In this video tutorial brought to you by photoshopuniverse, you will learn how to apply mood lighting to images in Photoshop. This is achieved by applying an adjustment layer, called a gradient map, which allows you to adjust the color of the light in an image. You will learn how to access the gradient map from the adjustment layers menu, how to apply the gradient map, then overlay the new layer and fine tune the gradient to create more dramatic looking images.

Some governments and organizations employ proxy servers to filter web content, permitting access to some web sites while blocking others. Here are several ways to get around these censorship policies. This is employed in China with YouTube and many other voices of anti-goverment ideas.
In this ASP.Net video lesson, you will explore the new membership capabilities of ASP.NET 2.0. In addition, you will learn about role-based security, and how you can use roles to control access to your Web site.

This video shows how to make your own webserver to share files or host websites for anyone on the net to access for free, in under 7 minutes using Apache, which is free software.

This video shows how to get intravenous access by doing an IV cut down.

Audio filters help you create a credible soundtrack. They can remove distracting noises, like the hum of an air conditioner, and add atmosphere, like an echo. Filters are accessed in the effects tab of the browser and organized into two categories: those provided by Apple and filters that come bundled with Final Cut Express. Drag a filter into the timeline and doubleclick it to edit it in the viewer.

Video filters let you adjust and enhance your clips for greater visual effects. Access Final Cut Express' filters in the effects browser. Simply position the timeline playhead over the clip, apply a filter, and the resulting changes are displayed in the canvas. Filters can be animated using keyframes, which work the same way with filters that they do with motion.

Learn a series of beginner's card magic tricks.

While many image sites allow you to hide image and video catalogs behind passwords, you can often gain access to these images by "guessing" the URL of the image. This process is called fuskering. Photobucket is one of the popular websites that can be fuskered and this tutorial will teach you how to use Nav.Net 4.2 to fusker private images

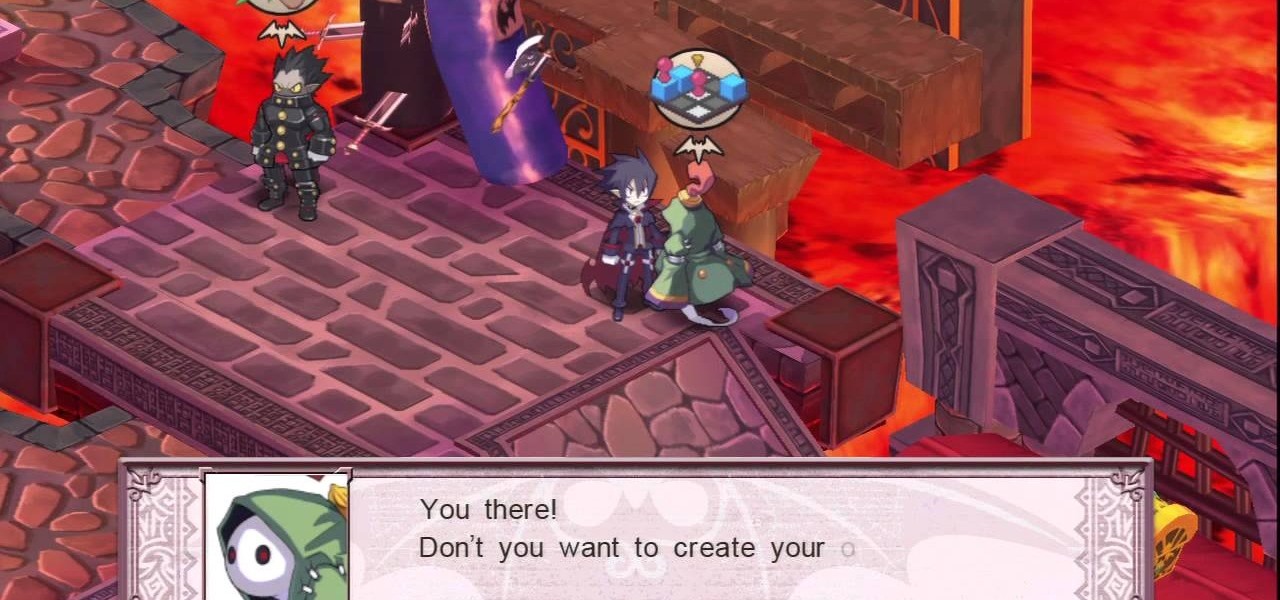
If you've completed chapter 3 of Disgaea 4: A Promise Unforgotten, you can access the map maker and start to create your own maps for multiplayer. This guide teaches you how to use the map maker in Disgaea 4 to create unique maps for use against your online opponents!

