News: Light & Composition Magazine Photo of the Day (and Month) Photography Contest - Ongoing
Type: Purist photography, no visual or graphic art manipulation Theme: Photo of the Day

Type: Purist photography, no visual or graphic art manipulation Theme: Photo of the Day
Type: Photography, no visual or graphic art manipulation or HDR Theme: Show Off Your School™
Type: Photography, no visual or graphic art manipulation Theme: Streetscape

Type: Photography, no visual or graphic art manipulation Theme: World's Cutest Pet

Type: Photographic Art Theme: All
This was a five-week contest with a weekly $250 winner. It has been extended two more weeks! So dig out those cute kid pictures for a chance at $250.

This is the last week of an eight-week contest that I just happened upon. One winner is awarded from each week so it's not too late to enter if you have pictures of this theme. The voting starts next week and is open for a week. Submission and the rules are easy for a chance at $250.

Type: All photography styles and themes Theme: Open to traditional, contemporary, alternative process, digital, mix processes, manipulated and experimental works

Ever been warned that sitting too close to the TV might damage your eyesight? It won't. That probably won't stop this electronic View-Master from giving your poor mother a heart attack, however.

It's one of the most popular queries on the web, meaning the wet electronic disaster is likely a common mishap. There are many answers out there, but if you're lucky enough to have never googled it, pay attention now. You never know when you may drop your cell phone or iPod in the sink...

It's been almost a century since we've last seen Kid Icarus start in his own game! The result of Project Sora, Kid Icarus will be released for the Nintendo 3DS!

Co-Directed by WonderHowTo's Ford Austin. Do any of those actors look familiar? If you like it vote for it here

Ever had poutine? It's a Québécois dish, consisting of french fries topped in fresh cheese curd and then smothered in brown gravy.

Arduino fashion (essentially, electronic textiles that can perform a variety of functions) is certainly not a new idea, but the Ping social networking garment brings a fresh and exciting perspective to the concept.

