Google's Allo is still a work in progress, but the innovations to the chat and messaging app just keep on coming. The latest update rolling out now includes chat backups and a group incognito feature that we're very excited about.

The first augmented reality hardware and software functional requirements guidelines have been released today by UI LABS and the Augmented Reality for Enterprise Alliance (AREA).

Google, the company that rules the internet, is now testing a method to leverage its machine learning with its ubiquitous presence on mobile devices. The new model they're employing is called Federated Learning, and it hopes to apply artificial intelligence to Google's services on Android without compromising user privacy.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

People have been transforming mud into art, aka pottery, for thousands of years. This is not a new phenomenon, but often the finished product has a certain utilitarian aesthetic, such as a bowl or vase.

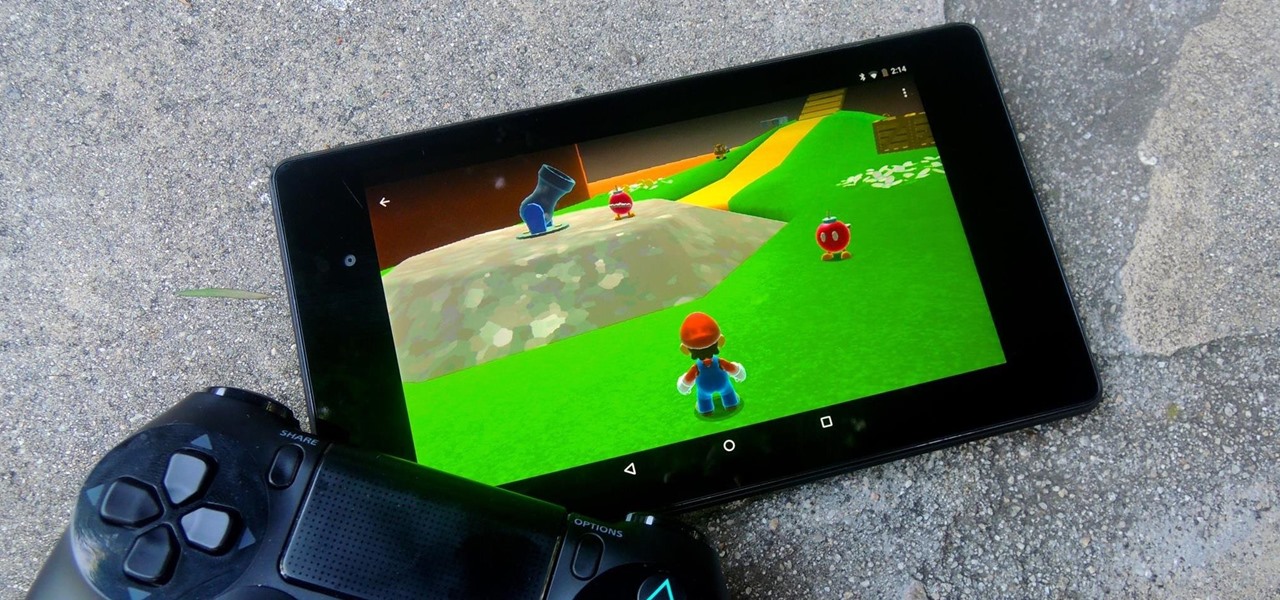
Super Mario Bros. is one of the most renowned games in history. It helped resurrect a dying video game industry in the mid-'80s and still remains one of the best-selling video games of all time—one reason why the new NES Classic Edition is so popular and impossible to get these days. Its simple story of a plumber trying to rescue a princess resulted in a video game empire for Nintendo.

Security journalist Brian Krebs recently suffered a record-breaking DDoS attack to his his website, clocking in at or near a whopping 620 Gbps of traffic. Krebs' site was down for over 24 hours, and it resulted in him having to leave his CDN behind.

