
How To: C++ Hash Cracker
This is my first ever how-to so I apologize in advance for any grammar mistakes or spelling errors. Introduction


This is my first ever how-to so I apologize in advance for any grammar mistakes or spelling errors. Introduction

I love brownies. Through the turmoil of my teenage years and the raucous over-eating of my college years to now, brownies have been a constant companion to my highs and (calorie-laden) lows. I've made brownies from scratch, I've used the box mix... hell, I was a baker at a bakery that specialized in brownies. So yeah... I'd say I'm pretty familiar with them.

Boxed brownie mixes advertise their convenience compared to homemade brownies—with only a few ingredients, they promise a moist, chocolatey crumb. However, these "instant" mixes still require fresh ingredients and a baking time that matches that of homemade brownies. When you're craving a chocolate fix but you're coming up short on eggs, oil, and time, don't despair: you can still make brownies using a can of soda. Two Different Methods, One Soda Required

Piracy, it can be argued, is the scourge of the internet. But when it comes to music, sometimes it's best to give a listen to a track or album before deciding to spend your hard-earned money on fully supporting it.

Hello, multicolored-hat hackers!

Other than salt, there's no ingredient that's as big a kitchen staple as olive oil. And just like salt, there are a million little known uses for it.

While a mobile game developer may have built something unique, they still have to go through an arduous process of fixing bugs, smoothing out gameplay, making sure it works on different screen sizes, and following Apple's rules before they can submit their game to the iOS App Store.

If you're a Mac user with an Android phone, some apps on your computer aren't very useful, such as Messages, which is meant to work and sync with iOS devices. But now, thanks to MDRS, LLC, using the Messages app on your Mac with an Android phone is now possible and easily achievable. Plus, we've got 50 promo codes to give away for a free year of service!

With smartphone screens getting bigger by the generation, one-handed mode mods are becoming rather prevalent. Most of these function by shrinking the screen to a more manageable size, but this is actually kind of boring when you think about it.

The Apple Watch is finally here! We'll have loads of guides and videos for you guys to check out in the following week and beyond, but we thought it'd be best to start off showing you how to set up and pair that brand new beautiful Apple Watch of yours to your iPhone.

One lump or two? That was the age-old question with sugar cubes, which used to be a staple of any tea salon or dignified household this side of Downton Abbey. These days sugar isn't really used in cubes much except in bars and restaurants, and that's a shame. Cubes are a lot less messy than granulated sugar, and you can measure the exact amount you put in your drink no matter what.

Throwing a party means making sure everyone has fun, but that pursuit can quickly get out-of-hand. Before you know it, you're once laid back get-together has received so many RSVPs that it becomes obvious you're throwing the party of the century. With an over-abundance of beer and an inflated guest list, your newly-formed epic reputation must live up to the hype.
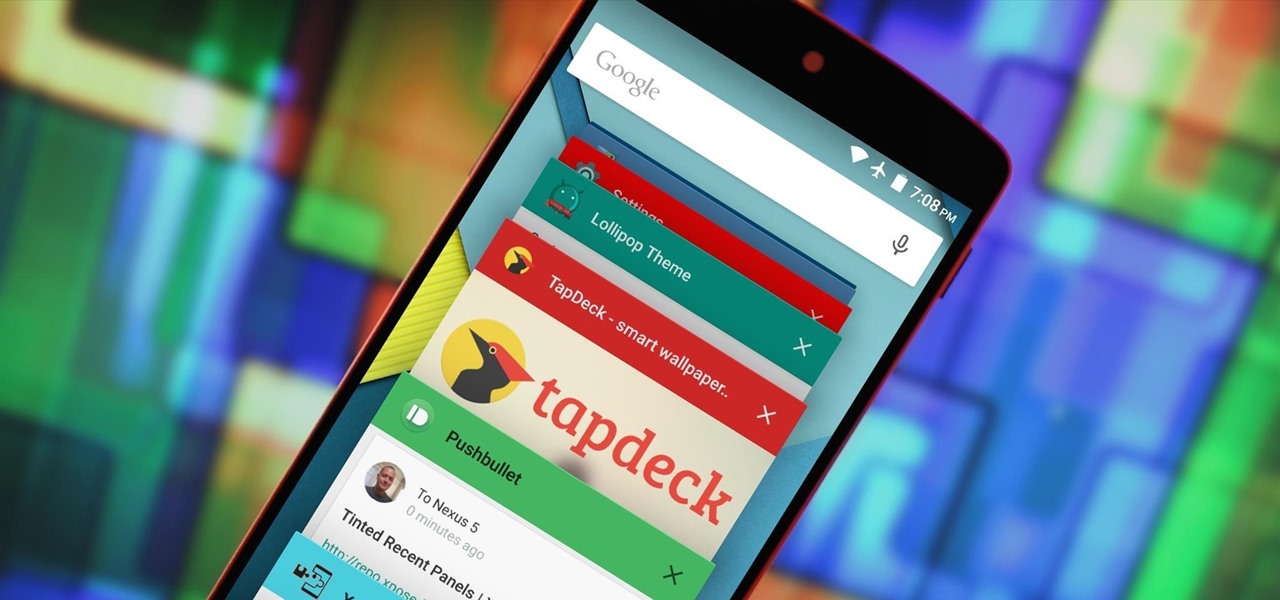
The Overview screen (aka Recent Apps) on Android got a huge upgrade when 5.0 Lollipop was released. Chrome tabs now hold separate entries in this multitasking list, which also got a nice new Material Design theme. One of the biggest changes, though, was a new API that allows apps to color the header on their entries in this list.

