Using your laptop you can set up a wireless internet connection at home. You will not need a wireless router to do this. You can turn your computer into a wireless internet access point and set up a local network to which other computers in your home can connect. This feature is recommended for those who have no existing network setup. If you simply have a computer connected to the internet then you would be not needing this. Go to your system preferences and select sharing. Click on the inte...

Learn how to connect a XBox 360 to the Internet via a Windows PC.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!
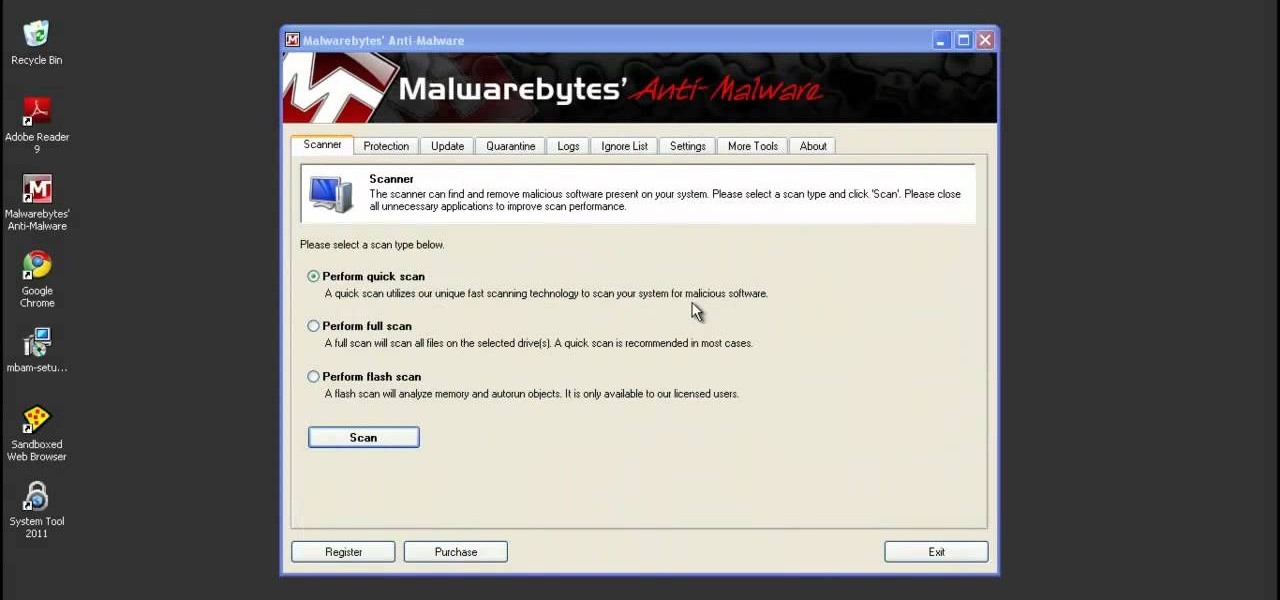
System Tool and System Tool 2011 are the most widespread fake-antivirus rogues on the internet today, infecting countless machines. This video will teach you how to uninstall both warez completely, returning your computer to blessed normalcy.