Does this sound difficult? It probably does to most people. Don't feel overwhelmed. Iin this step by step video series it will not only be better explained but Ross Safronoff, our expert, will show you how simple it really is and how to put it to work for you. Electricity is very powerful when harnessed correctly. He will walk you through every piece of equipment and detail of how electricity works and how we use it to our advantage as well as show you how to put it to use on a garage door. B...
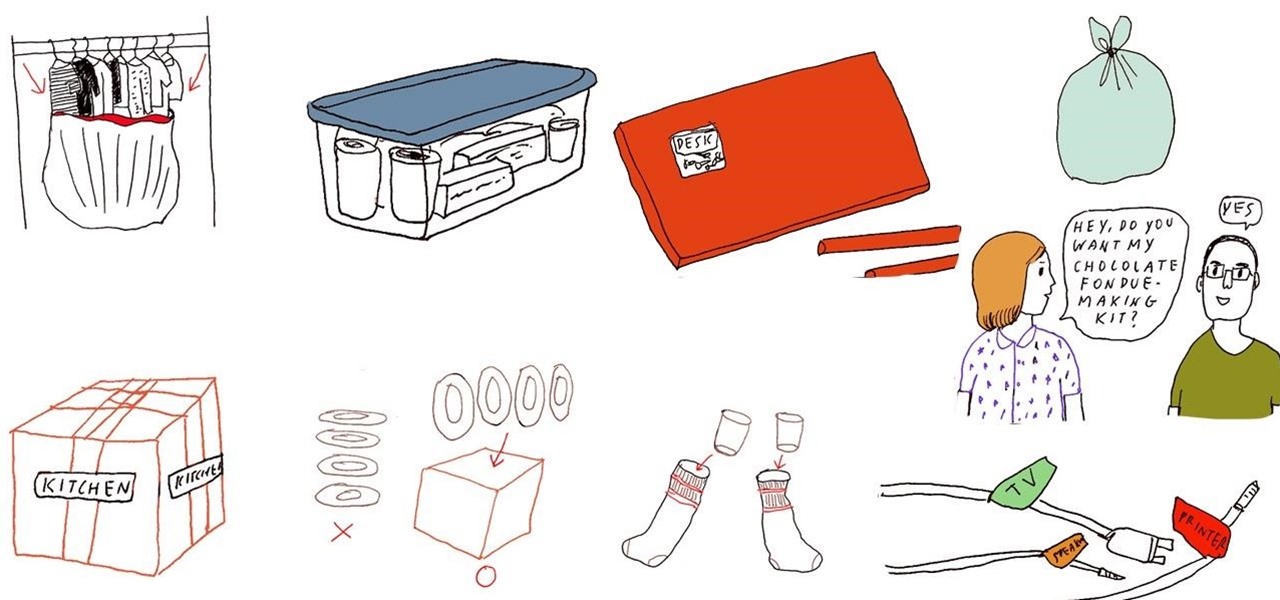
To decrease the possibility of breaking your glass dinner plates while moving into a new home, stack them vertically inside a box like vinyl records instead of horizontally like a stack of pancakes.
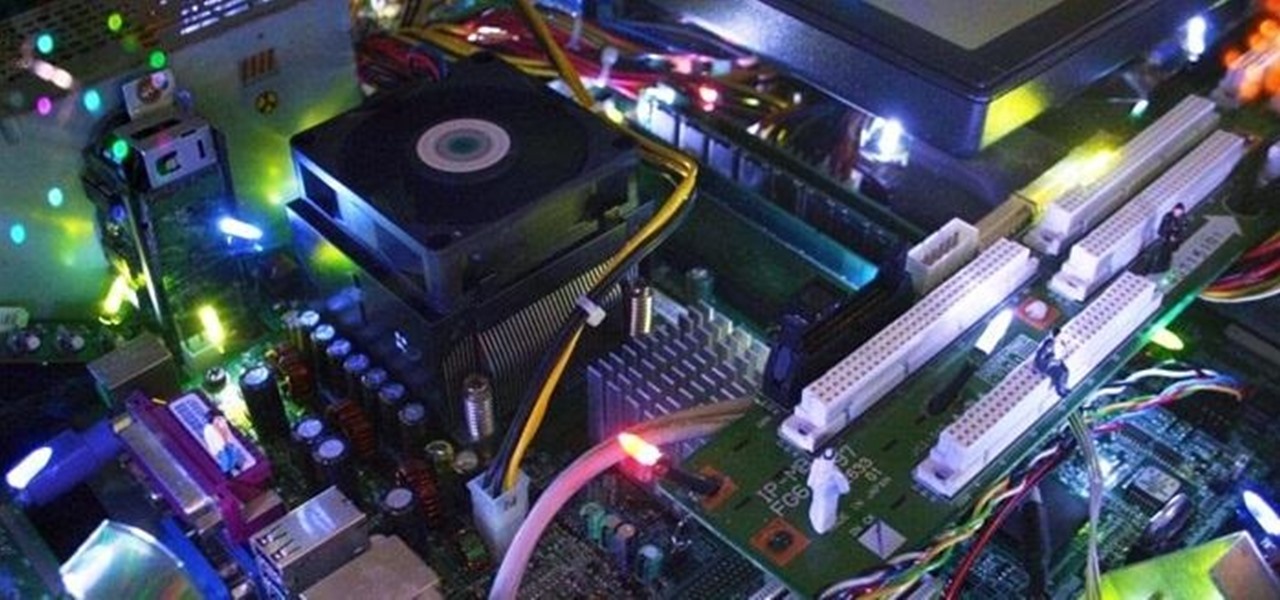
I have an interest in using recycled materials in sculptures, particularly circuit boards and other wasted electronic and mechanical components with which I put together sprawling cities lit with fairy lights. These cityscapes can conjure an image of a parallel society built from what we throw away. Utopian or dystopian, the ‘Electri-Cities’ remain a feast for the eyes and the mind. What makes them particularly intriguing is the population of tiny model railway people—they bring a host of nev...

Austrian composer Peter Ablinger has created a "speaking" piano. Ablinger digitized a child's voice reciting the Proclamation of the European Environmental Criminal Court to "play" on the piano via MIDI sequencer. Apparently, the computer is connected to the piano, which analyzes the human speech, and then converts it to key-tapping.

UGC beauty How-To video is a true YouTube phenomenon. Considering the internet's tendency toward the male bias, the complete domination of beauty in YouTube's How To & Style section is noteworthy.

If you've ever wondered how software pirates can take software and crack it time and time again, even with security in place, this small series is for you. Even with today's most advanced methods of defeating piracy in place, it is still relatively easy to crack almost any program in the world. This is mainly due to computer processes' ability to be completely manipulated by an assembly debugger. Using this, you can completely bypass the registration process by making it skip the application'...