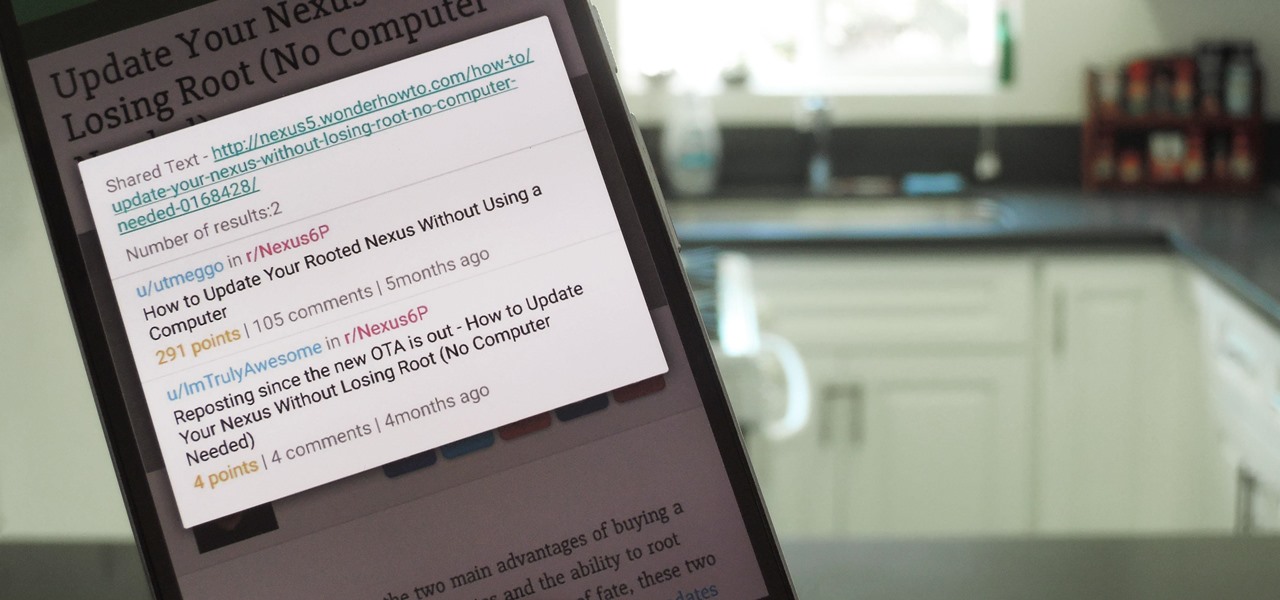
When you want to read product reviews, you go to Amazon—regardless of whether or not you intend on buying the product from their website. By the same sense, when you want to read discussions about certain topics you come across on the internet, there's no better place than Reddit.

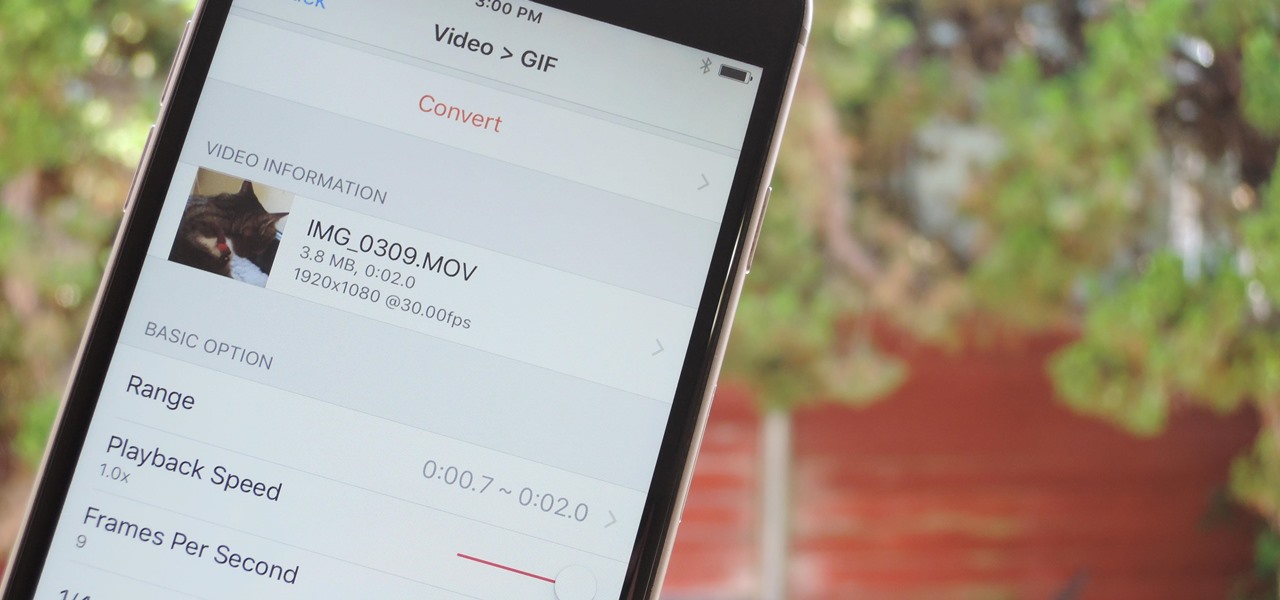
The internet has officially been taken over by GIFs—they're everybody's favorite method of communication these days, and nary a meme would exist without them. But even with the abundance of GIF-sharing websites, and even GIF keyboards, we're still a bit lacking in regard to creating GIFs on a mobile device.

