These days, if you walk through Best Buy, you will see an entire area designated to smart home technology. Thanks to the interest and growth of the Internet of Things (IoT), this exciting new technology has finally entered the mainstream. Appliances, thermostats, and even the lighting throughout your house can be controlled from your computer or smartphone. You could also use artificial intelligence; Simply tell Amazon's Alexa what you want your house to do, and she will do it.

Backdoors are convenient to leave behind once you've already found a way into a server, and they can come in handy for a variety of reasons. They're good for developers who want a quick way into machines they're working on, or for systems administrators who want similar access. Of course, backdoors are also a hacker's best friend, and can be added in a variety of ways. One good tool for doing this is Weevely, which uses a snippet of PHP code.

WordPress did not become what is arguably the most popular blogging and CMS platform on the planet because it was difficult to use. Rather, its user-friendly and rich feature set led to it finding a home on somewhere north of 70 million websites—and that's just counting blogs hosted on WordPress.com.

Robots are always really cool, if you ask me. Sometimes they're made out of Legos, and that's even cooler.

With the release of the HoloLens, Microsoft has put itself in both a great position while giving the competition a serious target to aim for. This is normally the case for anyone that is first to the market with a new idea, and now we've finally got a good competitor HoloLens coming. Stereolabs, a company known for its impressive 2K stereo camera, will be entering the mixed reality head-mounted display space with a Developers Kit as soon as early-2017.

This morning, Google opened a pop-up showroom where anybody can visit to get a hands-on look at the new Made by Google hardware lineup. At 10 am the line at 96 Spring st, in the SoHo neighborhood of New York City, was growing but still manageable. As we waited to be ushered in, Google representatives came by to offer us coffee drinks prepared by a pair of baristas in the Peddler Coffee cart parked on the curb. "Now that's latte art," said the guy in line next to me when he saw that the foam-t...

Now that we've talked about encryption and managing your passwords, let's continue this series on getting your Mac ready for hacking by turning our attention to the terminal.

Now that we've learned about keeping all our data safe with encryption, it's time to continue progressing through getting your Mac set up for hacking.

There's a new operating system on the horizon, and this one's so big that it may actually live up to its galactic moniker. Andromeda, a merging of Android and Chrome OS, has the potential to bring Google to the ubiquitous status that Microsoft's Windows enjoyed in the '80s and '90s.

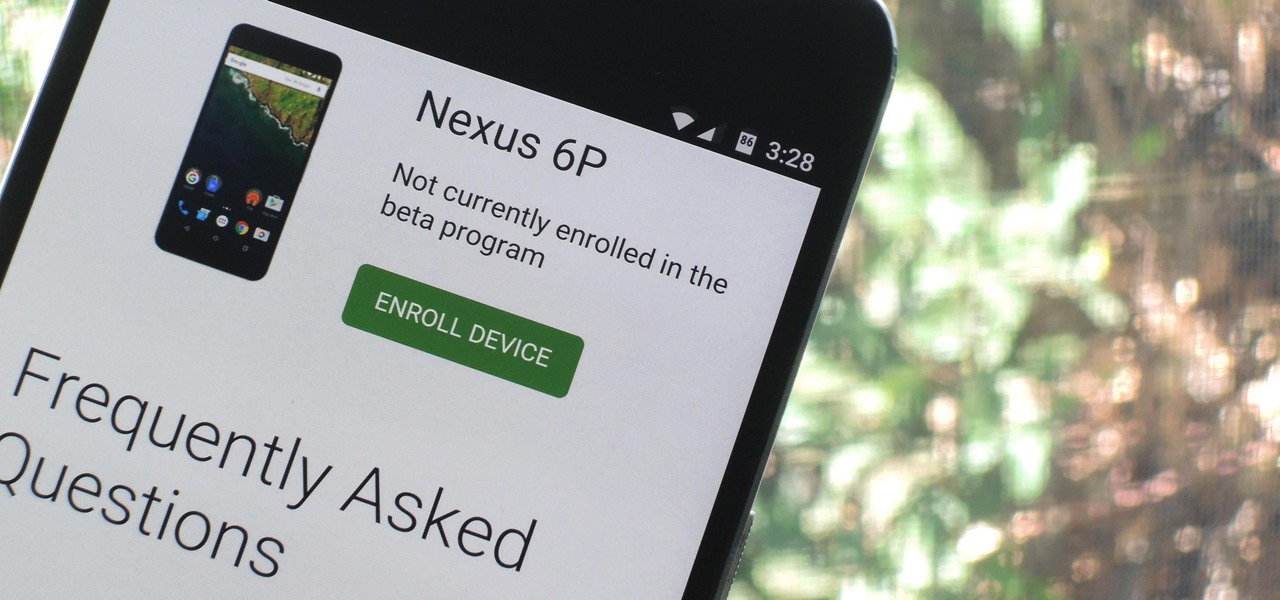
Google just released Android 7.0 Nougat, and as usual, they're doing a staged rollout. This means that most users won't actually get the update on their Nexus devices for a few weeks—that is, unless they take matters into their own hands.

