Unquestionably, one of the best parts of Hanukkah is the prevalence of latkes during the 8-day celebration. But even the most dedicated spud fanatic can get a little "latke'd out" as the week drags on. Here are some alternative preparations for latkes that will give you some variety in your celebratory food choices throughout the Hanukkah season.

Sadness won over the worried world with her downtrodden, mopey attitude in Inside Out, the widely popular animated film from Pixar and Disney. She's relatable, helping us to connect with all of our bouts of tears, sour attitudes, and blue feelings—and this Halloween, you can embody Sadness with this easy DIY makeup tutorial via Rotoscopers.

You know that sinking feeling you get when know you've just done the unthinkable? It's the worst. Sending that ridiculous text message to the wrong number or posting a shameful tweet during a weekend bender.

There is nothing more irritating than having a nice jam session interrupted by an ad selling B vitamins, and that's exactly what Spotify does to you if you don't pay up.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

A team of academics from three different universities and two private companies have just discovered a new vulnerability that affects almost every Android device since 2012. The vulnerability is known as RAMpage, and it could be used to gain complete control over the device.

Action Launcher has some exclusive features that add real value to your overall experience. One such feature is Shutters, and like with most aspects of Android, there's a workaround that will let you enjoy this functionality on other launchers.

About a third of the methane released into the environment comes from the production and transport of natural gas. The gas leaks as it moves along the transport chain from gas wellheads to market.

Imagine walking up to enter a live event — but instead of pulling out a physical or mobile ticket to get admitted — you pull out your smartphone which lets out an ultrasonic sound tailored for you that lets you into the event.

Termite poop and biofuels — what's the connection? New research into termites' intestinal comings and goings describes a process that may speed the development and lower the cost of fuels made from plant matter.

A young child becomes very thirsty very often and seems tired all the time. A visit to the pediatrician determines she has type 1 diabetes. The onset of type 1 diabetes may seem sudden, and it can be, but the disease may actually have been triggered by common childhood viruses years earlier.

Vegetables are perhaps the most important part of our diets, but often times they're an absolute pain to prepare. Cleaning every fleck of dirt off of dozens of leafy greens takes ages, and eliminating the more fibrous parts of certain veggies can be extremely tedious.

Be it happy hour, a Super Bowl party, or just a gathering of friends, buffalo wings are a universal favorite. Since they're usually prepared for large groups, there is always a mix of both those that aren't counting their calories and others who are.

Nothing makes my stomach growl and my mouth water quite like the smell of roasting chicken. It's a pretty universal reaction, too—there's a reason every grocery store places its rotisserie grills and delis near the entrance, after all.

The fridge is the heart of the kitchen; take it away, and the whole operation falls apart. Yet, despite this, the fridge is also one of the most overlooked appliances in any kitchen. Most people organize their drawers and shelves for maximum efficiency, while many others buy islands simply to make their culinary playground more space efficient. Heck, I know some people who have passed up on otherwise great apartments because the counter space simply wasn't large enough.

No one ever wants to experience pain, whether it's as small as a stubbed toe or as great as recovering from surgery. Yet so much of our lives causes pain, lasting or brief in its form. With a few mental tricks and unusual home remedies, you can relieve some of the most common aches and ailments that arise painlessly.

There are many, many home remedies out there for relieving itchy mosquito bites. Everything from mud to banana peels and basil leaves to Alka-Seltzer tablets can help curb the itch. But before you even have to resort to any of those methods, you should be thinking about prevention. Wearing white clothing can help to keep mosquitoes aways from your skin, and there are many plants that will help mask your mosquito-attracting smell. But there's even more ways to keep those bloodsucking bugs away.

The Problem If you are working on a car restoration project, then you are going to faced with rust damage. This problem can’t be overlooked, as the entire project depends on repairing and eliminating rust. This would be like laying down new carpet to a house that was flooded, without cleaning the mess and making necessary repairs before laying the carpet down. The problem will still be there and the new carpet will be ruined.

I have always favored a neat and tidy Home Screen on my iPhone, and one of the best ways to achieve that is by removing all the app, folder, and widget names. With a few workarounds, you can do this on iOS 17, but Apple finally just gave us an official feature on iOS 18 to hide app, folder, and widget names on the Home Screen. And it also works for iPad on iPadOS 18.