Graeme Devine, Chief Creative Officer at Magic Leap, spoke at the Games for Change festival about how mixed reality will change the world for the better. While we might need to take our own magic leap to believe in his utopian future, he hinted at a solution to the impending problem most of us fear: a cluttered, endless nightmare of ads.

We don't know exactly what form 5G cellular technology will take, but it intends to bring faster Wi-Fi-like performance to mobile devices. While that'll provide major advantages to lots of connected technology, PC Magazine notes that it could be what augmented and mixed reality needs to become widely adopted.

Logan's Run is one of my favorite movies of all time. The dialog is cheesy, the set design and special effects are wonky, and the main villain looks like he was conceived and built by an eighth grader in shop class—oh, and his name is Box.

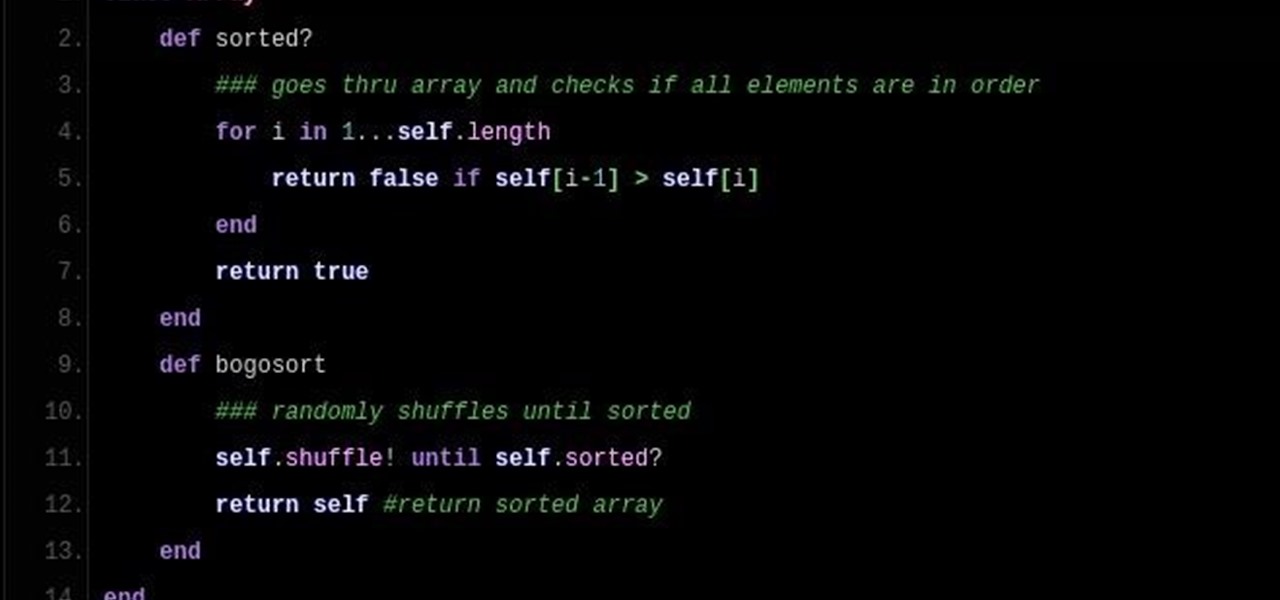
So DTM insisted I write up a little article on Bogo Sort. What Is Bogo Sort?

