Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.
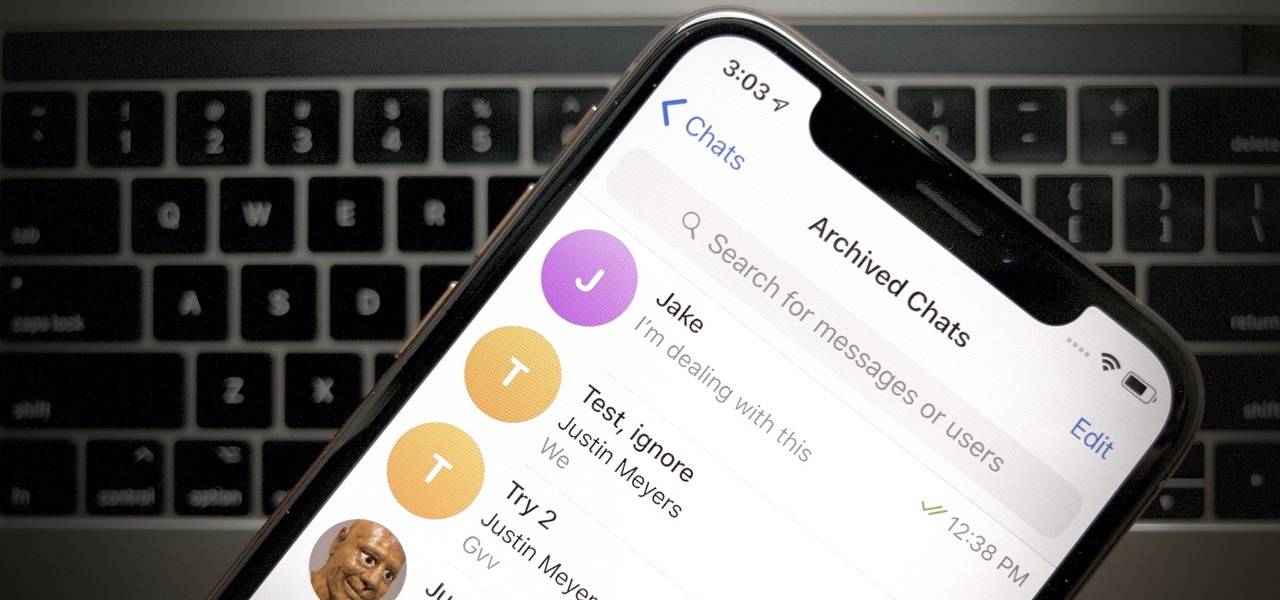
In Telegram — as with all instant-messaging apps — threads and conversations can pile up quickly. But you don't need to stare at all of your open chats on the main screen of the Android and iOS app. Instead, you can archive any conversation you like, keeping your main chats view relevant to your day-to-day communications without needing to delete any for good.

Streaming movies and TV shows on phones is more popular today than ever, but what about when you're on a plane, have a limited data plan, or will be in a no-service area? You'll want to download your movies and TV shows instead. While Netflix is excellent, you can't rent or download most of the latest movies and TV series. What you need is an app that lets you do just that.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

As augmented reality becomes more and more integrated into the mainstream, people have been wondering the future of AR is going to look like. Jay Samit has a pretty clear idea.

Puzzle games are a great way to kill time and exercise your brain in one fell swoop. They challenge you to think strategically and plan ahead, whether that's to create killer chain combinations for maximum points, or to plain old keep from getting killed.

Typing on a mobile device has come a long way since the days of flip phones. Today, there are awesome keyboard apps like Gboard, which integrates Google search features and makes typing a breeze. But the whole experience still stands to improve if you take some time to learn a few useful tips.

Whether you're riding the subway on your way home from work, or stuck in the backseat of the car on a long road trip, there are times when you need to entertain yourself without a mobile data connection. A good mobile game would pass the time perfectly, but not every game works without an internet connection.

Hi everyone. Recently I've been studying some topics about Assembly, memory and exploitation, and thought I could write something nice, easy and fast about it, just because I like to share what I learn, and probably sharing what you learn and trying to explain it to a stranger is the best way to learn it better. It worked for me, and I hope it will be useful for you too.

April Fool's Day, aka National Screw with Your Friends Day, is finally here. You can always pull a conventional prank, like strategically placing a whoopee cushion on your mom's chair, but that joke has been exhausted generations before smartphones were around. We live in a day and age where smack cam is the new level of pranking, so it's time to step your game up, novices.