Congratulations, iOS device owners! You can officially view Flash content on the web using the Skyfire web browser. This video will walk you through how the Skyfire browser works and how it converts Flash content to HTML5 content, allowing you to view it on your Apple iPhone, iPad or iPod Touch running iOS. It's about time.
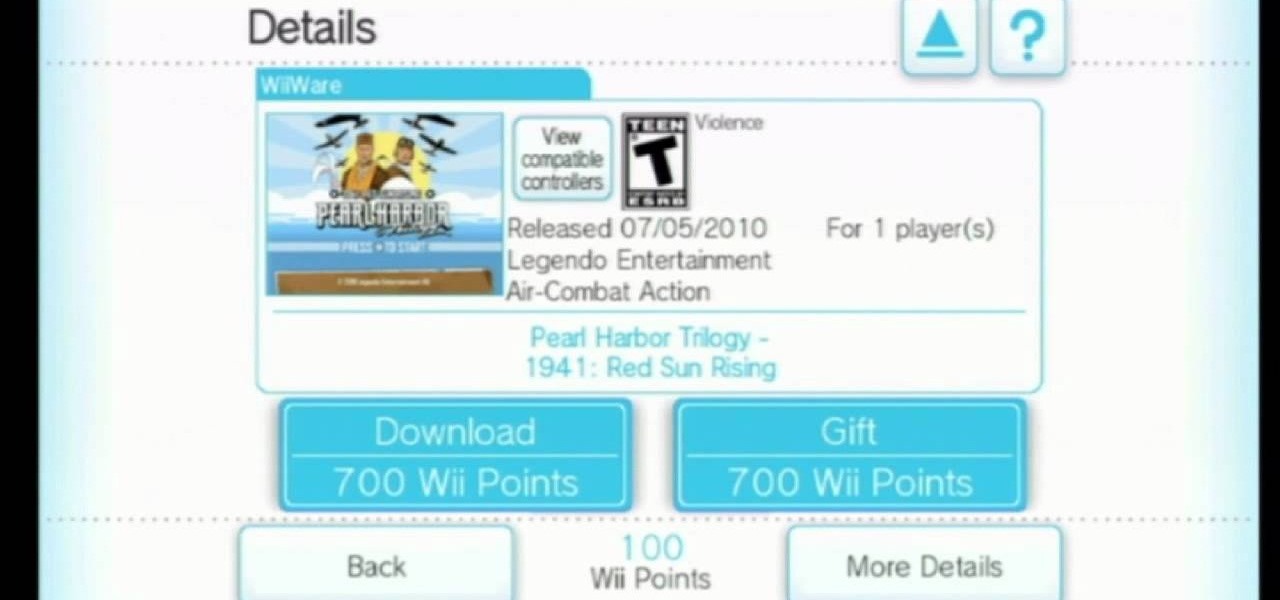
This video tutorial will teach you how to use the Nintendo Wii Shop Channel to download and play your favorite console games on your Nintendo Wii. To follow along, you'll need either a WiFi Internet connection or Wii Lan adapter.

Skype is definitely a revolutionary software for keeping in contact with your loved ones. It's a phone on the internet! What couldn't be good about that? If you are in Orlando, your spouse is at a conference in El Paso, your daughter’s at college in Raleigh, and your son is working in Dubai, you can keep the family in touch with Skype, a software application that lets you make free video calls over the internet.

Tired of cleaning the stove and oven every time you cook? (It always gets so messy, doesn't it?) Well, there's one solution to keep the cleanup to a minimum, albeit a little unconventional, and that is to use your dishwasher!

