
How To: Access a linux server remotely
A tutorial about why the two page resume isn't appropriate for most IT positions, and how to access a Linux server remotely and change the run level to turn off the GUI.


A tutorial about why the two page resume isn't appropriate for most IT positions, and how to access a Linux server remotely and change the run level to turn off the GUI.

Once you have access to the Detroit City Hub in Deus Ex: Human Revolution, it's possible to unlock a secret achievement dubbed 'Balls' on the Xbox 360 version of the game. This Giant Bomb walkthrough will help you locate the basketball hoop you'll need to earn the achievement with, and give you a little tip on how to easily get the ball through the hoop.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

If you'd like to have access to all your files at home without the hassle of spending money on expensive file hosting services or installing foreign software on your computer that could potentially harm it? Well Google has the answer for you, taking over the world one more computer at a time! In this video you will learn how to use your Gmail account and a Gmail Drive shell Extension to gain access to your files from any computer regardless of location!

In this tutorial, we learn how to open & utilize the trunk area of a 2010 Prius. To access the cargo area, open the rear hatch by pressing on the release above the license plate. To keep items out of sight, there is a sliding cover that you can pull back and hook into slots. To open, pull towards you slightly, then reel it in. There is additional space under the floor which can be accessed by twisting the locks and removing from the vehicle. Underneath this, there is a cargo bin, and undernea...

Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webmasters, SEO professionals, and others how Google works by answering their questions and giving them insights into how they can best integrate and utilize Google's functionality to improve their business. This video will ...
Clip Art from Microsoft Office allows you to insert stock photos into you PowerPoint, Word, Excel and Entourage documents easily. You can gain access to the Office Clip Art site easily in any of the mentioned applications. The Microsoft Office for Mac team shows you just how to download and use clipart from Office Online in this how-to video. You can get free stock images of low-priced professional quality photos.

First of all the tutor suggests that this tutorial is easy and you can complete it only fifteen minutes. However you need to use proper anti-static precautions when you are performing this upgrade. You have to ensure to discharge static electricity before beginning. You must also work on a static free surface. You need a "#00 Philips screwdriver" which you can find in the “Newer Technology” 11-piece tool kit. It is available from macsales.Gather all your materials and then shut down your comp...