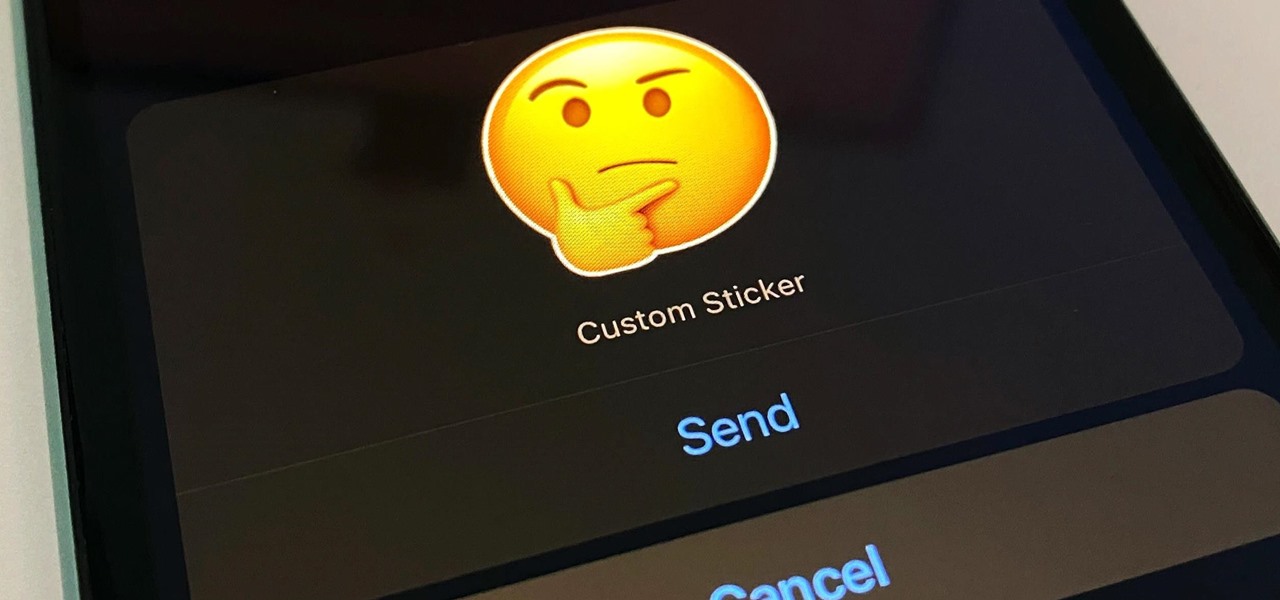
WhatsApp has a new sticker-making tool in the iPhone app that lets you create custom stickers directly in chats using your own images, eliminating the need to rely on third-party apps to make them.

Apple just rolled out the of iOS 14.5 to developers and beta testers, and one of the headlining features is the ability to keep your iPhone unlocked when your Apple Watch is nearby. As these things tend to go, Android has actually had this same feature for years, though it isn't quite as polished.

The virtual collaboration tool known as Spatial has consistently been one of our favorites due to its ability to leverage high-end augmented reality headsets to more easily facilitate remote meetings.

Despite some early and optimistic predictions that the world would have returned to normal by now, the surprisingly stubborn and resilient coronavirus continues to upend and alter how we live our lives when it comes to working from home instead of the office.

When filtered through the prism of the top stories of the year, the business of augmented reality 2019 was defined as much by epic failures of AR startups as it was by the promising developments that propelled the industry forward into 2020.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

For those with small hands, smartphones have gotten out of control as of late. Nearly every flagship phone is over six inches in length, so many are forced to use phones that are too big for them and hope they don't fall. Well, thanks to one developer, using these phones can be a lot easier.

Huawei has been in a losing battle with the US government for around ten years, with the last year being the spike of Huawei's problems. Because of US pushback against some Chinese-based smartphone manufacturers due to security concerns, Huawei is hoping to limit its dependency on US-based companies, and recent rumors of Huawei's very own mobile operating system may be the first step.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

With over 1 billion downloads on the Play Store alone, Google Maps has become a staple for those traveling. Its popularity is the result of Google consistently improving its accuracy and adding new functionality. And this was only achieved with help of you — specifically, your data.