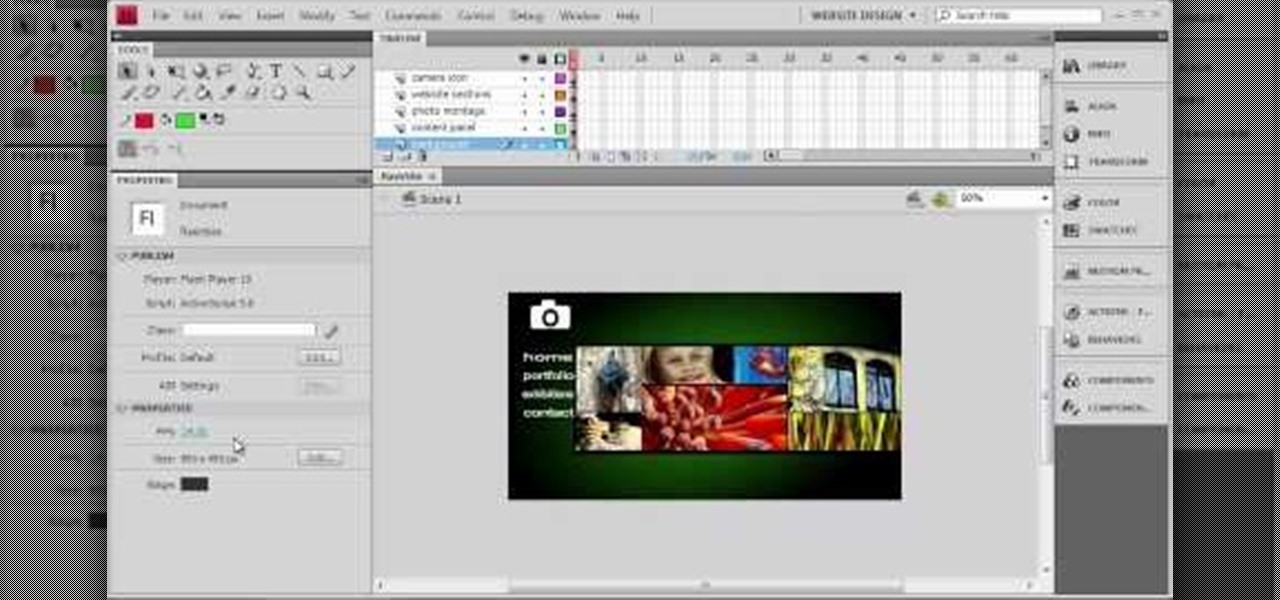
Making your own website from scratch is one of the most challenging and rewarding ways that you can take advantage of the internet. This mammoth 60-part video series walks you through the process of doing just that in Adobe Flash CS4. This is chapter 3 of that series, and covers the timeline of your website. If you haven't watched the previous chapters, do some now and come back. After you watch all of these videos, making your own site in Flash should be a cinch.

This video tutorial from iDeviceTutz shows how to change the SSH root password for iPhone or iPod.When iPhone or iPod is jailbroken it sets its password to default - alpine.Thus your device becomes vulnerable from a network attack that could steal your information or identity. So you need to change your password as soon as possible when your device is jailbroken.For this you'll need Mobile Terminal program on your device and SSH client (Cyberduck or WinSCP) on your computer.First download and...

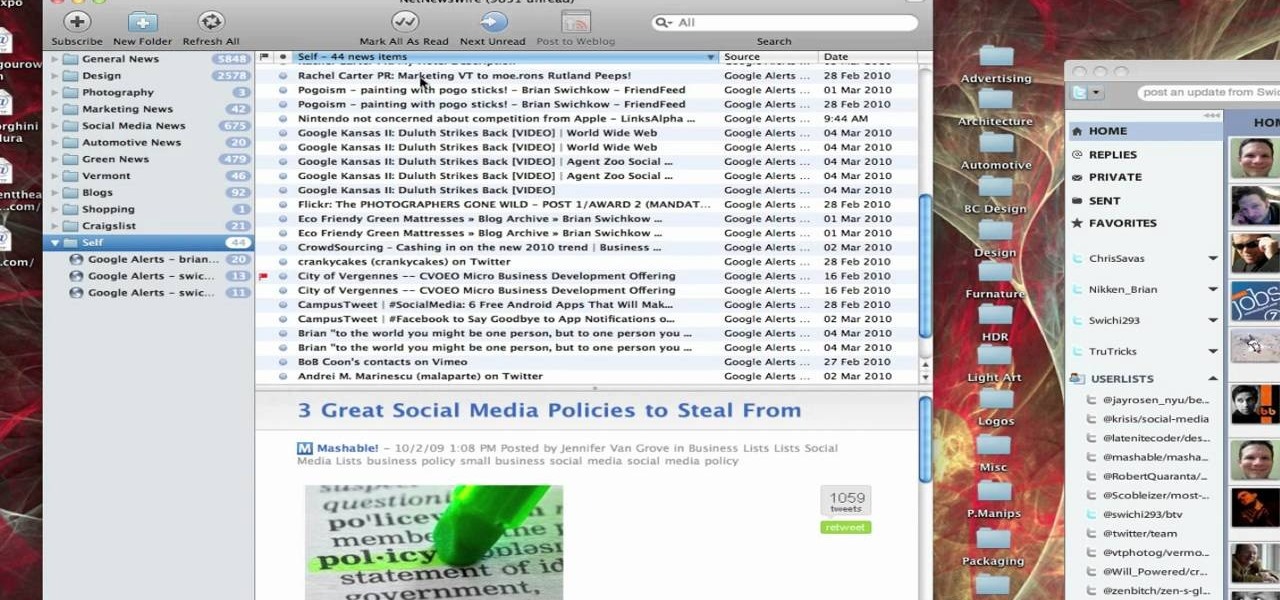
This video tutorial from TruTricks presents how to setup Google customized alerts.Open your internet browser and search for Google Alerts using Google search engine.Click first result that says Google Alerts.You will need to sign in to use this Google feature.Google or Google mail account will work. If you don't have it you should create one.After you signed in Google Alerts welcome screen will open.Here you can create new Google alerts using Create a Google Alert window.Enter Search Term you...

