How To: Hack MyBrute for more experience and stats (08/01/09)
Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to hack MyBrute for more experience and stats (08/01/09).


Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to hack MyBrute for more experience and stats (08/01/09).

Watch this video tutorial to learn how to play the Google language computer prank on a coworker. Change your colleague's Google settings with this easy prank, and watch their head spin!

Your friends want you to marry them! Before you can officiate their big day, you'll need to jump through some legal hoops. Learn how to officiate at a wedding.

Learn how to write a grant proposal. If your organization has come up with a great idea that needs money to get off the ground, you'll need a great proposal. Here's how to write one.

Go thrifty! Go vintage! Go second hand. With the right approach and an open mind, a trip to your local thrift store can yield some fashionable bargains. Buying used is a smart solution to this economy, and gives you a smart sense of fashion.
Look good for your internet friends. Edit photos on social networking sites such as Facebook and Picasa as well as blogs without having to download them to your computer.

Learn how to use Gmail to its maximum potential; get internet tools and computer networking tips from expert Drew Noah in these free instructional videos.

Reverbnation.com is a revolutionary new website that has been taking the internet promotion idea to the next level with free emailing, widgets and stats. Learn tips on how to use this great site in this free video clip series.

Want to control a friend's cell phone remotely and make "free" calls from it? In this hack how-to video, you'll learn how to hack Bluetooth-enabled cell phones with your Sony Ericsson or Nokia phone and the Super Bluetooth Hack—or "BT Info"—, a free program easily found through Google. Once installed, Super Bluetooth Hack will enable you to control your friends' cell phones remotely.
Check out this eight-part VB.Net video tutorial to see how to create a program from the ground up using VB.Net in Microsoft Visual Basic 2008 Express Edition. You'll need Internet access for this task, like most other tasks. Start a new program and get watching. If you're new to VB.Net program development, than this is just the spot.

In this video tutorial, viewers learn how to clear their cache in Internet Explorer. Begin by opening the web browser. Then click on Tools from the top menu and select Internet Options. In the General tab under Browsing History, click on Delete. When the Delete Browsing History window opens, click on Delete Cookies and click OK. To automatically clear cookies, click on Settings under Browsing History and check Every time I visit the web page. Then finish by clicking OK. This video will benefi...

Learn a little bit about technology with help from EMBARQ. Watch this how-to video tutorial on installing your EMBARQ 660 Modem. This will cover exactly how to install your EMBARQ Modem for EMBARQ High Speed Internet service. This is the complete process step-by-step from box to connected online.

Have you always wanted to make a prank call but never had the guts to do it? Well, now you can because there's the Internet. In order to make a cool prank call without getting caught, first you have to choose a voice. The best one to choose is Arnold Schwarzenegger. To get his voice, go to Google and search for Arnold soundboard.

Get basketball tips and tricks from a high school basketball coach. In this sports how-to video, Farmington HS boys basketball coach Shane Wyandt and team demonstrate the shell one defense drill. The shell one defense drill has been an effective method of defense training. Follow along with this instructional video to learn the shell one drill.

In this sports how-to video, Farmington HS boys basketball coach Shane Wyandt and team demonstrate the shell 5 defense drill. The five man shell drill is an effective way to train defensively for basketball. Follow along with this video demonstration and learn the shell five drill.

Need to know how to hold your pool stick? Well, learn these effective finger positions to elevate your game to a new level. Open bridges are for limited use only! Have you ever seen a professional pool player with an open bridge only?

Dr. Christopher Lepisto on a study that proves Kolorex (Horopito) is as effective as the leading pharmaceutical drug to killing fungus, without the side effects.

This video teaches you how to use NLP to anchor others to you. Create the impression that you are sexy, motivated, confident, etc. with this simple, yet highly effective, NLP (Neuro Linguistic Programming) technique taught by Steve G. Jones, Clinical Hypnotherapist and expert in hypnosis.

A Look into Internet Marketing including common pitfalls to avoid and how to build a userbase. Part 1 of 2 - How to Get into Internet Marketing.

