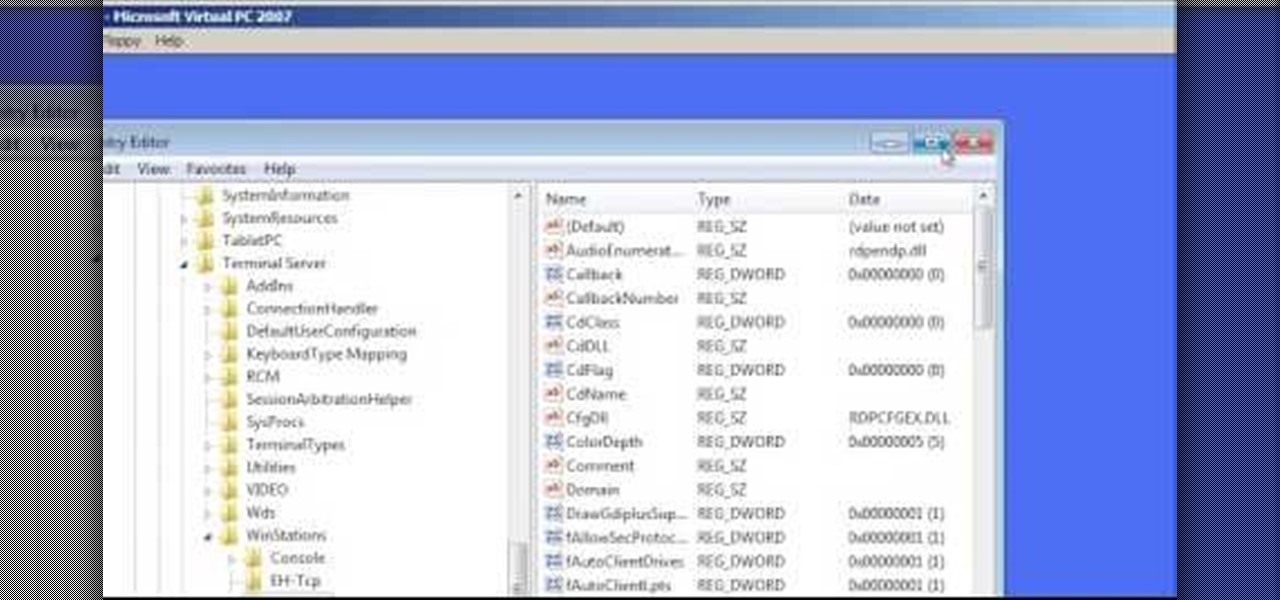
In this Computers & Programming video tutorial you will learn how to change the default Windows Remote Desktop port. It is actually a registry hack. You can check the IP address of our machine by typing ipconfig into the cmd prompt. For hacking into a machine, you should have created a user for the machine and allowed remote desktop to that user. Open up the remote desktop and type in the IP address and it will ask for a login. To hack the registry, click start and type in ‘regedit’ . now go ...
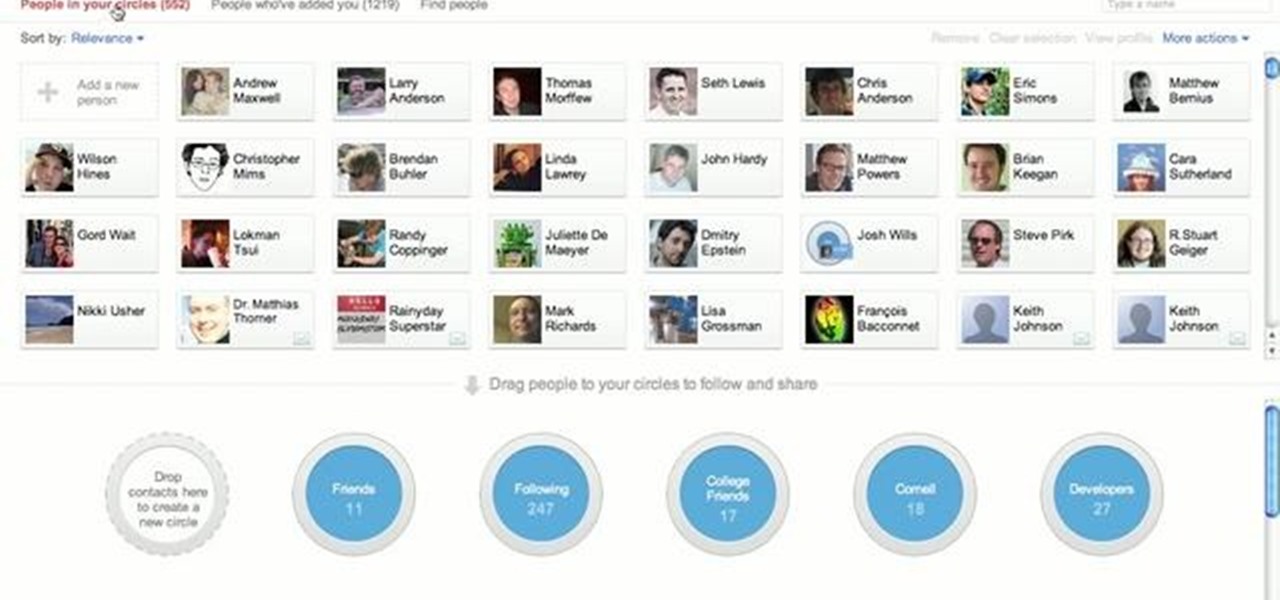
In addition to being a great way to share content and information that are also using Google+, additional sharing features in Google+ allow you to send content and information to other individuals who do not use the service. You can even import your address book to make sharing even easier.

