
There has been a huge shift over recent years to alternative medicine as people get disillusioned with conventional medicine to overcome anxiety. Natural and herbal supplements are becoming popular as people re-engage with nature. The list of potential side effects from drugs and the rebound effects from withdrawing often make the thought of taking medication unpleasant. Often the promise of how effective the medication can be is exaggerated or it simply does not have the effect it should bec...

Although wear and tear on kitchen knives is unavoidable, it's extremely frustrating when I can't cut through tough, fatty tendons in meat or even make a clean slice through an onion. If you don't have a steel rod or water stone to sharpen your knives, or even a cheap knife sharpener, you can get creative by using a coffee mug and even a newspaper.

From laptops to tablets, technology is taking over classrooms. Elementary schools offer kids tablets, and college students are bringing laptops into lecture halls, leaving their notebooks behind. Today, many students prefer putting their fingers to a keyboard rather than pen to paper, but are these helpful devices truly beneficial?
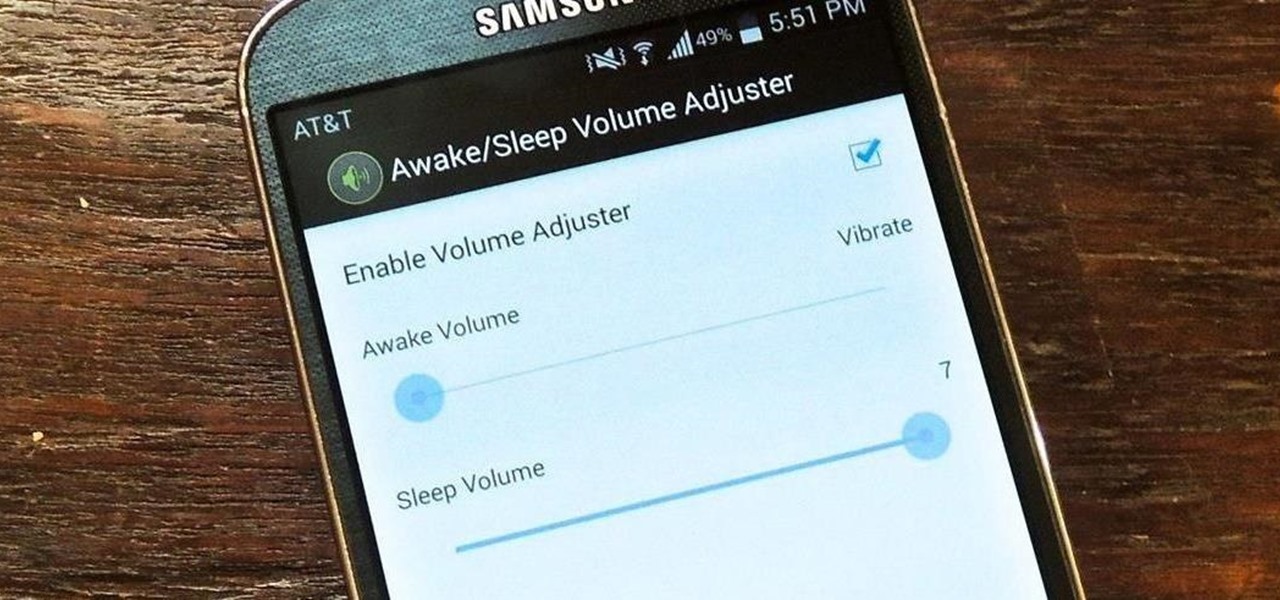
When I'm not actively using my Samsung Galaxy S4, I typically crank the volume up all the way so I can hear it in my pocket or if I'm in another room. But when it's in my hands and I'm using it, I don't want the ringer to blast at full volume, or any volume at all. Either I'll see a notification come in, or a quick vibrate will call my attention to any pertinent alerts.

There are many mods and tweaks you can do on your Samsung Galaxy S4 to make it feel more fresh, like using a more customizable keyboard and a better PIN unlock, but if you want to make your Galaxy S4 feel even fresher, add a little Galaxy S5 touch to it.
Conversations can be a little stale sometimes, so a little color help add some life. AOL realized this In the early days of AIM, and let you customize your colors just the way you want. Unfortunately, Apple doesn't let you go into your settings to customize your messaging app's colors, but with this awesome and effective tweak you can. All you need is a jailbroken iOS 7 iPhone or iPad, which is easily achieved.

Quickness and efficiency should always be a fundamental aspect of the experience when using any Android device. Anything less, and we've got a problem. As app development continually progresses, these adjectives become much more refined and polished, making the use of a smartphone a flawless affair of swipes and gestures.

By Zech Browning Shihan of Gyodokan Martial Arts. Step 1: "Storm Within the Calm - Putting It All Together - Part 1"

I'm all about safety in my life. I even put on safety goggles when someone opens a bottle of champagne—high life problems. But when it comes to driving, you have to be double safe, because the other drivers on the road may not have your safety in mind.

There are many ways you can protect your computer from unwarranted access. For instance, you can use Lockscreen Pro to lock your Windows 8 computer and then have the program snap a photo of the culprit using your webcam.

Nachos are one of those foods that are really hard to hate. Cheese, salsa, guacamole, sour cream...what's not to love? They're a favorite at Mexican restaurants, concession stands, and even inspired their own kind of cheese, so what's the downside?

If you don't have a car, or just prefer to take public transit to work, you know that an unexpected change in the weather can quickly...er, dampen your day. If you're not expecting it, rain or snow can turn your trip into a long, hellish ordeal—especially if you bike.

While the heyday of the Slinky may have been a few decades ago, I still think it's one of the coolest toys to ever go to market. Not to mention it probably has the best commercial ever created.

