In this how-to video, you will learn how to send a fax for free with your computer. First, go to the website MyFax. You will see a screen with forms to fill. Fill out the appropriate information, such as your name and who you are sending it to. You can also enter an external message with the fax. You can then upload the file you want to fax onto the form. Once this is done, enter the email addresses of the people whom you will be sending the fax to. Once this is all filled out, click on the b...
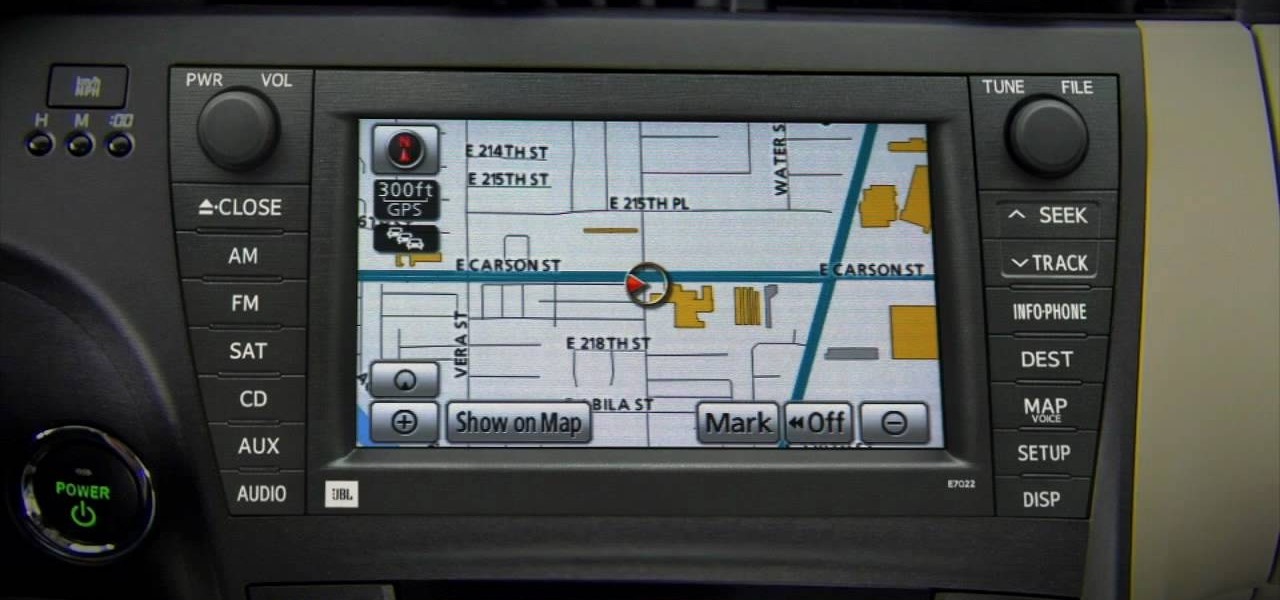
Learn how to use the navigation system in a new 2010 Toyota Prius in simple steps. It has DVD based navigation system with easy to use touch screen display. All the navigation routes of USA, Hawaii and parts of Canada are available in it supporting English, French and Spanish languages. When you start the car it opens the map and you can input the destination using voice command or entering text. You can also input your home address and five other special location address.

