Learn how to save money n clothes with these fantastic tips! 1. Before you go shopping, you must get to know your body shape, colors that suit you, and be aware of your style of life. 2. To determine your body shape, and which things actually suit you and make you look good, try on as many clothes from your friends or in the shops as you can, and be critical of your look. 3. To determine which colors suit you, find a book on the internet or in the library. (shades should complement your skin ...
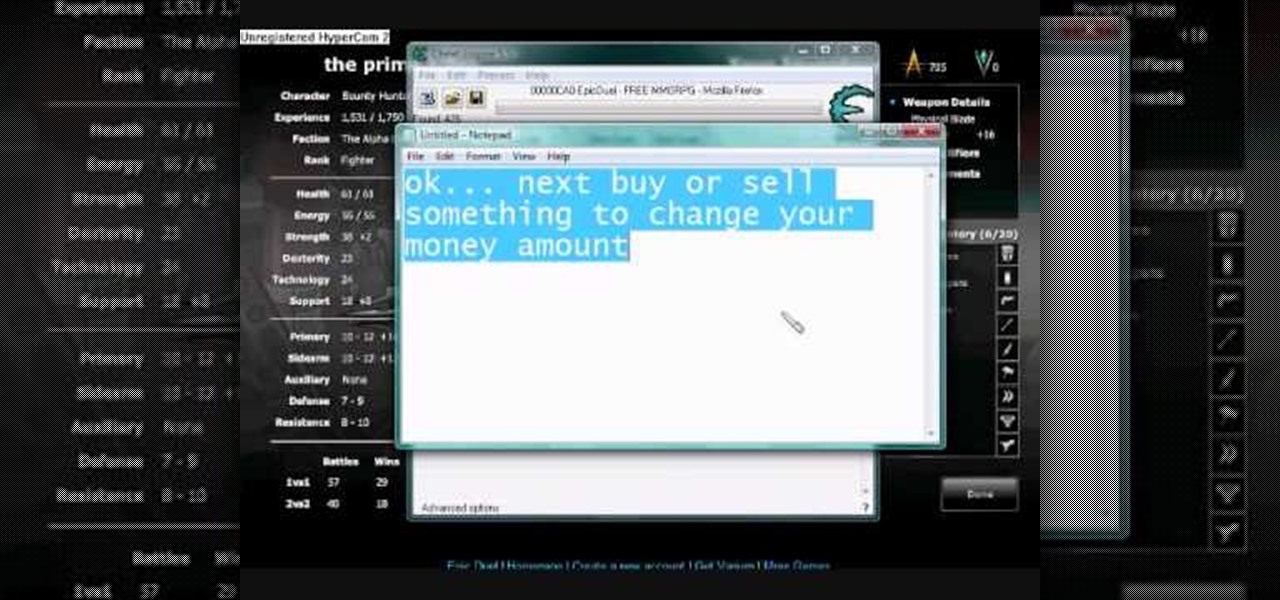
There's a great new web game called Epic Duel out on the internet, and everybody's playing it, but not everybody's hacking it, except you! Outshine them all with this EpicDuel cheat with Cheat Engine 5.5.

Researching genealogy takes a little enterprise and the skills of a master sleuth.. Watch this video to learn how to research your genealogy and family tree.

Learn how to fold simple origami Kusudama with instruction by Ancella Simoes. Be sure to click on all 3 chapters for full instructions.

Identifying snakes is difficult to do accurately. Identify snakes using field guides and the Internet with tips from a certified animal control officer in this free reptile pets video.

There is an easier way to get in shape—and you can do it from the comfort and privacy of your own home if you so prefer. There are a few low impact pieces of exercise equipment that you can use to tone and shape your body; and often these simple tools can produce dramatic results. In these exercise videos, learn how to workout with a resistance band and a fitness ball. Through the power of the internet, our expert can be your personal trainer and lead you through several exercises to tone you...

With so many competing outlets to reach people, accessing inboxes remains one of the most effective forms of communication. Yet newsletter creators run into a constant problem: bounced emails.

Before the internet, acquiring enough data to analyze was challenging. Now we have the opposite problem: a deluge of data makes trying to sort through it nearly impossible. That's where data science comes in.

The overarching and expanding field of data science and analysis has become virtually inseparable from areas such as programming and development.