There are plenty of times when it would be nice to be able to give other drivers a piece of your mind, or let them know you're having car trouble so they go around instead of riding your bumper.

LEGO has not attempted a blimp, zeppelin, or similar airship since 1999, the 5956 Expedition Balloon which used highly specialized parts. This is unfortunate as these vessels are well and truly part of the pulpy adventure and steampunk scene.

Keyless entry remotes are great, but they don't always work how you want them to. One of the most common complaints is that they just don't reach far enough, and there's nothing more annoying when you can't remember where you parked. After all, what's the point of having "remote" entry if you have to be right next to the car for it to work?

Wall Anchors. Drywall Wall Anchors. Plasterboard Wall Anchors. I discovered these plasterboard (drywall) anchors / plugs a few years ago and think they are fantastic. They are ridiculously easy to use and are extremely effective in attaching fixtures to walls. One of the main things to be aware of (as with all things that have fixtures hanging from them) is the recommended maximum weight loading of each size of anchor. What ever the packet says, adhere to it.

In this video, Dina Prioste shows us how to do an effective hip stretch with yoga. First, sit in front of a pillow and tie a yoga strap around your waist and feet. From here, tighten the strap as much as you can to bring the heels in so you are held into this position. Now, lie down comfortably onto your pillows and remain in this position for several minutes while deep breathing. Close your eyes and try to clear your mind as much as you can. The more you let go, the more your hips and chest ...

If you're having trouble with the Act 1 quest 'Act of Mercy' in Dragon Age 2, or just want to bask in watching a really good gamer discuss his craft while he pwns, watch this video walkthrough, watch this series of three videos and take them to heart.

Step1. Make sure you get your facts straight. Note down the dates, names, and numbers, what was said etc while talking over the phone. It is also essential that when you present your letter of complaint that it is chalked full of facts so that when it reaches a decision maker you may get justice properly. Do not write a novel that is 30 pages. Keep it short and write in bullets. Remember that they are interested in facts only.

Marriage isn't always easy, and there are going to be times when you irritate your husband so badly that the relationship may seem to be in jeopardy. If you want to apologize effectively but aren't sure how, this video will give you some tips on making an honest, heartfelt, effective apology that will get your marriage back on track.

Proper form is very important to lifting weight and strength training. One wrong move could potentially lead to an injury. Follow along in this how-to video critique by Mark Rippetoe as he guides someone through the correct lordotic arch position in bench pressing. Better posture can lead to more effective lifting. Learn to maintain the lordotic curve in your back when doing a bench press.

Are you lost? This how to video teaches you a simple way to turn your watch into a compass. An analog watch is even more effective than a compass because it is not influenced by the earth's magnetic fields. You'll never be lost again as long as you have an analog watch with you.

Space marines are one of the easier armies to build and effective for Warhammer 40k. There still is some skill involved when picking out the figures for the space marine army. Watch this video tutorial and learn how to build a space marine army for Warhammer 40k.

Eliminate pests like ants, termites and mice without using dangerous chemicals. Watch this how to video to learn easy and effective ways of getting rid of small pests that come inside the house.

A short introduction to a method of applying modes to chords. Very simple and effective. Find the tab and full descriptions at http://betweenthelicks.com.

In this video drum lesson, you will learn how to take any regular drum beat, and change it up by playing the snare shots with cross-sticking. This is a simple and effective way to dramatically change the dynamics of any drum beat.

An effective way to get rid of excessive body hair. There is no pain with the treatment.

Want to play a beautiful version of "Beautiful Day" by U2? See how it's done with this free video guitar lesson, which presents a complete (and we mean complete) breakdown of the song and its constituent parts. While this tutorial is geared toward those who already have some knowledge of the guitar, players of all skill level should be able to follow along given adequate time and effort. For more information, and to get started playing "Beautiful Day" on your own guitar, watch this video guit...

Want to play "Until the End of the World" by U2? See how it's done with this free video guitar lesson, which presents a complete (and we mean complete) breakdown of the song and its constituent parts. While this tutorial is geared toward those who already have some knowledge of the guitar, players of all skill level should be able to follow along given adequate time and effort. For more information, and to get started playing "Until the End of the World" on your own guitar, watch this video g...

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

In case you hadn't heard, Google is now a legit cell service provider. Google Fi has its pluses and minuses, but the biggest upside is in the pricing. Depending on how much data you typically use, there's a good chance you could save a lot of money without sacrificing coverage by switching to Fi.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

If you have encountered bed bugs lately, you are not alone. While the pesticides used to fight these pests are losing effectiveness, a fungus shows promise in knocking the bugs out of beds everywhere.

We can add one more health effect of our gut bacteria to the growing list. Researchers from the UK have just reported that the gut microbiota plays a role, both directly and indirectly, on the toxicity and efficacy of chemotherapy. Their findings are published online in the journal Nature Reviews Gastroenterology & Hepatology.

Bacteriotherapy sounds a lot more amenable of a term than "fecal transplant," yet they're both treatments that use bacteria itself to cure or treat infections. Fecal transplants, specifically, are an up-and-coming treatment option for a potentially deadly and difficult-to-treat diarrheal infection called Clostridium difficile.

Cleanliness is next to godliness. My interpretation of that age-old adage means that keeping your house clean is just as un-fun and boring as being a goody two shoes. That's why they call things like laundry and doing dishes "chores," I assume. Yuck.

We already know that Samsung's Galaxy S7 is one of the most versatile smartphones ever made, complete with edge-to-edge displays, water resistance, and a huge battery. But what's versatility without durability? How much punishment can the Galaxy S7 take? Let's play a game of Samsung Galaxy S7 Punch-Out!! and see what happens.









