Don't get us wrong - we love our iPhones and iPods - but sometimes we just want to kick back on the couch, pour ourselves a glass of Chardonnay, and go for the full surround sound musical experience. Get a more visceral exerpience of your favorite tunes by listening to them on your TV.

So you've found all the Romulus Lairs and collected all the Borgia flags - now you just need to find the treasure room! This tutorial shows you where to access it and what sort of goodies you can find inside!

Uh oh, you've forgotten your AT&T Online Account Management password! No worries, this simple guide shows you how to regain access to the site and reset a new password. Your AT&T Online Account Management portal is vital to keeping your information up to date, so make sure you know how to NOT get locked out.

this video first shows a type of modem that can be used to connect Xbox Live along with a router. It is shown that you must already have an internet provider and router for connecting more then one device into your modem. An Xbox live account is also required to gain access to Xbox Live. A DSL cable is then connect from the Xbox into the router which is then connect to your internet providers modem. You must then select connect in the Xbox Live access menu. After the Xbox has been connected y...

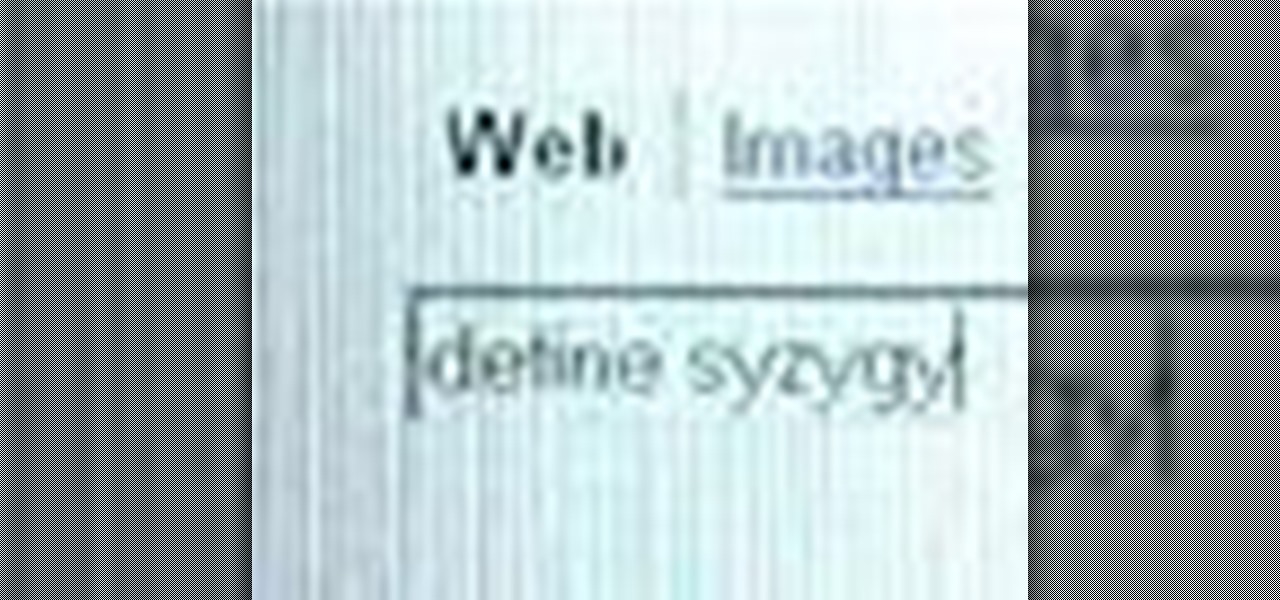
In this video tutorial, we learn how to use advanced search parameters like "define" and "site" to access hidden functions of the Yahoo! search engine. For more information, including a complete demonstration and detailed, step-by-step instructions, watch this how-to from the folks at CNET TV.

