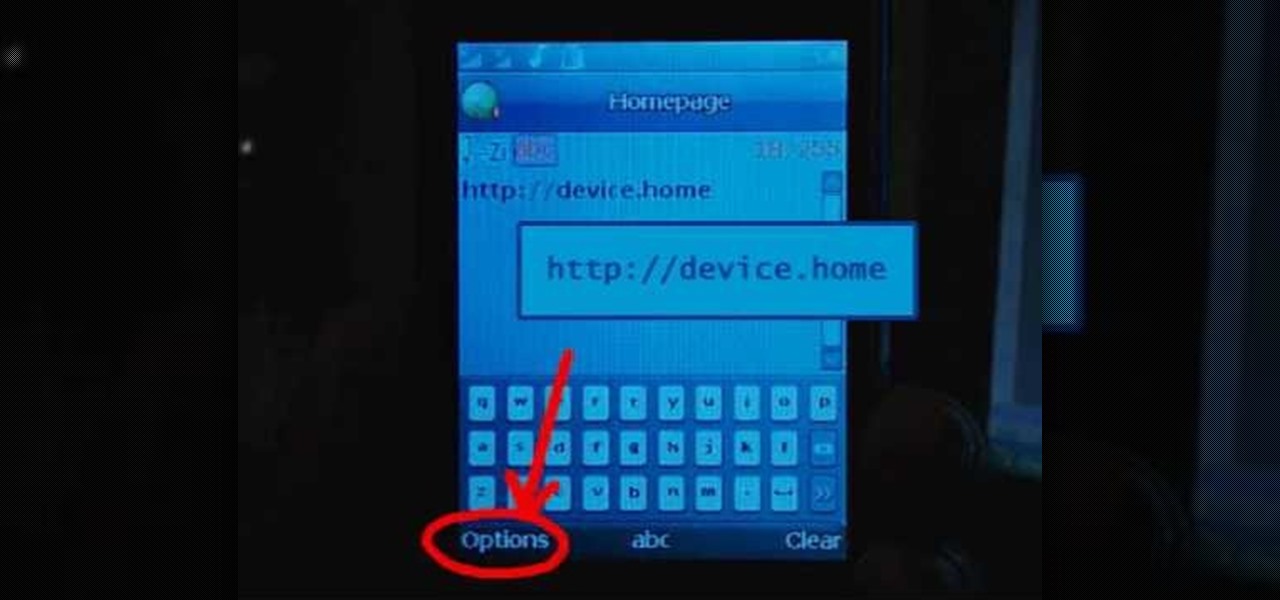
The video shows how to join a home group on a Windows 7 network by helves shows you how to join a home group on a Windows 7 network of computers. It is approximately one minute thirty seconds long. To join a home group on a Windows 7 network you first go to control panel, then you click on Network and Internet, after that you click on network and sharing center, and finally click join a home group in the top right. You now select what file types you want to share with the other Windows 7 comp...
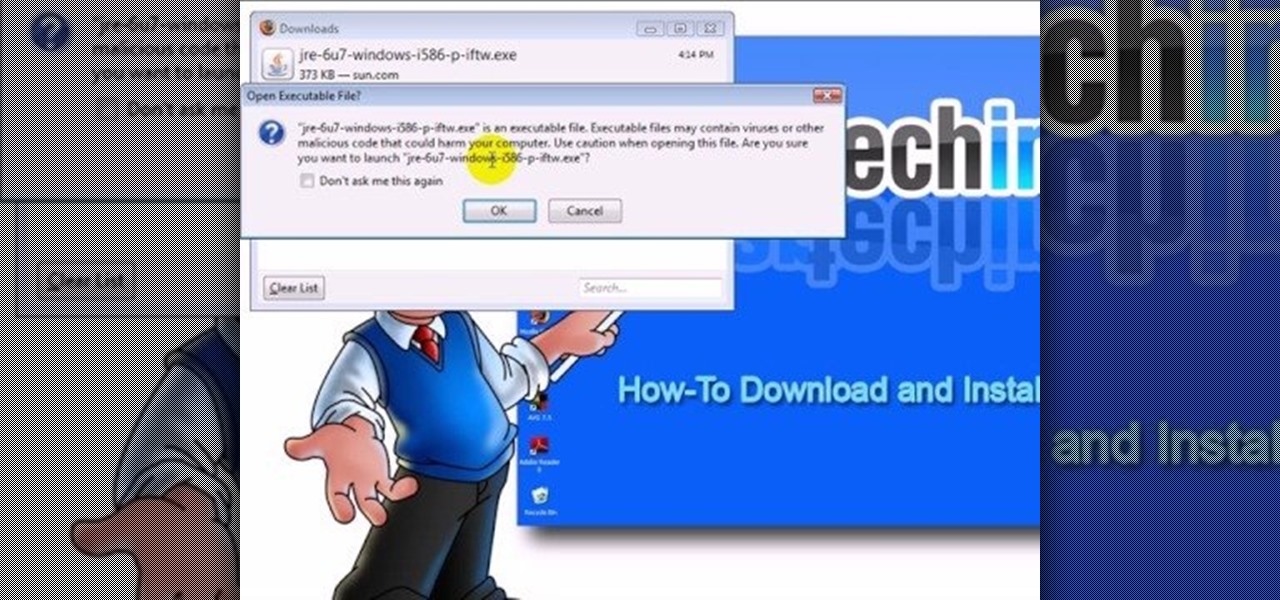
This video teaches "How to Download and Install JAVA plug in for your web browser". Open your web browser.
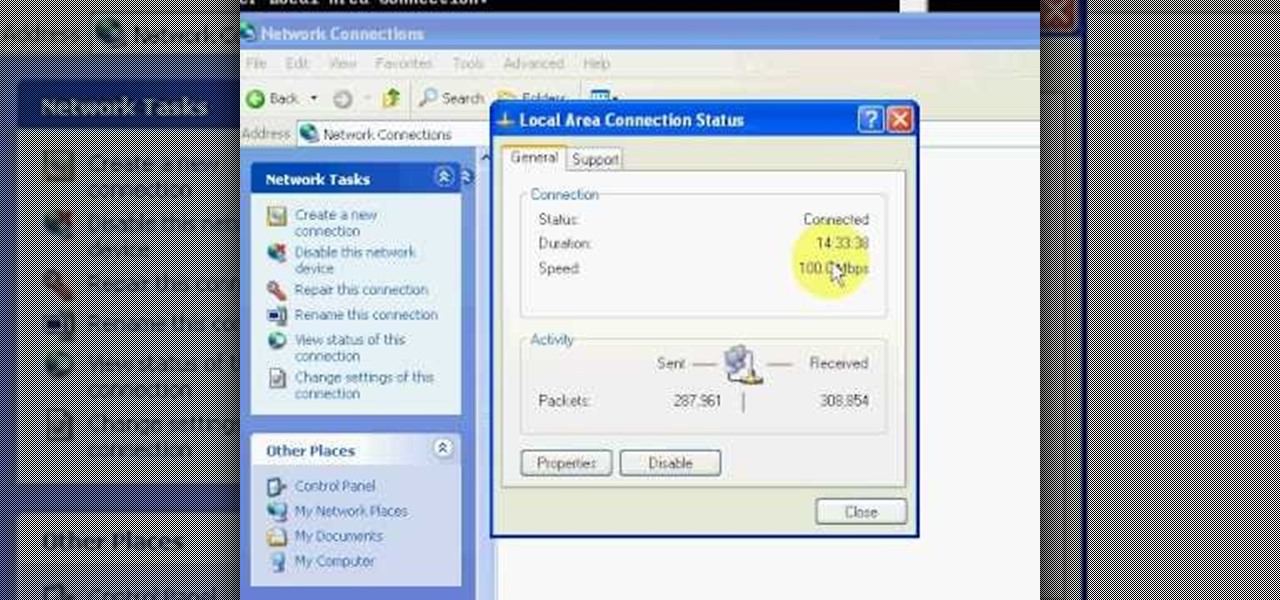
This video will show you how you can easily find out what your IP address is for a computer which is running the Windows XP operating system. You will first need to go to the start bar and click on the button which says "Run". Choose to run a program called "cmd" by typing this into the bar that appears. This will then open up a black box, where you should type in "ipconfig/all". Typing this in will offer you a list of information about the internet service you are currently using and one of ...
For people who would like to find an easy way to communicate with their loved ones via video or voice chat on their computer, this video will show you how to create and use a Skype account. After going onto Skype.com, you should download Skype, since you will not be able to use this without having the program on your computer. After downloading the file, you should then create an account on the program that appears, creating a username and password. By following these simple steps, anyone wil...

