An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

Because timing is everything, the latest entry in the location-based augmented reality gaming sweepstakes, Ghostbusters World, has arrived just in time for Halloween.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

I've had a few days to live with the Magic Leap One, and it's time to finally weigh in with some thoughts as someone who has been tracking this company from the beginning, for almost five years now.

During its presentation at Unite Berlin, Magic Leap gave attendees a crash course in developing experiences for Magic Leap One (ML1), we found out quite a bit more about how the device works and what we can expect to experience with the device.

Continuing our series on building a dynamic user interface for the HoloLens, this guide will show how to rotate the objects that we already created and moved and scaled in previous lessons.

Every industry has its own jargon, acronyms, initializations, and terminology that serve as shorthand to make communication more efficient among veteran members of that particular space. But while handy for insiders, those same terms can often create a learning curve for novices entering a particular field. The same holds true for the augmented reality (also known as "AR") business.

Now that we have unlocked the menu movement — which is working very smoothly — we now have to get to work on the gaze manager, but first, we have to make a course correction.

I think I hate this game. I don't really see how you can play more than 15 minutes of Tap Mania without smashing your head into a wall. You do nothing but tap. Tap, tap, tap. At least they got the name right.

Last June, Meta began shipping their Meta 2 mixed reality headset, to the delight of many. In September, it was announced that shipping had been delayed until the end of the year. Then it appeared that Christmas would bring something magical when Meta sent out an email four days before the big holiday saying that the Meta 2 developers kits were finally shipping. Unfortunately, having a few on order here at Next Realit,y we are still patiently waiting for ours to arrive.

In the tech world, when you're a small startup going up against the Goliaths and their massive marketing budgets, you're forced to find and produce something almost magical to help your product stand apart from the rest. And that's exactly what Occipital Inc. has done with their Bridge headset.

When the HoloStudy Demo app for HoloLens came out in September, it was a pretty impressive start to what could be a very valuable science tool for education. Now, Moscow-based HoloGroup, makers of HoloStudy, started an Indiegogo campaign to improve their modular teaching app.

The sweet aroma of cooked fruit filling your kitchen is one of the trademark scents of summer. Yet attaining the perfect consistency for homemade jam can be difficult to master. Often it ends up a watery mess or over-solidifies into thick mystery goo that is destined for the trash, not topping your toast.

There's been a whole lot going on at this year's Consumer Electronics Show, from the latest in virtual reality gear to televisions that continue to slim down while producing higher quality images.

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

Mobile payment systems have been around for almost 5 years now, starting with Google Wallet. But when Apple got into the game last year with their new Apple Pay service, things really started to take off. Around this time, Samsung responded by acquiring an up-and-coming mobile payments company that owned the rights to an incredibly innovative technology called Magnetic Secure Transmission (MST).

It seems like whenever someone sees my phone, they ask me two questions right off the bat; "What phone is that?" and "How did you get your Android to look like that?"

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operates, I'd like to take this moment to explain the philosophy around the Linux operating system.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

You probably already know by now that a custom Android ROM can change your user experience and give you what feels like a new OS on your device, and there's no shortage of them out there to try out.

It may not be as large as the Samsung Galaxy Note 2, but the Galaxy S3's screen size is still big enough to make iPhone owners cry themselves to sleep. The 4.8-inch AMOLED display with 720 x 1280 pixels makes the GS3 a great mobile companion—and an even better portable gaming device.

"You can never know too much" is a saying you hear all the time. Funny thing is, I have no idea where it originated, and neither do most of the people who continually say it. Nevertheless, it's a statement that very few would argue with.

Shorts, learning from your audience and the fundamental plausibility of being hustled in the desert Mike Clattenburg, creator of Trailer Park Boys and Afghan Luke, was kind enough to talk to us from Nova Scotia, where he was hard at work in preproduction, about Crackin’ Down Hard, his short that screens Monday and Tuesday as part of TIFF’s Short Cuts Canada Programme. We picked his brain about realism versus surrealism in comedy, the virtue of shorts, and the virtue of turning negative skinny...

The iPhone doesn't stop at last year's excellent iPhone 12 lineup. Apple's been developing its iPhone 13 models for a while now, and there are a lot of rumors already with eight or nine months still to go until a release. This year, we're expecting four new models with similar sizes and features to 2020's offerings. If you want to know what makes the 2021 iPhones so different, we've got answers.