Access your favorite FM radio station with your Motorola Q! This tutorial also shows you how to load your favorite music onto your cell phone, and then choose segments to turn into ringtones, which you can personalize further by assigning them to individual callers.

If you like shortcuts, then this shortcut for Windows XP should peak your interest. In this video, you'll learn the exact steps to adding a command prompt shortcut option to the Windows Explorer right-click menu. This allows you to access hidden functionality by adding a right-click option to select "Command Prompt Here" from the menu in Windows Explorer on a directory.

In this Computers & Programming video tutorial you will learn how to use Stock.Xchng to access free stock images. The site is at SXC. Go to this site and you will find a large number of stock images that are free to use. And every day new photos are being added. You can search for an image by category by clicking on the search box and scrolling down to find your category. You can also type in the search box to find a photo of your liking. The image also tells you what is the screen size, prin...

Forex— what is it? Any investor could tell you a complicated description of what Forex is, but the basics of the FX currency markets is— an over-the-counter financial market for trading currencies. The foreign currency exchange market has no central exchanges like the stock market and little regulatory oversight. With this beginner’s guide, learn the trading basics.

Learn how to use CSS (cascading style sheets) to style pages created in Adobe Dreamweaver CS5. Whether you're new to Microsoft's popular data management application or a seasoned MS Office professional just looking to better acquaint yourself with the Access 2007 workflow, you're sure to be well served by this video tutorial. For more information, and to get started applying CSS formatting to your own pages, watch this free video guide.

Protect your email account from would-be hackers and crackers with this free video tutorial from the folks at MacMost. If you have a Gmail, HotMail, Yahoo! Mail or other web-based email account, this video is much recommended. For more information, and to secure your own online free email account, watch this helpful guide.

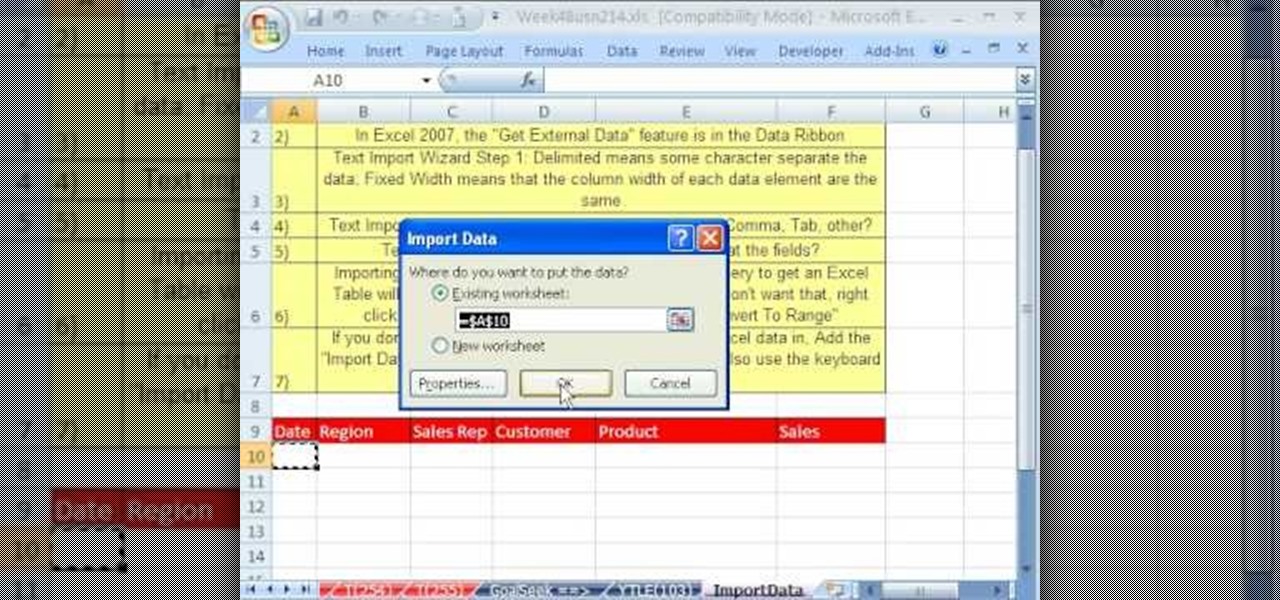
Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you're in the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 23rd installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn how to import data into Excel from text files, web sites, Excel files and Microsoft Office Access files. Also see how to import currency rates and major indicies from ...

