If you use apps on your smartphone, chances are you have no idea what those apps are doing with your information. Just this year, there have been several scandals involving apps transmitting user data, like Path uploading users' entire address books onto its servers, HTC's Security Flaw, and Brewster exposing users' personal information (even Ashton Kutcher's). A new service called Mobilescope wants to make sure you always know where—and to whom—your data is going. Lots of apps copy your cont...

Everything is documented these days, thanks to the Internet and mobile devices. Most people who own a smartphone use it to take lots of pictures. If you're one of those people, an app called Scoopshot can help you turn some of those photos into extra cash. Scoopshots lets you post your pics so that news organizations can pay you to use them. Companies can also post tasks, so if someone is looking for a particular photo in your area, you can accept the task, go take the photo, and earn money f...

Drinking games just got a little more sophisticated (kind of). Startup SmartThings built this awesome Arduino-based machine that automatically pours a shot whenever the US wins a medal in the 2012 Summer Olympics. Goldschläger for gold, Cuervo for silver, and Jack Daniels for bronze.

Cashcroppimp teaches you how to open your XBox 360's NAT with Verizon Fios. You first have to find your IP address. For this, you simply point your internet browser to http://findmyip.com to find IP. This is also calling the default gateway. Make sure to write this down somewhere. Now you need to input this number in your internet browser. Enter your username and password and proceed to the next step. Now go to Firewall settings-DMZ Host. Here you will need the IP address from the XBox 360, w...

Learn a little bit about technology with help from EMBARQ. Watch this how-to video tutorial on testing your phone line (NID) if you have no dial tone. If there is no dial tone on your home lines, just test your NID (Network Interface Device) on your house to see what's going on. This is an important step to getting your High-Speed Internet up and running.

Home cooks know firsthand what it takes to make delicious and amazing food for friends and family. One of the most effective ingredients to making foods as delicious as possible is herbs.

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

Connecting your Nokia N900 smartphone to a wireless hotspot or your home wifi network is just a few quick taps away! Take a look at this tech support video from Nokia that will tell you exactly where to find the available internet connections on the phone and select the one you wish to connect to.

Want to give yourself extra points or resources in the online game Wild Ones? All your friends will be asking you how you passed them up so quickly! Make sure you have the most recent version of Cheat Engine downloaded, first!

If you're trying to use Cheat Engine to cheat for more money on Ninja Saga and keep getting an error message, this tutorial shows you a remedy. Make sure that you're playing Ninja Saga in either Firefox or Internet Explorer.

After playing Minecraft for a while, the old skins and textures can start to get old. But thanks to the internet, there's a LARGE community creating skins and textures that you can put right into the game! If you're wondering how to do this, this video will get you quick tutorial on how to quickly copy and paste your textures and skins right into the right folder and use them right away!

Making anonymous prank calls got a little difficult for a while there in the early 2000's. Not anymore though! Between Skype and PrankDialer there are very few people that you can't prank call anymore without having to worry about them finding you. This video will show you how to use Prank Dialer to make prerecorded prank calls to whomever you want for free. Good times.

The cost of scrapbooking can really add up. You can still create wonderful scrapbooks to artistically document your memories by shopping smart and cutting costs by being resourceful. You can use things you already have around the house.

Assuming you have already downloaded your desired theme off of the internet, this video will show you how to load it onto your PSP. Having custom themes on your PSP makes for a more spiffy design. It allows you to break free from the default ones loaded by Microsoft. Theming your Playstation Portable is fast, easy, and requires access to a computer.

This one's for all you cheaters! Those who enjoy getting free money in flash games will certainly enjoy this video.

This is a video guide to wireless broadband from Top10.co.uk. Learn about wireless broadband in this interesting video. This "how-to" guide for wireless broadband explains the basics of what wireless broadband is, how and where it works and who offers it, not to mention how to set up a home Wi-Fi connection in minutes using a wireless router. Follow the steps in this guide and go wireless today.

This video explains how to speed up Opera to browse the Internet at fast speeds.

A quick guide on using the wonderful internet tool StumbleUpon - a great way to find new and interesting websites.

We all know that using a VPN not only has a ton of benefits but is essential in our digital age. But did you know that you can get access to your own industry-leading VPN for life with one one-time payment? Even better, we've found an amazing deal on one right now: for a limited time, a YoData VPN: Lifetime Subscription is on sale for just $17.99. That's 69% off the regular price of $59.

If you're living or staying out in the middle of nowhere or a rural area outside of a big city or town — where there are no reliable cable, fiber, or wireless networks available — how can you get an internet connection? There are several possibilities, but they all come with tradeoffs, which we'll go over in detail.

