Many have tried to prove (or disprove) that tennis ball lock picking really works, but it still seems up for debate. Mythbusters have supposedly debunked this technique (watch the video). Someone over at the Auto Blog also has tested this car lock method with failed results (watch the video).

This is how to make a DIY aquarium or fish tank background. Some people's methods may differ from these, but this is the easiest, most inexpensive way. You may want to listen to the Incubus song "The Warmth" while you are doing it. (Wait--is that Brandon Boyd?)
Although rare, sometimes a purchased song or video doesn't download properly. If this happens, there are methods iTunes provides to look for the lost music.

Learn about all the different types of numbers, like integers, irrational numbers, and real numbers, in great detail. Also includes how to use a number line, a dichotomist tool, and other methods of number manipulation.

Having trouble with your chess game? Well, try this "double attack" method to do a simultaneous attack of one piece against two opponent pieces. This is also referred to as the "fork."

This video will show you how to replace a wick in a standard Zippo lighter. This method can also be used in many other similar style lighters. As you will see in the video, you might not even need to change it, but rather just use what's left. There's a lot hidden in there!

In this soldering tip video brought to you by BEST, Inc. Norman Mier explains how to prepare through-hole components for installation using lead-free solder.

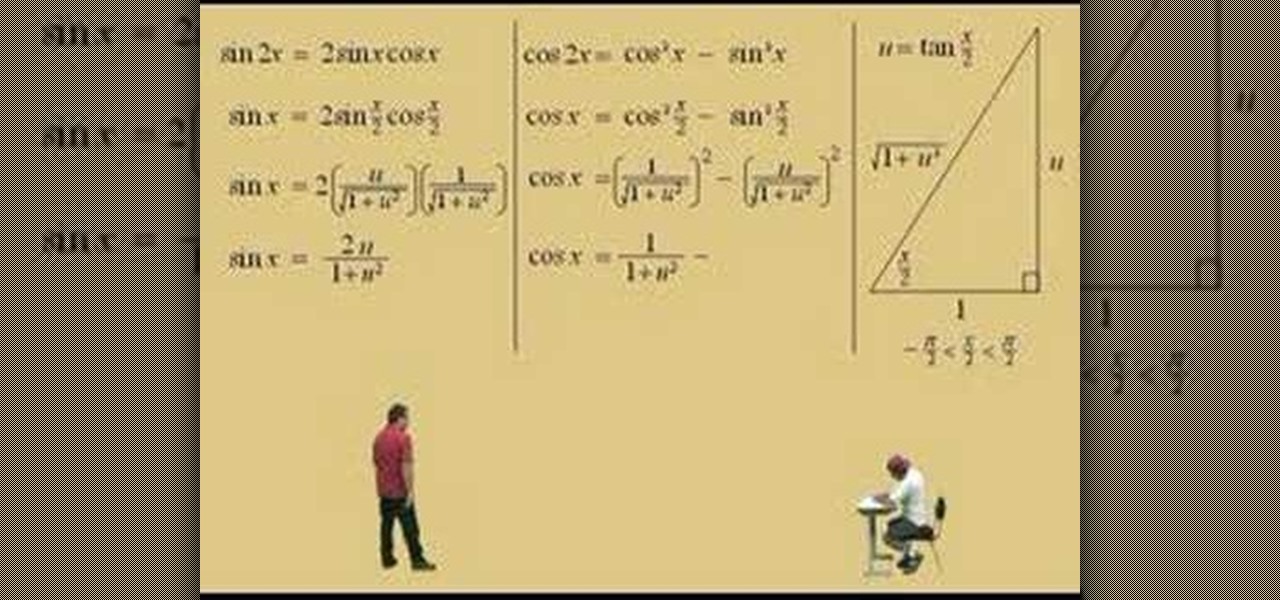
Lawrence Perez, from Saddleback College, and his assistant Charlie, give this two-part calculus lesson on integrating with special substitutions; rational functions with sine and cosines: Karl Weistrass method.

