Make delicious candy for Easter from the comfort of your kitchen with copycat versions of your favorite classics: Marshmallow Peeps, Cadbury Creme Eggs, Reese's Peanut Butter eggs, Almond Joy bars, and chocolate bunnies. The best part is that you get your sugar fix without the preservatives.

I'm starting to wonder if the people at Boston Dynamics have ever watched a Terminator movie. Not just because the robotics company with the oxymoronic name develops machines that are able to move around environments with animal- and human-like agility, but because the people testing them seem to take such joy in openly antagonizing their creations. It's one thing to tempt fate by creating superhuman robots that could potentially end mankind. You've reached a whole new level of hubris when yo...

Whatever you want to call it for now—Android Nutella, Android Nougat, or Android 7.0—the upcoming "N" release of Android will surely bring in tons of new features and functionality. We know it will be named after a dessert, and we know that Google uses an alphabetical naming system, so something starting with "N" is next in line after Android 6.0 Marshmallow.

Windows 10 has so many new features that we couldn't even cover them all with one article. From keyboard shortcuts to revamped search functions and all-new window gestures, Microsoft definitely piled on the fresh functionality in the latest version of their operating system.

So this is my methodology for this project of writing a rootkit. Please leave feedback on what is right/wrong. I tried to simplify concepts the best I could however...

Coffee mugs: nothing proliferates more quickly in my kitchen cabinets. People are always handing them out as gifts or as swag, plus I always seem to find a vintage model or two at a garage sale that I'm compelled to buy. I used to do a yearly purge of my excess muggage, but it turns out it's a good idea to hold on to one or two extras.

I've never had a black eye, but I was in a car accident that turned my entire ear dark purple a few years ago. Believe me; it was enough to get more than a few funny looks.

After an Instagram creator created a viral sensation last holiday season with the Which Disney camera effect, Disney followed it up with a Sponsored Lens playing a similar roulette with programming from Hulu.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

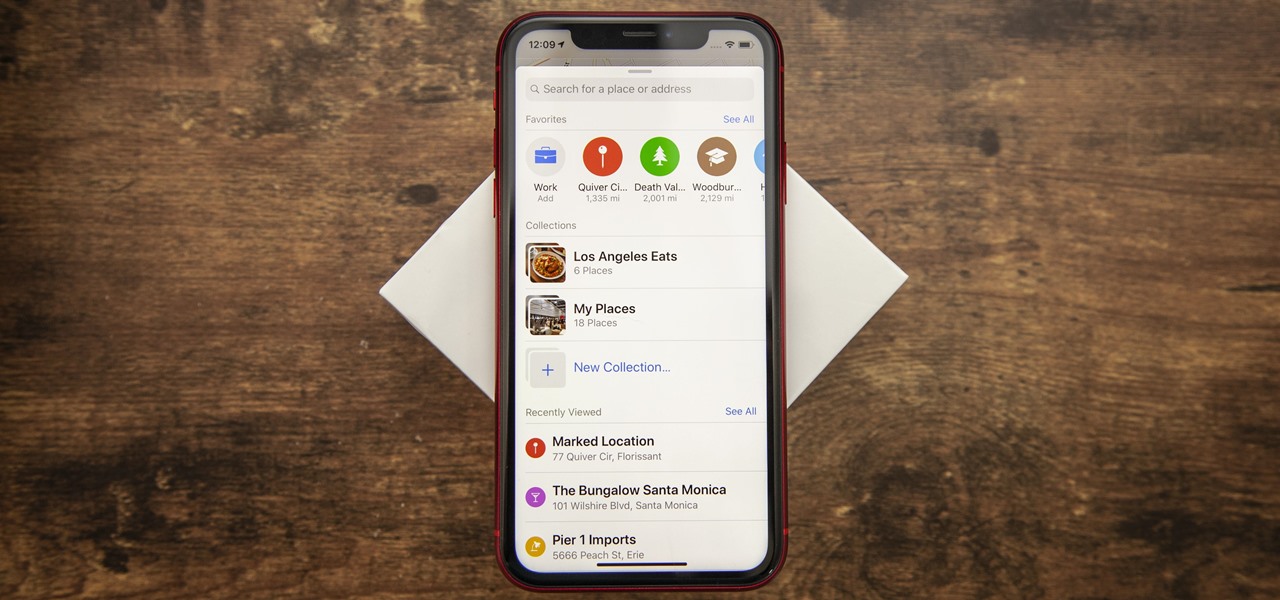
Apple Maps has had a rough lifecycle. After completely dropping the ball during its inception, Apple has been slowly improving its usability and feature set. After six and a half years, users still prefer third-party apps in iOS 12 over Apple Maps, with Google Maps stealing a large 67% market share. But iOS 13 for iPhone may finally close the gap.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