Making a video game requires an incredible amount of work. It requires people skilled in many disciplines to work together for thousands of hours merging visual art, computer programming, game design, sound design, and music composition into a fun game. The Indie Stone is a Scottish indie development studio started, like so many others, by industry vets who were tired of corporate restrictions and wanted to make the crazy games they had always imagined.

Anybody who spends most of their day on the internet should know all about lulz. Lulz are most often jokes made at the expense of web users, as popularized on 4Chan. Today, a consortium of hackers called LulzSec is attempting (and in some cases succeeding) in efforts to shut down some of the games that offer web users a giant share of their online fun. World of Warcraft, League of Legends, EVE Online, and Bethesda Softworks have all been targeted by LulzSec's hacking efforts in the last week,...
In terms of internet, faster = better. We all want faster internet, but how exactly do you get a fast wireless connection? Believe it or not, the answer is quite simple.

This is the third part of my electromagnetic pulse series (see Part One and Part Two). By now, I've covered the hardware and general concept of electromagnetic pulse generators, but how exactly do they disable electronics? How can an invisible field of energy have such a catastrophic effect on computers, cell phones, and most any other electronics? I'll be answering all these questions in part three of Making Electromagnetic Weapons.

Though under a lot of the average consumer's radar, the CISPA is now making rounds again with a coalition of advocacy rights groups. The act, known as the Cyber Intelligence Sharing and Protection Act, forces companies to ignore existing privacy laws and share information with the Federal Government. This short article will bring you up to date on this bill. The CISPA is another bill 'designed' to help prevent thefts and prevent them in cyberspace. But again, like all the previous bill before...

Keyloggers are a must-have tool in your arsenal. Hardware keyloggers have the advantage of being undetectable through anti-virus or other protection programs. They also capture keystrokes before the OS even boots up, so they are pretty handy tools.

Electronic Arts (EA) and Hasbro have always been a little slow at adapting Scrabble for the cyber culture. They failed to beat Scrabulous to the Facebook market by a whole year, but managed to save face by targeting the mobile market, specifically iPhone and iPod touch, making Scrabble one of the very first mobile apps in the iTunes App Store.

Electronic Arts is the biggest game publisher in the world, and have been for years. And yet, their only successful internally developed games nowadays are the EA Sports mega-franchises like Madden. Most of their success has stemmed from their ability to buy other companies on their way up, squeeze the creativity out of them, and then sell them to someone else or just let them go. This week they made their largest acquisition ever when they purchased PopCap Games for $750 million upfront—as m...

One of the creepiest musical instruments ever is undoubtedly the theremin, a device originating from the early 20s that emits eerie sounds with a just a wave of the hand. If you've seen the original movie The Day the Earth Stood Still, you know what I mean—freakishly creepy. Playing the theremin can be off-putting for some, since it's a relatively pricy gizmo, but a new geek gadget called the EaTheremin aims to make all of us professional, dinnertime theremists.

Type: Digital, Theme Theme: Kid of the Year

Type: Digital, Theme Theme: Cutest Daddy
Type: Digital, Landscapes Theme: Incredible Landscapes, "Beyond the Mundane"
Type: Digital, avian Theme: Bird portraits, "The Avian Persona", wild or in captivity
Running this World has prompted me to think about MTG on a deeper level than I ever have before. In attempts to contextualize it, explain it, research it, and understand the parts of it that I don't yet understand, I have come to an unexpected conclusion: I'm old.

Everybody loves Oprah Winfrey. Maybe it's because of her philanthropy. Maybe it's her onscreen personality. Maybe it's the fact that it was a rags to riches story. Or maybe it's because she likes SCRABBLE...

Yes, they are May numbers, NPD is late by a month due to "IT" problems. They might have well blamed it only oil spill crisis.

So, you scratched up your $500 Adobe CD and now it's unreadable. You could go buy a new one, but you already purchased it! Searching The Pirate Bay and downloading some Adobe software can usually be easy enough, but what should you watch out for?

Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. As governments move to close their long fingers around the free speech that exposes their secrets, this shadowy collective of loose-knit, but like-minded individuals are hell bent on preventing them. Or are they?

WonderHowTo is made up niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

In this article, I'll show you how to make a high-powered, long-range, air-powered rocket gun. This launcher is based on a sprinkler valve, a modified propane tank, and a few other components. Though not hard to make, this device is VERY dangerous! The rocket can seriously harm, if not kill any living thing it's shot at. Here's a video of it in action, quite an accurate shot by my friend Chris... Parts