The iPhone has a handy feature called AssistiveTouch that lets you quickly adjust volume, lock your screen, rotate your display, and even navigate through the phone's interface using a virtual home button. In a way, it's a lot like the on-screen navigation bar that you'll find on some Android devices, but with a lot more functionality, and bundled together in a floating bubble interface.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

You can now access Google's slick Weather app without having to first open the Google or News & Weather apps. However, you will have to use Google to access the weather the old-fashioned way one more time, but you'll have the option to place a shortcut on your home screen to access the weather directly going forth.
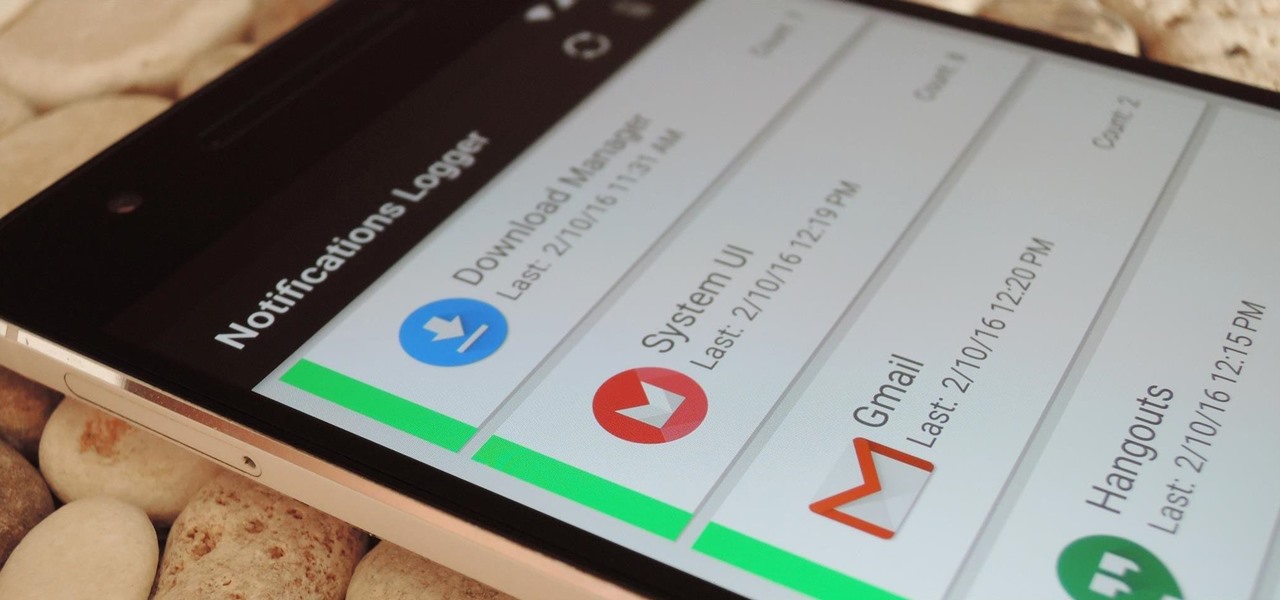
If you've ever prematurely dismissed all of your push notifications before you got a chance to read each one, you know how annoying it can be to dig through all of your apps to try and find the one with the missed notification.

