The emergence of Microsoft's HoloLens 2 as a cutting-edge US Army tool has focused a spotlight on the marriage between augmented reality and the military.

Consumers who haven't already delved into the interactive wonders of augmented reality are about to be pushed into the immersive waters by market forces.
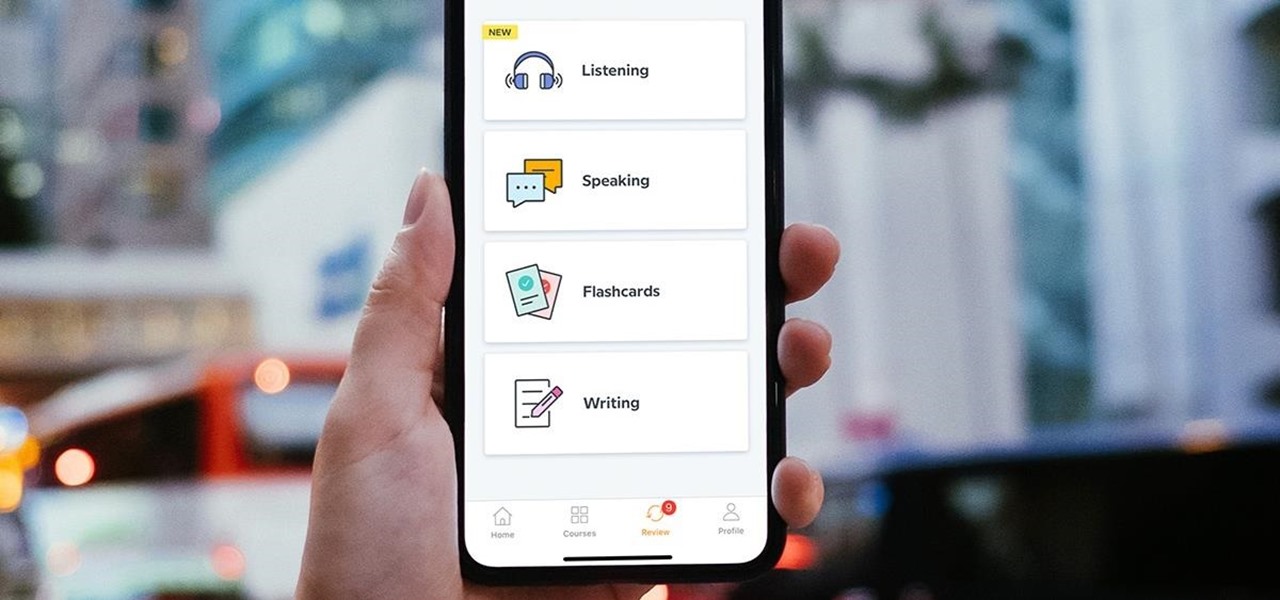
Learning a new language as an adult isn't just hard because your brain works differently from when you were a kid. You also have to contend with having less time and energy to practice. However, if you're looking to add another language to your repertoire at a pace you decide, then the Babbel Language Learning: Lifetime Subscription for All Languages: 2-Pack will be a useful tool for you.

As if teasing its own smartglasses weren't enough, augmented reality gaming developer Niantic gave gamers a glimpse of how 5G speeds can revolutionize how they play mobile games in the near future.

Even as the world continues to grapple with the pandemic, the tech industry continues to chug along, with some looking for ways to present new products, and in some cases continue major conferences that reveal the latest in augmented reality developments.

Two of the three entities behind Pokemon GO, the reigning champion in mobile augmented reality gaming, are joining forces again to see if lightning can strike more than once.

Like the layers of an onion, 2021 continues to peel back new hints of Apple's kinda-secretive augmented reality device development.

If you've been thinking about changing careers and you have just a little bit of time, The Ultimate 2021 Web Developer & Designer Super Bundle may be just what you need. This is also the perfect time to get it because it's on sale for $34.99, which is 98% off the regular price of $1,886. You'll get 14 courses that offer 39 hours of content on HTML, JavaScript, CSS, and more.