In this tutorial the author shows how to find, download and install Firefox 3. He points out to the Mozilla Firefox website which is [www.mozilla.org/firefox]. Now you reach the Firefox web page where there is a link to download the browser. After clicking the link you will be prompted to save the file and now you can download the software. Now after the software gets installed the author guides you through the various steps to get Firefox 3 installed. He also shows how to transfer settings a...

Is your PC too slow? Want your PC performance to increase without paying any money? Well, in this video the viewers will be taught how to speed up their PC and internet speed without spending a dime. First of all, the video goes through some of the potential applications that are draining the computers' resources, such as multiple anti-virus. The video teaches how to delete and remove unneeded applications and free up additional RAM. One of the key ideas is to close and disable applications t...

Learn how to set up Internet on iPhone clones with this video. *First thing you need to do is to make an AT&T GPRS data account.

This video explains how to make an Origami Icosahedron (designed by Heinz Strobl) using 50 strips of paper. You need 20 strips of a single color for the triangles and 30 of a contrasting color to connect the triangles.

Learn how to fold an origami dragon with instruction by Ancella Simoes. Ancella Simoes is the author of the Origamiancy Blog and creator of all the Origamiancy origami tutorial videos on WonderHowTo. From Ancella's site:

VNC stands for Virtual Network Computing. It is remote control software which allows you to view and fully interact with one computer desktop (the "VNC server") using a simple program (the "VNC viewer") on another computer desktop anywhere on the Internet. The two computers don't even have to be the same type, so for example you can use VNC to view a Windows Vista desktop at the office on a Linux or Mac computer at home. For ultimate simplicity, there is even a Java viewer, so that any deskto...