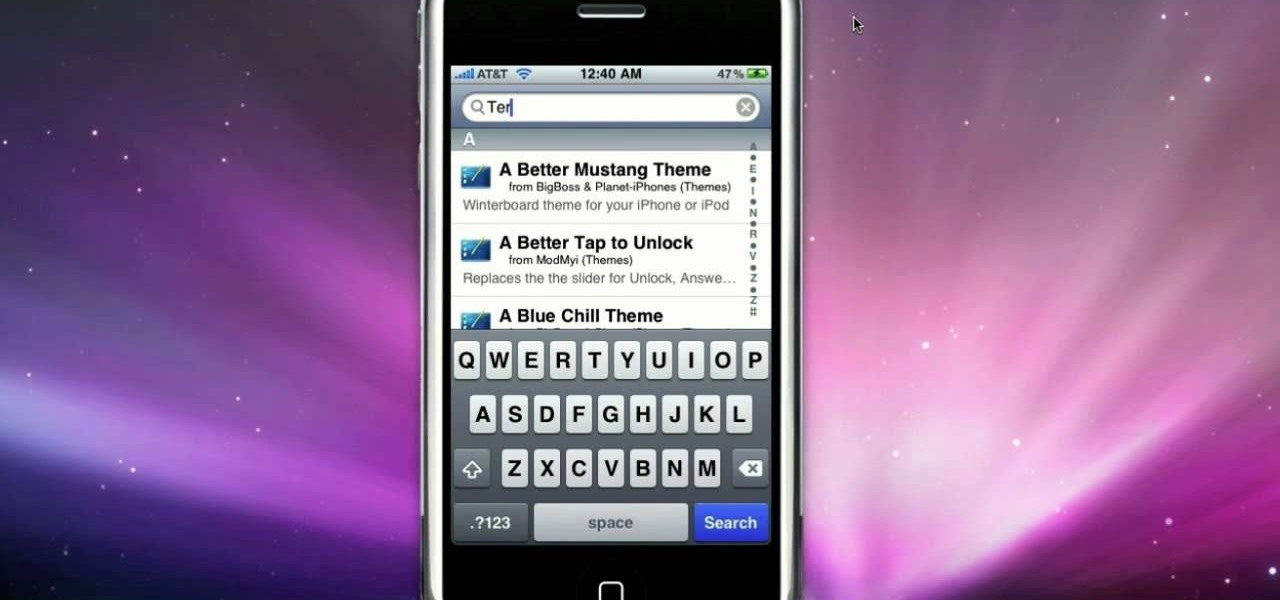
If you've been wondering how to get internet tethering working on your iphone 3G 3.0 or 3.0.1, check out this video! Jailbreaking your phone is optional for this.