Vince shows viewers hot to access the Chuck Norris trick on Google. First, you need to open your web browser and go to Google. In the Google search bar type in 'Find Chuck Norris' and click 'I'm feeling lucky'. Make sure you do not click enter but the 'I'm feeling lucky' button to the right. You will get a funny message that says 'Google will not search for Chuck Norris because it knows you don't find Chuck Norris, he finds you'! The suggestions should read 'Run before he finds you' and 'Try ...
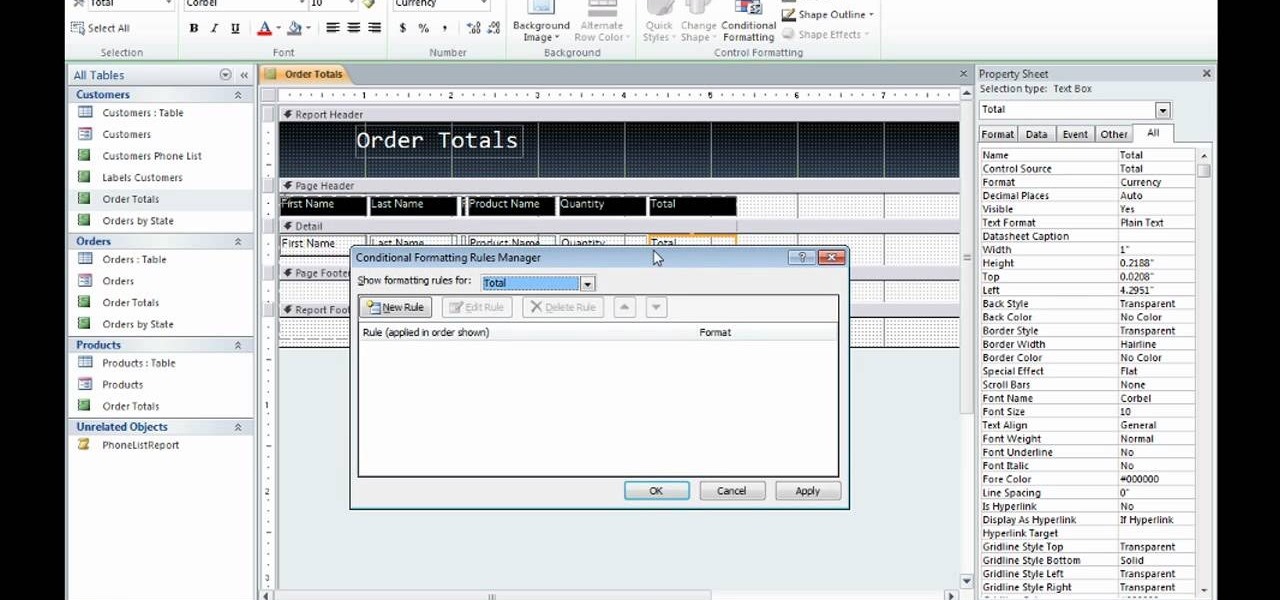
lyndapodcast teaches you how to apply conditional formatting withing Microsoft Access 2010. You click View - Design View. Click the Total tab and you'll notice some highlighted options above. Click Format and then Conditional Formatting. This where you will create rules. Click the new rule button. Now you will see the conditions with drop-down menus. Type in the numbers you want and then select the formatting you want when the rule is true. The preview below will show you how the numbers will...
This video instructs the viewer about the basics of cloud computing, using more than one computer and managing your computing needs online. The instructor explains, "Cloud computing is a metaphor for using the Internet for your computing needs." A program called cloudo, allows the user to store information online through an interface that looks like a regular computer desktop; then the information can be accessed via password from any computer with an internet connection. Other programs also ...
In this video tutorial, Chris Pels will show several aspects of defining and using master pages in an ASP.NET web site. First, see how to create master pages declaratively using the ASP.NET master page model and learn what information is best suited to a master page compared to an individual content page. Next, see how to programmatically assign master pages on-the-fly in an individual content page. Also learn how to create a base page class which assigns a master page programmatically for al...
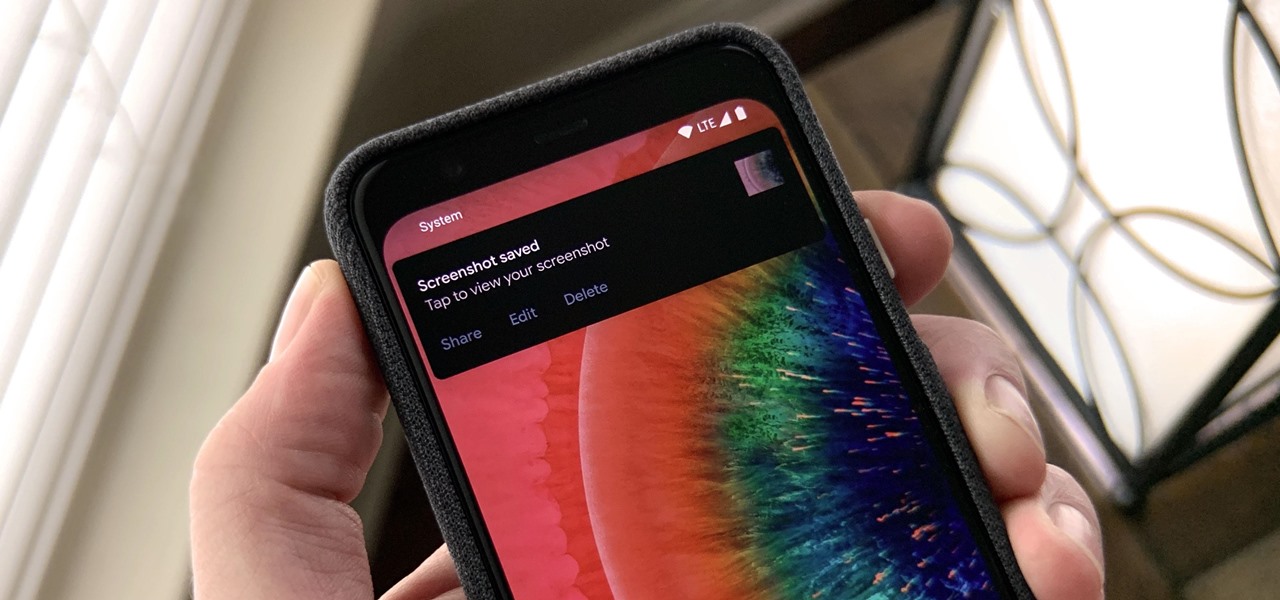
On stock Android 9 and 10, it is easier than ever to take a screenshot and quickly edit the captured image. However, the downside to that convenience has manifested itself in a heads-up notification that can also get in the way.
It wasn't too long ago that the power menu for stock Android didn't offer much beyond turning the device off, but Google has steadily added more functions, like capturing screenshots and provisioning access to emergency information.

Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long as you know where to look.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

The camera system on the iPhone has never been better. Apple's iPhone 11, 11 Pro, and 11 Pro Max sport some of the best shooters on the market. But no level of quality makes up for the fact that shady apps can access your cameras for nefarious reasons. You can take control of the situation, however, and block any app you want from using your rear and front-facing cameras.

The biggest new feature in Android 10 is the system-wide dark mode. Both Samsung and Google phones have it, so third-party support is everywhere. The only problem is OnePlus forgot to include a way to quickly toggle dark mode on and off.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

I'm a new parent and I just moved into a new home. The first thing I wanted to do was ensure my toddler's safety in his new digs. That meant buying a bunch of baby-proofing products from Amazon, realizing most were junk, then buying some more until I found solutions for all my needs.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

CarPlay is no doubt the best way to use your iPhone when behind the wheel since you can safely drive without too many distractions. It gets even better with all the music and podcasting apps available, as well as third-party navigation apps such as Google Maps and Waze. With more apps being added to CarPlay every day, it becomes more necessary to rearrange your home screen.
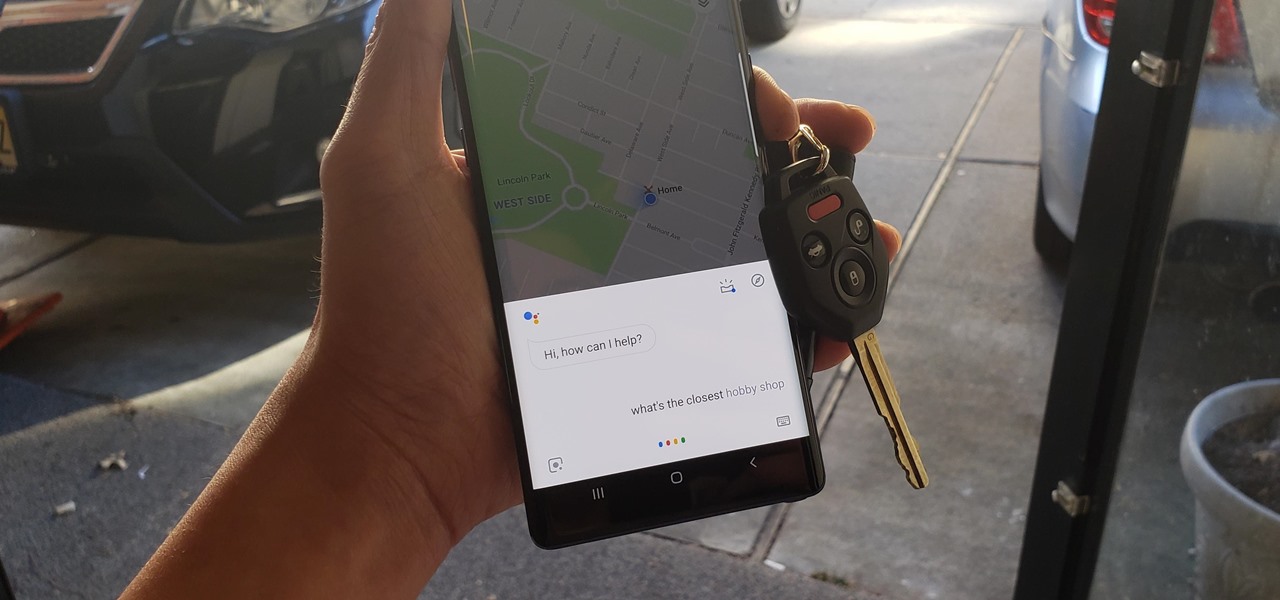
Millions depend on Google Maps for directions, and it's easy to see why. The app comes with tons of features like offline navigation, location sharing, and more. Google is far from done, however, and continually improves upon its navigation app to make it even more efficient and safer to use.