It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc.
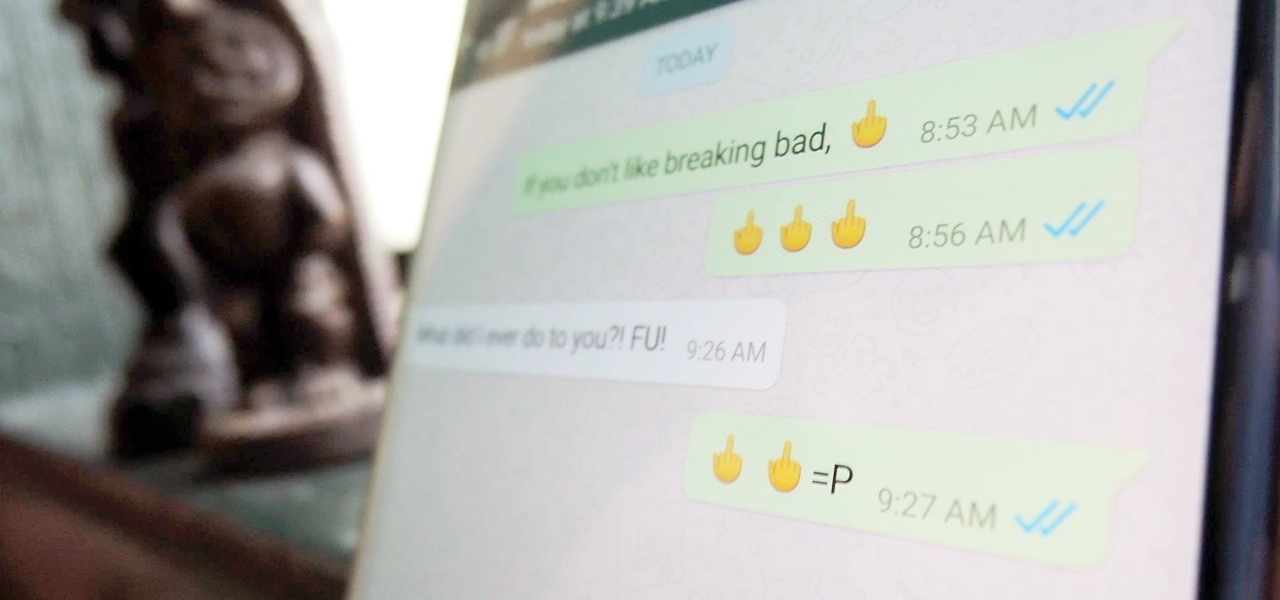
Hidden deep in WhatsApp's emoji database is a middle finger emoji, and there's a really easy way to use it. Much like Spock's "live long and proper" Vulcan salute, this one can be used simply by copying and pasting the emoji from our tweet. Note that the emoji, for now, does not display properly on iOS devices, but it can still be sent. So if you're in a conversation with an Android or computer user, they'll see it just fine.

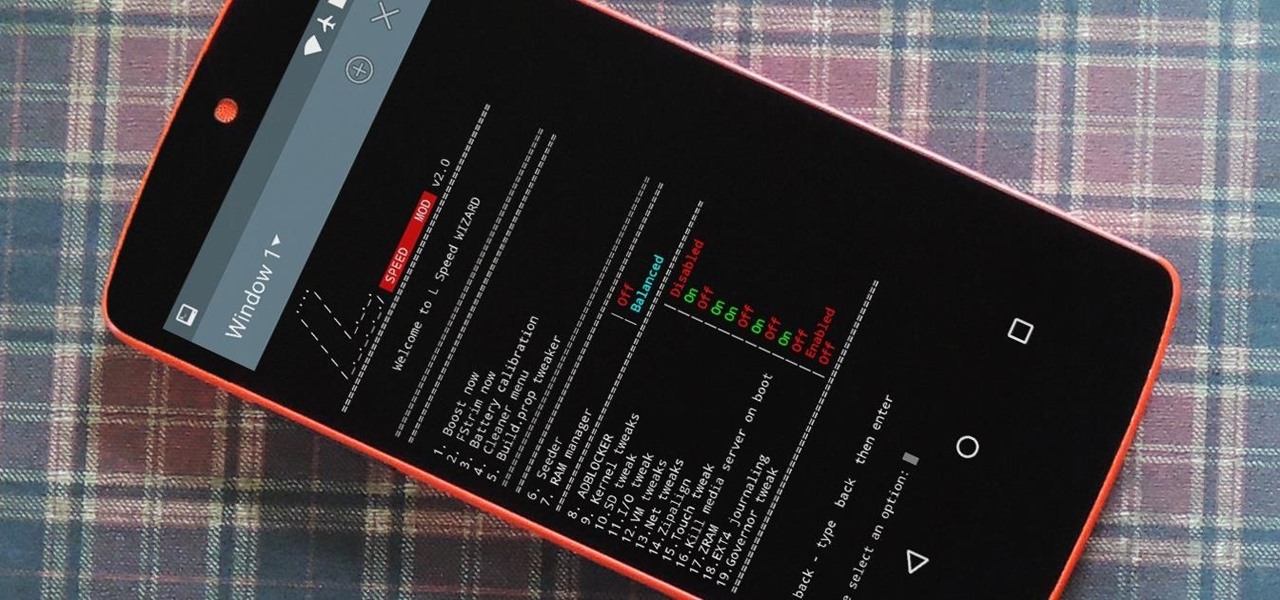
Performance boosters generally get a bad rap, but that doesn't mean they should all be dismissed—particularly when they're as well thought out as the latest work from developer Danijel Markov. After recognizing a few inefficiencies in the way Android handles memory management and other system-level functions, he created a flashable ZIP that will apply many fixes in one fell swoop.