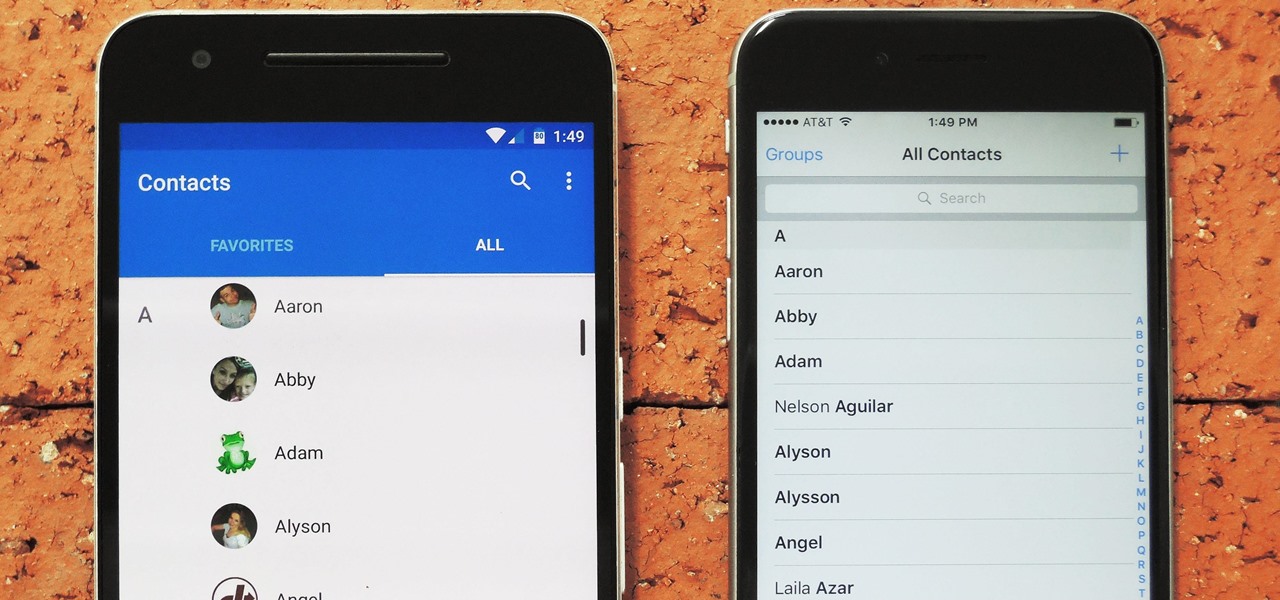
Switching between mobile operating systems is fairly easy, but there are a few bumps along the way that you're bound to encounter. One of the first issues you'll run into is that the contacts on your old iPhone don't easily sync with your new Android device.

Augmented and mixed reality experiences attempt to break us out of windowed computing experiences and allow us to place software anywhere in the room. But that software doesn't have to take a rectangular form—theoretically, the web doesn't have to restrict itself to a page in a browser any longer. Does this mark the end of the web browser entirely? Probably not. A lot of information works well on the page, and the Microsoft HoloLens still uses a pretty standard version of their own Edge brows...

Greetings comrades! Great leader has ordered that we gain intel on a website owned by the opposition. For all general purposes we will be scanning nmap.org because they really don't care if Big Brother decides to perform a whois on their IP. We will be using Dmitry for the scanning.

Virtual reality headsets are all the rage these days, and among the menagerie of tech companies gunning for the top spot, there's one mysterious startup that is ahead of the game—Magic Leap—and you can tell just by watching their latest demo video of their product in action.

You're only as smart as your communication skills allow you to be, as other people will simply never know your inner genius if you can't effectively express yourself. Regardless of the medium—be it a Facebook post or even a simple text message—this fact remains true.

You can use the F1 key to notably dim your Mac's display, but sometimes that just isn't dark enough. If you're working in pitch black conditions, have a migraine or tired eyes, or just want a more comfortable environment, you might want your screen even darker—without making it pitch black.

Near Field Communication, or NFC for short, is a feature that allows our smartphones to wirelessly communicate with other devices over a short distance while using almost no power at all. Think of it like a slimmed-down version of Wi-Fi or Bluetooth that can send a small burst of data two inches away without having any measurable impact on your battery life.

We knew it was coming eventually, but this is a bit out of left field—early builds of the next version of Android have been released almost two months ahead of schedule. Android N, as it's being called for now, is already available for the last two generations of Nexus devices, though it's just an early preview build for now.

Welcome to my very first tutorial ever. Today I will be teaching you how you can use Arachni to scan vulnerabilities of web applications. I welcome all criticism good or bad as a teaching method for myself.

continuing this series, I will now go in-depth on using advanced search queries. What Is Search Queries Again?

This article is to all the newbies on here wanting to become a hacker. Since I have seen many newbie questions on here, I need to address this.