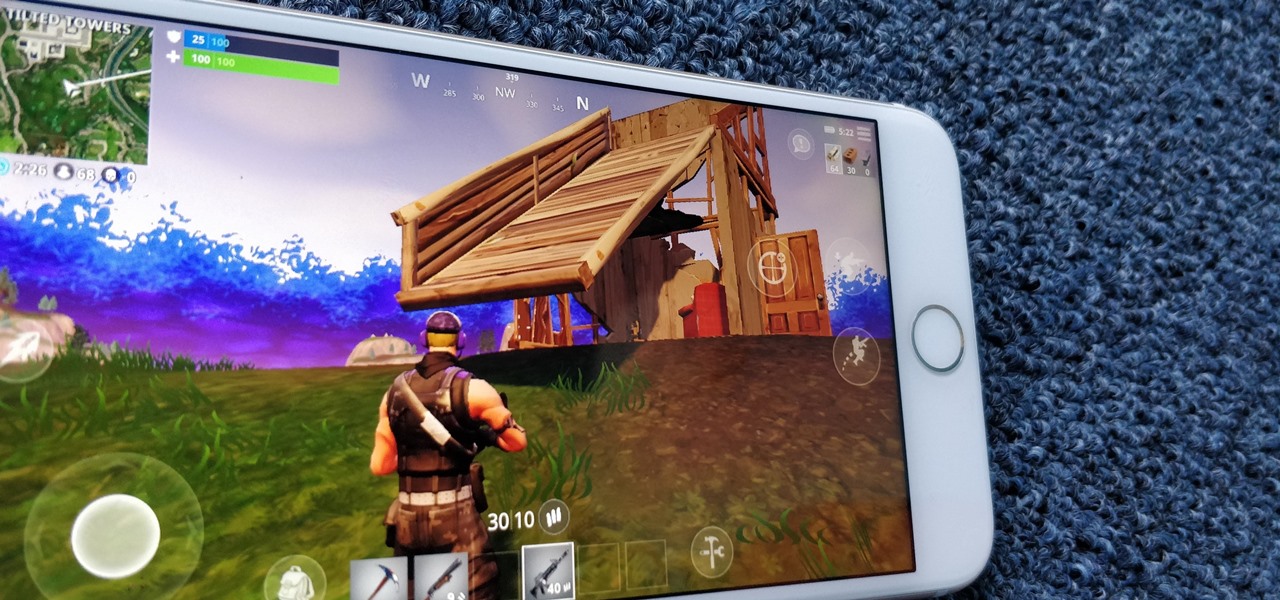
One of the more unique aspects of Fortnite Battle Royale is the ability to create structures. Using in-game materials, players can create walls and ramps for cover and to extend mobility. But creating isn't limited to just the basic generic structures. To really maximize their benefits, great players edit their creations to fit their needs.

If you need a tiny, flexible attack platform for raining down human-interface-device (HID) attacks on unattended computers, the USB Rubber Ducky is the most popular tool for the job. By loading the Ducky with custom firmware, you can design new attacks to be effective against even air-gapped computers without internet access. Today, you'll learn to write a payload to make "involuntary backups" through copying a targeted folder to the Ducky's USB mass storage.

Old habits die hard. It may be a cliché, but it's undeniably true, especially when it comes to the bad ones. Nail-biting, fidgeting, and overspending can label you as someone who is obsessive-compulsive, overly nervous, and routinely stressed out, but you can make the break less painful with a few simple tweaks to your routine and by understanding how your habits work.

What is gluten, why do some people think it is pure culinary evil, and why are there more and more products devoted to being free of this mysterious substance? Here's what one person thinks: What Is Gluten Really?