This video will show you how to find your own IP address in Windows Vista, which is more difficult and confusing to use than Windows XP was. First, you should go down to the bottom right hand corner and find an icon of two computers, which is your network connection button. Click on the Networks and Sharing selection and find the section which says "View status". After clicking on this, you will find a section which will be labeled "IPv4". The numbers which are indicated after this are the nu...
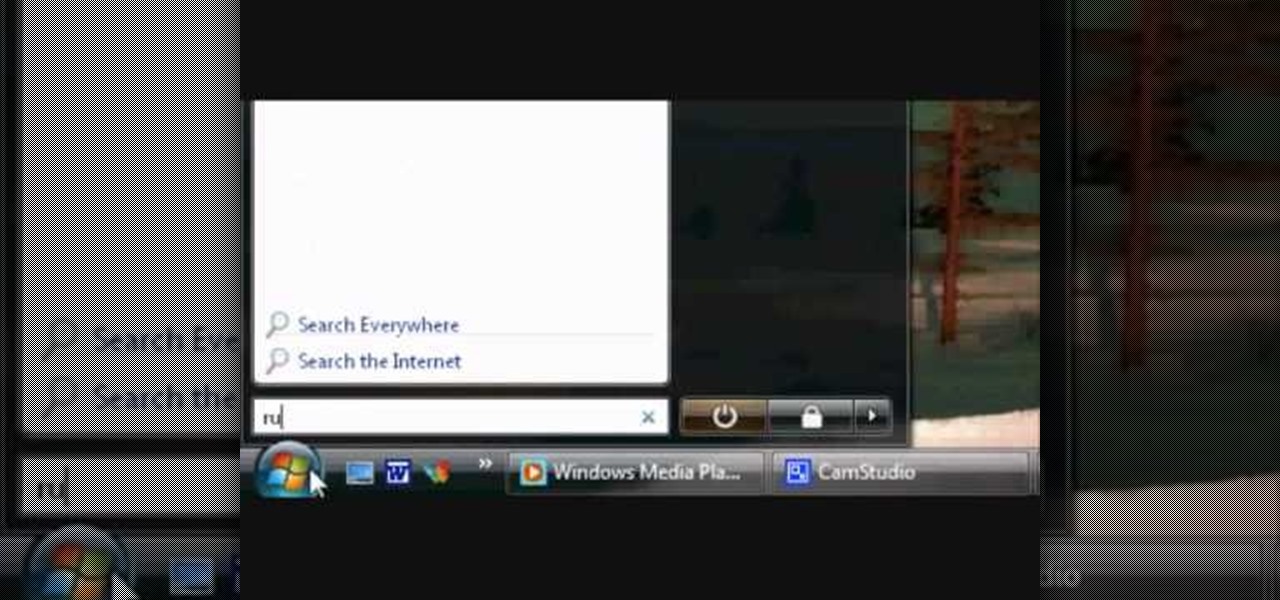
This walk-through video tutorial shows you how to find out your IP address for XBox live. First press the start button and search for run as shown, click the result, bring up the dialog and type in the given command to open the command prompt window. Type