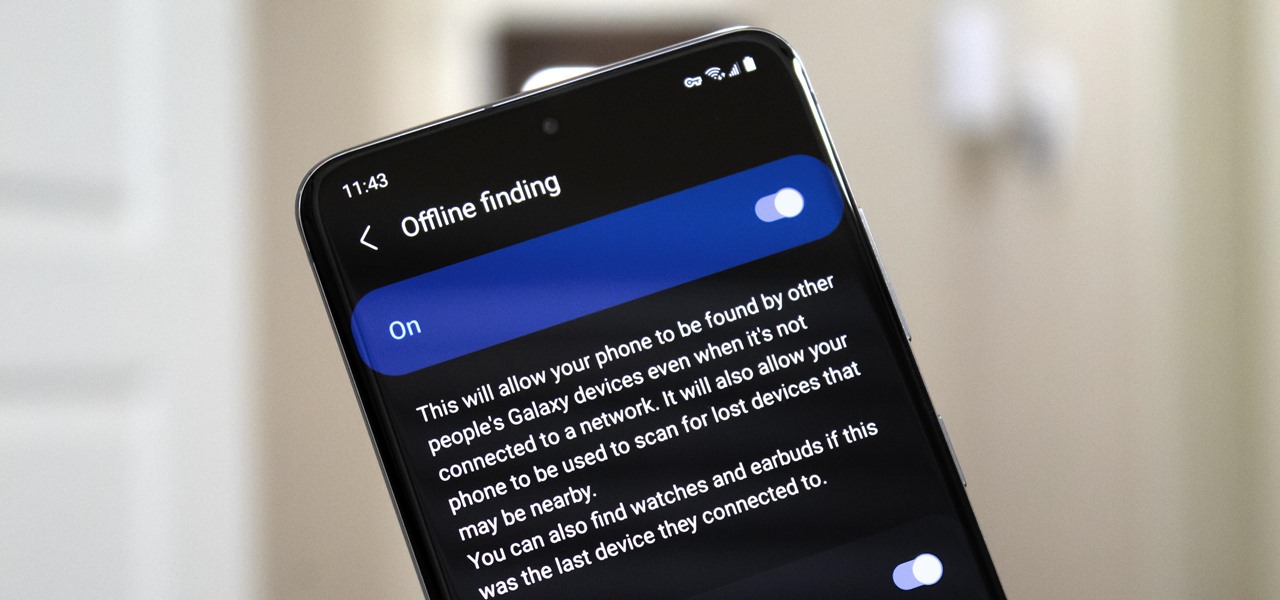
Nowadays, even the dumbest thieves know that the first thing you should do after you steal a phone is turn on airplane mode. Not only does this make it harder for police to track the phone through cell tower triangulation, but it also disables security features the person you stole it from may have implemented — for instance, Samsung's Find My Mobile service.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

The worldwide health crisis around the coronavirus has gripped the live events industry, particularly in the tech sector, with the cancellations of Mobile World Congress, the Game Developers Conference, Facebook's F8, Google I/O and now South by Southwest.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

The next phase of the holographic display is upon us, and Looking Glass is aggressively making sure that it's at the tip of the spear when it comes to leading that charge.

Halloween may be finished, but the augmented reality chills are not over yet for some people. Arachnophobes are bravely facing their fears by cozying up to augmented reality spiders for a university study.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

In the last few years, the HoloLens has become a popular tool for use in medical procedures and training. But recently, the Magic Leap One has gained momentum in the space as well when it comes to medical use cases.

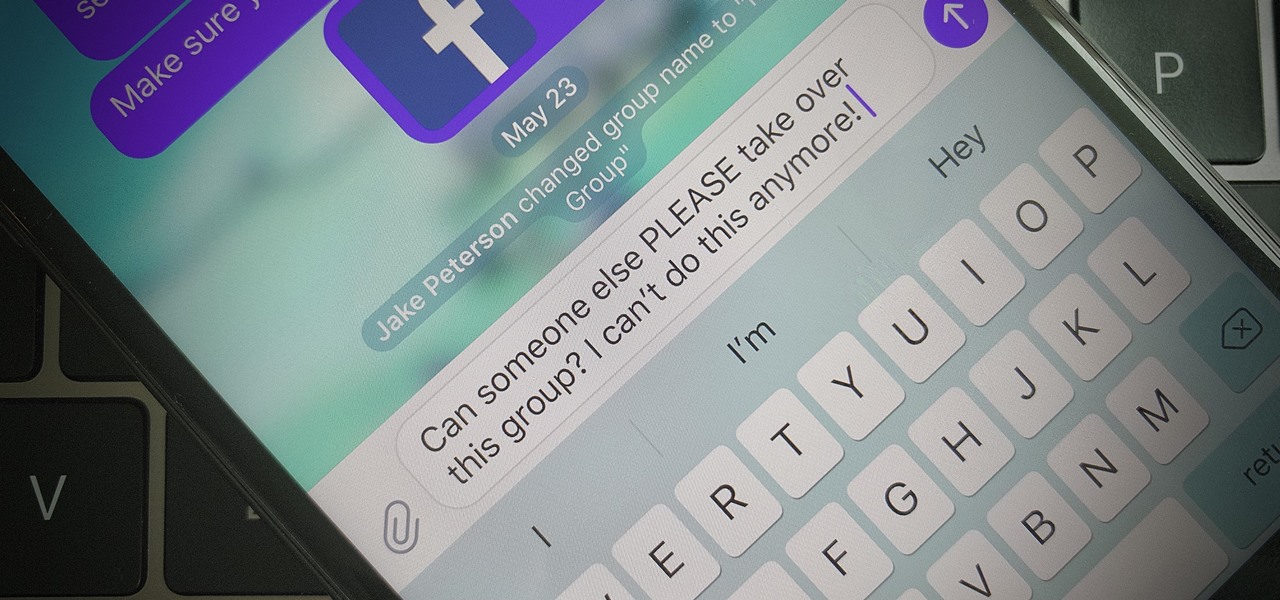
Group chats are fun, effective ways of staying in touch with the many people in our lives. Whether it's the local friend chat or the group from work, we rely on these groups to keep connected. Running one of these group chats, however, can be a monster task. If you're feeling overwhelmed with administrative responsibilities, why not pass on that burden to another member of the Telegram group?

