teaches you how to play the solo from "It's So Easy" by Buddy Holly on the guitar. Once you get a hang of these popular guitar chords and tunes, you can start incorporating them into your own songs. With this lesson and a bit of practice you will be able to play the solo from "It's So Easy" by Buddy Holly on the guitar. The next time you are with your friends you can ...

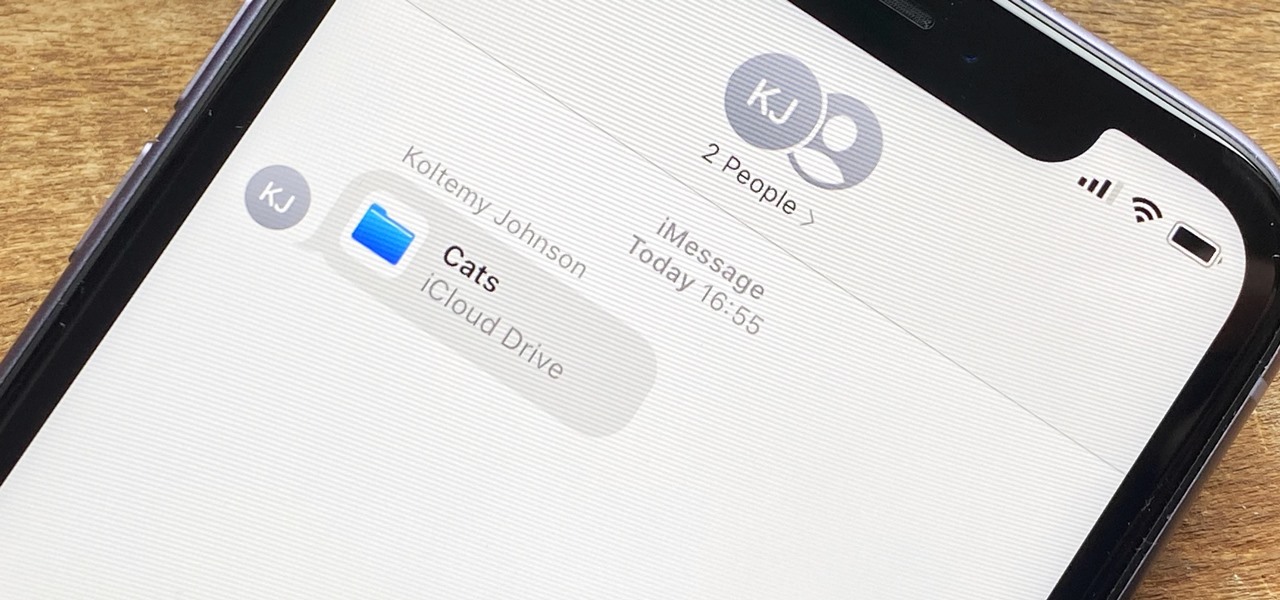
In the iOS 13.4 update, Apple added folder-sharing capabilities in the Files app. That means you can share multiple documents at the same time instead of doing it one by one. But that's not all — you can share folders with numerous contacts and even enforce access and permission settings.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

One of the most useful features of the Pixel Launcher is access to the Google Discover page. Initially, this feature was exclusive to Google's launchers, forcing users to give up the customization of apps like Action Launcher if they wanted the quick access to relevant news and updates it provided. Fortunately, this is no longer the case.

One of the main reasons Authy was able to top our list of the best two-factor authentications apps was its ability to transfer access to a new device. This feature ensures that whenever you get a new phone, you don't lose all your tokens. However, if the process is done incorrectly, you can leave your account vulnerable.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

Two-factor authentication (2FA) is a great way to add another layer of security to sensitive third-party apps and websites like Venmo. However, before iOS 12, to log into a particular 2FA-secured app or site on your iPhone, you'd have to memorize or copy the SMS code from Messages, then jump back in a timely manner to log in. Apple's latest iOS version streamlines this process.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