Everyone needs a great website. Whether you want to launch the new business you've been dreaming about in 2021, increase your brand's web presence and bring it into the digital realm, or promote yourself and your portfolio, a fully optimized website is the way to do it — and the results can be life-changing.

Rumors of Apple developing smartglasses have persisted as prophecy since 2016, but the arrival of what many herald as the savior of augmented reality have eluded even Nostradamus himself.

You're in the middle of the fight for your life in your favorite iPhone game when all of a sudden, that critical move you tried to make activates Control Center inadvertently, throwing you completely off track. Instead of fuming, do something about it — block Control Center when you're in apps.

Last year this guy made his own smartwatch from scratch, so in 2020, naturally, he decided to give making smartglasses a try. And it worked!

Effective communicators are always in high demand in every industry. Whether your team is building the next billion-dollar app or you have a giant data set in front of you for filtering, communicating with your team is essential.

While the stock market can be unpredictable, it's not a complete enigma. There are patterns to watch for that can make you a successful trader. Fortunately, there is an expert guide to becoming an analyst that's now available to everyone.

Good communication is essential when managing teams and overseeing complex projects. Whether you're developing the latest and greatest app or trying to get ahead of a large data science project, effective communicators are always in high demand.

For the last three years, Apple has hosted its Worldwide Developers Conference at the San Jose Convention Center, but thanks to the COVID-19 pandemic, WWDC 2020 is now an online-only event. So what can you expect from the new virtual format and when and how can you watch the keynote and developer sessions?

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

When it comes to iOS beta updates, developers get their updates first, and once they do, public testers play the waiting game. Sometimes Apple releases the public version three hours later. Other times it waits 24 hours. It's a roll of the dice almost every time. As for iOS 13.4 public beta 2, it's the latter case, coming exactly one after developer beta 2.

Last week, Apple released the first iOS 13.4 beta with fun and useful new features, such as new Memoji, an upgrade Mail toolbar, and the ability to control your NFC-compatible car via CarKey. To add to that, Apple just released iOS 13.4 developer beta 2, but does the update have any more new changes to be excited about?

The words of three of tech's most important executives in the last 48 hours are providing some valuable insight into the near term future of augmented reality and the cloud infrastructures that support it.

This week, the beginning of an epic legal battle was set to begin between augmented reality players Magic Leap and Nreal, the small China-based startup accused by the former of stealing trade secrets.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

With EA chief executive Andrew Wilson stating the official mobile version of Apex Legends won't arrive until the 2021 fiscal year, fans have to wait at least another year to enjoy their favorite battle royale game on the go. But for those who can't wait, there are ways to play the game on iPhone and Android right now.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

On Monday, Apple unveiled its Apple Card, the company's boldest move yet toward becoming a truly mainstream mobile payments company. And the product has vast implications for our augmented reality future, some of which may not be immediately obvious to many.

Microsoft Office files can be password-protected in order to prevent tampering and ensure data integrity. But password-protected documents from earlier versions of Office are susceptible to having their hashes extracted with a simple program called office2john. Those extracted hashes can then be cracked using John the Ripper and Hashcat.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

Your iPhone is just that — yours. Why should your home screen look like everyone else's? While iOS, and by extension, Apple, famously locks its users into its way of doing things, there's a lot more room for customization than you'd think. Before you make the switch to Android, you might want to see what you can do with the iPhone you already have.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

