Listeria monocytogenes bacteria don't play fair. Healthy people can usually handle the food-borne infection, but the bacterial infection hits pregnant women, fetuses and cancer patients very hard. Interestingly, a new study found that other bacteria may help prevent Listeria infections in those people.
Samsung's recent TouchWiz rebranding didn't really change much — the skin is still as bloated as ever, and the UI still uses tacky accent colors. But while you can't fully remove TouchWiz without rooting, there are ways to make it look a lot better.

As headlines focus on melting glaciers and rising water levels caused by global warming, climate change is quietly taking its toll on the nearly invisible occupants of this planet, the microbes.

In order for software developers to do their jobs as new hardware reaches the market, they will need the right tools to get their projects off the ground and into augmented and mixed reality devices. There have been completely new approaches to development when it comes to AR and MR, and these are some of the faces behind them.

A virtual design and construction services firm has built an augmented reality application that uses the Microsoft HoloLens to improve the efficiency of quality control on construction sites.

If you have a HoloLens, you can now control the lighting throughout your home or office via holographic controls using the free Hue Lights app in the Windows Store. The app, made by California-based AfterNow, works with the Philips Hue colored lighting system and is much more polished than the prototype we saw in January.

Specialized cells in the lining of the gut may provide a key to preventing an infectious brain disease caused by misfolded proteins.

A gold-medal winning entry into the iGEM synthetic biology competition could change the way we look at Esherichia coli, the bacteria better known as E. coli.

Pumpkin pie is a symbol of autumn, and it's the traditional dessert to whip up for your fam when Thanksgiving Day arrives. But year after year of the same old thing can be a total bore if you're not a strict traditionalist. So, we found 8 unique ways to make that pie a little less snooze-fest and a little more interesting.

Whether you made the switch from iOS, or you came from a different Android device, there's a lot to learn about your new Galaxy device. Samsung does things a bit differently, and thanks to their TouchWiz interface, there are tons of added features to take advantage of—though some folks might find these extras to be a bit too much.

Microsoft's HoloLens comes with helpful features for capturing video and photos, but sharing whatever you record isn't as straightforward as you might expect. So here are the many ways to get your media off the device to share with the world.

Garlic is a key ingredient in many delicious meals, and if you've been a fan of our site for even a short while, it's no secret that we love to share tricks and tips to make cooking with garlic even easier than you first assumed.

This is an in-depth look at how to drive a Peugeot 308 ALLURE SW (2015, 2016, and 2017 European model) with an automatic gearbox and transmission.

Alright, NB community! Here we go... Bubble Sort. What Is Bubble Sort?

Macs are generally highly power efficient due to, in part, the optimized sleeping schedule with OS X. Yet in certain scenarios, you might not want your Mac to go to sleep: downloading a huge file, reading a book, reviewing a spreadsheet, analyzing some content on the screen... the list goes on. To resolve this, you can go to System Preferences and mess with the settings, but this can be an annoying process if you need to do it often.

Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

If you purchased something from iTunes, the iOS App Store, iBooks Store, Apple TV App Store, or the Mac App Store and it doesn't work, didn't download, is buggy, or wasn't what you thought it was, you can get a full refund from Apple—you just have to know how to ask.

Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems with your newly discovered vulnerability with impunity!

In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.