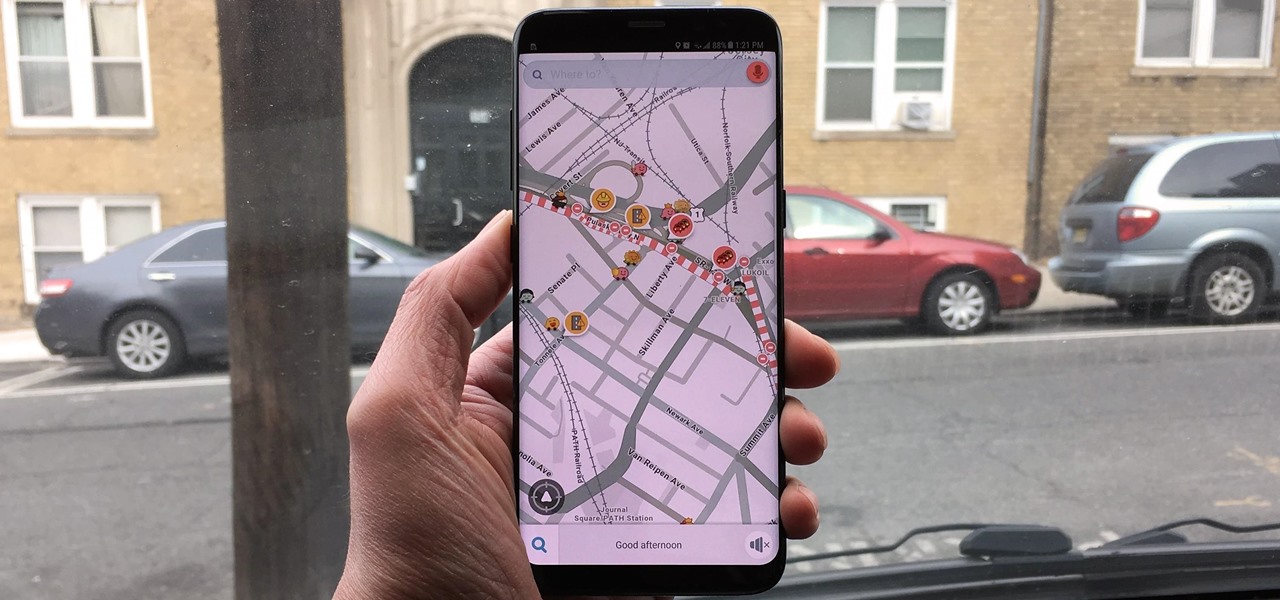
Because it sources a majority of its vital data from actual drivers on the road, Waze is easily one of the best navigation apps to use if you prioritize safety. Benefits such as crowd-sourced traffic data, police trap locations, and road work avoidance, when combined, help you anticipate traffic conditions with unprecedented accuracy and make adjustments accordingly.

Most of us have probably used a GIF at least once or twice to respond to a message, and that's why a lot of messaging services and keyboards have GIF search tools readily available to use. Now, Google wants to take GIF responses to a more personal level, by allowing you to create your own selfies GIFs to instantly sent to family and friends.

Using the Mail app to log in and sync to email services such as Gmail and Outlook is incredibly easy to accomplish on the iPhone thanks to the intuitive nature of its operating system. This is still evident with iOS 11, and though the process differs slightly from its predecessors, it can still be accomplished with relative ease.

Spotty cellular reception is a fact of life that we all have to deal with, especially when you're traveling. For those of us who rely on our smartphones for navigation, driving through areas with bad mobile data service can be a cause for major headaches.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

If you're a parent of a toddler (or have a friend that acts like a toddler), you occasionally need to take a break just to preserve your mental health. The perfect way to buy yourself some "me time" in this scenario would be to pull up an episode of Dora the Explorer on Netflix or YouTube, then hand your phone or tablet over to your child (or child-like friend) and try your best to relax while they're occupied.

It seems like a new, dangerous Android exploit is uncovered every month or two. The latest headliners are NightMonkey and Chronos from the list of CIA hacks reported by Wikileaks, which have been billed as gaping security holes in the world's biggest mobile operating system.

With every flagship device they release, Samsung makes sure to add in at least a few little software goodies. Last year's Galaxy Note5 was no exception, because among other things, Samsung included a revamped version of their useful utility called Air Command that gave users quick access to tools and common functions with a small floating bubble.

