Wrapping leather is the least of your worries when it comes to the meticulous and dexterous art of making jewelry. IIf you have the basic jewelry making skills down, doing this wire-wrap on leather should be a cinch.. This demonstration video will help walk you through the process of wire-wrapping leather.

The clam shell is a clasp for homemade jewelry. Putting a clam shell on can be difficult, because jewelry making is meticulous and dexterous, but with a crimper, it should be easy. But a crimper isn't all, a pair of pliers is also needed. This demonstration video will help walk you through the process of this clam shell attachment.

Afraid to wear black because of your dandruff problem? There are many ways to cure dandruff so don’t give up hope. Try the home remedies and if you need to there is always medicated shampoos for the problem.

A computer’s safe mode is useful when fixing problems or saving work after, say, your hard drive malfunctions. Safe mode can easily be accessed as your computer starts up and is a useful tool to have in your belt.

If you want to improve violin technique then this tutorial is for you. This violin lesson teaches you to play broken third in 1st and 3rd position. This exercise, based on the Yost system, is designed to increase your familiarity and comfort in all positions, develop confidence and accuracy in all positions, develop an understanding of what to listen for while shifting, and improve your ear training and overall intonation. When practicing this exercise you should relax your fingers, hand and ...

If you want to improve your violin technique then this tutorial is for you. This violin lesson teaches you to play thirds in 1st and 3rd position. This exercise, based on the Yost system, is designed to increase your familiarity and comfort in all positions, develop confidence and accuracy in all positions, develop an understanding of what to listen for while shifting, and improve your ear training and overall intonation. When practicing this exercise you should relax your fingers, hand and w...

If you want to improve your violin technique then this tutorial is for you. This violin lesson teaches you to play thirds in 2nd and 4th position. This exercise, based on the Yost system, is designed to increase your familiarity and comfort in all positions, develop confidence and accuracy in all positions, develop an understanding of what to listen for while shifting, and improve your ear training and overall intonation. When practicing this exercise you should relax your fingers, hand and w...

If you want to improve your violin technique then this tutorial is for you. This violin lesson teaches you to play an advanced thirds exercise. This exercise, based on the Yost system, is designed to increase your familiarity and comfort in all positions, develop confidence and accuracy in all positions, develop an understanding of what to listen for while shifting, and improve your ear training and overall intonation. When practicing this exercise you should relax your fingers, hand and wris...

If you want to improve your violin technique then this lesson is for you. This violin tutorial teaches you a way to improve ear training with octave exercises. This exercise is based on the Yost system. This exercise is designed to increase your familiarity and comfort in all positions, develop confidence and accuracy in all positions, develop an understanding of what to listen for while shifting, and improve your ear training and overall intonation. When practicing this exercise you should r...

Do you want to improve your violin playing technique? This violin lesson teaches you a great exercise to improve your octave playing in scales. This exercise is based on the Yost system. This exercise is designed to increase your familiarity and comfort in all positions, develop confidence and accuracy in all positions, develop an understanding of what to listen for while shifting, and improve your ear training and overall intonation. When practicing this exercise you should relax your finger...

Reiki is a form of holistic healing that originated in Japan. It is a way of magnifying the healing "ki" energy of the hands. Reiki uses the same kind of non-physical "ki" energy martial artists use to nourish the body's health and vitality.

n this how to video clip series, learn the proper way to tackle a tree trimming project. Lessons include having the right equipment and tools, safety gear, what order to cut branches in, and other important tips and cautions. Make this home & garden project a safe and effective one, says George Finn.

This video series will show you tips, techniques and information about how to teach your children to read and what methods are most useful in certain cases. Our expert, Debbie Noah, not only explains how children comprehend reading but also ways to make it fun for them and gives you tips on where and when reading to your child is most effective.