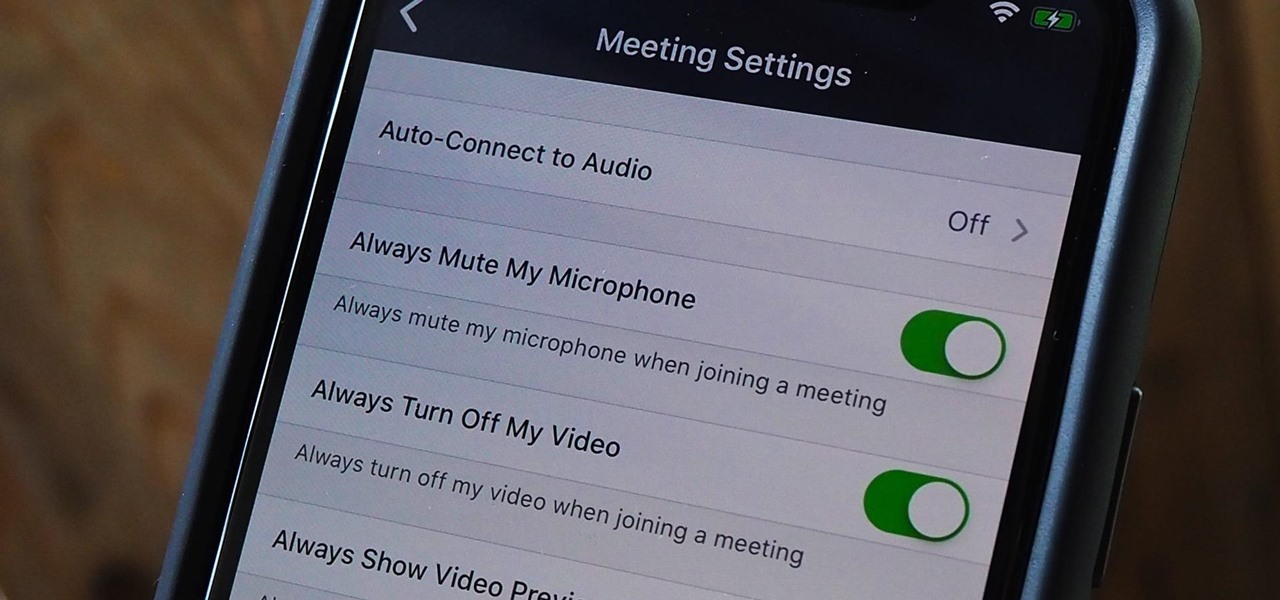
By default, as soon as you join a meeting on Zoom, both your microphone and camera turn on, sharing your audio and video to the other chat participants. While that isn't usually a problem, it can be an issue if the meeting hasn't started or you're entering in the middle of a class, and you don't want to disturb the video conference.

When Samsung announced its new Super Fast Charging 2.0 system was based on USB PD, the industry rejoiced. By using an open standard, Galaxy users could pick from hundreds of third-party chargers in addition to first-party options from Samsung. Trouble is, this never came to fruition.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

While Snapchat augmented reality often embraces pop stars like Drake and Ariana Grande, a couple of bands from the louder side of the music industry have found a home with Facebook.