the command in the given window and hit enter. The number that appears is your IP address, use it as the key for XBox Live. In the case of XBox 360, it automatically detects it.
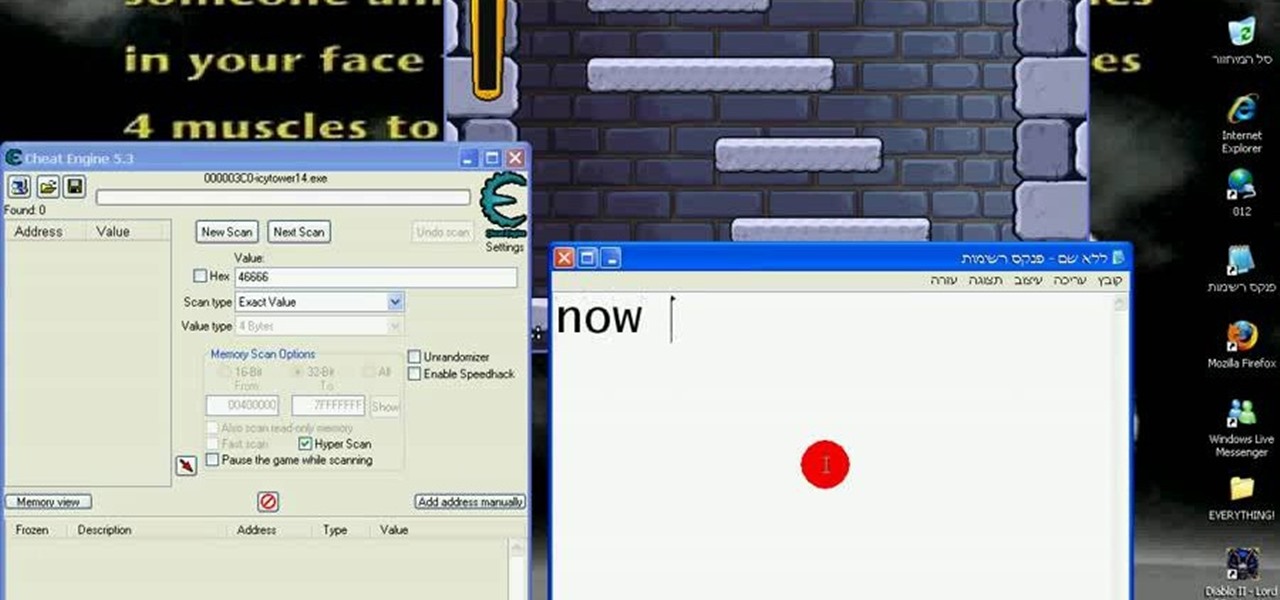
The cold time of Christmas is upon us, and Icy Town is a winter-ific game you can play… and hack. With Cheat Engine and a little patience, you can hack and unlock floors in the game easily.
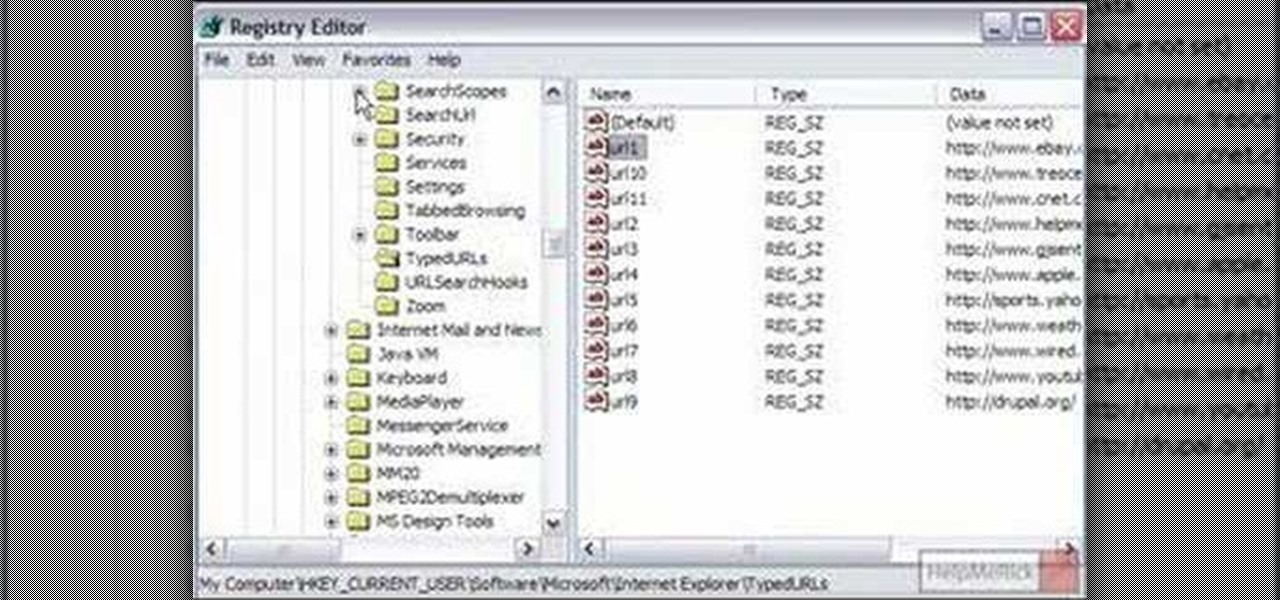
Ever wondered how to go about deleting individual entries from the Internet Explorer address bar? While it's possible, it's not particularly easy. You can do it all at once by purging your entire history through Internet Options or you can hack your Windows registry. For more information, or to try this hack for yourself, take a look!