When a headache strikes, I reach for the nearest painkiller. Forget closing my eyes, laying down, or even applying an ice pack—I seek the quickest and most immediate relief possible, and normally that comes in the form of pills. However, fast relief can be found from another, more natural source: herbal beverages. So if you're tired of popping pills when you have aches and pains, try some of these herbal drinks out instead.

YouTube announced last October some of the original programming it was producing for its YouTube Red subscription service, and the first four originals went live on Wednesday, February 10th.

The Google Cast feature that serves as the primary interface for the Chromecast and comes bundled with Android TV devices like the Nexus Player is a marvel of modern technology. But as these things go, troubleshooting issues can be difficult with something so groundbreaking, especially when you consider that there are two parts to the equation—the casting device (your phone, tablet, or computer) and the receiver.

Five Phases of Hacking:- The five phases of Hacking are as follow:

Starting in Android 4.3, Google added some code to AOSP that tagged your internet traffic when you were running a mobile hotspot, which made it incredibly easy for carriers to block tethering if you didn't have it included in your plan. But as of Android 6.0, this "tether_dun_required" tag has been removed, which means you no longer have to edit a database file to get tethering up and running.

Brand loyalty is one of the main factors behind our decision to choose a particular mobile device, but it doesn't have to be the entire equation. Educated consumers know that certain devices simply fit their budget and usage better than others, which means you can't always let a logo dictate what kind of phone or tablet you buy.

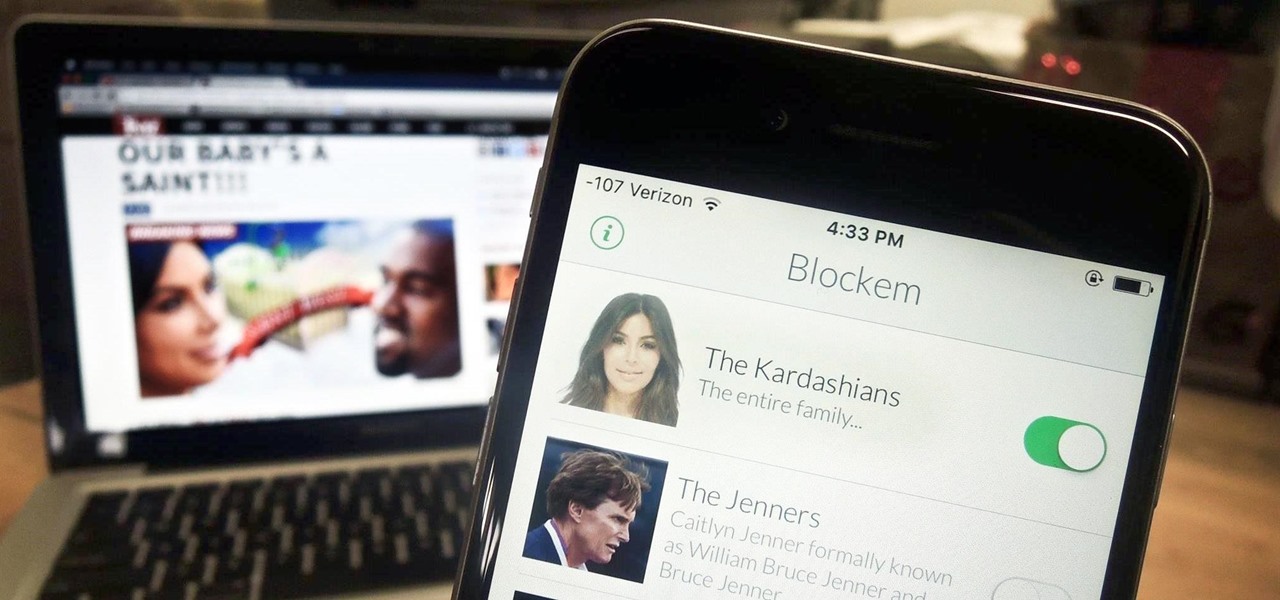
Kim Kardashian and Kanye West have fittingly named their second child "Saint," but I'm sure you don't care about that—and neither do I. Unfortunately, regardless of our pop culture interests, we're forced to know these types of stupid facts because the internet is so densely populated with Kardashian-related content that it's impossible to avoid. It's enough to make you puke.