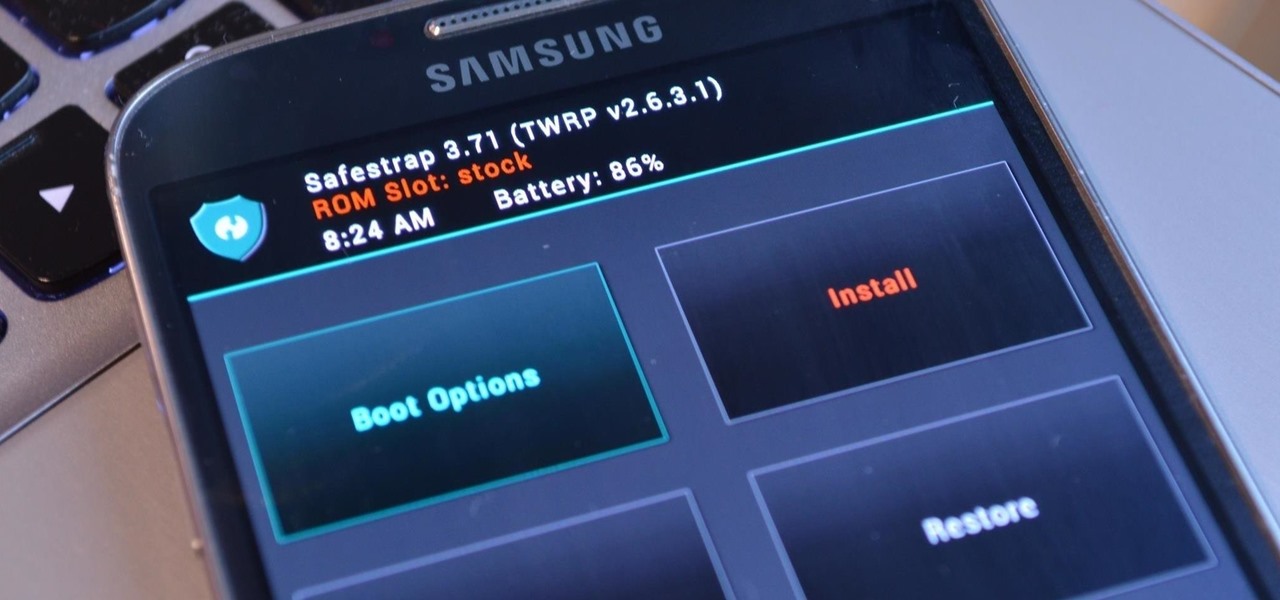
Third-party ROMs like CyanogenMod are the ultimate form of customization for softModders. Hard-working developers offer us alternate Android experiences to replace our often bloatware-riddled stock ROMs.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

If you don't work in construction or are a woodworking master, you probably aren't entirely sure what all those marks are on a tape measure. Sure, you likely know the basics, like there are 12 inches to a foot, but what are all those little tick marks for? Don't let all those little lines dissuade you from using a tape measure. Follow these guidelines to help you read all those little ruler marks.

Drawing is easy for some, harder for others, but drawing letters is pretty simple for both the pro and novice artist. There's all kind of text styles you could conjure up, and they don't have to be boring fonts. Fire up your imagination to create different styles for drawing numbers and letters of the alphabet, adding individuality and pizzazz to names, messages, greeting cards and decorated items.

Pastry Chef Anne Heap demonstrates how to use a pastry bag, as well as techniques for decorating cupcakes. Frosting a cake or cupcakes with a pastry bag is much easier than using a knife. The bags come with many different styles of tips. Just choose the tip you want to use, fill the bag with frosting, squeeze to apply the frosting, pull up and let go.

You have your gift and a card and now all you need that special cake for mom on Mother’s Day. You’ve tried other cakes now try a hat cake. This festive and spring inspired hat cake is sure to make this year’s Mother’s Day a memorable one.

You don’t need a camera to recreate a picture you see. Choose and object and with only a pen and pencil you can recreate that object as a sketch. Take your time, and choose somewhere quite where you can focus on your creation.

You can learn to deal with the thing we all dread, a computer crash. Hopefully you diligently back up work but even if that's not case, stay calm. There is still hope and even if you're not a wiz at computers there are people out there who can help.

Bennett's fracture takes place at the base of the thumb. It typically occurs when an individual falls on an outstretch hand. The force is directed this way; the fracture occurs here. Learn how to diagnose and treat a Bennett's fracture in this medical how-to video.

A dislocated shoulder involves movement of the ball of the humerus away from the ball and socket joint. Ninety-five percent of the time, it will come out anteriorly when an individual's arm is forcefully pushed backwards and rotated in such a way that the ligaments in the front of their shoulder tear and the ball will pop out the front of the shoulder. This is a very common injury seen in contact sports. Learn how to diagnose and treat a dislocated shoulder in this medical how-to video.