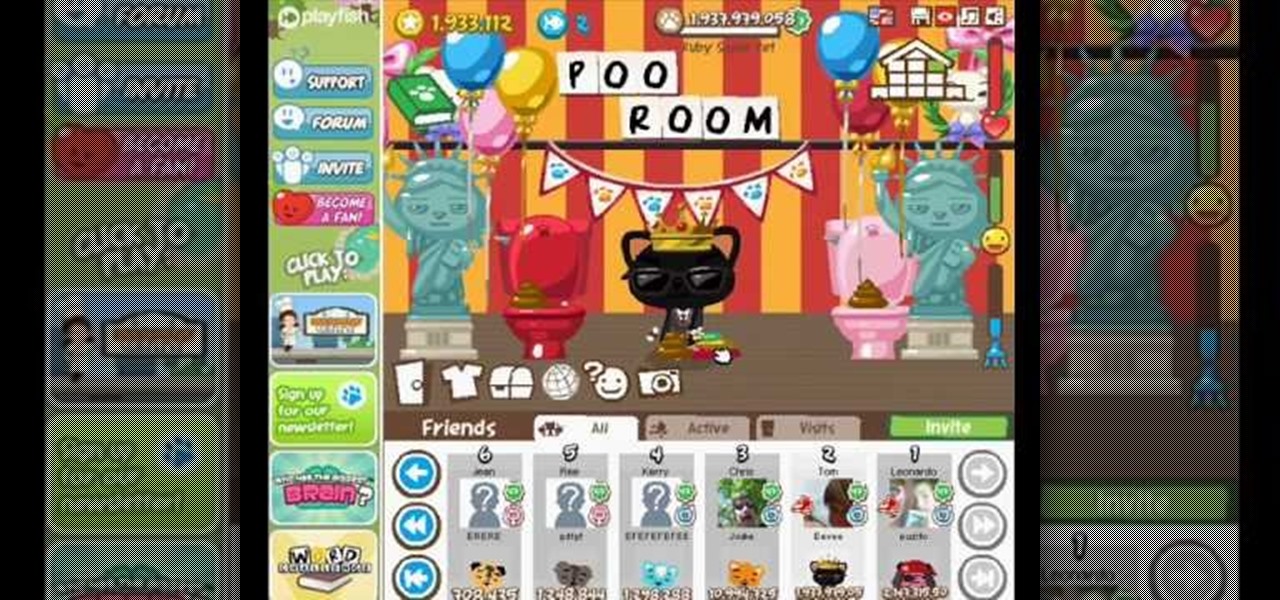
How to hack Pet Society! Pet Society cheats, tricks, hacks. Watch this video tutorial to learn how to hack poo and coins on Pet Society (09/10/09). See how to get unlimited poo: normal, gold, or rainbow! You can sell them for lots of money!

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to build a firewall from a junk PC to protect networks.

Check out this informative video tutorial from Apple on how to do more with the Sidebar in the Mac OS X Finder. Learn about the Sidebar devices, the Sidebar shared, the Sidebar places, and the Sidebar search for. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to use the basics of the Mac OS X Finder. Learn about the Finder basics, the Sidebar, view buttons, and Quick Look. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to organize your Mail in Mac OS X's Mail. See how to sort messages with rules, create smart mailboxes, and comlpletely organize your mail. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to use the basics of Mac OS X Mail. See how to set up mail with your email accounts, compose messages, add attachments, view attachments with Quick Look, and search through Mail. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to use Mac OS X Mail to its fullest. See how to filter out junk mail, use data detectors, and view RSS feeds in Mail. Mac OS X. It's what makes a Mac a Mac.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

Every state has begun reopening in some capacity. While there are important steps for everyone to get back to work and begin socializing, precautions will be in place for some time, especially with an expected second wave coming this fall. The virus is not over.

Ever since Facebook announced Spark AR at the 2017 F8 Developer's Conference, the social media giant has been looking for ways to implement its mobile augmented reality camera platform in the lives of everyday users.