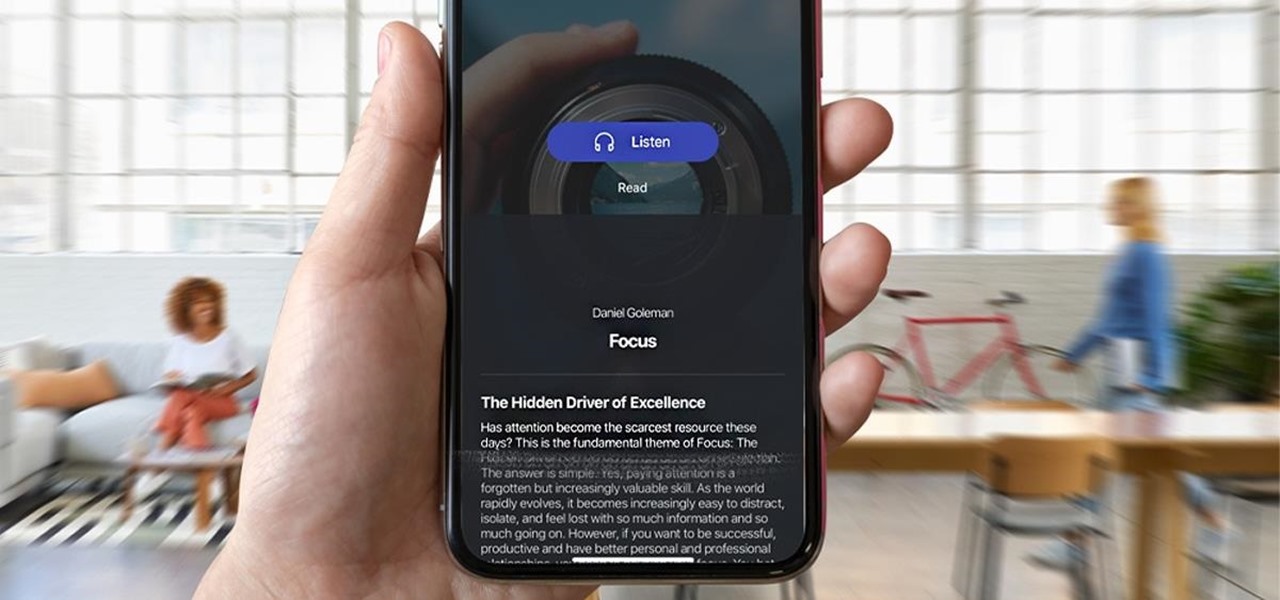
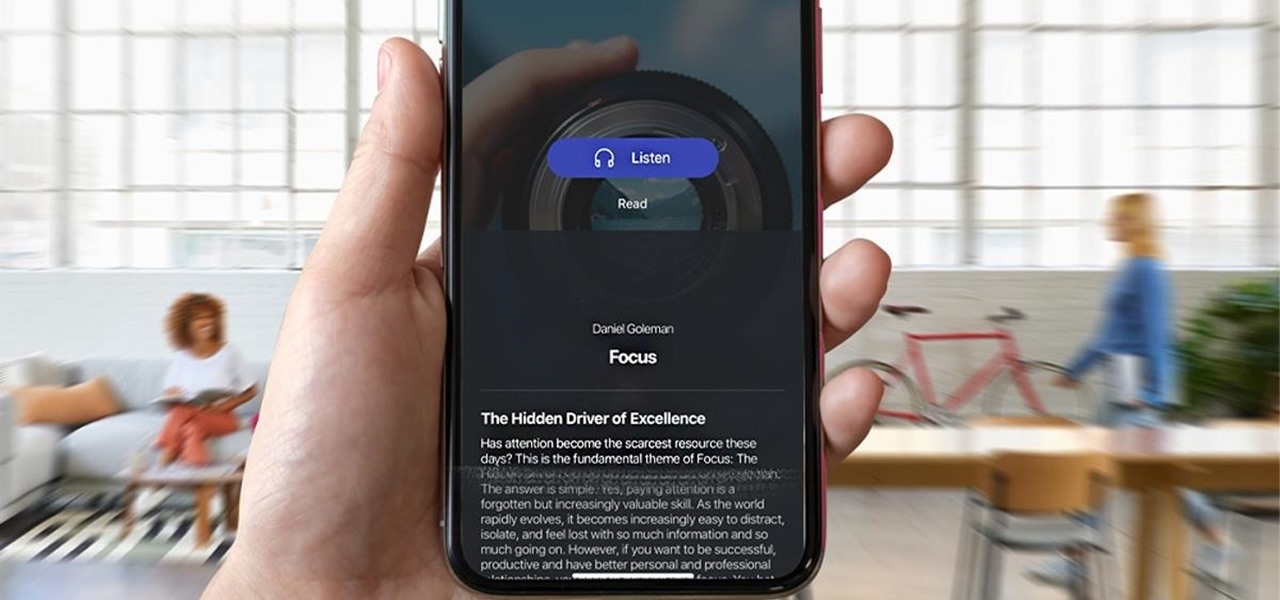
Reading is as gratifying as it is time-consuming, the more you put it off, the bigger your to-be-read stack gets. Eventually, that stack will become a shelf, then a case, and then even if you want to read, who has the emotional fortitude to pick just one from all those unread books. With 12min Micro Book Library: Lifetime Premium Subscription you can read an entire book from start to finish in 12 minutes without losing any of the meaning, and it's on sale now for $39.