Aluminum foil is one of those things that every cook, experienced or just starting out, has in their kitchen. And while we may think we know how useful this handy material can be, there are hundreds of ways we could be utilizing tinfoil to make our lives a whole lot easier.

Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long as you know where to look.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

I noticed the neon yellow sign at the new location of Pho Bar in Chinatown right away. The sweeping cursive yellow letters spell out "Crazy Rich Broth"; the same phrase printed on the back of servers' shirts. It's the kind of minimalist but colorful design feature that is especially popular on Instagram at the moment — shots of patrons in front of a glowing sign.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Our smartphones are full of personally-identifiable information. So much of what we do with these devices is tracked and recorded to make our experience more streamlined and personalized. For many users, that's a fair trade — but for privacy-minded folks, it's a raw deal.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

The year was 1947. Scientists had isolated a virus from a pyrexial rhesus monkey in Uganda and named it after the forest where the monkey lived — Zika.

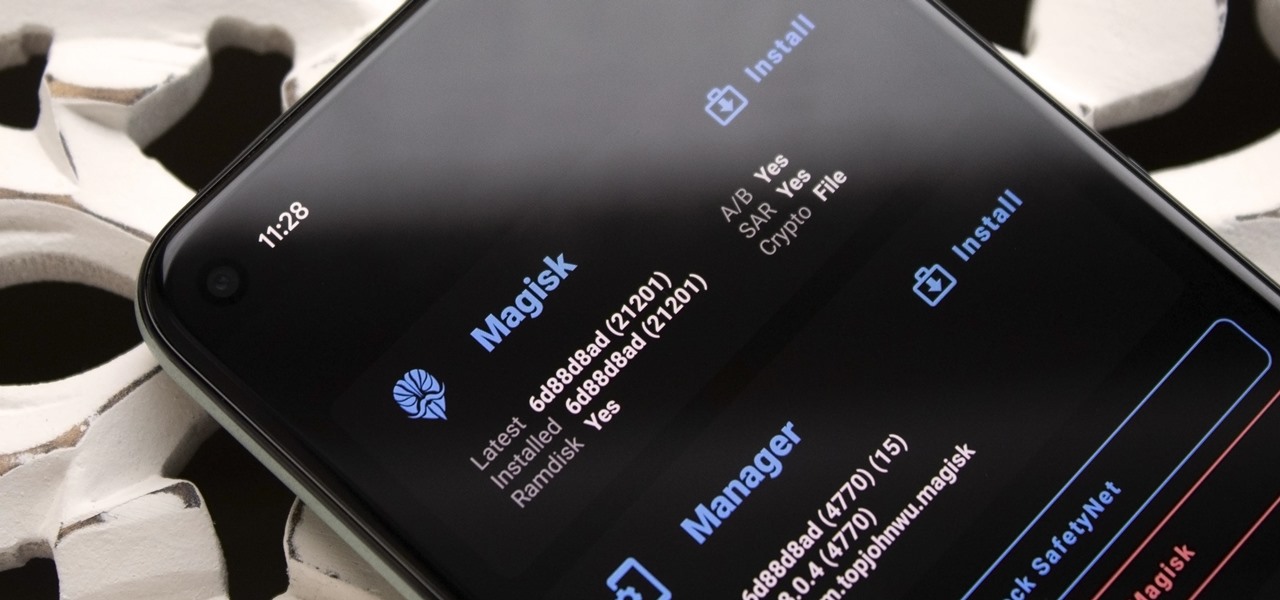
Okay, so you rooted your Android phone .... now what? There are a few ducks you need to get into a row, like backing up your stock boot image, getting SafetyNet sorted, and improving security with biometrics. But there are also awesome root mods waiting for you — just don't get ahead of yourself.