The first written account of "stock" as a culinary staple goes back to 1653, when La Varenne's Cookery described boiling mushroom stems and table scraps with other ingredients (such as herbs and basic vegetables) in water to use for sauces. But really, the concept of stock has probably been around for as long as people have been using water to boil food.

The Xposed Framework was just recently made available for Android Marshmallow, but everything isn't quite back to status quo just yet. Sure, some Xposed modules function properly, but others are a bit buggy, and several don't even work at all. This is mostly a result of changes to the Android system that Lollipop modules relied upon, and such modules will need to be updated for Marshmallow compatibility.

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION

Live Photos is an interesting new feature introduced by Apple on the iPhone 6S and 6S Plus models that captures the moments immediately before and after you snap a picture in the Camera app, resulting in a GIF-like animation.

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.

Greetings, hackers and friends! I know it has been a while since I posted a tutorial, and hopefully I can make up for that by posting a series.
I've recently been on holiday in Europe, staying in a hotel that was part of a big chain that included many in the local area. A quick review of the wi-fi within range of my room showed that there was another in the chain that was in range of my Yagi Turbotenna, which naturally got me thinking. If I wanted an anonymous internet connection, this could be quite handy.

Thanks to the internet and its increasingly lack of privacy, secrets don't even seem safe in our own homes anymore. So how do you hide your secrets, stash your cash, or keep your valuable jewelry out of sight where no one can find it? Well, the answer might be right above you... if you're standing under the threshold of a door, that is.

One thing the whole Internet can agree with is that cats are cute and (sometimes) cuddly. But what those endless cat videos you find yourself watching for hours on YouTube don't tell you is that cats stink. While cats aren't the source of the smell, owning a cat means a stinky litter box.

Baking a cake is relatively easy... if you happen to have a cookbook or some boxed cake mix nearby. And though you can use the internet or your favorite cooking app, it can be nice to just cook without a recipe. That seems impossible with baking, which is such an exact science, but it's actually relatively easy.

Based on OTW's encouragement in his post on "How to Find the Exact Location of Any IP Address", I decided to make a gui(graphical user interface) which would hopefully make the process easier. However, because turning a python script into a standalone executable is a right pain in the nether-regions, particularly for linux, I haven't yet completed this step(I will soon and update this). I did however, make an apk for android(you use a .apk file to install an app on your android device), which...

There are countless methods and cleaners aimed at eliminating stubborn stains from everything to clothing, carpet, and furniture. But completely removing every last trace of a stain doesn't require an arsenal of chemical cleaners and repeated cycles in the washing machine. Most stains can disappear in a matter of minutes with a dose of alcohol.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