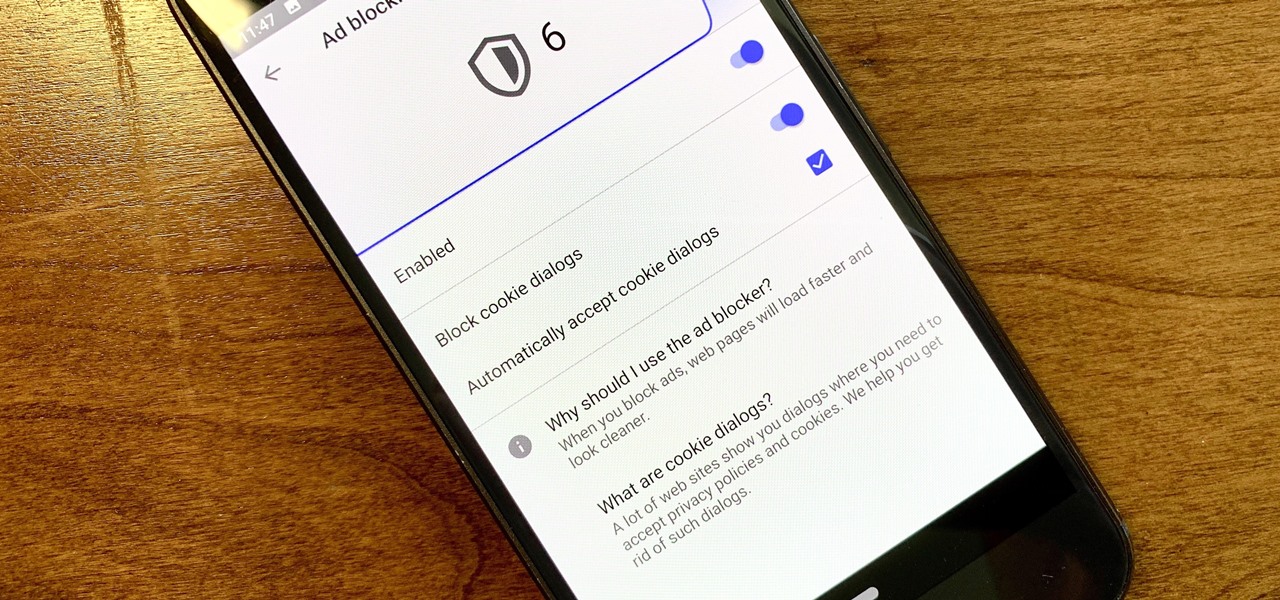
Ever since the GDPR was implemented, it seems every website on the internet needs to inform you of how its privacy policies have changed. If your web browsing experience has been marred by a constant barrage of these cookie pop-ups and privacy dialogs, you should know there's an easy way to block these web annoyances so you never have to tap another checkbox or accept button again.

Yesterday, I talked about what I think is the most immediately mainstream-friendly app on the Magic Leap One is (Screens), and now we'll touch upon the runner-up: Helio.

Less than a week after debuting its AR Cloud platform in public with a multi-user installation of more than 100 participants, Ubiquity6 announced on Tuesday that it has closed a Series B round of funding totaling $27 million.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

When you drive along the deceptively sedate streets of Silicon Valley, there are few hints that all those nondescript office parks and low-rise buildings contain the very future of the planet, but they really do. On a recent trip to tech's epicenter, I found that out firsthand when I got to visit the offices of Meta, the startup that produced the Meta 2 augmented reality headset.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Remember that scene in Tim Burton's Batman where the Joker and his goons defaced dozens of priceless works of art? A collective of digital artists have found a less criminal, more geeky way to do the same thing.