Some people are of extremely secretive nature. They do not like sharing their personal events in their lives with anyone. Thus people around that person wont be able to figure out details on their life's personal matters. It is not like they want to hide some mysterious secrets from the world, but it is just their nature that they do not want others to know much about them or are too shy to share their feelings with others. Being secretive is neither good nor bad, it is just how they are.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

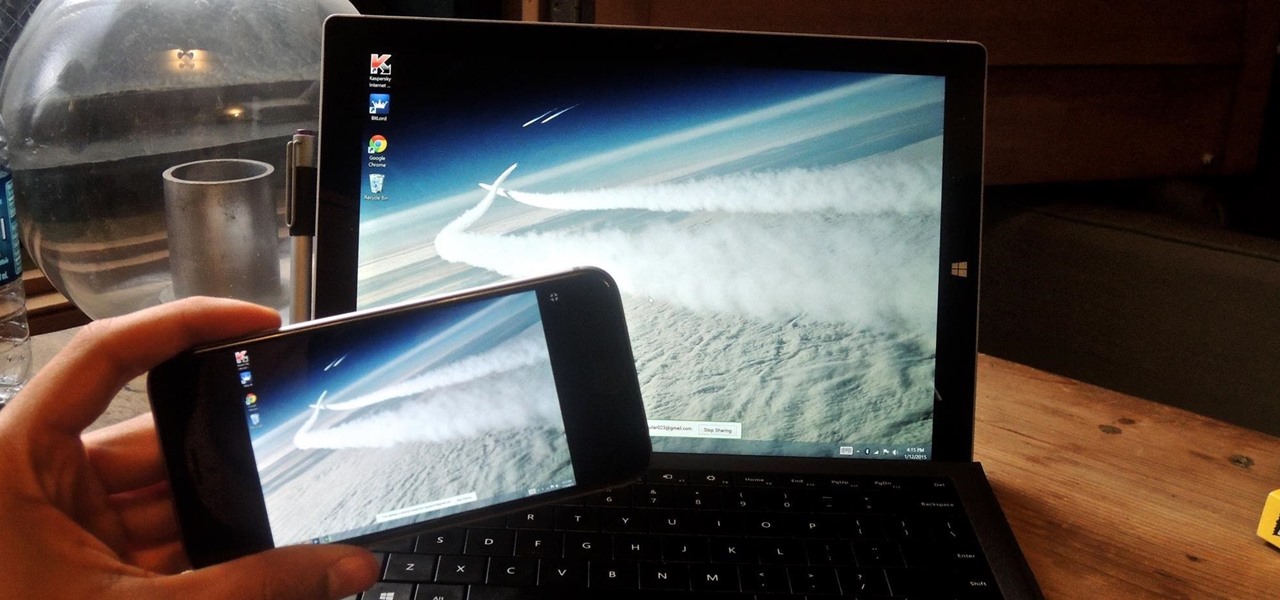
Google's Chrome Remote Desktop, which allows for remote access to your personal computer from your smartphone, has been out for almost a year now. Sadly, it's only been available for Android devices—until now. So, if you got an iPhone (or other iOS device), you can now access and control your computer directly from your smartphone or tablet just like with Android.