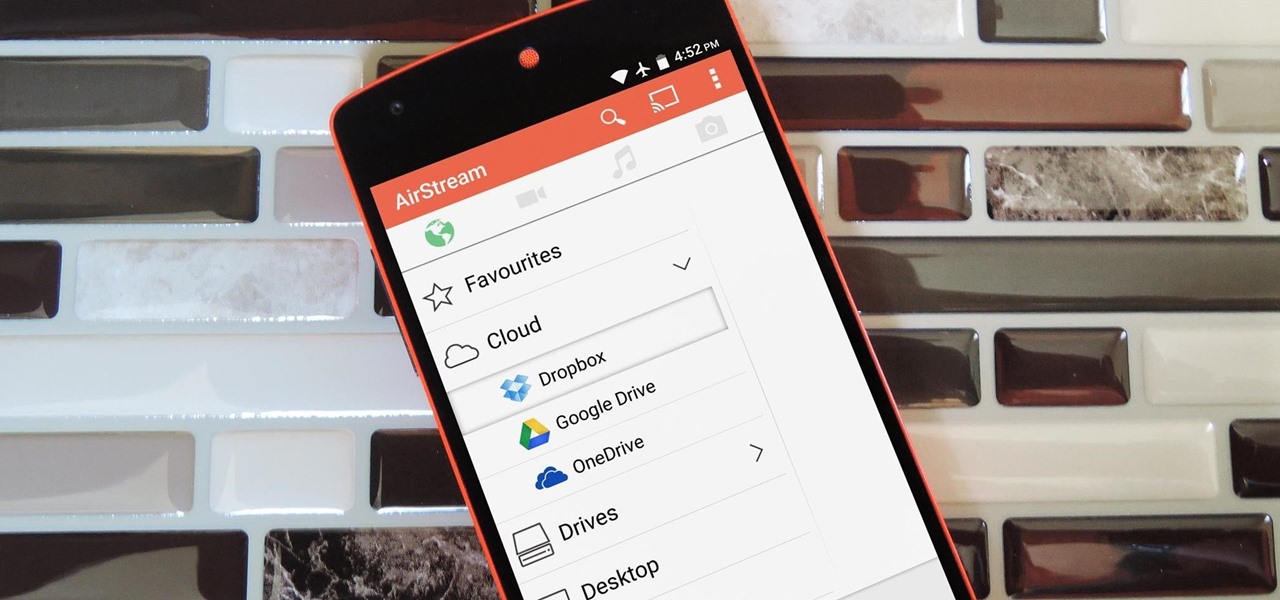
Smartphones generally have limited storage, but counter this issue with an always-on internet connection. This led to the proliferation of cloud storage services, which allow us to store and access our large media libraries remotely.

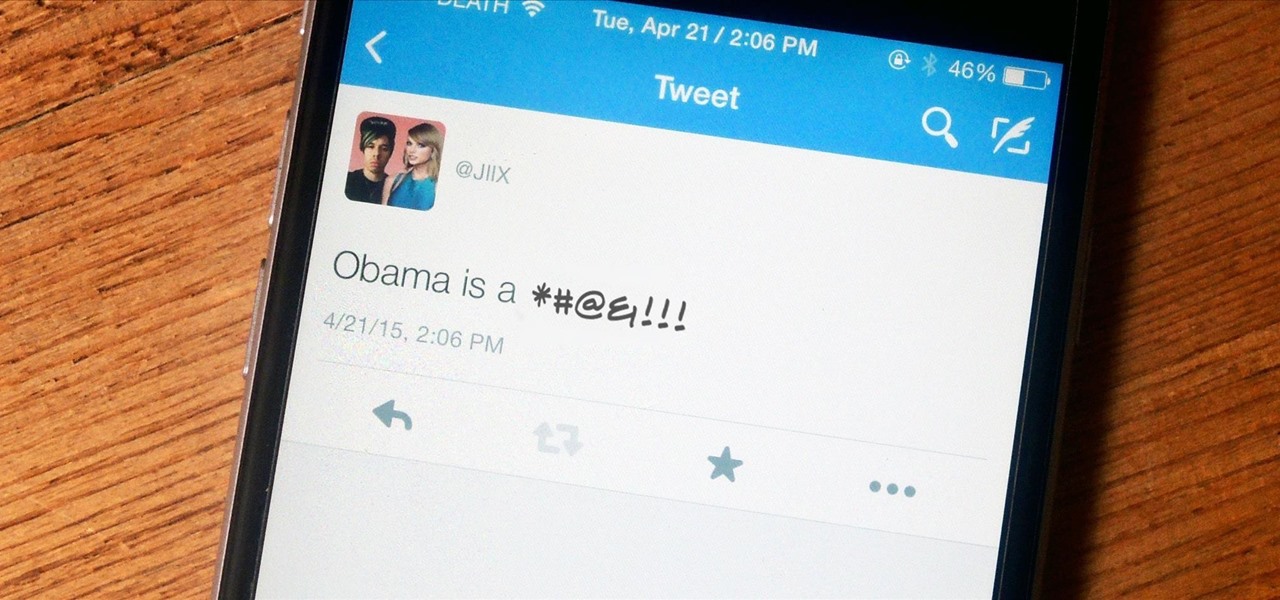
One tweet can get your fired from your job. At least, in the cases of Gilbert Gottfried, Rashard Mendenhall, Ozzie Guillen, and Mike Bacsik, who were all either fired or forced to resign from their jobs after posting regrettable tweets online.