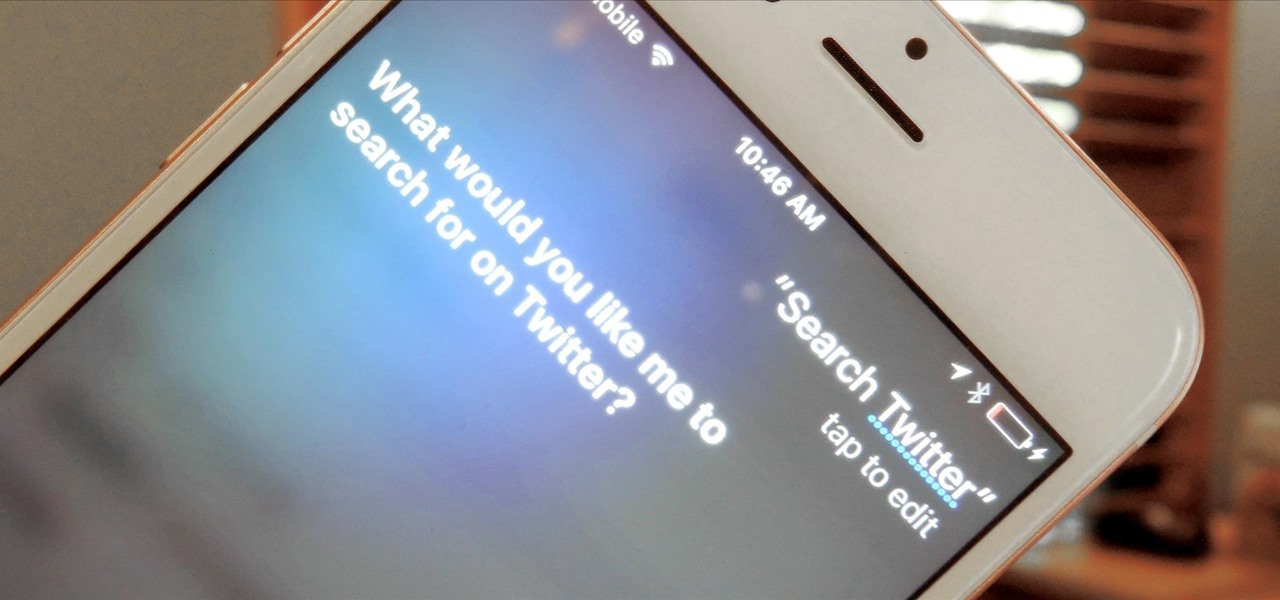
A new iPhone exploit has recently been discovered by YouTube user videosdebarraquito, who has found many other exploits and bugs in iOS over the years. This new exploit allows someone to bypass the lock screen and gain access to contacts and photos via Siri, Apple's digital voice assistant—but it only affects the iPhone 6s and the iPhone 6s Plus because it requires 3D Touch functionality.

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

As familiar as it may look at first glance, there are still tons of subtle changes in Windows 10. Many options that existed in past versions have been moved, and virtually every system menu received at least a small visual makeover.

Since the days of Android Jelly Bean, Samsung has implemented an energy preservation feature known as dynamic voltage and frequency scaling, or DVFS for short. What this essentially does is limit or adjust the frequency of the microprocessor to conserve power and prevent excessive heat from being generated.

Contacts on your phone can be messy. Keeping all of those numbers, emails, and addresses organized takes time and, even then, they still may not be be as accessible as you want them to be.

Trust can be a touchy subject in general, and is often required when sharing personal information—especially so when handing our phones over to others. You may not have a ton of secret or nefarious information on your device, but that doesn't mean you want your mom or snoopy coworker having easy access to your messages or Facebook app.

Third-party keyboards have been available for iPhone ever since iOS 8, but which ones are worth checking out? There have been many options over the years, and if you want keyboard features like swipe-typing and themes, you're going to have to put Apple's stock QuickType keyboard on the backburner and try out these top hits.

App switchers are a great way to conveniently access your favorite applications from any screen, but most limit the number of apps you can use. That means that whenever you want to switch over to another app, you have to leave your current one, and either find the one you want in recents, on your home screen, or in your app drawer.

It's hard to believe it's already been a year since I was frantically searching every Best Buy in the Los Angeles metropolitan area to find one with a Chromecast in stock.

Parents, grandparents, aunts and uncles, and even older siblings have all likely dealt with handing their smartphones over to young children. No matter if they want to play games or watch cartoons or record funny noises, you're handing over a very personal device to those who can mess up what they don't know.

There are a ton of great mods and tweaks available in Cydia, but occasionally there will be one you want to install that hasn't quite made it into one of the main repositories yet. If you're not patient, it can be still be installed by manually placing the .deb file directly onto your device and installing it with iFile.

Improved S Pen functionality materialized in the form of Air Command controls on the Samsung Galaxy Note 3, allowing users to access shortcuts for their stylus features from anywhere on the screen. While the pie-interface controls are extremely useful, the only way to access them is when the S Pen is removed—making it impossible to use otherwise.