Tinder, the extremely popular dating app, has the wonderful tagline, "Any swipe can change your life." However, if you downloaded their most recent update, your next swipe could cost up to $19.99.

Today marked the official unveiling of the HTC One M9 at Mobile World Congress in Barcelona. The newest HTC flagship will be released by the middle of March globally, and come in gold, gunmetal, pink, and silver. And if you were wondering, yes all of the leaks were pretty much spot on.
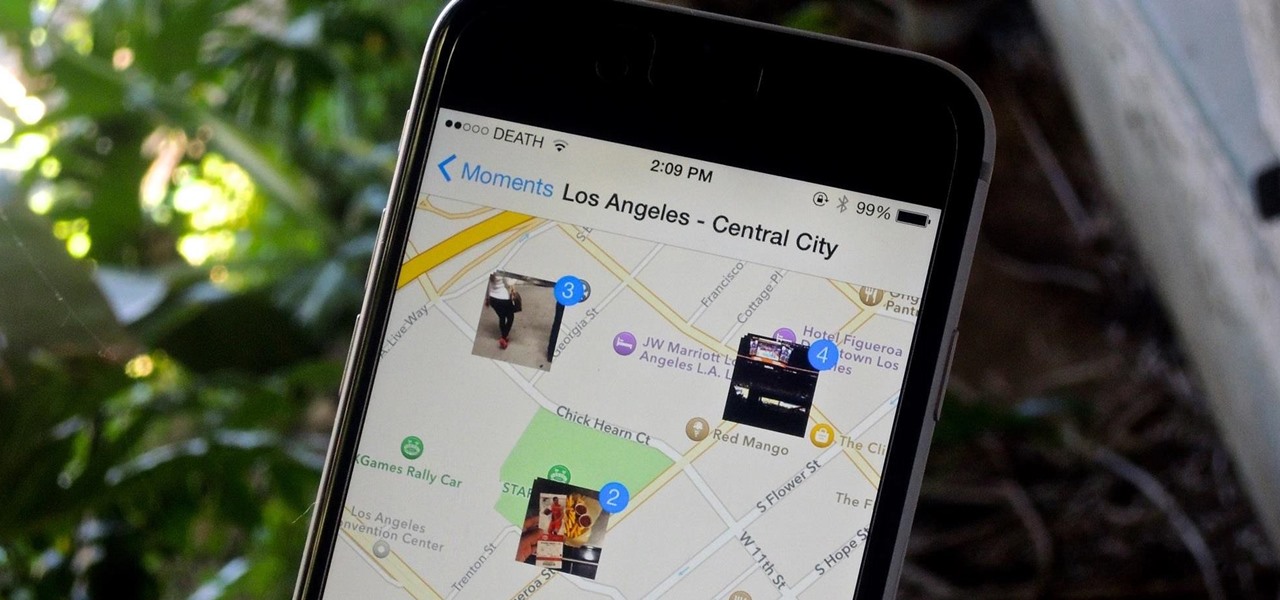
Location Services, a native feature on iPhones since iOS 6, is used to pinpoint your approximate location using a combination of GPS, Bluetooth, Wi-Fi, and cell tower information. Apple uses this on their smartphones for many useful reasons: so that you can tag locations in Instagram, get better directions in Maps, and check for matches based on your location in Tinder.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

Scented candles tend to magically turn a house into a home. The light flicker of the flame gives a relaxed or romantic tone to the atmosphere, and keeps the space smelling fragrant for hours. The only problem? Wax melts, and the candle becomes worthless after the wax is all gone. So how do you keep the flame going for more than a few hours? Simple, just remove the problematic ingredient—don't use wax!