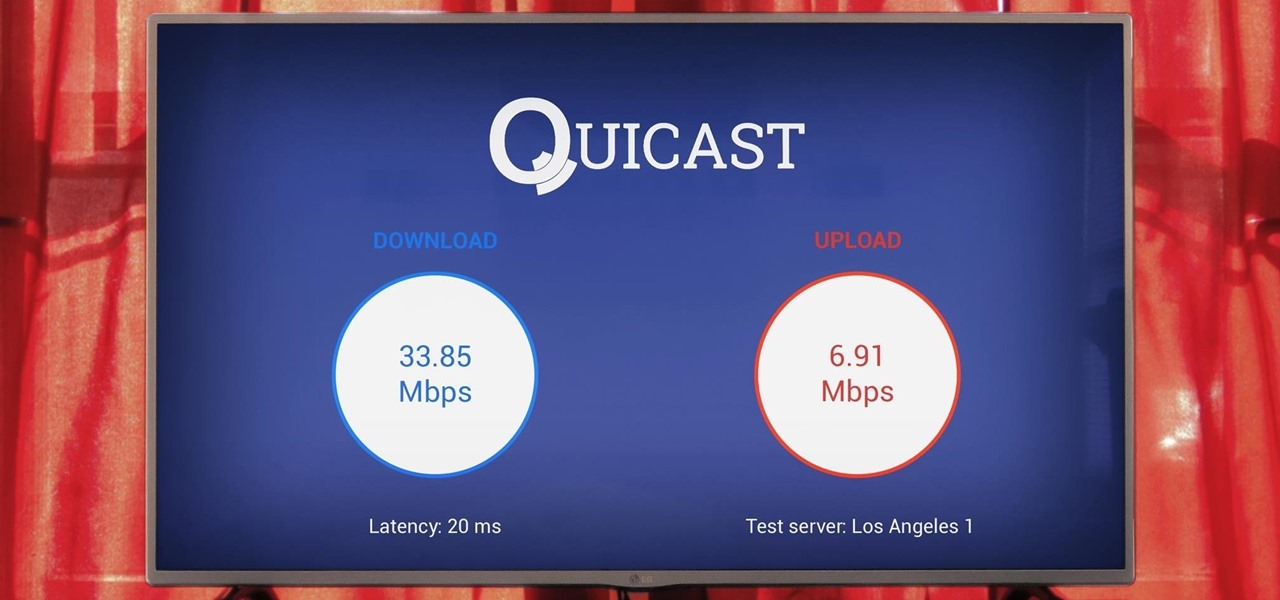
Recently, a group of Duke University students got together to tackle an age-old problem with mobile devices. You see, mobile data coverage isn't exactly ubiquitous, and many folks have restrictive mobile data plans, which means internet connectivity is not always an option.

If you're jonesing to play some Super Mario Run on your Android phone, you might not be able to get your fix for some time—at least, until Nintendo figures out the best way to keep piracy down and security high. But if you can't wait for the first official appearance of Mario on Android, we've got the next best thing...

Every smartphone manufacturer is susceptible to defects, but after dropping a good chunk of change on a shiny new device, we as consumers have little tolerance for such issues. We want our gadgets to be perfect in every regard, so even the tiniest flaw is irksome.

Back in the '80s, recording live radio was as simple as popping a cassette tape into your boombox and pressing the record button. While we've come along way with regard to accessing radio stations thanks to websites and apps that stream live broadcasts over the internet, it's no longer quite as easy to record.