Learn how to perfect that upstrum and ghost-strum on your acoustic guitar with Charles Sedlak. What's a ghost-strum? Why don't you stop asking questions and just watch and see for yourself?

Violin Lesson #40 -- Legato Bowing (Smooth Bow Changes). Todd Ehle shows how to accomplish smooth bow changes with the legato method in this lesson.

Be green and eco-friendly by learning about compost. This video shows the basics of compost, composting materials, and the different methods of composting.

We may not all be Macgyver, but we can certainly channel our inner detective by bolstering our lock picking skills. And some of the hardest locks to crack open are combination locks, which have several disks are require advanced lockpicking skills.

This video shows basic kendo footwork (ashi-sabaki). In this video, very basic ashi-sabaki are introduced such as suri-ashi (gliding/sliding) and okuri-ashi (very basic footwork). There are also some basic training methods of ashi-sabaki.

This video demonstrates how to make a glass hummingbird bead with the lampworking method. Watch for efficient instructions and a very clear view of the process!

Barry Fahr, an associate professor of drawing at Otis College of Art and Design, demonstrates how to create a still life drawing of a red delicious apple.

No website will be inaccessible and no web filter will deny you content once you learn the skills presented in this internet hacking video.

Crunches on the Swiss ball offer several advantages over more conventional methods and machines. When done correctly the Swiss Ball crunch is super effective.

Jeff Schell walks you through simple yet effective methods to show two people having a phone conversation on screen at the same time. Jeff starts by showing you how to quickly make a picture-in-picture effect in Premiere Pro CS3, and then adds on a cross-dissolve transition to fade the video in and out. Jeff then demonstrates how to use the Position property to slide a clip to one side, so the people on the phone are side by side.

Did you know that malicious people can use scanners to read the Radio Frequency Identification (RFID) chips in your credit cards and identification documents and steal your personal information? Learn to protect your personal information from hackers and scammers with this simple method involving aluminum foil.

People are terrified of cooking rice for some reason, and claim that it never comes out right. They say it’s either a big gluey mess, or crunchy and under-cooked! Well, this method should fix all those problems.

Have you ever gotten the error message, "BOOTMGR is missing" on your PC? Well, if you have check out this video. In this tutorial, learn how to remedy and fix this problem in no time.

Jacob shows the importance of washing your car properly. First use two buckets. Fill one with soapy water, the other to rinse your car. Use a grip guard to keep your tools above water, and use white buckets. The principal is to keep the wash water as clean as possible. Get your sponge soapy, wipe the car. You then rinse it in the clean water, making sure there's no dirt. Use the foam/rinse method to wash. First use a soapy sponge, making sure the sponge doesn't actually touch the car, then ri...

Learn two different methods of meditation, as used by David Blaine and Chris Angel. In the first method, you will push up on your toes of one foot, while lifting the other in the air. Keep your audience behind you at a 45 degree angle for optimum levitation illusion. In the second method, cut a slit up the front of a pair of pants to your waist. Tape the very bottom of your pants together. Next, take the shoelace out of one of your shoes (this should be the same side as the pants leg with the...

If you are going to a toga party or just want to be prepared in case you need to improvise some clothing you will want to know how to tie a toga around yourself. This video will instruct on two ways you can tie a toga for men or for women.

This video is about using the grouping factoring method. We're using a four term polynomial. There is a even number of terms. We can break them into two groups of 2. The first group of "2" the common factor is "a." The last group, the common factor is "-2b". The reason we use -2b is to assure that what is in the first group is the same as the second group. Because of the distributive property of multiplication over addition, we take the a-2b and put it in one bracket. Multiply by 3x+1. With 6...