In order to access your wireless router settings in a Windows PC you need to use a command called ipconfig. The purpose of this command is to find out what your IP is. Go into the command console and use ipconfig to find out what it is but instead of noting down the IP address, we actually have to note down the default gateway values for the task at hand. Now all you need to do is open your web browser and insert the default gateway values from before into the address bar. By doing so you wil...

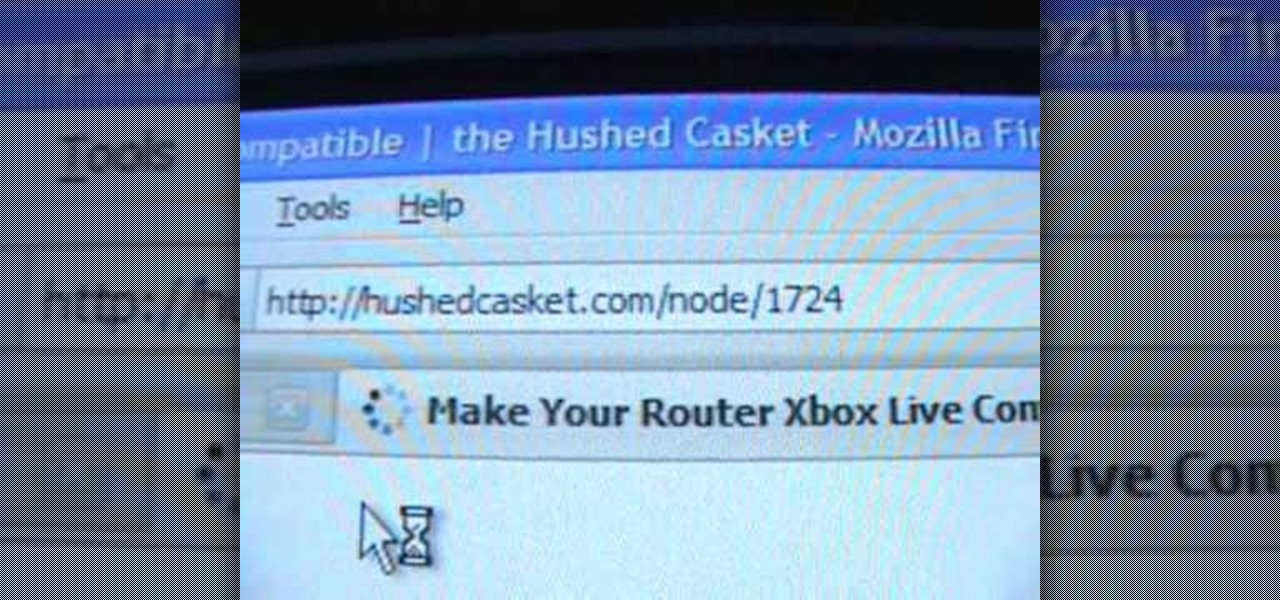
Open your internet browser, type in the address bar 192.168.1.1 and enter your user name and password to access. Look in the right and search for Port Forwarding / Port Triggering. Click on Add Custom Service. Type a name to the service, like XBox Live, now access HushedCasket and scroll down to see the ports you need to open. Go back to the setting and select UDP in Service Type. Put 88 in Starting Port and Ending Port. Go to your XBox and enter in System Settings, go down to Network Setting...