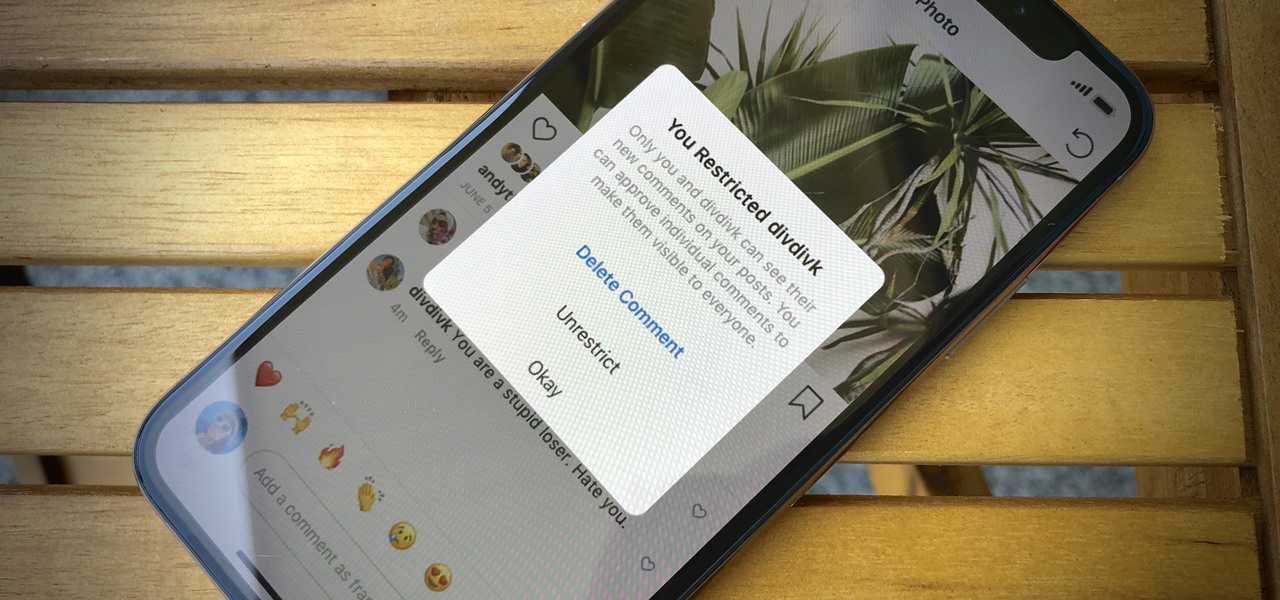
In general, the internet can be a cruel place, and Instagram is no exception. Most of the time, the platform is a fantastic way to share and view unique and creative content, to reach an audience of both fans and friends. People can step out of line and harass or bully others on posts to the detriment of the entire community. However, this type of commenting won't be sustainable for much longer.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

Nowadays, our phones are capable of just more than 30 fps video. Phones like the Galaxy S10 can shoot 4K at 60 fps, even on the front camera. Slow motion functionality has recently started to appear on more and more devices — but as you may have noticed, the quality of the feature differs from phone to phone.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users.

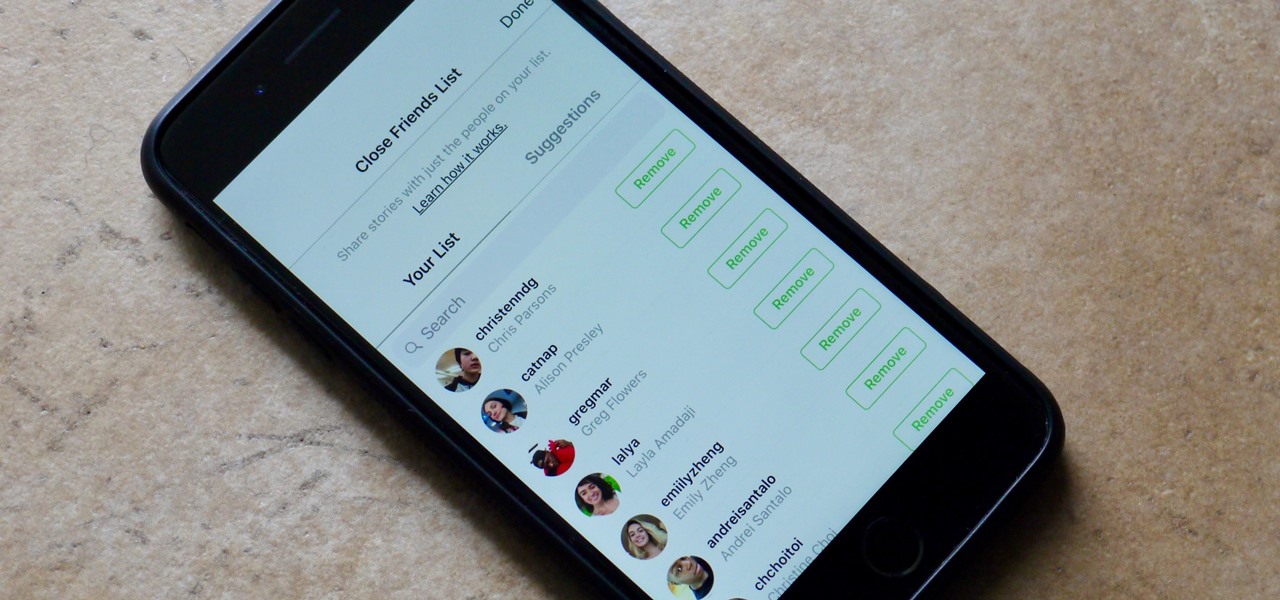
Stories make sharing your day-to-day highlights fun on Instagram. However, other than choosing who to hide stories from, by default, stories don't have much privacy control, especially if your Instagram account happens to be public. Instagram recognizes this flaw, which is what its "Close Friends List" is all about.