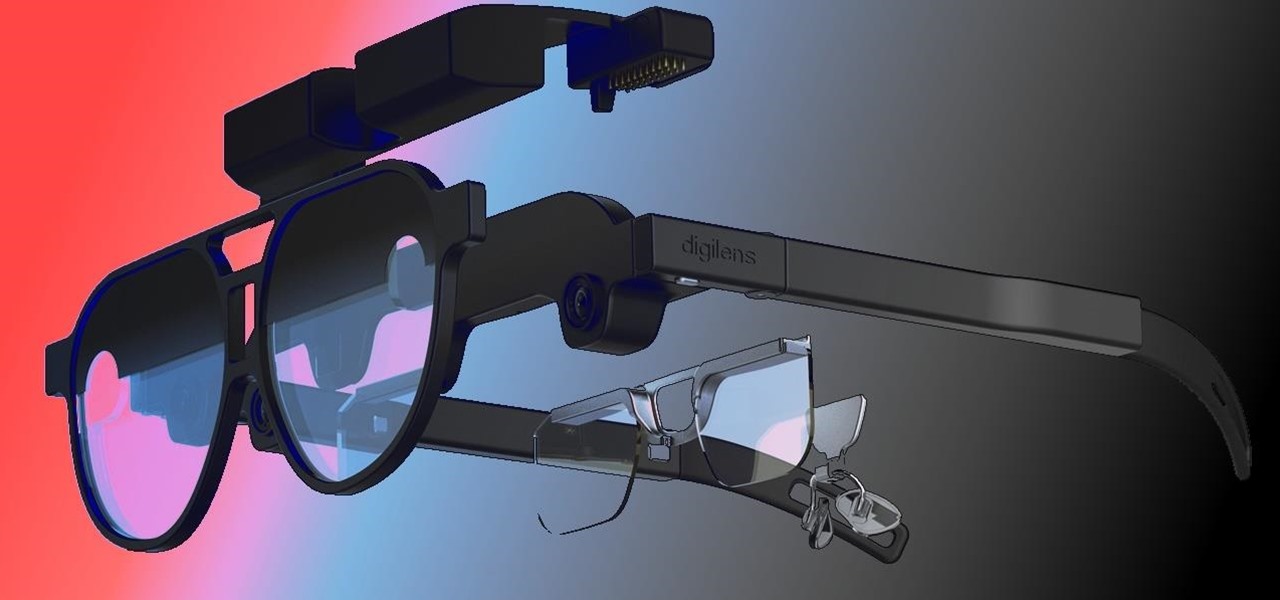
When it comes to the future of AR smartglasses, DigiLens has one word for you. Just one word. Are you listening? Plastics.

One fight for augmented reality branding that we thought had been settled has suddenly turned into a full-fledged legal battle—again.

QR codes are so handy. Nowadays, all you have to do to scan one is open your phone's camera app and tap a button. But creating one is a different story — online QR code generators aren't always trustworthy, and most phones don't have a built-in feature for it. Thankfully, Google Chrome now does.

Next year, fans of Mario Kart will be able to experience the game in real life with the assistance of augmented reality.

Despite the fact that over 600,000 Snap Lens filters have been created since Lens Studio debuted in 2017, and Facebook is reporting that more than a billion users have interacted with its Spark AR filters across Facebook properties, social augmented reality filters get a bad rap in the AR industry.

There's something extremely satisfying about hunting down your online adversaries and knocking them out with a well-placed shot, which probably explains why shooting games are still one some of the most popular time killers for iOS and Android.

My autistic son loves music. One afternoon, when he was nine, I downloaded GarageBand to his iPhone to help with the boredom of a long wait at a doctor's office. Instead of pacing or escalating into a meltdown, he spent the entire hour and a half practicing, learning, and composing. When we finally left that day, the rest of us exhausted and irritated, he shared his first composition with a big smile.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

If there's been one signature design element for Apple's iPhones, it was the circular Home button. It served as the "everything" button for each iPhone model until last year's iPhone X, but now, it's completely absent from the iPhone XS, XS Max, and XR. Should you be worried? Short answer: No.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

2017 was a down year for HTC. First, the U11 and U Ultra were widely criticized. Later, Google purchased a large chunk of HTC's manufacturing division, leaving the Taiwanese company running with a skeleton crew after losing 2,000 key employees. But that's not stopping HTC — their flagship U12+ was just announced, and it's quite impressive.