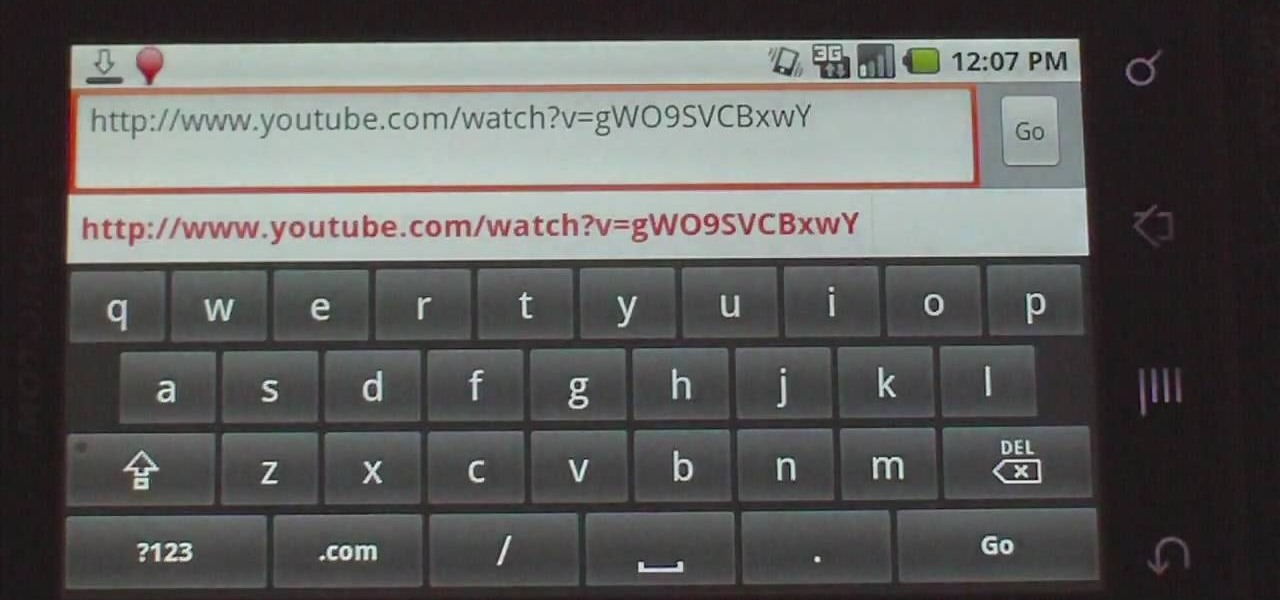
This how-to video explains how to copy and paste text in the browser in a Motorola Droid phone.

To prepare for planting take a fork and poke it into the ground and loosen up the ground. Do this throughout the beds so that the ground is completely loosened up. After you finish loosening the soil take a shovel and dig to the bottom of the bed and turn the soil over. If there are leaves in the bed go ahead and turn the leaves over into the soil. It will provide extra compost for the soil. Add some rabbit manure to the soil to provide extra nutrients. Turn the manure into the soil so that i...

Sunny Anderson prepares tasty shrimp pot pie that's easy for anyone. Follow along for this easy to make real food shellfish recipe.

Want to play lead guitar in a rock band? Well first you have to learn techniques from the masters. This two part guitar lesson teaches you how to play the solo from "It's So Easy" by Buddy Holly on the guitar. Once you get a hang of these popular guitar chords and tunes, you can start incorporating them into your own songs. With this lesson and a bit of practice you will be able to play the solo from "It's So Easy" by Buddy Holly on the guitar. The next time you are with your friends you can ...

Want a new way to solve the OLL (Orientation of the Last Layer) on a Rubik's Cube? Well, go no further, this video tutorial will show you how to use the 2-Look OLL method to solve the Rubik's Cube.

Hacking an Easy Button? Easy! In this video tutorial from Make Magazine's Kip Kay, you'll learn to hack the Staples Easy Button to say whatever you want it to. For more information, including step-by-step instructions on replicating this hack at home, watch this how-to video.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

Slack is meant for business, but it's inevitably used for personal reasons too, or even just to goof off with colleagues. However, you never know who's looking over your shoulder (nosy coworker? boss?), and you could get in trouble for something sent to you. That's why you might want to hide images and GIFs to help keep your conversations private.

Who's ready to let future Facebook augmented reality smartglasses read their brain? Well, ready or not, the tech giant is making progress in the area of brain control interfaces (BCI) by funding research.