Lending someone your phone to make a call is always an awkward situation, as you closely monitor them to make sure they stick to a phone call rather than wandering off into private applications like your photo or messaging apps. You don't necessarily want to eavesdrop on their conversation, but trusting people with your phone is difficult, especially if you have some risqué or embarrassing pictures stored on it.

Airports are terrible germ-infested purgatories where people sit around for hours without Wi-Fi while they anxiously await to get wherever they really want to go. Unfortunately, there isn't much we can do about waiting, but this little Wi-Fi hack could help make the waiting a little less boring.

This video will show you how to protect others from accessing saved password on Google Chrome. Saving account passwords in browsers are useful for time saving as well as threatening for malicious activity. This is dangerous for security. So you must protect your accounts detail from others to secure your browsing. Watch the video and follow all the steps carefully.

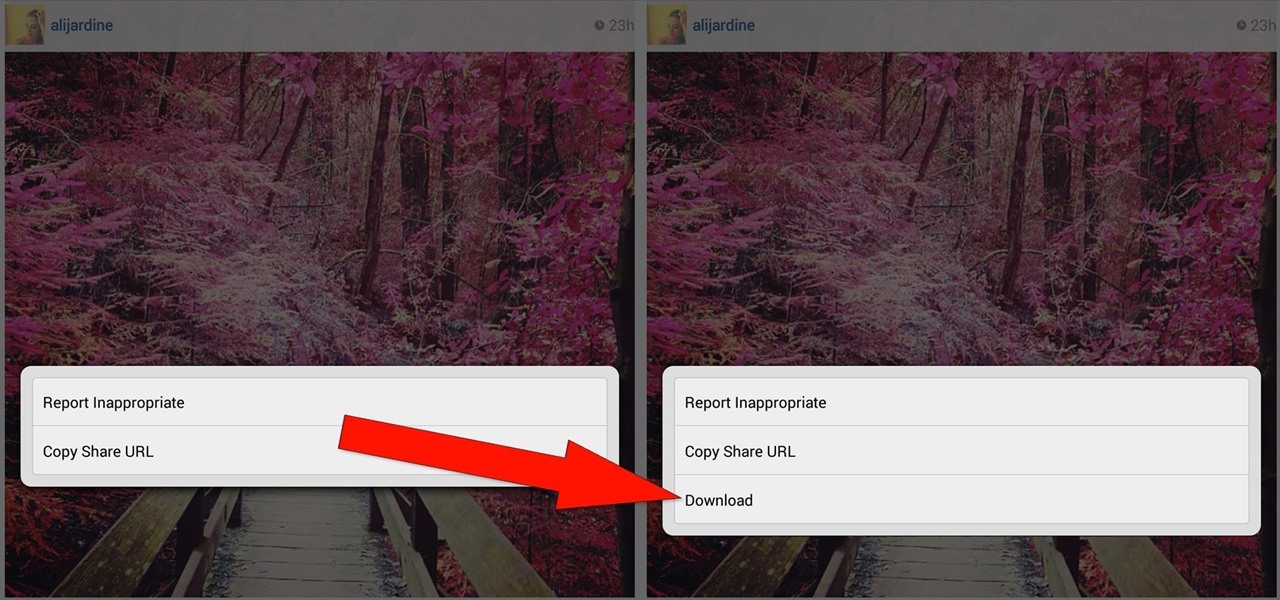
Known for its easily recognizable filters—and coining the hashtag #nofilter—Instagram has long been an app that focused more on photo posting rather than photo editing. Yet today, Instagram released an upgrade for both Android and iOS users that edges the app towards becoming a full-fledged photo editor.