Don't lose your friends' numbers; save them to the address book. Watch this iPhone tutorial video to learn how to save numbers in your iPhone's address book. This how-to video is intended for new iPhone owners.

Male instructor explains how to create new contacts in the BlackBerry 8700 mobile device. Going to the BlackBerry's address book, it is a matter of entering in all the information for a new contact to be created. Step-by-step process makes it very easy to understand and complete the contact.

For spreadsheets that require contact information, you can grab that information from your address book when you are working in Numbers '08. This tutorial shows you how it's done.

Pages '08 allows you to access the information in your address book and add it to your documents. This is helpful if you are printing envelopes or writing letters.

You may not always want to, but there will probably be a time when you'll want to know if an email you send — like a job application or a support request — is opened by the recipient. It's actually easy to implement, and you may be using an email client on your device right now that supports email tracking.

There has been drag-and-drop functionality for iPhone since at least iOS 11, but iOS 15 adds a new ability that makes essential emails even easier to find when you need them.

Your sensitive personal data should be strongly protected, and it's never more vulnerable than when you are online. The internet connection is a prime avenue of exposure, and email is one of the least secure forms of communication. Fortunately, there is an easy solution to both of those problems.

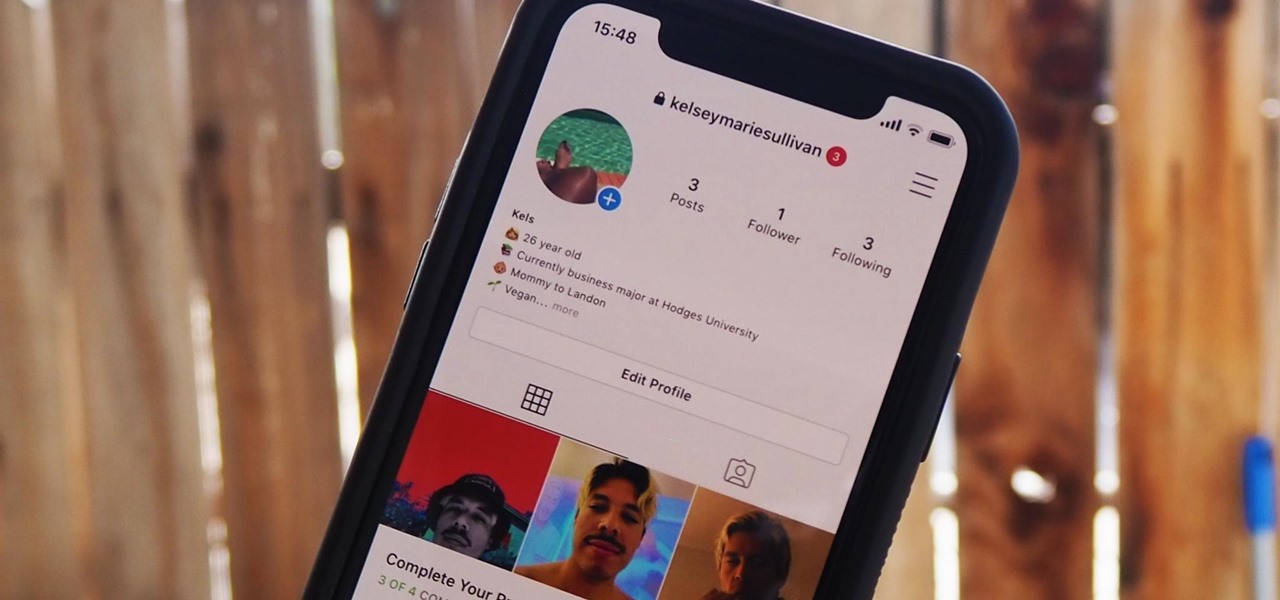
Everything you post on social media lives there forever — even if you delete it. Just ask anyone that's ever posted something stupid. Instagram does not provide built-in tools to save or download images and videos from other users, but there are workarounds. Third-party tools make saving other people's photos and videos easy, and there are always screenshots.

There's something about alcohol that compels you to contact people. Most of the time, the drunken calls or messages you send out will have you cringing hard tomorrow morning. But if you have a jailbroken iPhone, you can help prevent this potential embarrassment with a free tweak.

Are you here yet? When will you arrive? How long until you get here? How far are you? Hurry up! When you're meeting up with someone or a group of people, you may get flooded with messages like that. Instead of trying to answer them mid-trip, you can send them your status from Apple Maps, so they know precisely when you'll arrive, and they'll even get updates if traffic is holding you back.

While iOS 12 is arguably the best iteration of Apple's mobile operating system yet, one major fault so far is security. On Sept. 26, Videosdebarraquito discovered a passcode bypass that gave access to contacts and photos from the lock screen. Apple has since patched that security flaw, but Videosdebarraquito has discovered a new one that affects all iPhones running iOS 12.1 and 12.1.1 beta.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

While the Mail app didn't get as much love from Apple in the iOS 11 update as Maps, Photos, Safari, Siri, Camera, Messages, Notes, and the App Store did, there are still a few new features you need to know about when emailing on your iPhone.

Greetings comrades! Great leader has ordered that we gain intel on a website owned by the opposition. For all general purposes we will be scanning nmap.org because they really don't care if Big Brother decides to perform a whois on their IP. We will be using Dmitry for the scanning.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Hello fellow grey hat hackers, as hackers it becomes necessary for us to be able to send emails anonymously. Whether for whistle blowing or pranks or social engineering or whatever, it just is necessary for us to do that.

A group ironically called the "Guardians of Peace" hacked into Sony Pictures' computer systems and released a mountain of internal information such as medical records, leaked scripts, work complaints, and even celebrity aliases.

Metro apps are pretty nice, but they absolutely suck on a Windows desktop with a mouse and keyboard. That's to be expected though, since Metro (also known as Modern UI or Microsoft design language) was created mainly with touch input in mind for Surface Pros and Windows Phones.