Singing runs can add your own special style to a song. Get tips and techniques for preparation, rehearsing, and singing runs from a professional singer in this free voice lesson video series.

Our chef will walk you through this recipe step-by-step, with special consideration for preparing the oysters, including instructions on how to clean and shuck them. Also get an ingredient list, learn how to prepare the vegetables, create the sauce, and bring it all together. Also get a quick recipe for an oyster stew.

In this instructional video series, our expert will show you the basics of Afro-Cuban dance by teaching basic steps, giving pointers on special moves and techniques as well as history on the origins of Afro-Cuban dance and the music and musical instruments that accompany it.

In this series of expert video clips, learn more about the theremin. Our expert goes into detail about what makes up the complicated workings of the theremin including the coils and other components. Get a full history on the musical instrument and learn about the many uses of a theremin. What makes a theremin sound so special? Get answers to this question and many more in our expert instructional videos.

This recipe has a lot of steps, so you may want to save it for a special occasion dinner, but it still sounds delicious! Follow along with this video series and see how to make pork chops with carmelized onions and smoked gouda.

DarkStar One: Broken Alliance is an updated version of the space flight simulation video game DarkStar One (2006), and was made exclusively for the Xbox 360. It features updated graphics and presentation, making it the perfect space flight game for you wannabe astronauts.

Seventeen years ago, Apple released iPhone, the first mainstream consumer phone with a touchscreen as its main typing input method. Apple has been perfecting its onscreen keyboard for almost two decades, and it's built with some fantastic features that make typing faster and easier. But it's easy to overlook some of these features, so here are some tips and tricks you need to be using if you aren't already.

Losing pictures is a uniquely frustrating experience. You take pictures to remember something, to capture a moment so you can look at it again later. So when you lose the thing that's supposed to be what's keeping your memories safe, it's unfortunate and infuriating. Photo Backup Stick® Universal will keep your pictures safe. Right now, you can get this awesome backup tool for $53.99.

Did you know there is a simple trick to making beautiful, professional charts? Whether for your work or for making running your own business easier, Edraw Project Software will make all your projects simple. Right now, a Perpetual License, which includes three-year upgrades and maintenance, is on sale for almost half off, at just $89.99 — that's a 49% discount off the regular price of $179.

Whether you want to build your own website for your business, start your new lucrative career in web development, or gain a wealth of projects to add to your portfolio, this course will help you do it. And right now, "The Complete Web Developer Course" is on sale for just $14.99 — a staggering 92% discount off the regular price of $199.

5G is undoubtedly the future of mobile networks, and there's a good chance your next phone will have it. But just like with 4G, as carriers race to get the best 5G coverage, the ones running behind are abusing marketing terms to make themselves seem further ahead than they actually are.

I recently picked up a Pixel Slate when Google had a deal going on. I'd been in the market for an Android tablet since the Nexus 7, and this was the closest thing to it. Unfortunately, I soon learned Chrome OS and Android aren't as integrated as I had hoped.

Google recently released a new mesh router known as Nest Wifi. The updated and rebranded Google Wifi brought many improvements, such as faster processing power and an increased level of wireless security called WPA3. But while it's not enabled by default, you can still get the new WPA3 security on your original Google Wifi.