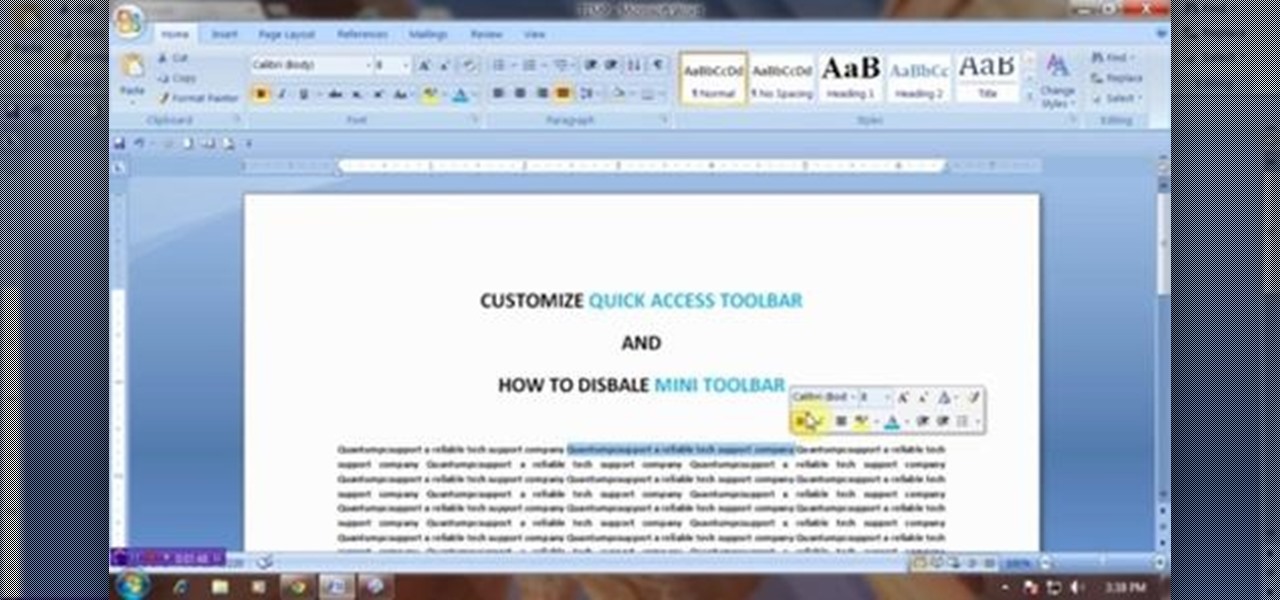
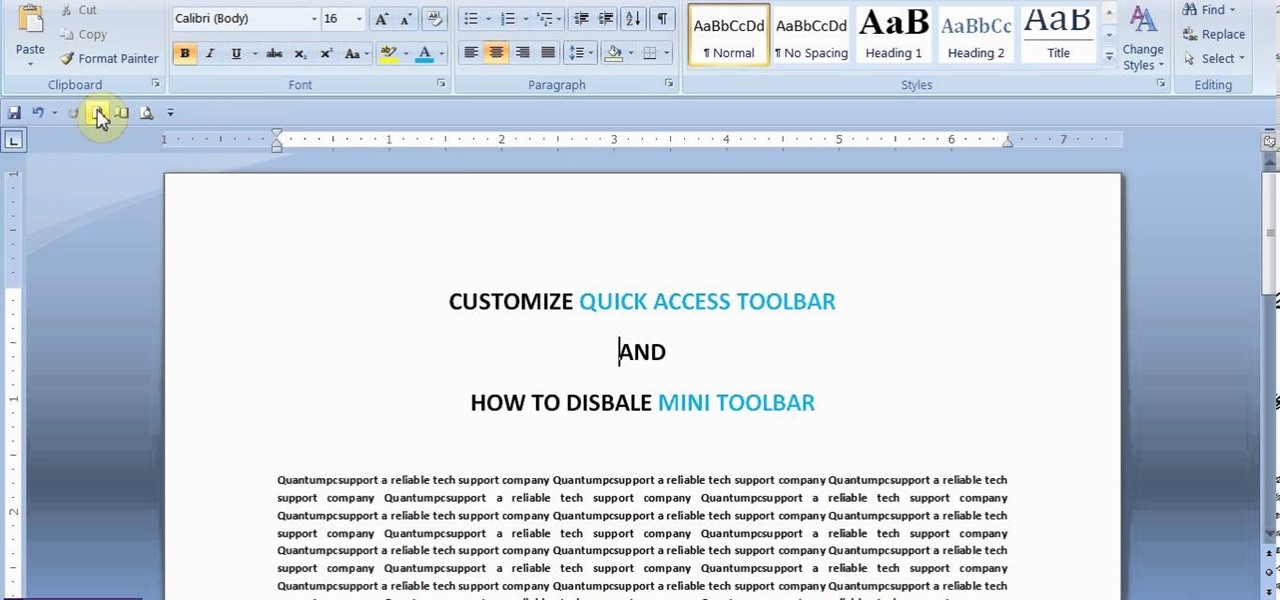
This video will show you how to customize quick access toolbar and delete mini toolbar in MS Word 2007. These 2 things are very useful. Watch the video and follow all the steps to employ it yourself.