During the keynote at WWDC earlier this year, Apple introduced the latest iteration of its mobile operating system, iOS 12. Despite a thorough demo on stage, Apple glossed over new eye tracking features that use ARKit 2. Developers can now use the TrueDepth camera on the iPhone X, XS, XS Max, and XR to determine where your eyes are looking, opening up incredible new possibilities for new apps.

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

When BlackBerry made the move to Android OS, they were aware of the limitations it presented. Unlike with BB10, they didn't create the operating system and would have to deal with the vulnerabilities already included. As a result, they added numerous security enhancements, and at the heart of this is DTEK.
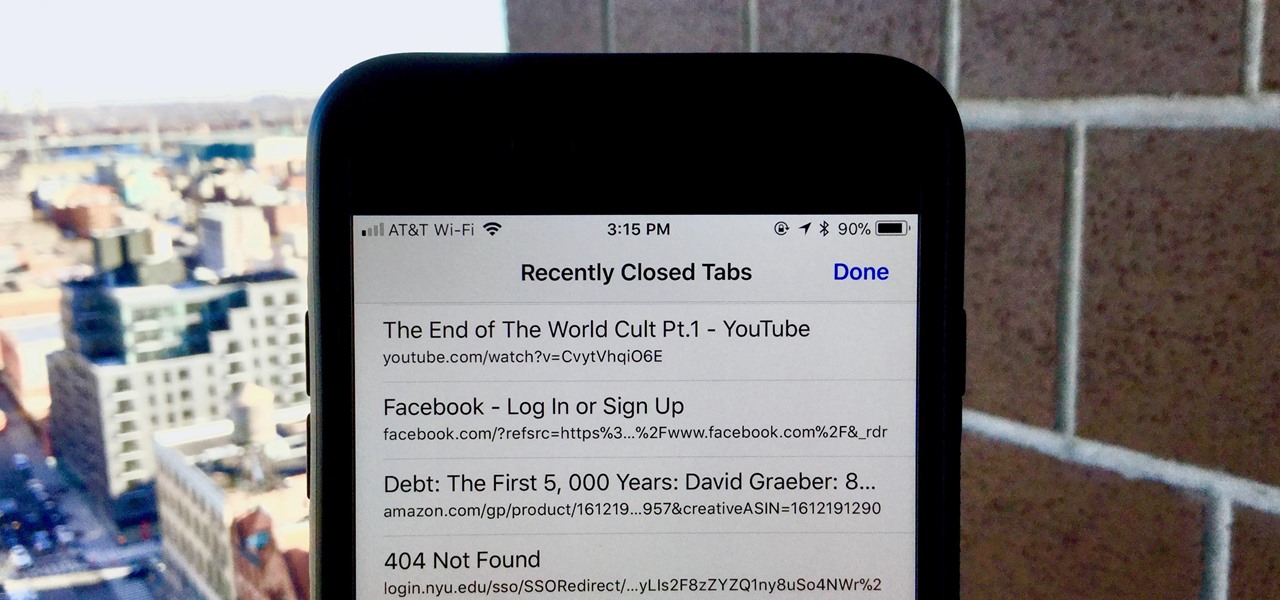
Almost certainly, you've closed out of a webpage that you didn't want to at some point in your iPhone-owning life. Whether you accidentally swiped the tab away or closed it only to need it moments later, tab-regret is just a part of our internet culture. Luckily, Safari on iOS includes an easy way to open recently closed tabs.