Did you know that you can improve the Wi-Fi in your home without the stress of changing providers or using a costly professional? The answer lies in a simple app you can use yourself at home, and right now, the NetSpot Home Wi-Fi Analyzer With Lifetime Upgrades is on sale for just $39.99. That's 41% off the regular price of $68.

Almost 20% of the US population (about 60 million Americans) live in rural areas where mobile reception is weak or nonexistent. In times of crisis, these Americans can't rely on the internet to communicate with loved ones or receive new information. This is why being able to interact offline is so important.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

Data is king. Nearly every carrier and MVNO offers unlimited talk and text with their cellular plans. Where they differ is the amount of data available, so that's the part that can save or cost you the most money.
So far, iOS 13.4 hasn't been a disappointment. From new Memoji stickers, a refreshed Mail toolbar, and even the beginnings of controlling your car with your iPhone, Apple's latest iOS update is looking like a good one. That's why we're excited that Apple just released the third 13.4 developer beta today, one week after the release of the second one.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

Windows 10 passwords stored as NTLM hashes can be dumped and exfiltrated to an attacker's system in seconds. The hashes can be very easily brute-forced and cracked to reveal the passwords in plaintext using a combination of tools, including Mimikatz, ProcDump, John the Ripper, and Hashcat.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

If you use the internet regularly, it's nearly impossible to avoid memes. They are the epitome of internet culture, demonstrating how jokes can spread and change like wildfire. While there are many different types, the most common ones you'll come across are images and GIFs with humorous text accompanying them, and we've found the best iOS apps to help you create your own.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.
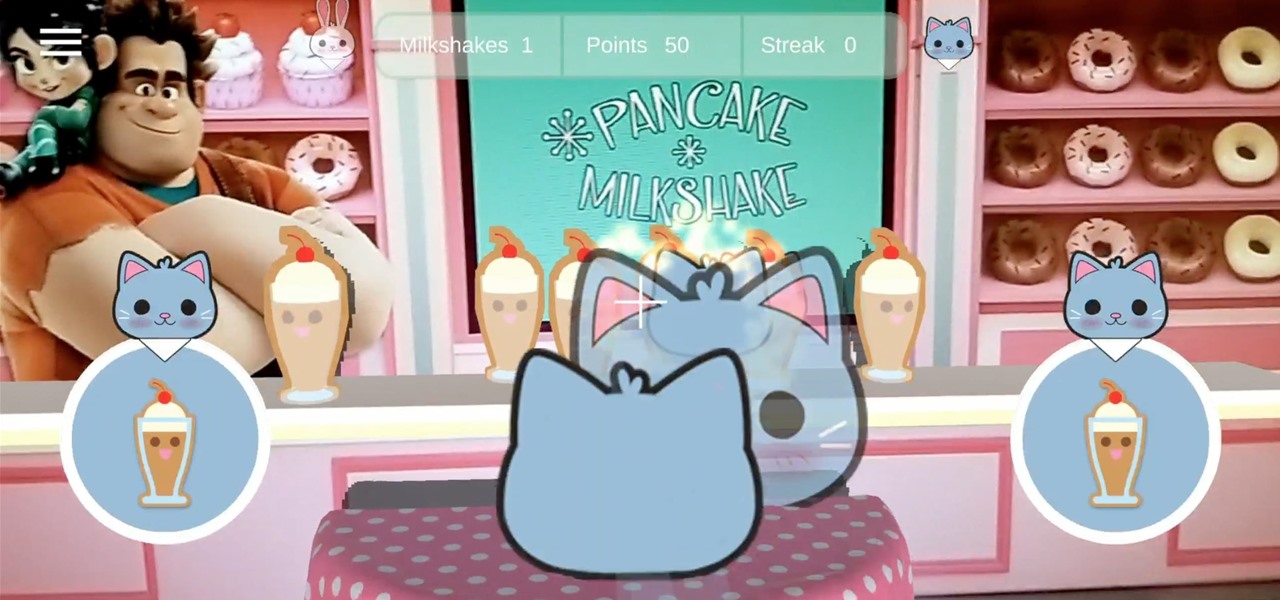
One of the funniest scenes from the teaser trailer for the Wreck-It Ralph sequel is the basis for the new pre-show augmented reality experience via the Noovie ARCade app.