With popular remote desktop app LogMeIn recently ending its free service, lots of Android users have begun looking for alternatives. There are some good ones out there like TeamViewer and Microsoft Remote Desktop, but today, Google released an app that makes a pretty good contender.

Parlez-vous français? While we all wish we were fluent in multiple languages like Jason Bourne, most of us are probably one-trick ponies. When traveling abroad, or even when taking language courses, having a translator handy is extremely important.

Getting into fastboot or recovery mode on your Android device is nothing new, especially if you're a softModder. Accessing the bootloader menu is the genesis to a lot of mods, and if you're like me and constantly tweak your device, you probably get irritated every time you have to shutdown, then use the power button and volume rockers to access the special menus.

There are a gazillion lock screen apps available on Google Play, but the majority of them are subpar and not worth your time. However, in my opinion, there is definitely one out there worth your time—one that constantly learns and adapts to what apps you use when and where to determine which shortcuts to give you.

Ways to Blocking a Website on a PC Open the “Control Panel” by click “My Computer” on your PC

These days, everyone's snapping selfies, taking pics of their latest meals, or sharing pet trick videos on Instagram for the whole world to see. It's not only fun to shoot photos and videos for Instagram, it's inspiring to look at everyone else's creativeness in your feed.

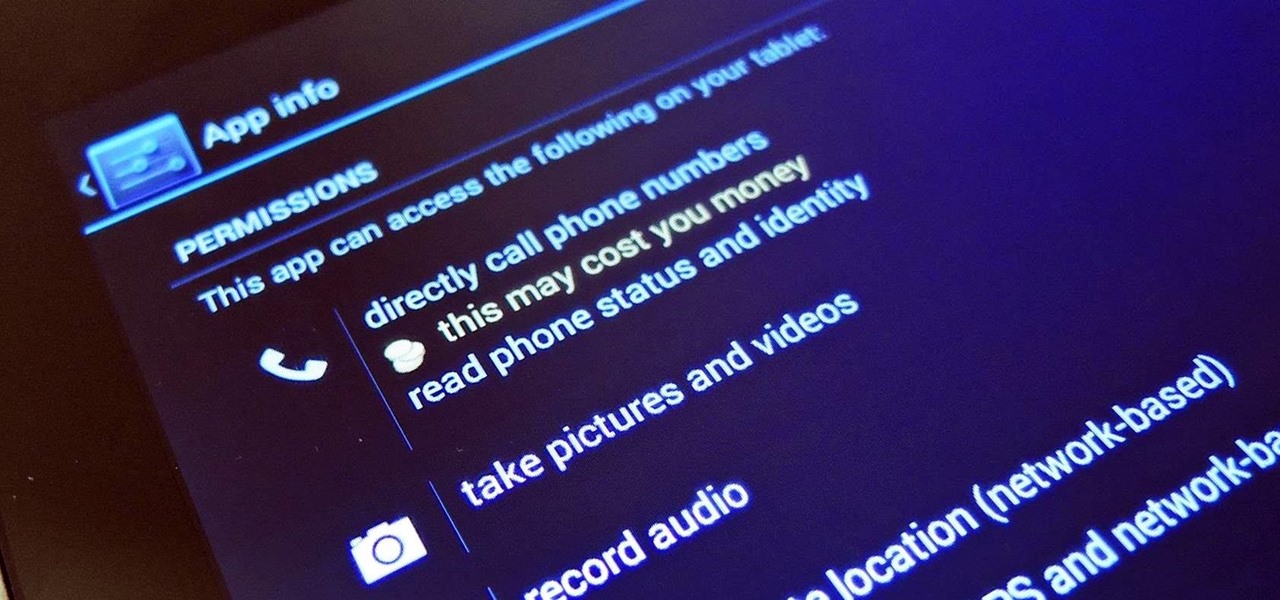
Privacy has been a heated topic in recent months, with everyone now up in arms over unauthorized leaks and exposures. And guess what—tablet and smartphone users are just as vulnerable.

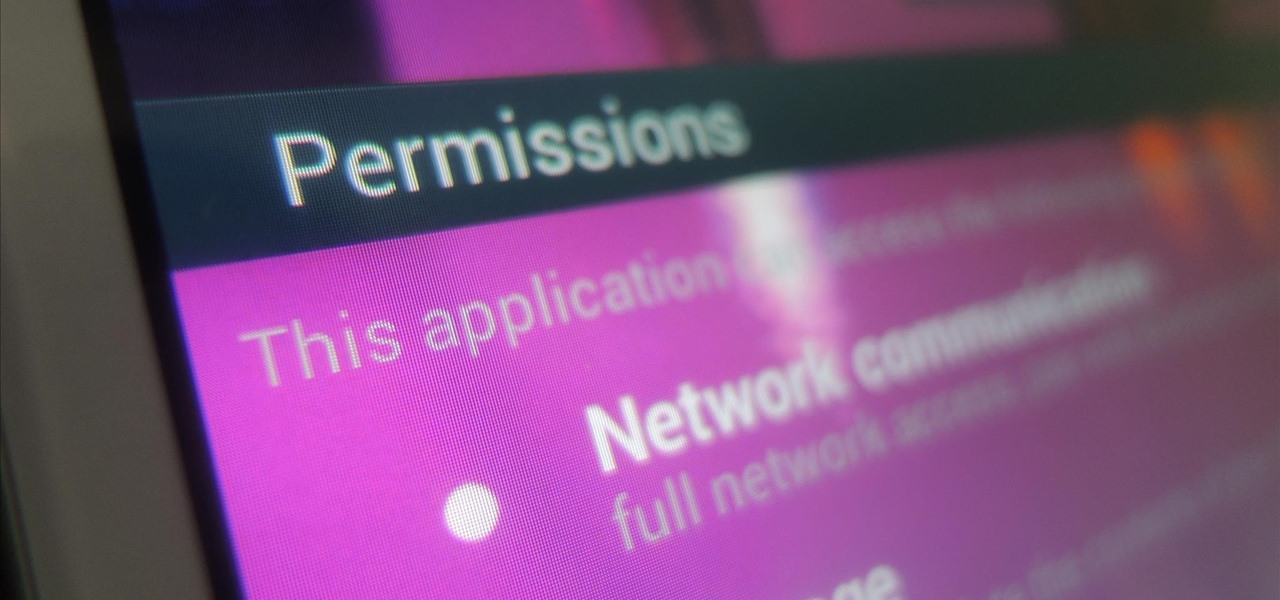
While we're usually responsible for leaking our own private information through mediums like Facebook, there are other times when we mistakenly and unwillingly allow certain applications to scour through our personal data. Some apps may have enabled permissions for internet access, thus allowing it to share said data with its external servers.