We've previously shown you how to get your Samsung Galaxy S4 looking more like its successor by installing the revamped S Voice app and the new Quick Settings. Now, we're taking it a step further by giving you the Galaxy S5's stock Settings app. After this mod, it'll be pretty hard for others to distinguish your GS4 from a GS5.

Creativity and well thought-out planning are qualities to be admired when choosing a costume for Halloween. Going out in hordes to purchase the same 'ol outfits from a local costume warehouse means you're probably wearing the same thing as thousands of other people.

I have never been a morning person, and that's a trait that I don't think is going away. Combine my distaste for early hours with being a heavy sleeper, and it adds up to a lot of alarms being dismissed in a haze, with no real intention of ever waking up.

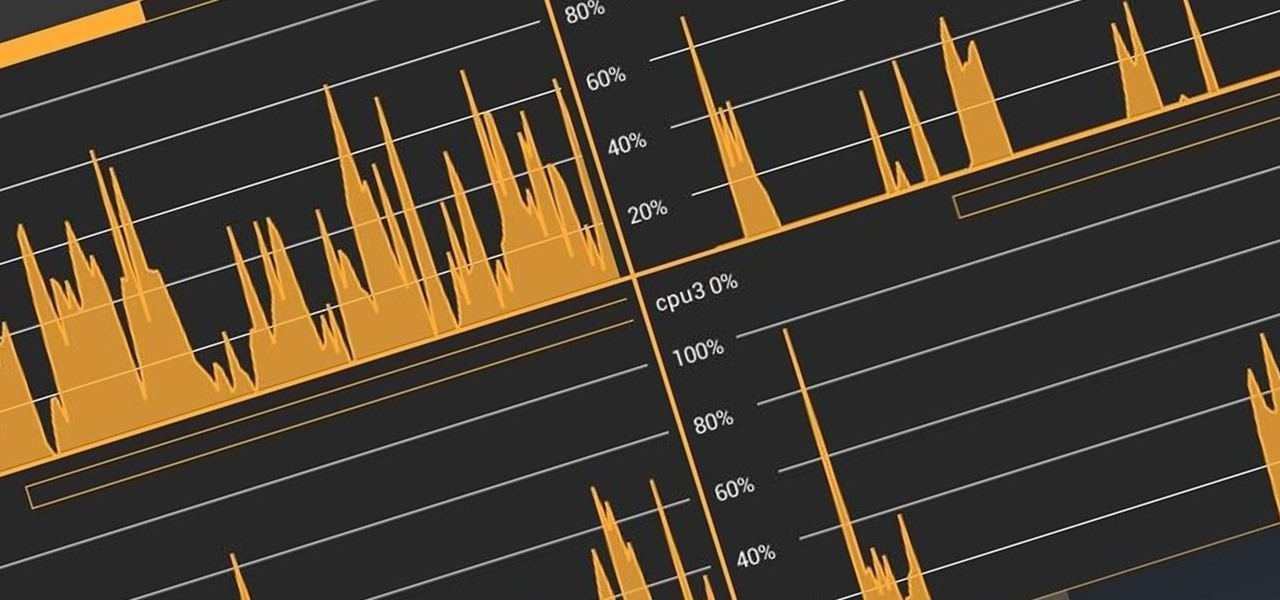
At the core of your Galaxy S5's hardware lies the central processing unit, or CPU for short. Practically every piece of data, every binary bit, has to pass through your CPU before it can be used to display a video or execute a game command.

If you keep sensitive data on your phone, you've surely considered a "lockout" app before. There are many such apps that can add an extra layer of security to other apps within Android. For instance, you can require a PIN or password before anyone is able to launch a particular app.

Although lacking in megapixels, the HTC One M8's camera can be considered a top-tier, flagship-level shooter. With the Duo Camera and UltraPixel technology behind it, it can make even the most inexperienced photographer snap pictures like a pro. There seems to be little missing for the average user, but for the more seasoned photographers, some of the standard settings may seem a bit too dumbed down.