Want to Google Earth-style bird's eye view of a given address? This clip will show you how it's done. It's easy! So easy, in fact, that this handy home-computing how-to from the folks at Tekzilla can present a complete overview of the process in about two minutes' time. For more information, including detailed, step-by-step instructions, take a look.
While Google Maps is useful for finding addresses and calculating directions, it's not, strictly speaking, very fun. Unless, of course, you know how to hack it. This hacker's how-to from Tekzilla will show you how to access a number of Easter eggs and hidden features like a geography quiz game.

The Contacts application on Android-powered cell phones provides a powerful way to manage your address books and keep in touch with friends and family. You can even add and manage multiple accounts from various sources. Watch these tips from Google to learn who to get the most of the Contacts Android app.
If there are words that you use often but Swype doesn't know them yet, you can easily add them to the database of your texting program. In this clip, learn all about adding uncommon or unique words to your Skype dictionary so that you can text even faster. You can even add web addresses, e-mails, nicknames and anything else you use often and don't want to tap out.

Whether you miss the good old days of Telnet or you want to know what hacking was like when security was nothing but an afterthought, Telehack is the game for you. The text-based hacking game is a simulation of a stylized combination of ARPANET and Usenet, circa 1985 to 1990, with a full multi-user universe and player interactions, including 26,600 hosts.