As much value as you can get out of reading, finishing a book takes a while, even if it's a best seller or a unique and valuable piece of work. To save you time while still giving you the value of reading, 12min Micro Book Library: Lifetime Premium Subscription provides access to hundreds of micro-books that can be fully read in just 12 minutes, and you can get it for $39 while it's on sale.

We're living in the age of Big Data. As the primary force behind everything from targeted marketing campaigns and online search algorithms to self-driving cars and even space exploration, massive sets of complex data stand at the heart of today's most exciting and important innovations.

If you're interested in becoming an in-demand project manager or leader in today's data-driven world, you need to know more than just a few generic management strategies to lead teams and companies successfully.

With thousands of people across the country protesting, you might be thinking about joining the march. But as is too often the case, law enforcement has been called to oversee the protests, and interactions aren't always peaceful or lawful.

After more than two years of teasing, augmented reality startup Mojo Vision has confirmed that "invisible computing" means what we've suspected all along.

Sniffing packets over a network is an easy way for hackers to gather information on a target without needing to do much work. But doing so can be risky if sniffing packets on an untrusted network because a payload within the packets being captured could be executed on your system. To prevent that, Sniffglue sandboxes packet sniffing to provide an extra layer of security.

The wearables space experienced its "big bang" moment back in 2015 when Apple released its first wearable device, the Apple Watch. Although the device was initially dismissed by some as an unnecessary charm bracelet packed with frivolous tech, in very short order, the public learned just how useful the Apple Watch can be.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

Developers and enterprise customers chomping at the bit to get their hands on HoloLens 2 may not have to wait much longer, as Microsoft passed one of the remaining hurdles needed to release their new tech into the wild.

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

Niantic's Harry Potter: Wizards Unite offers players an augmented reality look into the world of witchcraft and wizardry. The Wizarding World and Harry Potter novel series is full of unique and interesting characters, which is why it makes sense that Wizards Unite offers you to take the role of one of three "Professions" — Auror, Magizoologist, and Professor. The question is, which one do you pick?

The ability to shift between virtual reality and augmented reality seamlessly on one device is a dream of many AR fanatics, but the execution is usually fairly buggy or underwhelming.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

If you want your photos to look like they came straight out of a movie scene, the best method is to use split toning. Many Hollywood producers use this effect to recreate the cinematic look of cameras before the digital film era, which is why most people associate split toning with a cinematic feel.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

In recent years, many software publishers have tried to sell the business community on remote meetings via VR, but if social media chatter is any indication, it hasn't taken off in a big way just yet. However, for some, the notion of holding remote meetings using augmented reality, a medium in which you're still directly tied to the real world and not closed off in a blindfold-style VR headset, might be the better solution.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Action Launcher has some exclusive features that add real value to your overall experience. One such feature is Shutters, and like with most aspects of Android, there's a workaround that will let you enjoy this functionality on other launchers.

You may have noticed improved photo quality in the Android Snapchat app in recent months. Believe it or not, this is because Snapchat only just recently started using a decade-old camera API that predates every Android phone in existence.

If you can't afford an unlimited plan, you're limited to a certain amount of data each month on your iPhone. Even some unlimited data plans have carrier-imposed mobile data caps that throttle the user if they exceed them. Keeping track of your exact usage each day will help make sure you don't get billed more or throttled like a chump near the end of the month.

One of the biggest improvements with the Galaxy S9 and S9+ is the redesigned camera, with the latter scoring an impressive 99 overall on DxOMark. But with an abundance of features and enhancements, tweaking the camera's settings for optimal performance can be a little confusing.

One of the standout features of Nova Launcher is its vast customization options. Not only does it includes numerous tweaks to alter the aesthetics of your home screen, but it even has plenty of features that reduce clutter. One area of our device that has a high potential for disarray is our home screen.

There are over 3 million apps in the Google Play Store, all optimized for the small screen in your hands. While that number sounds staggering, there are still many online tools and websites that require you to use a mobile browser since app development is expensive. However, that's where Progressive Web Apps (PWAs) come into play, a cost-effective way to turn websites into mobile apps.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.