Most of us have never put much thought into this, but the question needs to be asked — what exactly happens to all of our online accounts when we die? No, the internet won't just know and delete accounts for you, so you need to plan for life's one guarantee. Because without a plan, things become a lot harder to sort out.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.
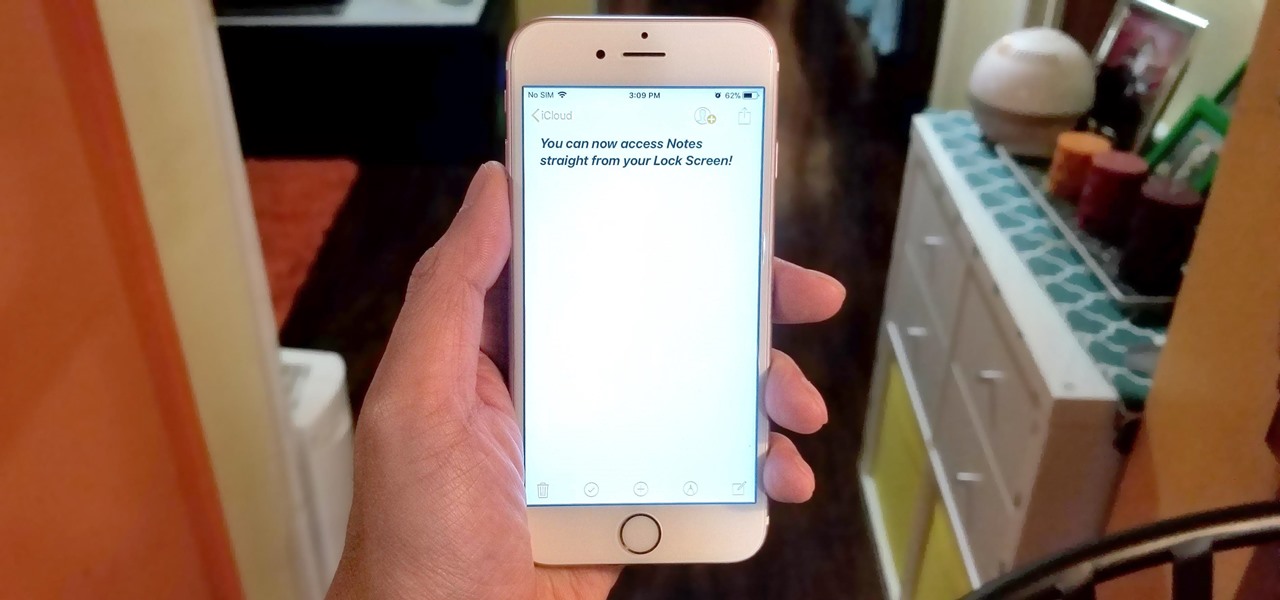
All to often, many of us are struck with a brilliant idea out of nowhere, only to forget about it moments later thanks to the distractions of daily life. Sometimes, the actual process of jotting these ideas down in our iPhones can be a holdup, as the idea we want to record fades from memory before we can even unlock our devices and open Notes to get started.

More often than not, road trips will include unforeseen pit stops that have to be made, no matter how well prepared you are. In the past, making an unscheduled stop may have led to headaches and delays when your navigation app got off track, but thanks to a feature in Google Maps, this is no longer an issue.

The peaceful, pastel and doily-filled world of Pinterest is my oasis. My account conveys who I want to be and what I want to accomplish, so the idea of someone hacking it and ruining my favorite escape for me is heartbreaking. Fortunately, Pinterest has updated its security, implementing three new features to hack-proof your account.
The Pixel and Pixel XL both use AMOLED screens, which are noted for their deeper blacks and sharper contrast ratios when compared to traditional LCD panels. However, AMOLED displays still have one fairly major downside, and that's the fact that they're vulnerable to screen burn-in.
The widget system on iOS leaves a lot to be desired when compared to Android's offering, but that's not really Apple's fault. The system is there, we just need some good widgets to really get the most out of it, so it's up to developers to create some awesome apps that work with the home screen and lock screen widget panels on iPhone, iPad, and iPod touch.