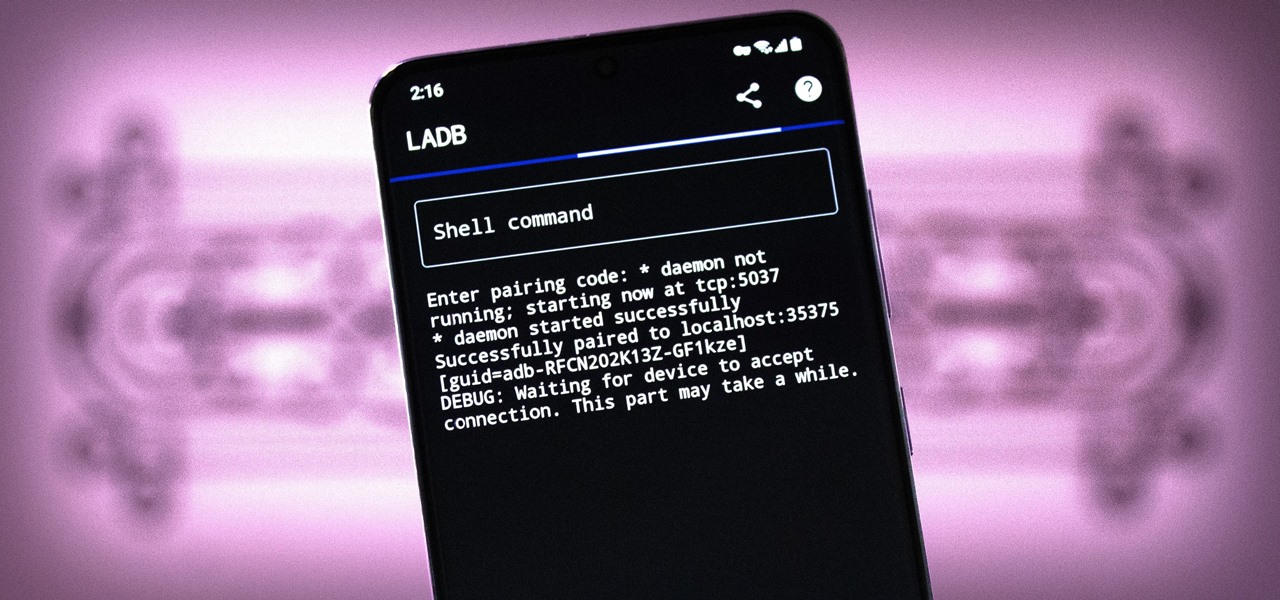
There are three tiers to Android customization: things you can do by default, things you can do with ADB, and things you can do with root. While root is still pretty tricky to get, ADB mods just got a lot easier.

After teasing the feature in Android 10, Google finally added proper native screen recording to Android 11. But when you start a capture, you'll see a small red indicator in your status bar as long as recording is ongoing, which can really distract from your video. Thankfully, it can be removed with a little ingenuity.

Windows 10 and macOS have poor reputations when it comes to customer privacy and user policies. Our hacking Windows 10 and hacking macOS articles might make it seem like a reasonably secure operating system doesn't exist. But I'm here to tell you that there is a viable alternative that could provide some sense of security and trust.

Privilege escalation is the technique used to exploit certain flaws to obtain elevated permissions relative to the current user. There are a vast number of methods out there to go from user to root on Linux, and keeping track of them all can be difficult. This is where automation comes into play, and a privilege escalation script called Linux Smart Enumeration is one to take advantage of.

A rather exciting development has recently surfaced in the jailbreaking scene for iPhone. The Checkm8 bootrom exploit was shown off to the public by axi0mX, which made way for the undefeatable Checkra1n jailbreak tool. With it, you can freely jailbreak a variety of older iPhone models without any restrictions. The success rate is quite high, too, when compared to other jailbreak methods.