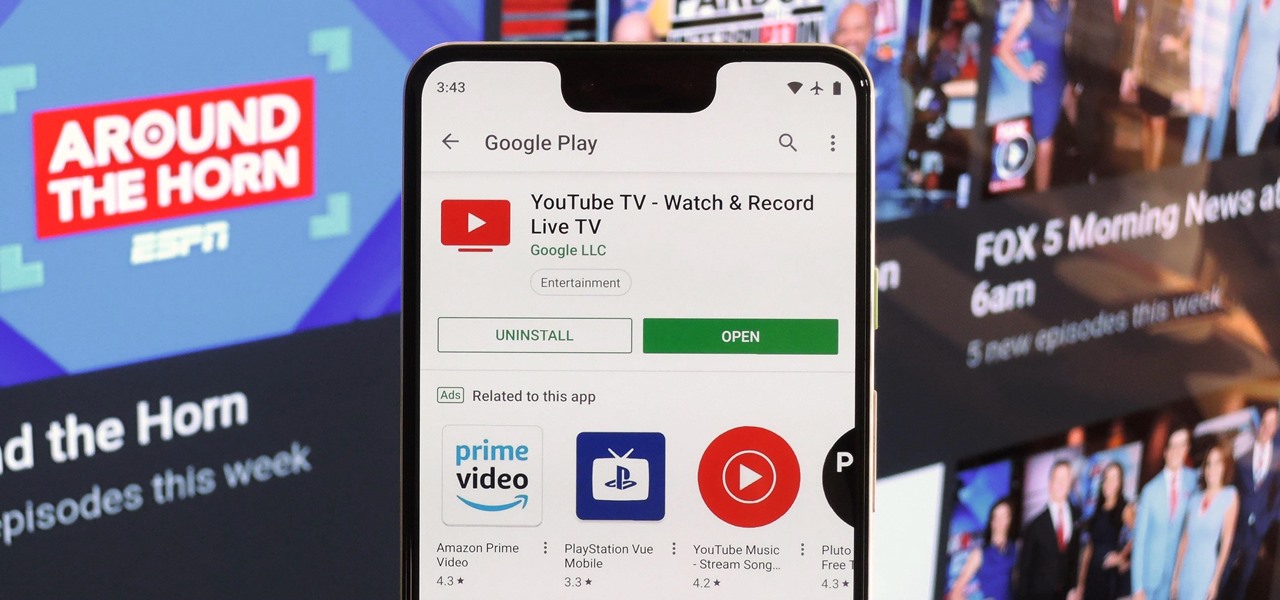
With YouTube TV and DirecTV Now starting at $40/month, and others like Sling TV offering an eye-catching $25/month plan, streaming cable services may sound like a great way to cut costs while cutting the cord. But when you look at all the factors, the price you pay may very well end up being just as high as your traditional cable bill — if not more.

Mystery is a tricky thing. Used correctly, it can give onlookers the impression that wondrous and perhaps valuable things are afoot. However, once the veil of suspension of disbelief is removed in any significant way, that same mystery can quickly turn into not just skepticism, but outright anger at what may have seemed like an attempt to dupe trusting onlookers.

On Tuesday, the smartglasses startup known as North finally took the wraps off its Focals product, but in a very unique way: The team simply opened a couple of stores and invited the public in.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

Like many things associated with Magic Leap, the start of the company's first annual L.E.A.P. conference got off to a unique start. Taking the stage on Wednesday morning in Los Angeles, the company's CEO, Rony Abovitz, gave a brief introductory speech welcoming the crowd and outlining the mission of Magic Leap.

One of the first steps in reconnaissance is determining the open ports on a system. Nmap is widely considered the undisputed king of port scanning, but certain situations call for different tools. Metasploit makes it easy to conduct port scanning from directly inside the framework, and we'll show you three types of port scans: TCP, SYN, and XMAS.

One of the primary marketing tactics used by Magic Leap in promoting the Magic Leap One was selling early adopters on the "magic" contained within the device. On Thursday, some of that magic was uncovered as the Magic Leap One was completely disassembled by repair engineers, revealing the delicate innards of the device and detailing how it delivers its augmented reality experiences.

Yesterday, I talked about what I think is the most immediately mainstream-friendly app on the Magic Leap One is (Screens), and now we'll touch upon the runner-up: Helio.

I've had a few days to live with the Magic Leap One, and it's time to finally weigh in with some thoughts as someone who has been tracking this company from the beginning, for almost five years now.