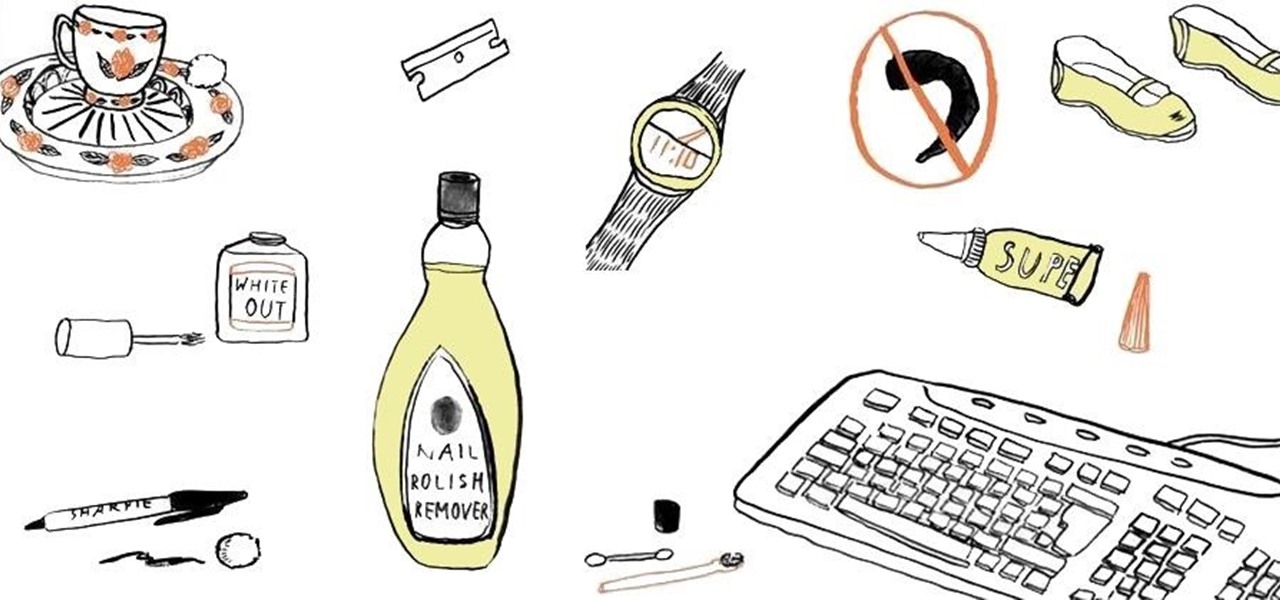
Acetone-based nail polish remover is great for removing nail polish, and it's also great for some DIY uses around the home. From eliminating scratches to fixing the consistency of correction fluid, its uses are varied but all effective. With nail polish remover, you can also clean your computer keyboard, get rid of ink stains, and even remove leeches from your skin. Talk about versatile!

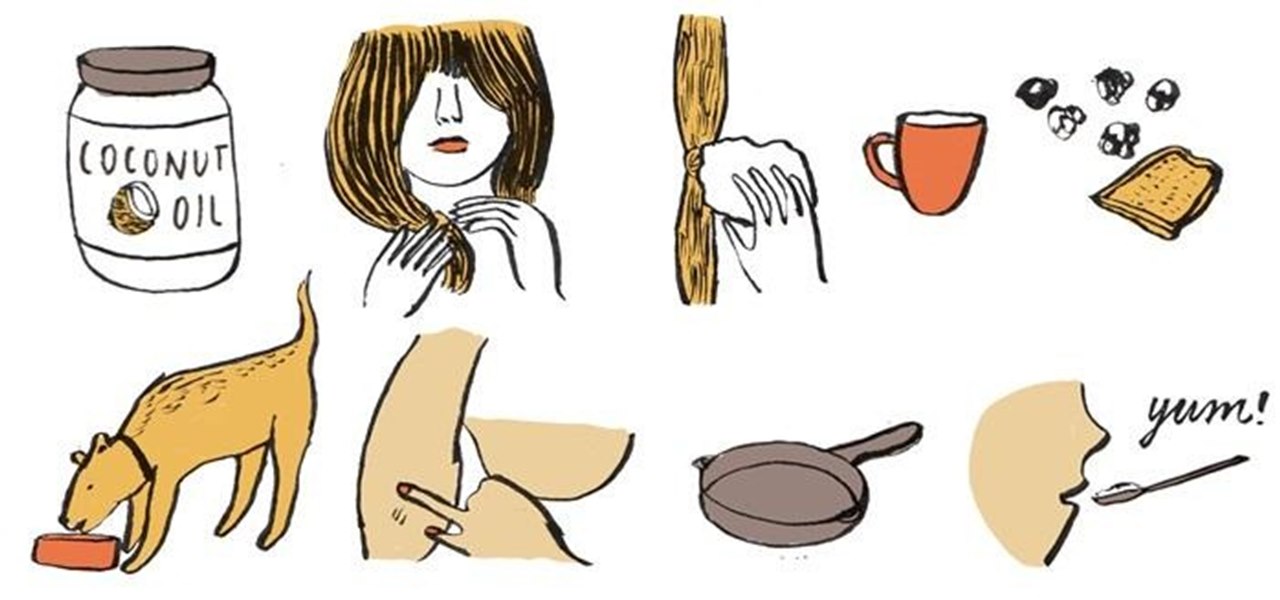
What can't coconut oil do? This edible oil, extracted from the copra or meat of a coconut, has done what most other food, beauty, and health trends have not: demonstrated real lasting power. Indeed, the "superfood" continues to make headlines, with its many uses the subject of debate, study, and fervent support. From the obvious (cooking) to the less so (home improvement), there are likely many coconut oil uses you're not yet aware of.