I regularly use iTunes on my home laptop and my work desktop forty-five traffic minutes away. I'm ashamed to admit it, but until recently, I'd been saving my iTunes library on a USB and transferring it back and forth, over and over again, between the two computers.

Merely fidgeting and shivering can burn calories, but now you can add trembling in fear to the list too. Just pop in a good horror movie and turn down the lights to burn off up to 200 calories. What would you rather do? Walk for over 30 minutes or watch a 90-minute scarefest?
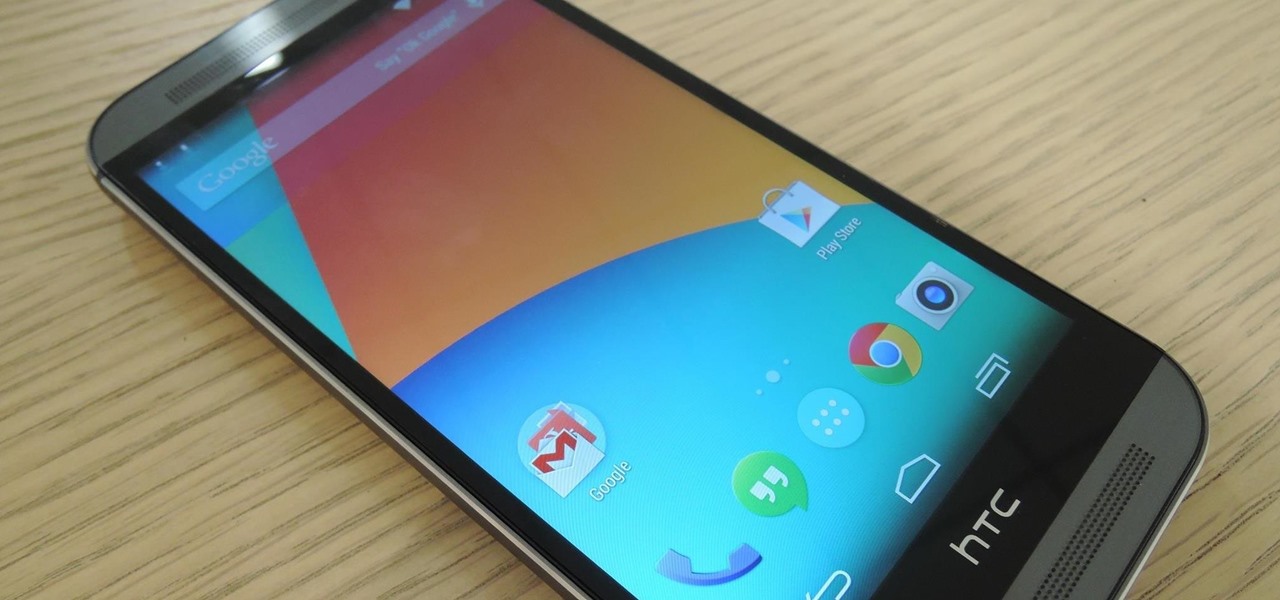
There really isn't any custom manufacturer skin, like Sense, that can match the clean look and fluidity that comes with stock Android. HTC knows this, and they, just like Samsung, include a Google Play Edition version in their flagship lineup.

Hey, coffee drinkers—your morning cup of joe is killing your metabolism.

Released last year for iOS devices, Frontback is a simple photo-taking and sharing app that not only snaps a picture of what's directly in front of the camera, but also behind it, which is to say, a selfie.

What's the point of having a 1080p screen if you're not using it to get in some quality gaming time? Google Play is great for downloading games, but you probably already have an extensive library of games for your consoles, so use those!

The wait is almost over. The sixth season of Game of Thrones kicks off this Sunday, April 24th at 9 p.m. (PT) on HBO, or at 5:57 p.m. (PT) on HBO GO and HBO NOW, with the first episode "The Red Woman."

Dried fruit makes a great, healthy snack by itself, and it's a nice addition to both sweet and savory dishes. Most people assume you have to have a dehydrator to make it at home, but you don't really need one unless you plan on drying fruit pretty frequently. Your oven does the job just fine. Drying fruit in an oven is a pretty simple process: just bake it at a low temperature for a long time. It's usually cheaper than buying dried fruit from the grocery store, and a great way to use extra fr...

Samsung's exclusive music streaming service, Milk Music, has been making waves across the web thanks to its peculiar name and ad-free stations.