Whether you're used to 3D Touch or Haptic Touch, deleting and rearranging apps and folders on your iPhone is a little bit different in iOS 13.

After two dramatic Conference Finals, the dust has settled to reveal ... the Golden State Warriors and the Cleveland Cavaliers. Well, at least the Irving-less Celtics and Rockets (short of Chris Paul for Games 6 and 7) gave it their all. With these teams battling for the fourth straight time, people want to know if the Cavs can even up the score at 2-2.

Android has gotten significantly better at handling intrusive ads over the years. Things have gotten to the point to where these nuisances are largely a non-issue for most of us. However, there are still a few ad-laden apps that fall through the cracks — particularly the kind that bombard your lock screen with ads.

If you're anything like me, when you first find a good song, album, or playlist on Spotify, your initial reaction may be to share it with your family and friends. While there are the usual share methods available in Spotify that are available in other streaming music services such as Apple Music and Google Play Music, Spotify goes one step further with QR-like codes users can easily scan.

If you want to automate tasks with your smartphone, IFTTT is a great app. It does a tremendous job of helping you find applets or creating your own from scratch, so it's easy to connect your favorite online services and make them react to each other. With all this personal information, though, you should ensure that your data is secure by enabling two-step verification.

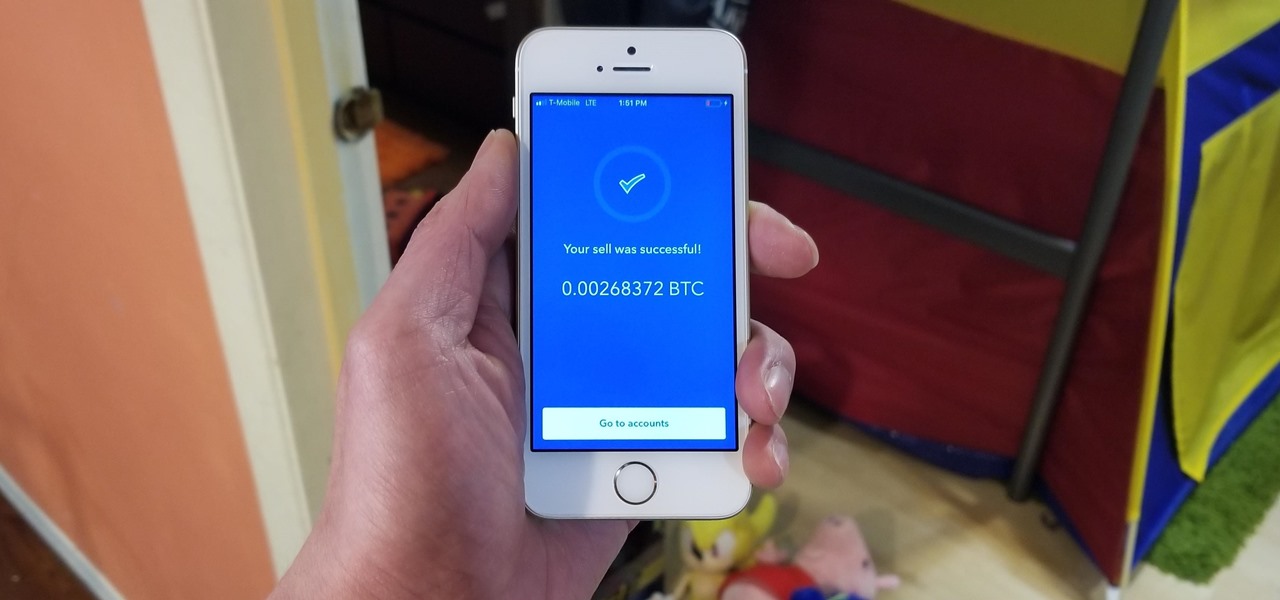
Coinbase has become the most popular mobile wallet app due in large part to its user-friendliness. The app takes the hassle out of buying and selling Bitcoin (BTC), Bitcoin Cash (BCH), Ethereum (ETH), and Litecoin (LTC), letting Android and iPhone users alike trade their favorite cryptocurrency in a few easy steps.