When browsing the web, you may not be quite as anonymous as you think, especially if you are using public WiFi. The easiest way to stay as anonymous and safe as you are going to get, is to use a VPN (there are a number of great free ones). In this tutorial, we will show you how to set up a VPN on Android, and how this protects you.

In a era where cyber security is becoming increasingly important, Comcast has decided to use its customers' routers to provide hotspot access to the public. A new program, outlined by Dwight Silverman over on the Houston Chronicle website, seeks to provide Xfinity customers with city-wide Wi-Fi hotspots by using, well...other customers' wireless routers.

Google is widely renowned for its mastery in using data to tailor specific search results and ads. Their Android and iOS search apps put this ability to use in finding the most relevant pages for your query, and their desktop site is the most-used search engine on the web as a result of it.

Privacy features have become quite the hot commodity, emerging from the aftermath of the NSA scandals that rocked the United States this past year. While the NSA has the means to gather information on all of us (regardless of any security software we implement), it doesn't mean that they're the only ones looking.

Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.

When the 6.1 version of iOS was released back in February, complaints of severe battery drainage for iPhone, iPad, and iPod touch users exploded onto every Apple-related forum on the Internet. Everyone was either losing a percentage every three or so minutes, or their battery only lasted half as long as it did before the update. Earlier this month, Apple released iOS version 6.1.3, to supposedly fix a recent exploit that allowed anyone to bypass the lock screen—but as it turns out, the update...

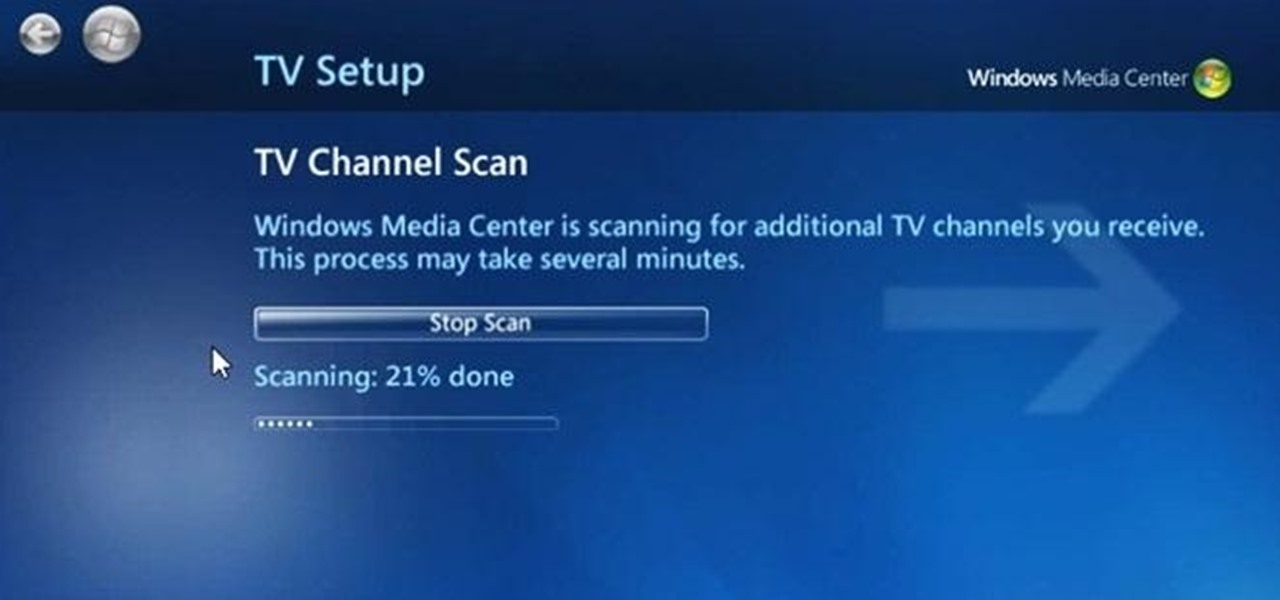
Can't play your DVD movies on your brand new Windows 8 system? That's because Microsoft decided to omit Windows Media Center from Windows 8 this time, instead making it available as an extra download—and it's not free anymore. At least, it won't be next year.