Drama seems to follow red smartphones. The internet nearly blew a gasket when Apple released a red iPhone 7 with a white front, and now OnePlus is taking some heat. The new Lava Red 5T comes with black bezels, not repeating Apple's mistake, so why are people mad at the Shenzhen-based company? Because Lava Red is only available in China.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

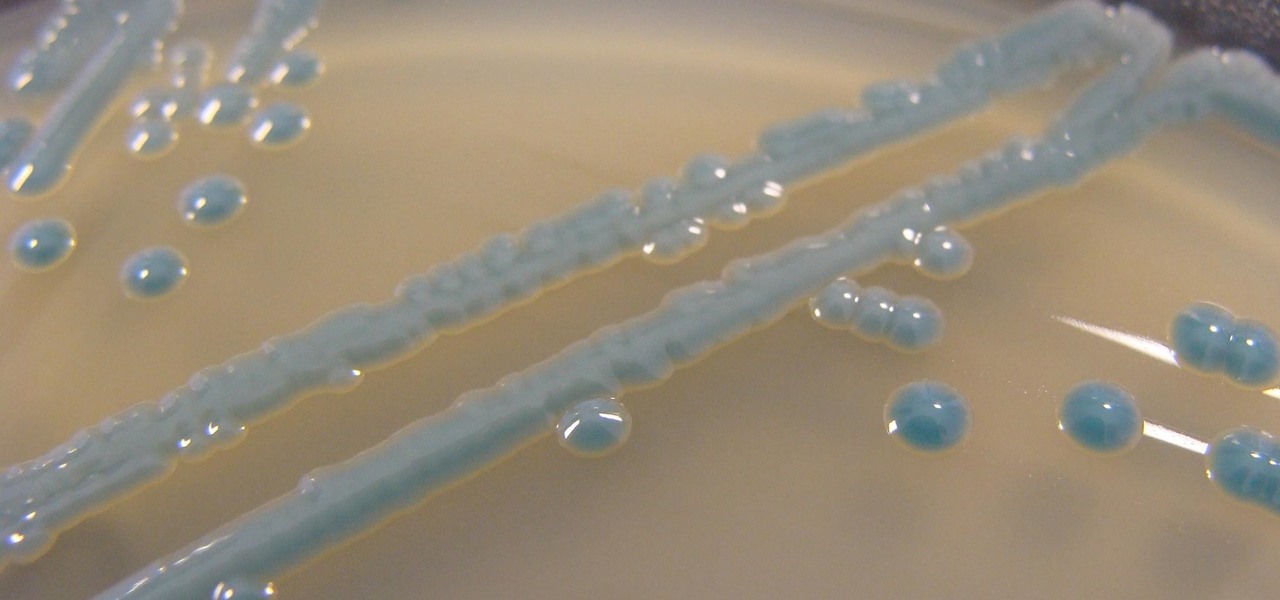
The growing list of dangerous antibiotic resistant organisms has just acquired three new members. Researchers have discovered three new species of Klebsiella bacteria, all of which can cause life-threatening infections and have genes that make them resistant to commonly used antibiotics.

After years of telling patients to finish any prescribed course of antibiotics completely, a group of researchers in the UK say it is no longer necessary, and could even be harmful if we want to preserve the antibiotics we can still use.

Sex makes the world go 'round, and when it does, so does gonorrhea. Finally some good news on the growing menace of drug-resistant gonorrhea — a large, long-term study shows a vaccine may work in reducing the incidence of an increasingly dangerous infection.

Cycling accidents are more common than you think. In the past month, two men have been hit and killed while cycling in New York City. I even saw a cycling accident occur yesterday morning here in NYC. It's dangerous enough to be cycling in populated areas, it's made worse by people wanting to text while riding.

It's not always easy to get to the root of an infection outbreak. Epidemiologists study infected people, contacts, and carefully examine where the infections happened and when. In the case of a 2012 outbreak of pertussis — whooping cough — in Oregon, scientists just published an analysis of how vaccination status affected when a child became infected during the outbreak.

Alzheimer's disease — an irreversible, progressive brain disorder — is the sixth leading cause of death in the US and more than afflicts 5 million Americans. As if those numbers aren't scary enough, the Centers for Disease Control and Prevention expect that number to nearly triple by 2050.

Fighting fire with fire, scientists are harnessing the adaptability of helpful microbes to challenge the adaptability of deadly microbes. What are we talking about? Hunting with phages — viruses that attack and kill bacteria.