Most of us have never put much thought into this, but the question needs to be asked — what exactly happens to all of our online accounts when we die? No, the internet won't just know and delete accounts for you, so you need to plan for life's one guarantee. Because without a plan, things become a lot harder to sort out.

While there aren't as many ways to customize your iPhone like there is on Android, there are still a lot of apps out there that can help streamline and enhance your experience beyond Apple's own default options — and we've hand-picked over 100 essentials.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

The primary method of activating Siri is done by pressing and holding either the Home or Side button, depending on the iPhone model, but there's a much better way to ask a question to Siri or command it to do something — and you don't need to touch your iPhone at all to do it.

To celebrate its tenth anniversary, PornHub has just exposed all of our porn habits. All. Of. Them. Before you panic, no individual information has been released. Instead, PornHub has exposed the adult video trends and preferences of a variety of demographics.
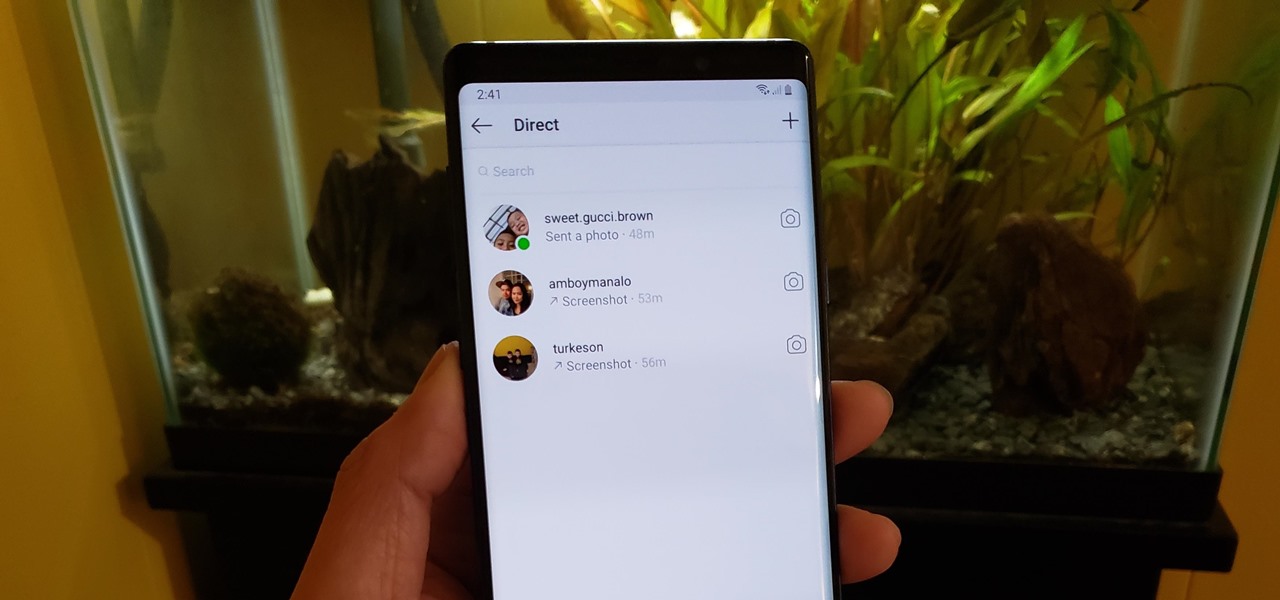
If imitation truly is the sincerest form of flattery, then Snapchat must be blushing profusely as Instagram continues to shamelessly copy its features and dig into its wallet. Instagram has also managed to copy some of the security aspects — or lack thereof — of one of Snapchat's hottest characteristics.

A VPN service is almost an essential these days. Good ones can block ads, prevent tracking cookies, encrypt your internet traffic for better security, and even spoof your device's location to bypass geo-restrictions — all things you should be concerned about in the age of NSA snooping and Facebook data mining.