Applicants looking to attend Magic Leap's first annual L.E.A.P. conference next month in Los Angeles have begun receiving their confirmation invitations, and now we have more detail about some of what will happen at the event.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

Before Google Chrome entered the scene and subsequently dominated the market, Firefox trailed only Internet Explorer as the most popular web browser. Now, Mozilla has its sights set on a new opportunity to revive its browser for immersive experiences.

Why would Magic Leap, a company preparing to launch its first augmented reality headset this year, need a developer for iPhone and iPad apps? It's not as crazy as it sounds.

One of Android 8.0's best features is also one of its most subtle — customizable lock screen shortcuts give you more control over the two functions you care about most. Your Galaxy S9 has the Phone and Camera apps in those spots by default, but you can quickly and easily change them if you have other ideas in mind.

On Sunday, the annual Grammy Awards delivered its usual mix of fashion, live performances, and music industry magic, but this time with one important difference: Animojis.

Using the CES tech conference in Las Vegas as the launch pad, Dell has announced that it's partnering with Meta Company to offer its augmented reality headsets to business customers.

If you know your internet history, then you fondly remember the Star Wars Kid and his epic lightsaber display on YouTube. Now, many years later, everyone is following in the footsteps of the Star Wars Kid thanks to the Lenovo Mirage and the new Star Wars: Jedi Challenges app.

There may be many third-party file managers for Android to choose from, but until now, Google offered no proprietary option. Enter 'Files Go,' which, while initially anticipated for December, is now available for you to try.

Tech companies are embroiled in controversy this week. No, not the hearings on Russian interference in last year's election; in this case, it's all about the burger emoji.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

Young girls, especially those who live in areas where HIV is epidemic, like sub-Saharan Africa, are particularly vulnerable to becoming infected with HIV. A vaginal ring containing the antiviral agent dapivirine has been shown to decrease the chance of developing HIV-1 in adult women over 21 and now in the first step for use in adolescents, the ring has been shown to be safe and well-tolerated in that younger age group.

Killing more than 29,000 people each year, infection with Clostridium difficile (C. diff or CDI) is the most common healthcare-associated infection in the US. In a disturbing development, new research reveals recurring cases of the infection are soaring.

Bed bugs are parasites not yet known to spread disease — but they cause plenty of irritation. As scientists and landlords search for new ways to deal with the pests, a new study examines how we can deter bed bugs without so many chemicals.

Are you looking for a get-rich-quick scheme? Need a way to buy that Tesla you lied about having? Well, I don't know how to get you that. But what I can tell you is there is an emerging market that pays pretty darn well, for work that's more than interesting. I'm talking, of course, about iPhone repairs.

Apple announced upcoming changes today to prevent third-party tracking of users and prevent autoplay, on Safari. Safari will prevent the recording (by anyone other than Apple) of users' browsing behavior, and by doing so prevent advertisers from targeting ads based on individuals' history.

For companies wary of the temperature, PTC just made it easier for them to dip their toes in the waters of augmented reality.

Last month, Google introduced the Family Link app. This app, much needed in a world where the average age of kids first getting a smartphone is just over 10 years old, allows parents to set some limits on their children's phone usage. However, the app premiered with one caveat: Both the parent and the child had to have an Android phone. Now, Google has updated the app so it works on iOS devices.

Google released its "Android Security: 2016 Year in Review" report last month, and to no one's surprise, included its own flagship phones. However, one surprise on the list was the BlackBerry PRIV, which Google named one of the best Android devices for privacy.

Nineteen days ago, several hundred people could have been exposed by a traveler with measles in Nova Scotia, Canada. The next day, someone flying from Minnesota to Nebraska may have spread the measles to other passengers. A couple weeks ago, it's possible that a man and his six-month old child spread the measles in several Seattle-based locations. Authorities are trying to locate persons who may have been in contact with these people. None of the persons with measles were vaccinated. Why?