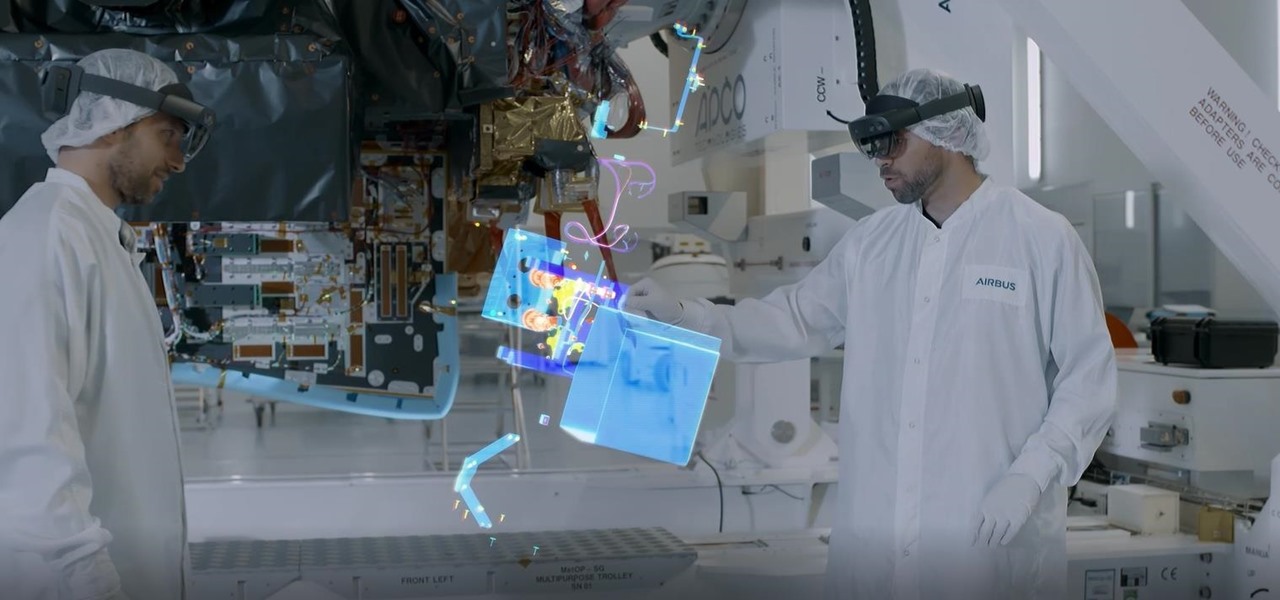
Aircraft manufacturer Airbus is so impressed with the boost in productivity it has gained from Microsoft's HoloLens, the company will begin offering augmented reality software to its customers.

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

A relay is an electrical component that works like a light switch, where it's turned on or off with an electrical signal. By connecting a relay to a Wi-Fi connected microcontroller like an ESP8266, you can build a connected switch that can be controlled from the web browser of any device connected to the same Wi-Fi network — all for just a couple of dollars.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

In Guardians of the Galaxy Vol. 2, Mantis resides in the shadow of an Ego who considers himself the actual heart of the universe. But when it comes Halloween costumes? Mantis will be the center of attention every time. The internet sure has noticed Mantis, and it's abuzz with debate over who she is. Is she just another iteration of the submissive Asian woman stereotype? Or is her character an empowering representation of empathy and the autism spectrum?

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

Apple introduced Portrait Mode with the iPhone 7 Plus, a feature which utilized the iPhone's dual cameras to create a shallow depth of field around a subject. This effect replicates the look of DSLR cameras, making your photos look more professional. Apple, of course, carries Portrait Mode to the iPhone X and iPhone 8 Plus in iOS 11, however, with it comes a twist — Portrait Lighting.