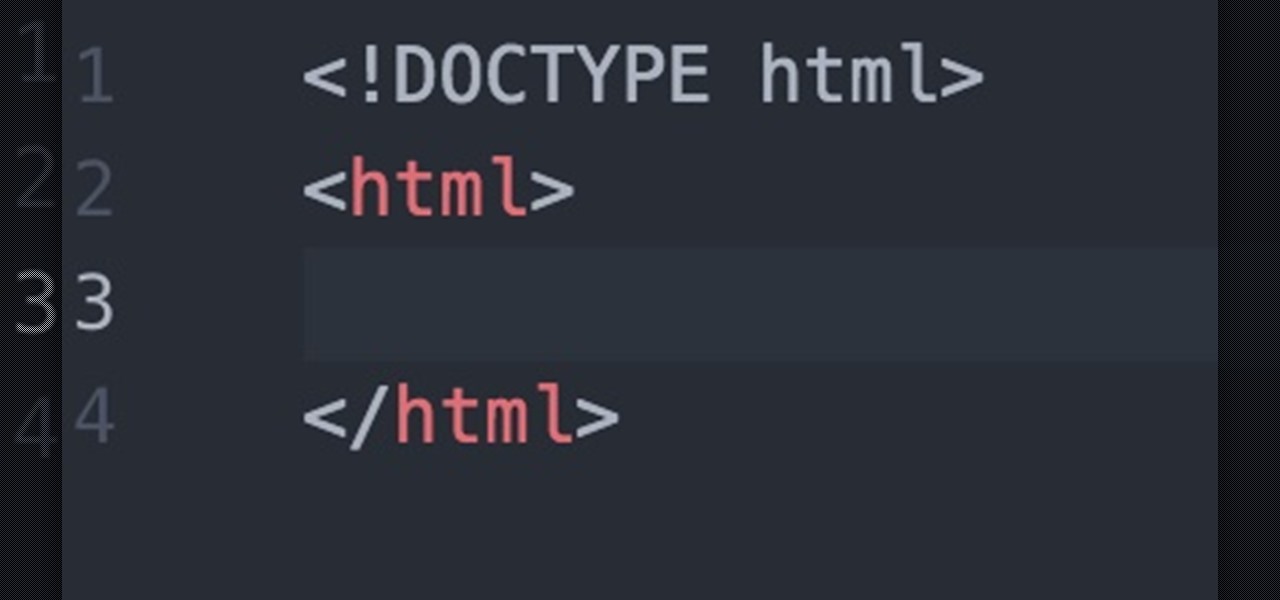
Hello fellow Null-Byters! In this "tutorial" we will be going basics of HTML. In the next tutorial, we will be going over CSS and then apply JavaScript.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

When it's time to get down to work, a clean, organized workstation is key to accomplishing tasks and being more productive. Or, so we thought.
I see many people posting the same thing on the internet. "How do I become a hacker? Where do I commence?"

Historically, battery life has not been a strong suit for machines running Windows. Poor decisions by hardware manufacturers combined with the resource-hogging behavior of Windows are to blame. However, Microsoft is trying to resolve this issue, once again, with the release of Windows 10.

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.

No offense to water, but if I could survive on coffee alone, I would. I swear I'm not addicted... I just really, really, really love the taste of a cuppa joe, whether it's hot, cold, frothed, milked, flavored, plain, whatever! And while my favorite thing to do with coffee will always be to drink it, recently I've become crazy about using coffee in cooking.

As Android owners, we ultimately have to look at our device and ask the difficult question: "Where the hell did all these applications come from?"

When it comes to smartphones, the biggest complaint voiced by most users is battery life. Sure, it's unrealistic to expect your Android device to run for weeks without a recharge, but many folks struggle to even make it through the day without having to top off their battery.

The wait is over. The Samsung Galaxy S6, arguably the best Android phone of this year, has just launched. There was already a lot of hype about this super phone—its looks, its specifications, and its other functions have been under the microscope for quite some time. It will not be a good idea that you take this phone in your hand and use it in the same fashion as you have been using your other phones in the past.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

Complete silence or a non-stop Pandora playlist? People are often divided on what type of work environment they prefer. Whether you're a frequent loud music listener or you can't stand any kind of background noise, chances are you're pretty set in your ways.

Third-party keyboards have been available for iPhone ever since iOS 8, but which ones are worth checking out? There have been many options over the years, and if you want keyboard features like swipe-typing and themes, you're going to have to put Apple's stock QuickType keyboard on the backburner and try out these top hits.

Better sleep, smartphone news, and changes to your favorite forms of entertainment. There's been a lot going on over the last couple of weeks in the world of tech, and we thought we'd show you all of the need-to-know products, updates, and ideas that we think are most important.

Listen, I'm not disparaging using really good knives—they can literally change your life, or at the very least, the way you work in the kitchen. However, there are many cutting and slicing tasks where you're better off using a sturdy pair of kitchen shears rather than a chef's or even a paring knife.

The microwave oven is a monumental technological achievement that's saved college students and single people from starvation for decades. Almost 97% of all American households have one, which makes it the most-owned kitchen appliance in US homes right after the refrigerator.

After many beta builds, Apple has finally released iOS 7.1 to the public. It includes bug fixes for the old iOS 7.0.6, along with UI enhancements and even some new features.

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

February may be the shortest month of the year, but for iOS softModders, there were plenty of apps and tweaks to fill up those days. Whether patching major security holes or just a tweak to make speed dialing more efficient, there was a plethora of great mods for our jailbroken iOS 7 devices. These are our favorites from the month.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.