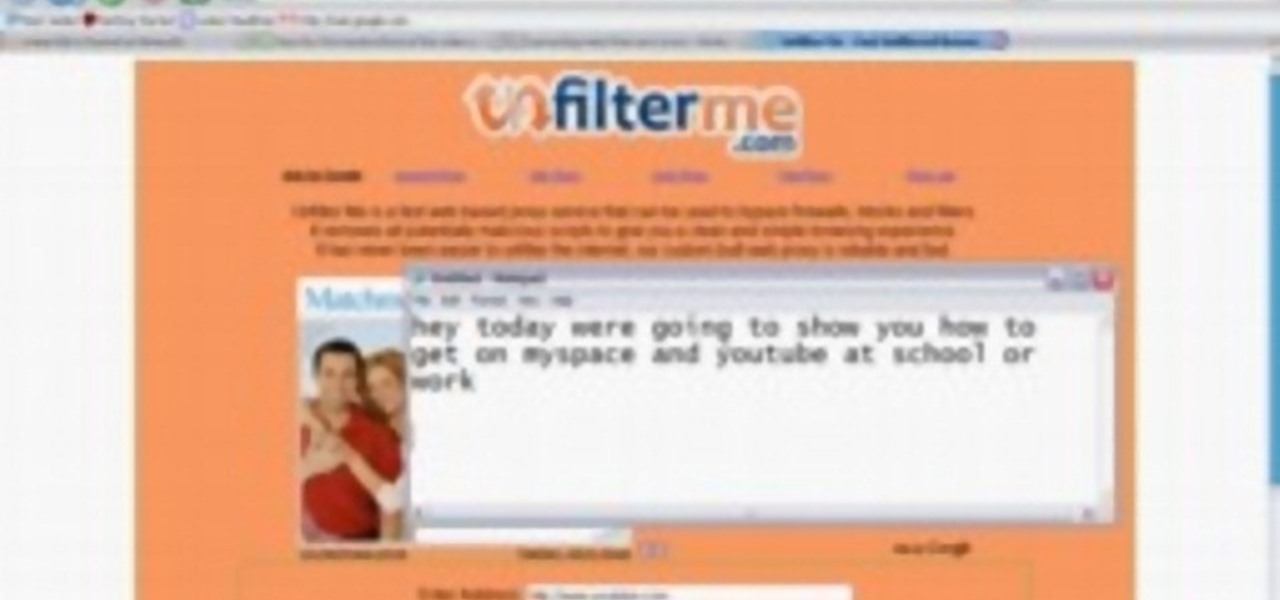
This video shows you how to easily access blocked website like MySpace or YouTube at school. The first thing you have to do is open the web browser and surf to Unfilter Me . Then, type your desired web site URL in the "Enter Address" field. Hit the "Start Browsing" button and wait for the site to load. Note that the URL in the address bar is different. This is the easiest way to access blocked websites at school. That's it! Good Luck!

Learn how to change the themes in Gmail with this video. * Access your Gmail account.

In this video one of the ultimate iPhone hackers, Jonathan A. Zdziarsk, demonstrates how to use a forensics toolkit to recover deleted text messages on an iPhone. But wait - there's more! Not only can you access text messages, but almost any other data on an iPhone as well. We can't be responsible for what you find though!

In this two-part video, learn how to jailbreak an iPhone, iPod, or iTouch 3.1.2 with help from computer whiz, Black Rain. In order to complete this jailbreak, you will need Cydia and web access to visit www.blackra1n.com.

In this tutorial Lindsay Adler will teach you how to add makeup to your models in Photoshop. Sometimes you do not have access to a makeup artist, or after the shoot decide you want a splash of color. Lindsay will teach you to add makeup in a few quick steps in Photoshop.