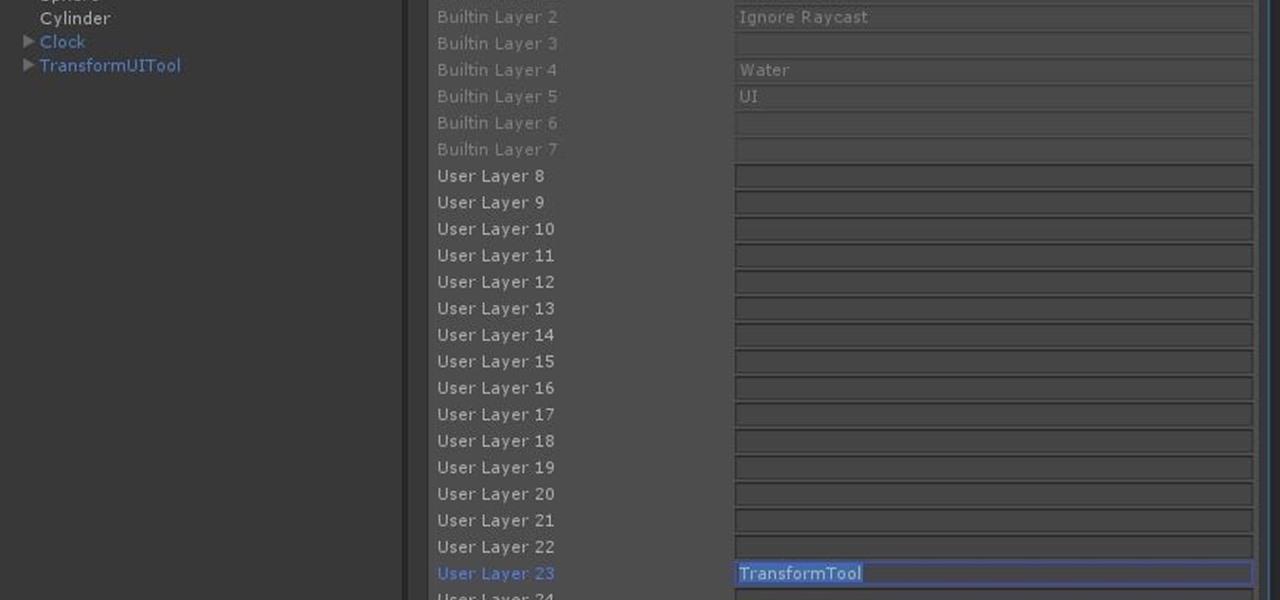
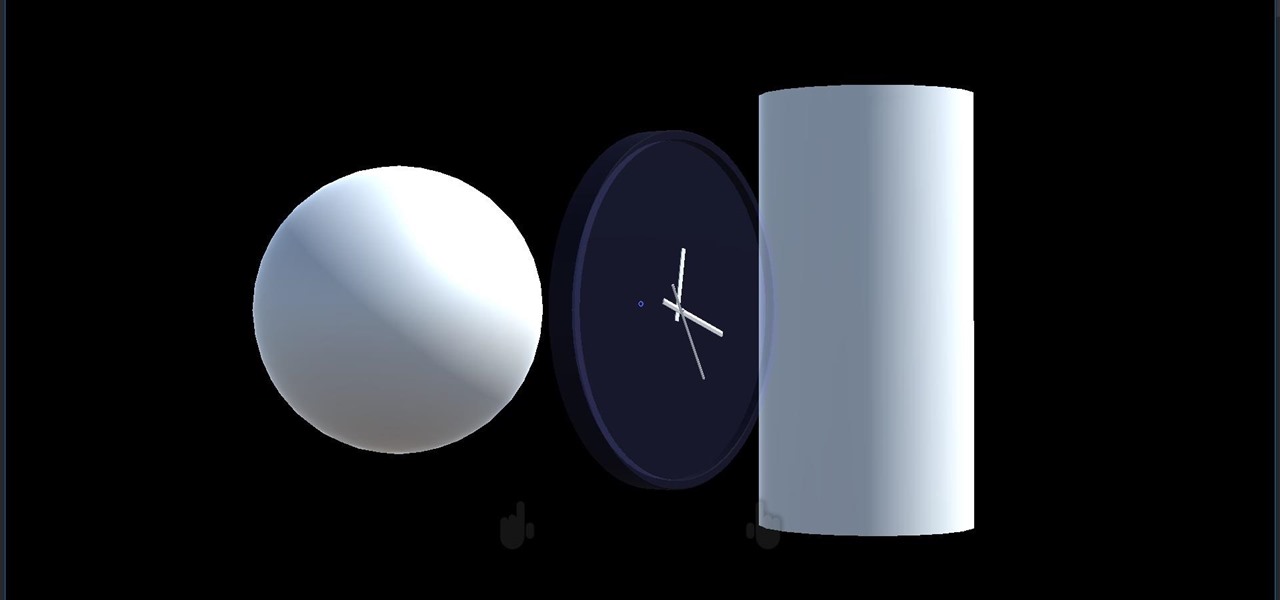
In this chapter, we want to start seeing some real progress in our dynamic user interface. To do that, we will have our newly crafted toolset from the previous chapter appear where we are looking when we are looking at an object. To accomplish this we will be using a very useful part of the C# language: delegates and events.

We started with our system manager in the previous lesson in our series on building dynamic user interfaces, but to get there, aside from the actual transform, rotation, and scaling objects, we need to make objects out of code in multiple ways, establish delegates and events, and use the surface of an object to inform our toolset placement.