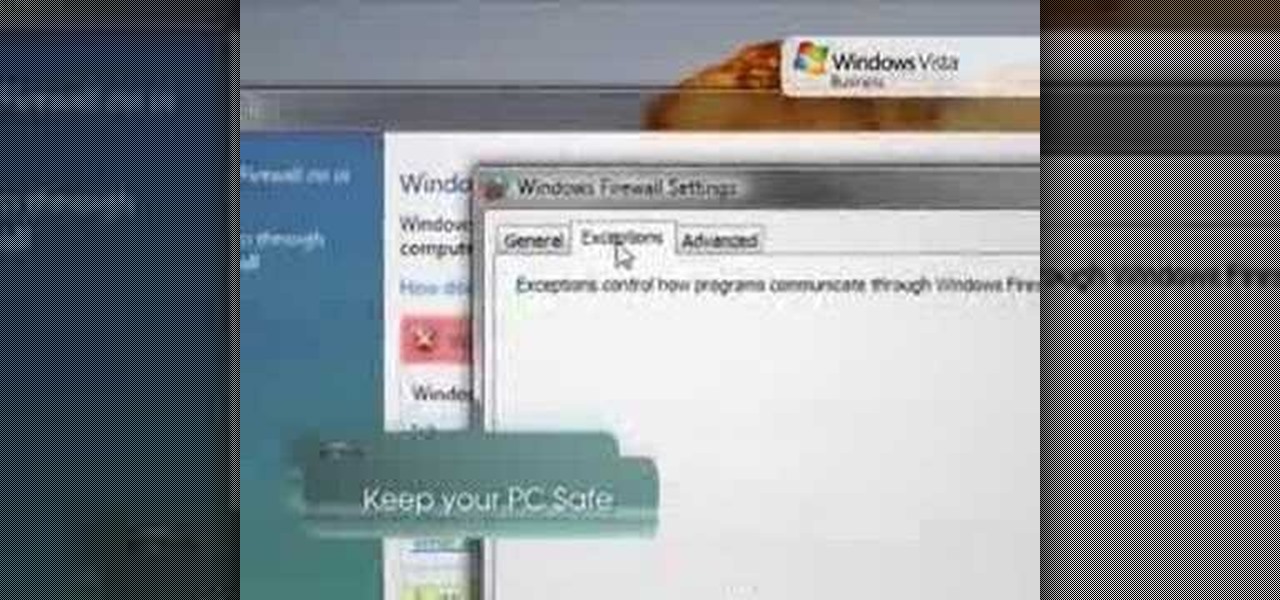
In order to keep your PC safe from annoying or potentially dangerous threats on the Internet, a properly-configured firewall is a crucial item in helping prevent your system from becoming compromised. The Windows Firewall in Windows Vista™ is the first line of defense in helping to keep your computer safe. By preventing your computer from being infected by malware, Windows Firewall is designed to be easy to use and is automatically enabled to protect your computer as soon as Windows starts. T...

A good video can turn a mediocre song into a smash hit, while a bad video. Well, that's just embarrassing. While MTV doesn't really play music anymore, the internet is flooded with good old fashioned music videos. This how-to video will offer some tips for making yours stand out of the crowd. You don't need to be too literal, but try picking a style. Watch this video tutorial and learn how to make a music video.

Here are five different techniques you can use to create rounded corners for boxes on a website. There are always different ways to do things with CSS and rounded corners is a great example of that. Each of these five techniques has advantages and disadvantages. Knowing all of them so you can choose the perfect one in each situation is the kind of thing that makes you the best CSS ninja you can be! So if you want to make cool Internet websites and be the best designer around, why not start he...

Plug this baby into your FiOS-powered computer and simulate the real-time climate of any location in the country -- rain, lightning, fog, sunshine.

This new episode of Full Disclosure shows you how to use a SSH Tunnel to secure your data when you are on an untrusted LAN (ex. Coffee Shop, School's network, or Defcon). Furthermore, you can use the SSH Tunnel to bypass the LAN's internet filters. The SSH tunnel protocol works by encapsulates your data into an encrypted payload and transmitting it to the SSH Server which is setup on a trusted LAN.

So, AOL might not be mailing as many internet CDs as they did in the past, but chances are you have a few of those junk discs lying around. Chances are you have tons of junk CDs and DVDs laying around, not necessarily from AOL. And now... it's time to turn them into something useful, or at least fun! Kipkay shows you how to build a mini-disco ball from those recycled discs, with scissors, hot glue and a styrofoam ball also needed.