The convenience of storing things on the cloud can definitely make life easier, but if you're storing sensitive files, it could be a total disaster if anyone hacked your account. Some encryption services can be expensive, but if you just need it for personal use, there are some really great ones that don't cost anything. Here are three programs that let you encrypt your cloud storage for free. BoxCryptor

Hello, today I will tell you about how you can create a page through wordpress. this is a performance for those who have scarcely been touched wordpress. This guide will put you through basis and create a user and a website among millions of people.

This video tutorial shows how to open a port for torrent downloading on your computer. Click Start menu, type cmd command in Search area. In cmd window type ipconfig and press Enter. Remember or write down your IP adress. Type exit and press Enter to close cmd window.

This video shows you how to control your computer from your iPod touch. 1. Go to UVNC. Click on Installation. This will take you to download options. Download the latest stable version. 2. Install Hamachi, which helps you find your computer's IP address. Click on Download Here link, fill in the registration information, and click submit. 3. Install a VNC listener on your iPod so it can connect to your desktop. Jailbreak your iPod, and open the installer. Click All Programs; scroll down until ...

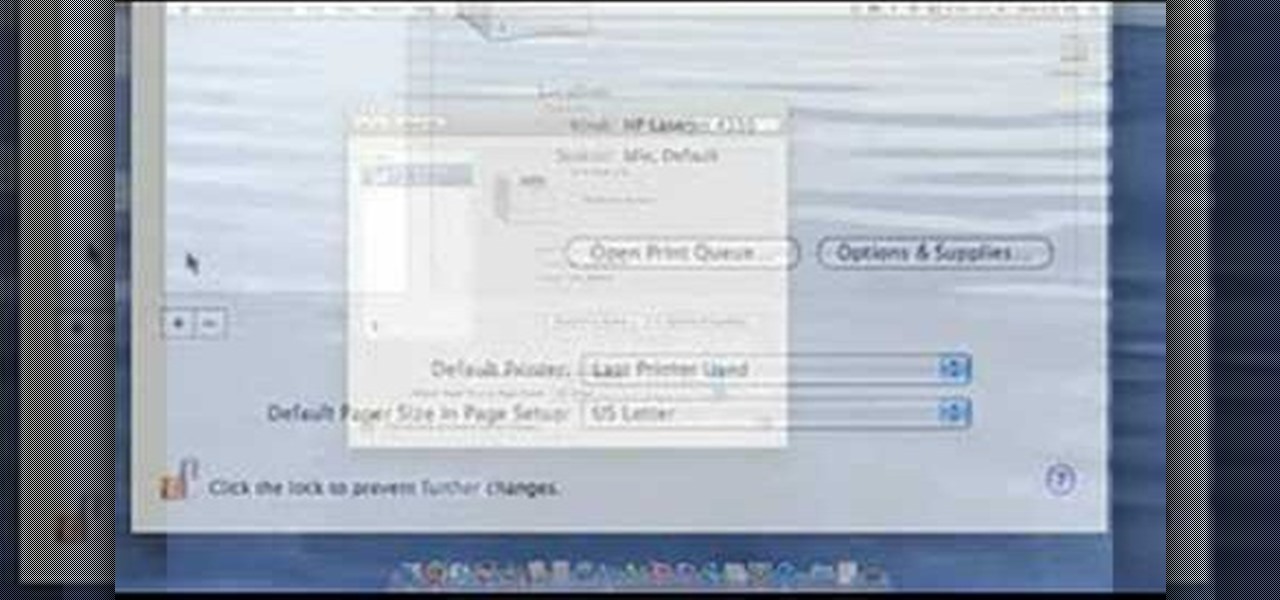
This video demonstrates how to setup a printer on a Macbook Pro.Open the document you wish to open. Go the File menu on the top bar menu and select Print. On the Print dialogue box, you will notice that no printer is selected. Click on the drop down menu to select Add A Printer. Click on the IP found on top of the window. Change the protocol to IPP or Internet Printing Protocol. On the address bar, type in the address of your printer then click on Add. Once done, you can now print your docume...

In this tutorial, we learn how to use GPS and maps on the Nokia N97. From the home screen press the menu key. Then, scroll down and tap the maps icon. After this, tap yes to go online. You can now navigate around the map by using your finger and you can zoom in and out by using the zoom icon. This icon is on the left hand side of the screen. To search for an address, tap the search icon and then tap address or places to choose where you want to go. You will then be shows the GPS and have dire...

A leaky washing machine is a problem that should be addressed quickly. Any access water leaking out of your machine can cause your floor to be slick and possibly create a mess, especially if you have carpet.