T-Mobile's "Binge On" service for streaming videos has received mixed reactions so far. On one hand, it gives any T-Mobile subscriber unlimited access to popular streaming video services like Netflix and Hulu without having to worry about going over their monthly data cap. On the other hand, it reduces video quality to 480p, which is 6 times lower than full HD.

OS X is built upon a UNIX foundation, which grants you access to the benefits that UNIX offers, including the standard toolkit (make, gcc, clang, git, perl, svn, size, strings, id, and a lot more) via the command line developer tools, which are an essential if you're a developer. Aside from developers, the command line tools can offer benefits to normal users as well, like the ability to purge RAM for better performance.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

Before you sell or give away an old iPhone, Find My iPhone, which works in conjunction with Activation Lock (Apple's anti-theft system) needs to be deactivated from your iCloud account. This also applies if you've lost your passcode and are locked out of the device, if you're restoring to a previous iTunes backup, or just want to remove it from your list of iCloud devices.

There's a feature in Google's Photos app for Android, iOS, and the web that lets you create shared albums with your friends and family. It's really a useful feature that makes it fun and easy to collaborate on an album with a person or persons of your choosing.

3D Touch on the iPhone 6S and 6S Plus is a pretty cool feature, and will only get better as more developers begin to roll its functionality into their apps.

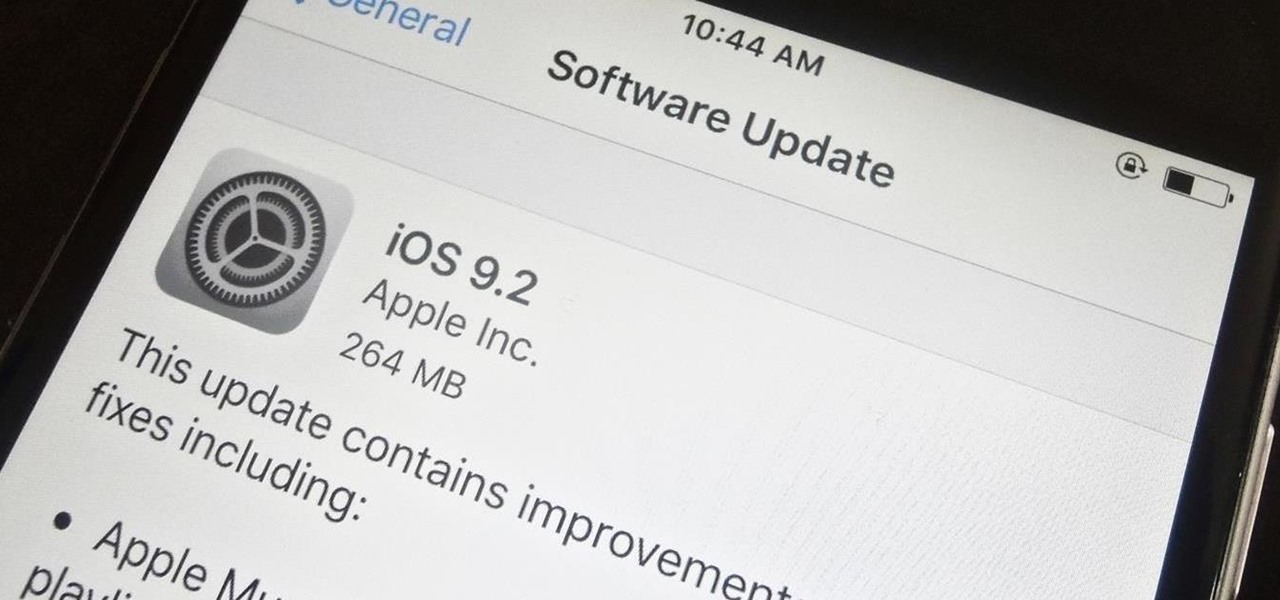
We're near the end of a productive year for Apple, one that introduced a new Apple TV, the iPad Mini 4 (in conjunction with the Apple Pen), the iPad Pro, and the iPhone 6S and 6S Plus, as well as iOS 9. Now, the second major update to iOS 9—version 9.2—has just been released to the public.

Hello! This is my first post on this awesome website! I know that Windows exploits are less common than the more advanced hacks, but I found something I deem pretty cool and figured why not share it with you all. Alright, enough about me, lets begin.

Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

This is my first tutorial on this website. So, if you think anything to be wrong, just place it in the comments.

Microsoft's "Fall Update" to Windows 10, code named Threshold 2, has a lot of new tricks up its sleeve. It's the biggest update we've seen since Windows 10 was released this summer, and it's rolling out to all users right now.

Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

Roughly four years ago, Adobe decided to abandon development of the mobile version of their popular Flash Player browser plugin. Their excuse at the time was that this move would enable them to focus more on HTML5 development for mobile devices and allow them to put more effort into maintaining the fluidity and security of their desktop Flash plugin.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.