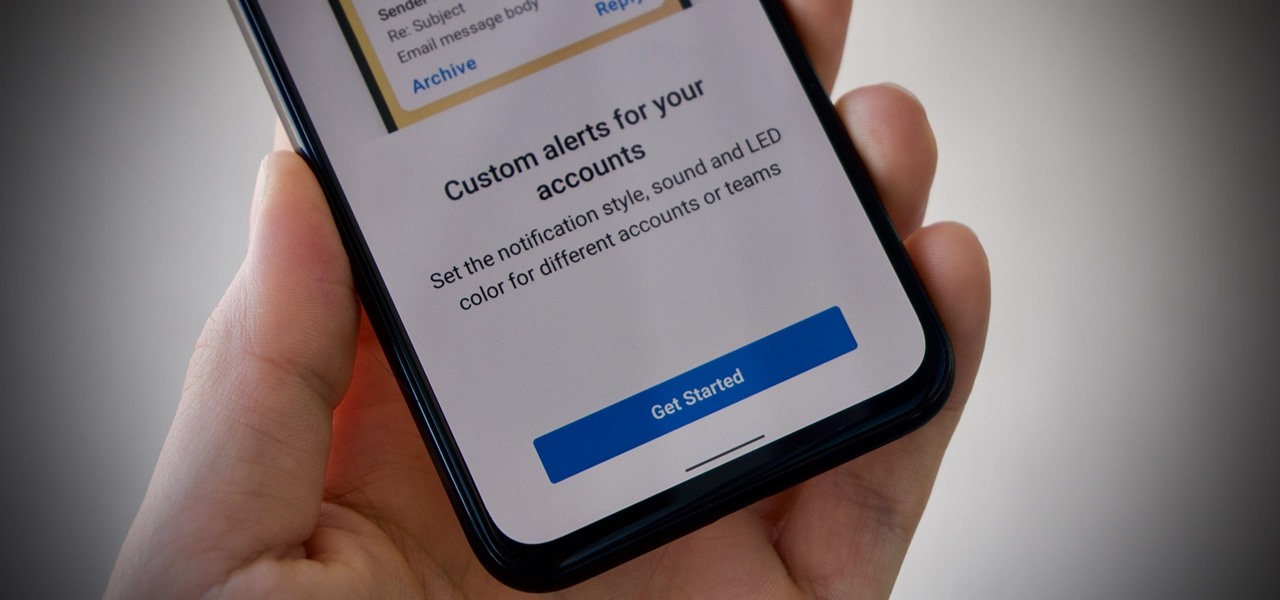
Android is all about customization. That's why it's entirely appropriate that Spark for Android's newest update adds a ton of customization options for your out-of-control email alerts. Now, you can add lights, sounds, and vibrations to notifications, and you can even set specific settings for all of your email accounts.

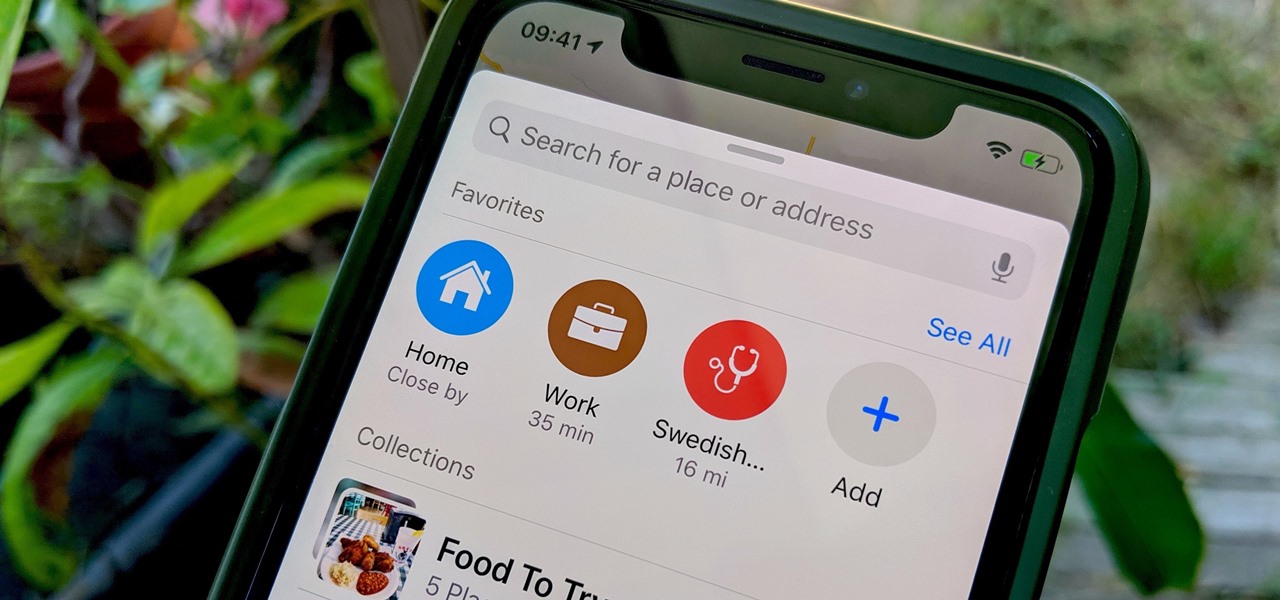
In iOS 13, Apple Maps makes it easier for you to organize essential places on your iPhone, allowing you to save locations as favorites that you can access at a glance.