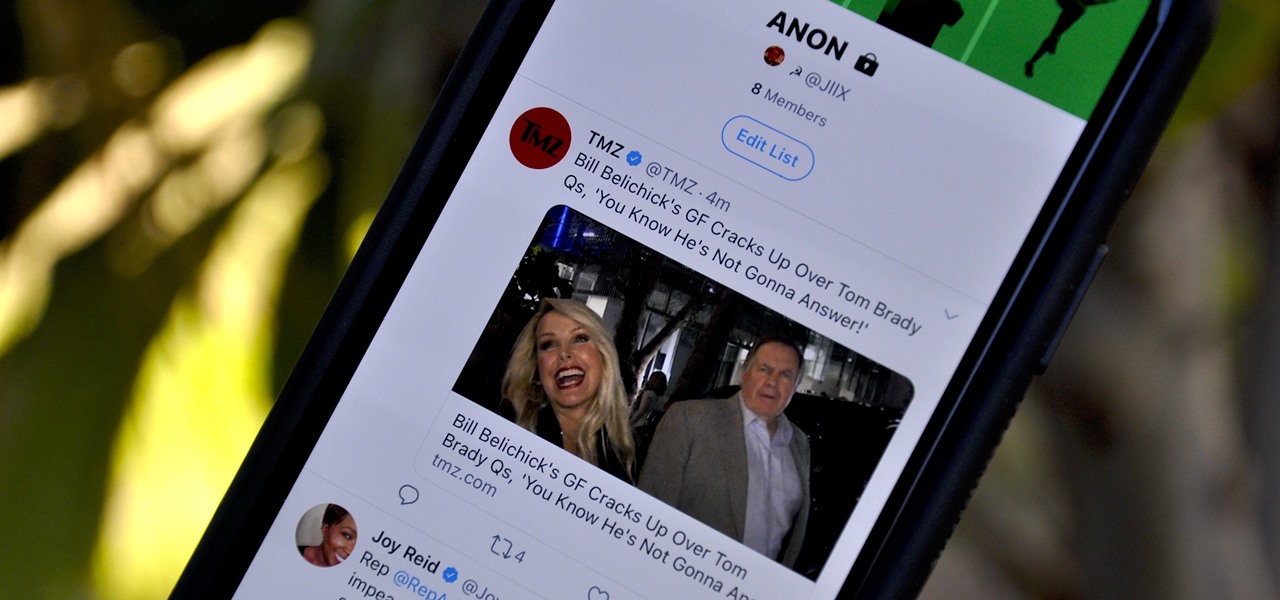
Following someone on Twitter is an investment. You virtually agree to have their opinions, tirades, and hot takes spewed across your timeline. It can get annoying real quick if they're known to post controversial comments periodically. However, there are other ways to stay updated on someone's tweets without you having to hit the follow button and go all in.

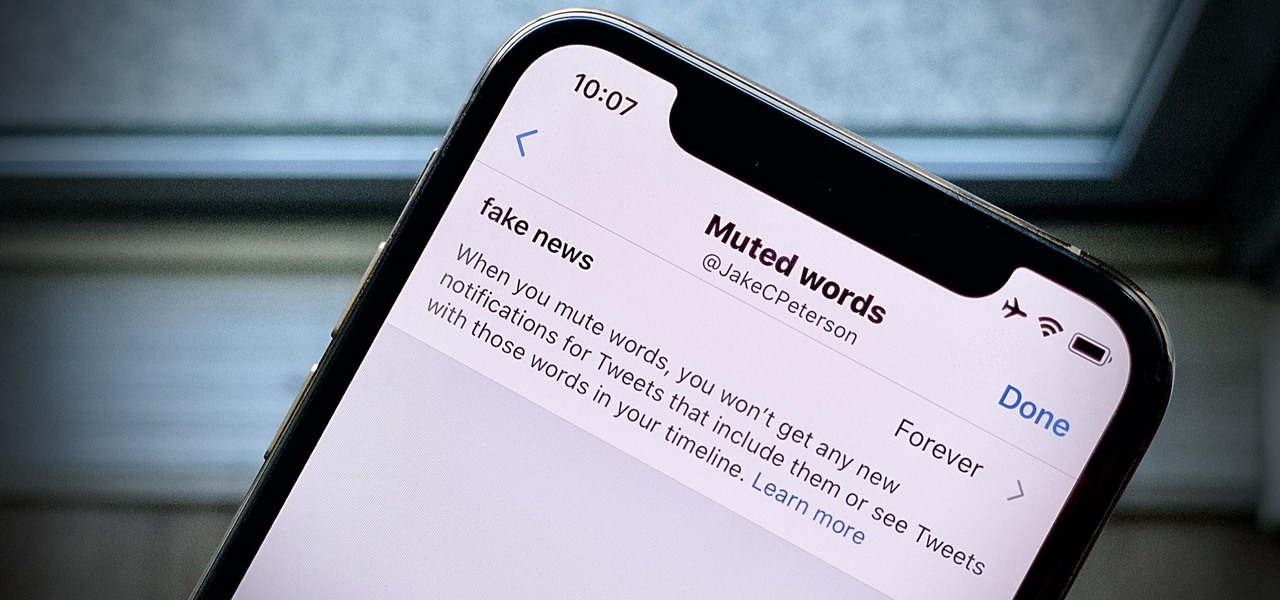
Twitter can be a wonderful place for people to express their emotions and chat with each other in brief. However, it can also be a breeding ground for hateful comments, foul language, and a whole lot of political talk.

If you don't want to be found on Twitter, there are several ways to do that without making your account private. For instance, you can choose an obscure username, omit your real name, or pick a random avatar. But there are lesser-known features deep in your settings that can also protect your privacy online, including preventing photo tags.