Welcome back, my neophyte hackers! As part of my series on Wi-Fi hacking, I want to next look at denial-of-service (DoS) attacks, and DoSing a wireless access point (AP). There are a variety of ways to do this, but in this tutorial we'll be sending repeated deauthentication frames to the AP with aircrack-ng's aireplay. Remember, hacking wireless networks isn't all just cracking Wi-Fi passwords! Our Problem Scenario

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

This video will show you how to customize Quick Access Toolbar in MS Work. You could add, delete commands and can set the placement of the bar.

The majority of our documents and music are digital, which is great for convenience, but it presents a problem for those with a lot of stuff—where do you store it all? There are tons of sites that offer cloud storage, like Dropbox, SkyDrive, and even Flickr, but most of them have limits unless you want to pay, and no way to connect them all.

In this Windows 8 Tutorial you will learn how to use the shortcut key for accessing the charms bar in Windows 8. There are a few benefits to this for one the charm bar remains in place even if you don't have your cursor over it also you save yourself time by not having to go all the way to the upper right hand corner of your screen every-time you want to access the windows 8 charms bar.

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

Having access to your computer from your cell phone is an extremely useful feature. Whether you need to edit documents or send files that are on your home desktop, or you simply want to watch movies you have saved on your computer, access is key.

Can you feel your inner Dennis the Menace trying to get out? Trying to recreate the early 90s bad boy Bart Simpson look? Watch these videos to learn how to make yourself a slingshot. This slingshot is made from materials that are probably laying around your house, but you will need some power tools.

Holiday cards are great, but their prices ($5.95 average for a nice one) are not as easy on the eyes. Save up your hard-earned cash this holiday season by making your own festive Christmas cards.

In this clip, we learn an easy technique for generating anaglyph 3D images in Adobe Photoshop CS5. It's easy! So easy, in fact, that this video can present a complete overview of the process in about two and a half minutes. For all of the details, take a look.

Looking for an easy way to export a list of songs from iTunes? With the copy and paste technique demonstrated by this tutorial, it's easy. So easy, in fact, that this home-computing how-to from the folks at CNET can present a complete overview of the process in just over a minute. For more information, including a complete demonstration detailed, step-by-step instructions, take a look.

Looking for an easy way to protect your privacy when using Google Search? With the right habits, it's easy. So easy, in fact, that this home-computing how-to from the folks at CNET can present a complete overview of the process in just over a minute. For more information, including detailed, step-by-step instructions, take a look.

If you already know how to sew a lapped zipper, than it's time to move onto the centered zipper, and that's exactly what you'll learn in this sewing tutorial. There's easy-to-follow directions for sewing lapped zippers using a basic sewing machine. If you don't have a sewing machine, check out all of the other zipper sewing tutorials. A center zipper is easy on any type of clothing fabric!

Looking for an easy way to make certain that your sensitive personal information is secure? With Identity Finder, it's easy! So easy, in fact, that this home-computing how-to from the folks at TekZilla can present a complete overview of the process in just over three minutes. For more information, including step-by-step instructions, take a look.

If you are interested in making something cool from scratch using paper, then next tutorial should help. this video is showing you how to make an easy cool looking origami ball from scratch. It's easy to follow and can be used for a bunch of different reasons, including playing various games with your friends. So good luck, pay attention, and enjoy!

Looking for a light-and-easy makeup look suitable for everyday use? Well, you're in luck, as this home beauty how-to offers advice on just that. For more information, including complete, step-by-step instructions, and to get started using this easy and understated makeup look yourself, take a look.

If you find yourself out in the wild and need to find a way to keep yourself free of any moisture or animals, installing a hammock is s good idea. Not only does it give you a place to lay, but it can keep you safe from small critters and any kind of moisture from the ground.