Apple has finally given Control Center the love that it needs with an updated interface design and more customizations than ever before. Taking the more customizable overhaul one step further, iOS 18 and iPadOS 18 have elevated controls beyond Control Center, so you can use controls from other places on your iPhone or iPad for even faster access to your most-used shortcuts.

The new iPhone 12 Pro Max is equipped with MagSafe, the iPhone 12 lineup's most talked-about feature. While Apple previously used MagSafe for its magnetic charging connectors on older MacBook models, it's given new life to it on the iPhone, and in a much better way. But can it do for you exactly?

Apple's iOS 13 has been available for beta testing since June, and the stable release pushed out to everyone on Thursday, Sept. 19. To help you make the most out of iOS 13 for iPhone, we've rounded up everything you'll want to know, whether a colossal feature, small settings change, interface update, or hidden improvement.

Data can be injected into images quickly without the use of metadata tools. Attackers may use this knowledge to exfiltrate sensitive information from a MacBook by sending the pictures to ordinary file-sharing websites.

With smartphone cameras and software getting better and better every year, more and more users are getting passionate about photography. So when you're shopping for a gift to get someone, if they have a smartphone, chances are they'll more than appreciate some tools and accessories for taking better photos with their pocket friend — and we've got some gear ideas they'll love.

In this video, we learn how to perform corrective stretching to help knee pain. Perform these stretches on each leg for 1-5 minutes each. The first exercise you can do is with a step or a slightly elevated item. First, elevate your toe and stay on the heel, then bed at your hips and squeeze the quad of the front leg. Bend down so your arms touch the ground, remembering not to bend your knees. Next, place a mat on the floor and kneel onto it, placing your foot on a chair that's behind you. Hav...

This pool shooting video shows a way to use a cue ball that is frozen against the rail to hit the object ball directly into the opposite corner pocket without scratching. Hit with a high left English with an elevated cue, to deflect the cue ball off the rail just enough to hit the object ball into the corner pocket. Make a kick shot when the cue ball is frozen to a rail.

Are your exterior lamps looking totally out of place? Bring them back into the fold with a simple spray paint face lift. As every fashion-conscious gal knows, accessories make all the difference. The same is true for your house: the decorative touches, accent pieces, and color schemes can make the difference between a house that looks all together or altogether tacky. Exterior lights are a perfect example: do your lamps match your home like the perfect pair of earrings match your outfit? If n...

I took this photo standing on some bleachers at Berlin’s Hamburger Bahnhof Museum for Contemporary Art. Artist Carsten Höller’s “SOMA” installation consisted of live reindeer milling around, canaries in cages, and mice in mazes. It was trippy (the concept for the piece does include hallucinogenic reindeer urine), over-conceptualized, and super fun. The craziest thing was an elevated bed at the end of the walkway, in which patrons of the museum could spend the night (upon winning a raffle tick...

If you've yet to witness B.A.S.E. jumping, it's an activity for adrenaline junkies first publicized by filmmaker Carl Boenish in '78. The freefall sport employs ram-air parachutes, and is most commonly executed in locations such as the highly elevated El Capitan rock formation of Yosemite National Park (El Capitan is also technically the birthplace of the sport).

As a kid, my favorite thing to do at the Natural History museum was a midday stop, when my family strolled past an antiquated looking vending machine in the museum's musty basement. The Mold-A-Rama machine was oddly shaped, George Jetson-esque, and spewed out made-to-order, brightly colored plastic dinosaurs. There was such joy in watching the liquid wax pour into the mold, and then eject a warm, custom toy—well worth the dollar or two demanded. A version of this tradition was recently elevat...

The ball exchange is a fairly simple exercise that can be used to work the core muscles. It should be noted that this exercise requires extensive use of the hip flexors. These muscles reside on the uppermost part of the thigh, and are activated whenever the legs are elevated off the ground from a supine (on your back) position. Supine leg elevation can put a strain on the lumbar spine. Thus, the ball exchange is not recommended for those with lower back issues.