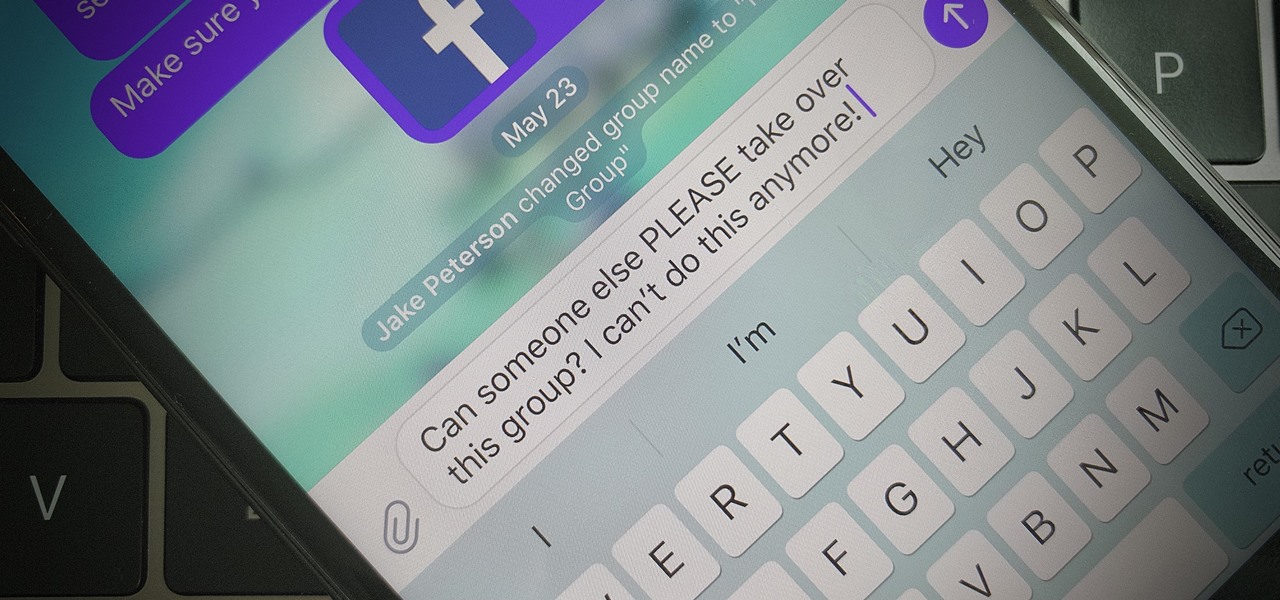
Group chats are fun, effective ways of staying in touch with the many people in our lives. Whether it's the local friend chat or the group from work, we rely on these groups to keep connected. Running one of these group chats, however, can be a monster task. If you're feeling overwhelmed with administrative responsibilities, why not pass on that burden to another member of the Telegram group?

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

Business hours and addresses change, but they're not always updated on Yelp by business owners for the rest of us to see. Showing up when a business is closed or going to the incorrect address is a major annoyance, which is why the company allows us, the customers, to help update business information through the Yelp mobile app on iOS and Android. If owners won't do it, somebody has to.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

With the release of Android 9.0 Pie, Google's focusing on digital health. Digital Wellbeing is a new set of features designed to help you curb your own smartphone addiction. Starting now, the beta version is available, and Google's looking for testers.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