You can read at 500 words per minutes. Don't believe me? Here, see for yourself. This amazing technology comes from the startup Spritz, and they're ready to unleash it onto the smart device world, starting with the Samsung Galaxy S5 and the Galaxy Gear line of smartwatches.
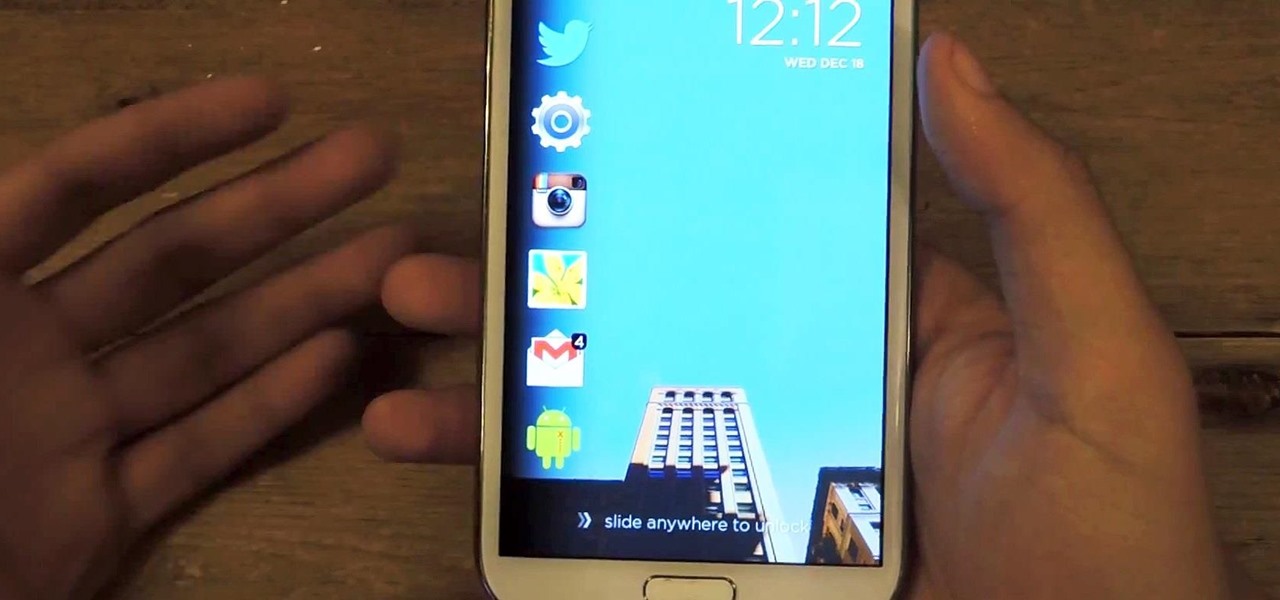
Not particularly good looking, TouchWiz's lock screen adequately supplements the clunky and almost cartoonish-look of the infamous user interface on the Samsung Galaxy Note 2. While there are hundreds of lock screen options in the Google Play Store, I've never quite discovered one that I've thoroughly enjoyed, due to the obfuscation from so many options.

It may not be as large as the Samsung Galaxy Note 2, but the Galaxy S3's screen size is still big enough to make iPhone owners cry themselves to sleep. The 4.8-inch AMOLED display with 720 x 1280 pixels makes the GS3 a great mobile companion—and an even better portable gaming device.

We've gotten pretty close to a Google Experience before, and even played around with the actual Google Play Edition build. However, the devs over at XDA have a much better solution: actually converting your HTC One into a complete factory-fresh Google Play Edition.
I remember how fast my Nexus 7 was the first time I turned it on. Boy, do I miss it. Now my tablet is pretty buggy and crashes happen frequently, and I'm sure that goes for many of your Nexus 7s as well. Even if you upgrade to the new Nexus 7 next week, it will eventually develop similar issues.

Every time Apple releases a new version of their mobile operating system, it comes packed with an assortment of bugs, issues, and other hindrances.

If you thought humans were reading your résumé, think again. Robots do, and their one solitary objective is to systematically crush the hopes and dreams of those who don't make the cut. Instead of paying a few humans to read thousands of résumés over a couple weeks, many companies use computer programs that can do the job in less than an hour. In fact, at least 90 percent of Fortune 500 companies use what they call an applicant-tracking system, aka rejection machines.