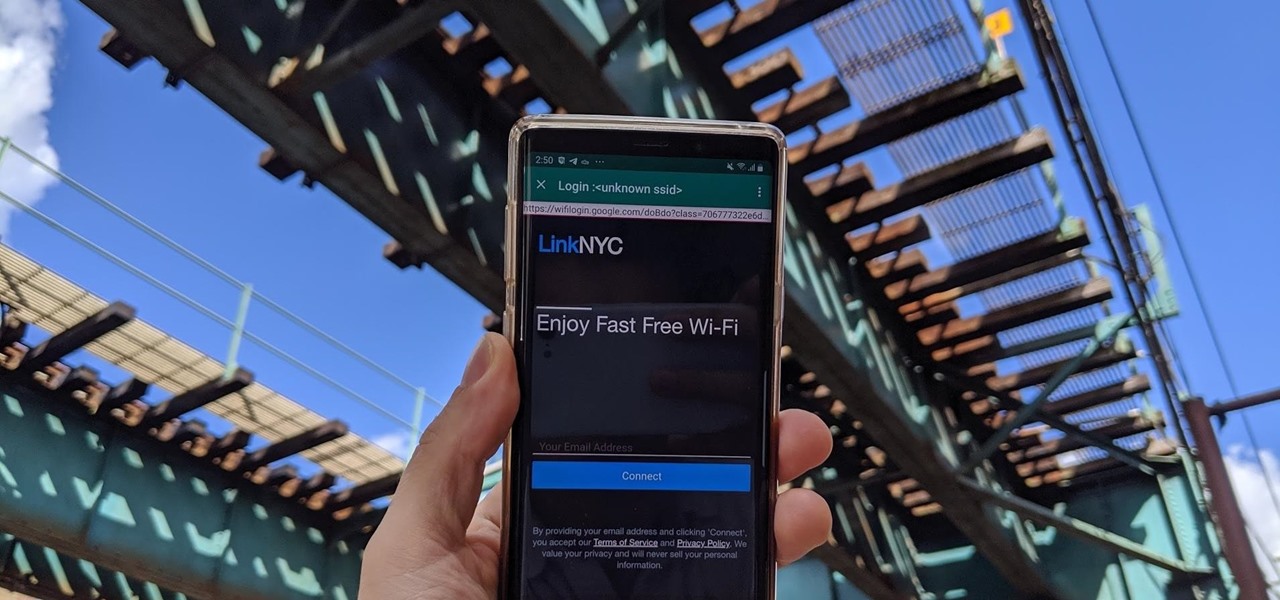
Public Wi-Fi networks that have a captive portal sign-in screen can sometimes be broken on Android. This seems to happen randomly and on some devices more than others. You'll get the "Sign into Wi-Fi network" notification, but it just doesn't work. If that's happening to you, you'll be glad to know an app can help fix the issue.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

When I'm with my friends on the weekend, we always end up Snapping shots of one another, adding in whatever stickers and lenses we've accumulated over the last week. But these filters are fleeting, so it's always a challenge to keep up with the best new ones. If you want to get a leg up on the competition, this is your one-stop-shop.

It has not been a good year for Apple, as far as software scandals are concerned. From autocorrect nuisances to secret slowdowns of aging iPhones, Apple has had a lot to answer for. iOS users now have another issue to worry about — it's being called "chaiOS," and it's wrecking havoc on iPhones with just a simple URL.

When you're on the go, Plex makes sure your media always stays with you. Just install the server app for Mac or PC and enable remote access, then you can stream movies and TV shows from your computer to your phone over the internet.

Antibiotics are one of our main weapons against infections. The problem is that many bacteria are becoming resistant to most of the antibiotics we use to treat them, and those 'superbugs' have created an urgent threat to our global health. A research group found a new way to hit a well known bacterial target and have developed a drug to hit it.

After laying off 40% of its staff this month to cut costs, SoundCloud appears to be struggling to stay afloat. While blog posts from the company have assured fans that the music platform is not in danger of shutting down, some people aren't so sure this is the truth. Internet Archive — a non-profit dedicated to preserving websites and services — announced today that they will be conducting a partial backup of SoundCloud to safeguard the site's content in case of closure.

One inventor wants to bring augmented reality to internet radio and home audio speakers. Meanwhile, a leading consumer electronics company has opened up access its deep learning tools for building augmented reality apps. In addition, analysts examine how augmented reality will impact the design and construction and profile the top developers in augmented and virtual reality.

At Facebook's first Communities Summit, admins from top Facebook groups assembled to discuss tools to better manage and optimize their members. Here, Facebook CEO Mark Zuckerberg announced that these changes fuel the company's shifting focus from connecting the world to uniting it.

The Centers for Disease Control and Prevention estimated that there were 212 million cases of malaria across the world in 2015, and 429,000 of those people died — mostly children living in Africa. Preventing and treating those infections has been a challenging world priority. That makes a new malaria drug discovery — published in Science Translational Medicine — incredibly important.