This video tutorial presents instructions on hacking a weak Wi-Fi Protected Access, or WPA, wireless network. To follow along, and replicate this hack yourself, you'll need knowledge of the deauthentication, or DeAuth, process. For more information, and to get started hacking WPA networks for yourself, watch this hacking how-to.

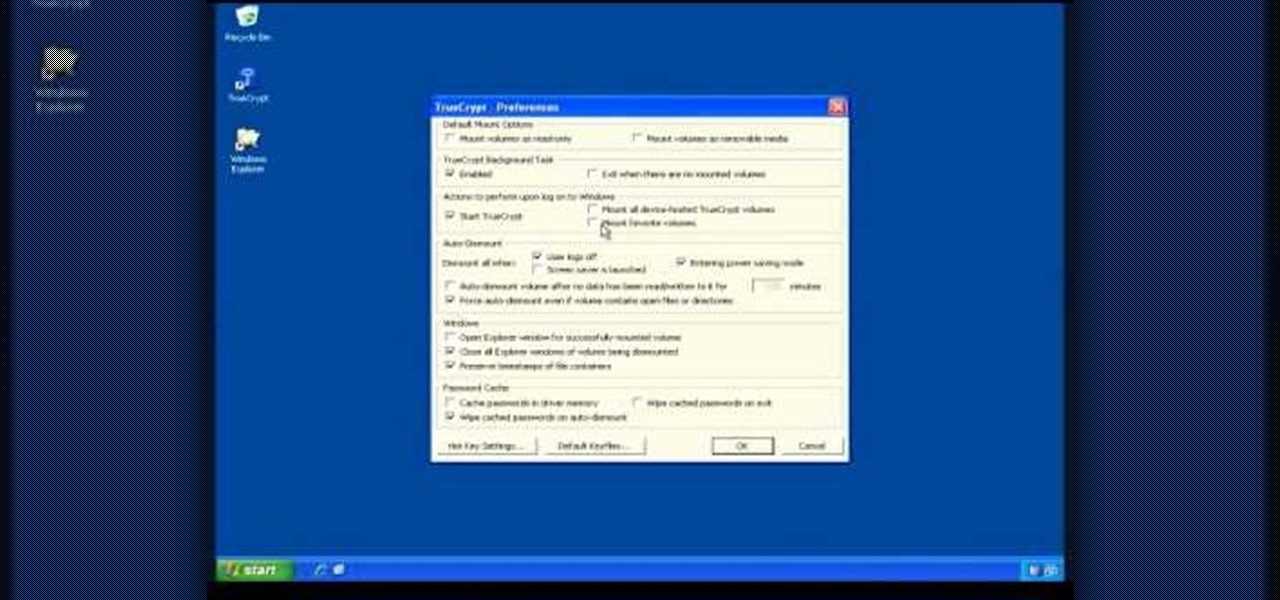
How to use or mount a TrueCrypt volume to access the data that you have encrypted with the program.

Mac users know why they love Apple. Of course, there are limitations. An entire universe of shortcuts is unavailable to the average user.

The overarching and expanding field of data science and analysis has become virtually inseparable from areas such as programming and development.

In previous Android versions, you lost about an inch of screen real estate to the status bar and navigation bar. But if you enable Android 10's new navigation gestures on your Samsung Galaxy, you can regain the bottom part — and with the help of ADB, you can reclaim the top portion as well.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

When you place your iPhone over a card reader for Apple Pay, it'll always pull up your default card. That might work fine for you, but perhaps that isn't the card you want to use. The problem is, you don't have time to switch cards before the payment goes through. That might result in using your rewardless debit card to buy groceries when you could've snagged 2% back by using your Apple Card.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

Apple has seemingly always made it a priority to show how much it cares about user security and privacy — enough that it has a page dedicated to it, proclaiming that "privacy is a fundamental human right." It's true that there are few issues more important than user privacy when it comes to technology, and Apple only makes things better in iOS 13.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.