Despite the fact that over 600,000 Snap Lens filters have been created since Lens Studio debuted in 2017, and Facebook is reporting that more than a billion users have interacted with its Spark AR filters across Facebook properties, social augmented reality filters get a bad rap in the AR industry.

If you're looking for your gaming fix and nothing on the App Store is piquing your interest, you should give soft-launched games a try. These are games that haven't been released in the US yet because they're getting tested in smaller markets first. Using a simple workaround, you can install them on your iPhone in any country.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

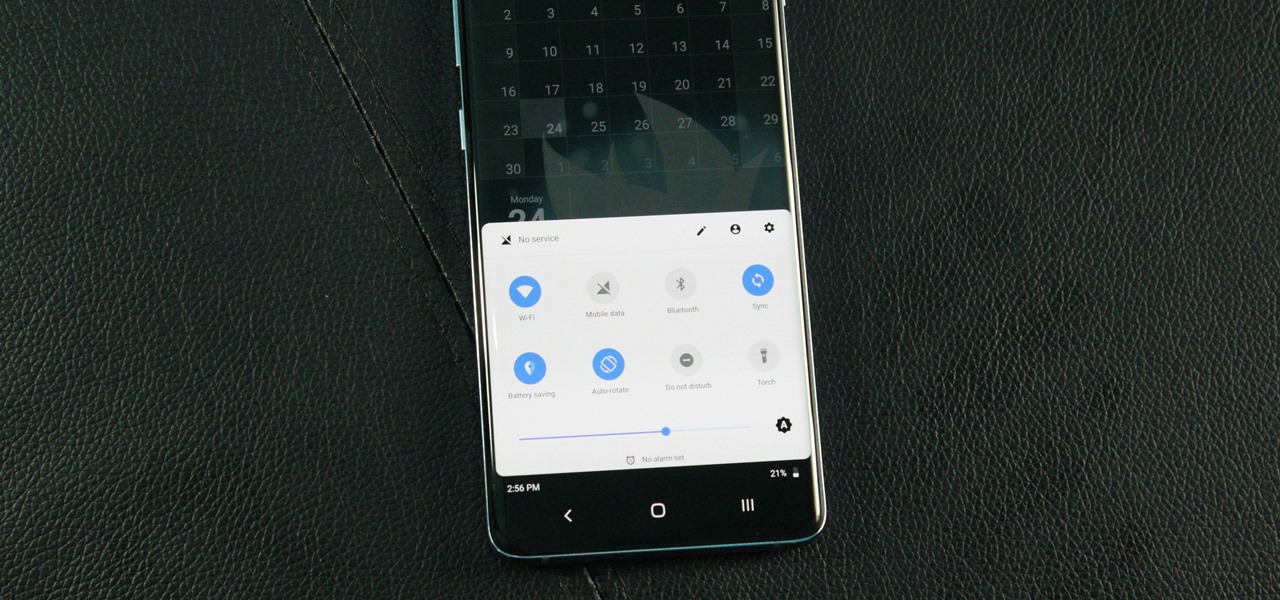
The Galaxy S8 has finally touched down, and it's an absolutely gorgeous device. Samsung's brand new flagship comes jam-packed with new features — some refined, and some that aren't. Luckily, we've compiled some major features to help you get started as quickly as possible so you can go about the rest of your day and show off your shiny new S8 to friends and coworkers.