The Google Pixel was just knocked off its pedestal as DxOMark Mobile's best smartphone camera, courtesy of the HTC U11. Ouch ...

Nintendo's first ever game for Android has finally touched down (unless you actually count the abomination that is Miitomo). Fire Emblem Heroes, a classic turn-based RPG optimized for mobile gaming, has come out for Android and iOS in Australia, Europe, and Japan, and is due out in North America and other worldwide locales very soon. Due to Nintendo's staggered release, the game isn't available to us in the United States at the time of this writing, but fret not—there's another way to downloa...

No matter which smartphone you buy, it will come with an internet browser preinstalled. Depending on your OEM, the default browser might be called Samsung Internet, HTC Internet, Silk Browser by Amazon, ASUS Browser, or Google Chrome—there's just so many stock browsers available.

Augmented and mixed reality experiences attempt to break us out of windowed computing experiences and allow us to place software anywhere in the room. But that software doesn't have to take a rectangular form—theoretically, the web doesn't have to restrict itself to a page in a browser any longer. Does this mark the end of the web browser entirely? Probably not. A lot of information works well on the page, and the Microsoft HoloLens still uses a pretty standard version of their own Edge brows...

Today's pollution, hectic lifestyle, inadequate sleep and no time for pampering can leave your skin lackluster resulting in drying skin and making dry skin drier ultimately causing the early appearance of wrinkles and aging. A good fruit facial helps relax your skin from deep inside and the proper messaging gives it a rosy glow by increasing blood circulation imparting your face with a luminous glow. These are even better because they are natural and chemical free unlike the artificial facial...

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

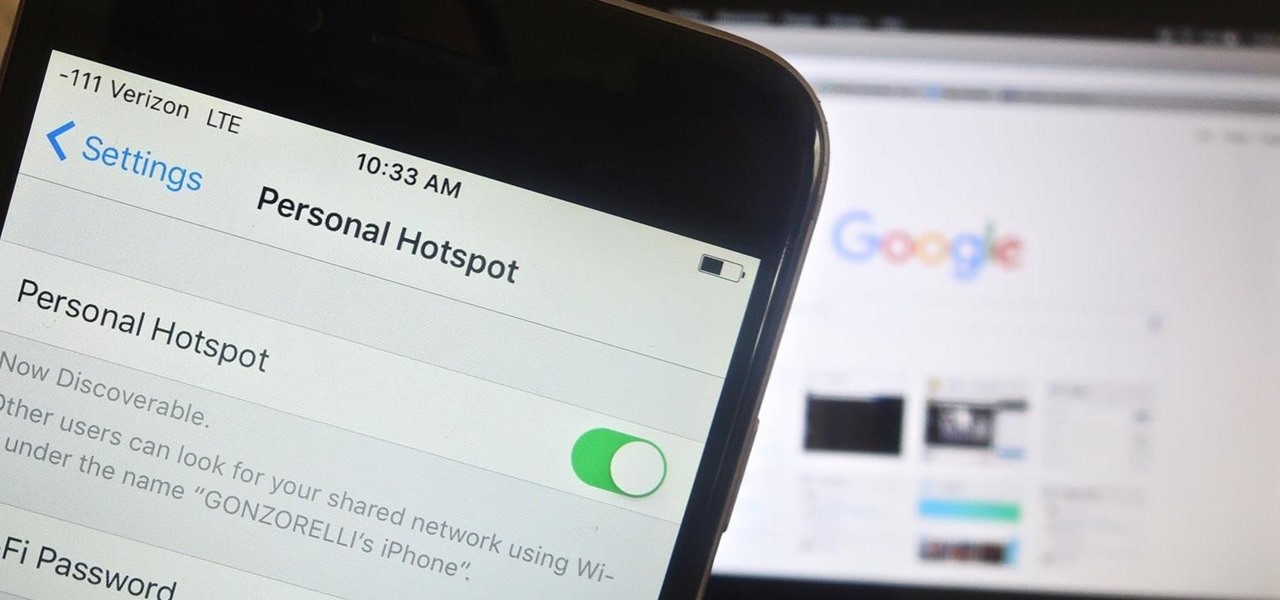
When you're in a bind and need an internet connection for your laptop, look no further than your iPhone. Using the Personal Hotspot feature in iOS, you can share your iPhone's internet connection with other devices by way of Wi-Fi, Bluetooth, or even USB.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

I'm lucky enough to have internet access on my laptop practically everywhere I go because of my mobile hotspot plan. All I have to do is enable the personal hotspot feature from my iPhone and I can surf the web on any Wi-Fi enabled device. But of course, there's a catch.

If you're just starting out with Android—or smartphones in general, for that matter—there are a lot of little things to learn. One of the first terms you'll likely encounter is "Wi-Fi," which is a wireless internet connection served up by a router in your home, office, or local coffee shop. This differs from your smartphone's regular "Mobile Data" connection, which is provided by your cellular carrier and included as part of your monthly bill.

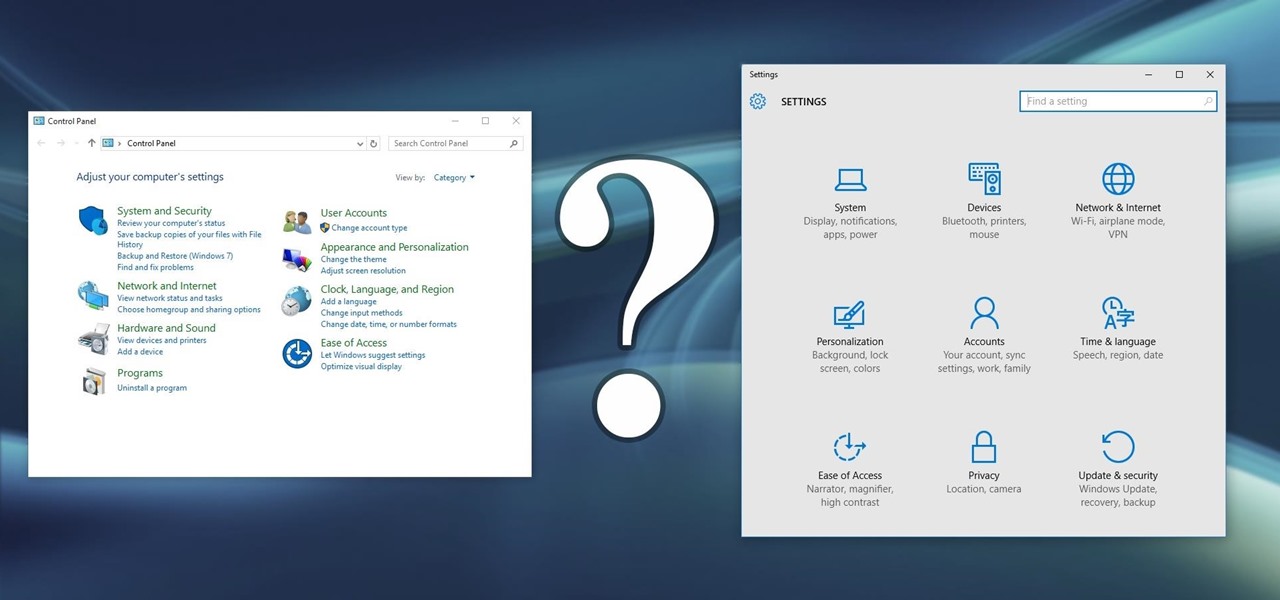
Slowly but surely, Microsoft is pushing more and more options out of the Control Panel and into a new menu simply called Settings. This new Settings menu debuted with Windows 8 and mainly focused on touchscreen-related options, but starting with Windows 10, you'll find quite a few general options residing here as well.

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.