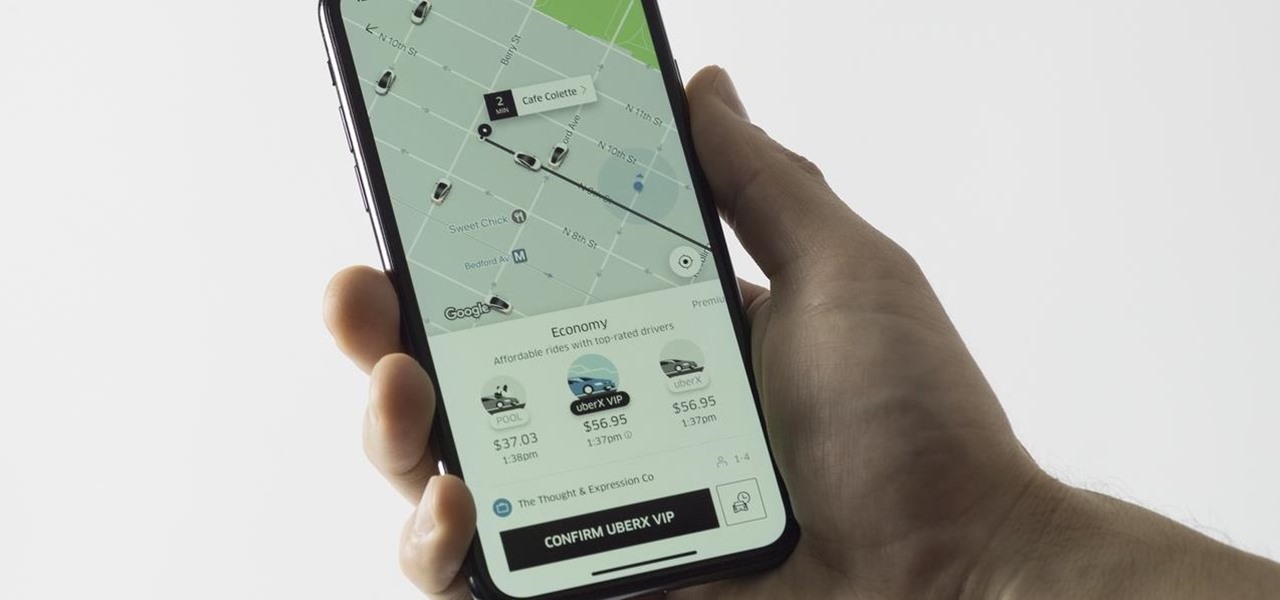
Uber is one of the best ride sharing services out there, allowing you to travel without needing to be tethered to a car of your own. Still, if you're a frequent flyer, you may get tired of entering the same few locations into your app every time you use it. Fortunately, Uber lets you streamline this process.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

In the previous article in this short series, we learned how to find our neighbor's name using publicly accessible information and how to monitor device activity on their home network. With this information at our disposal, it's time to get into installing and configuring the necessary tools to begin our attack on John Smith's computer.

Nobody likes spam, and that's why email apps continue to vie for your digital attention by boasting about new ways to filter and reduce unsolicited messages. Outlook, an already fantastic client for focusing your cluttered inbox, has now joined in on the action, giving its users new, simple tools to fight against junk mail.

Your email is just that — yours. You shouldn't have to worry about other people gaining access to it on your iPhone. Fortunately, Outlook agrees, and has included a way for you to protect your messages with one of two keys no one possesses but you — your face or fingerprint.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

When most people first become aware of Kodi (formerly known as XBMC), they hear about its ability to stream illegal content. But the real Kodi community knows that it's much more than just a haven for pirated material — it's an all-in-one media player that addresses the majority of home theater needs, particularly for those that decided to cut the cord.

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

While it's currently impossible to go back in time, there is something wonderful about being able to undo the stupid stuff that you just did. While this is only really possible in the digital world, it does save you from real-life repercussions. If you've ever sent an email to the wrong person or sent some not-so-genius text messages, you know exactly what I'm talking about.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

Apple prides itself on simplicity, but the company makes downloading video and music files onto your iPad or iPhone an overly complicated process, requiring iTunes and/or iCloud.

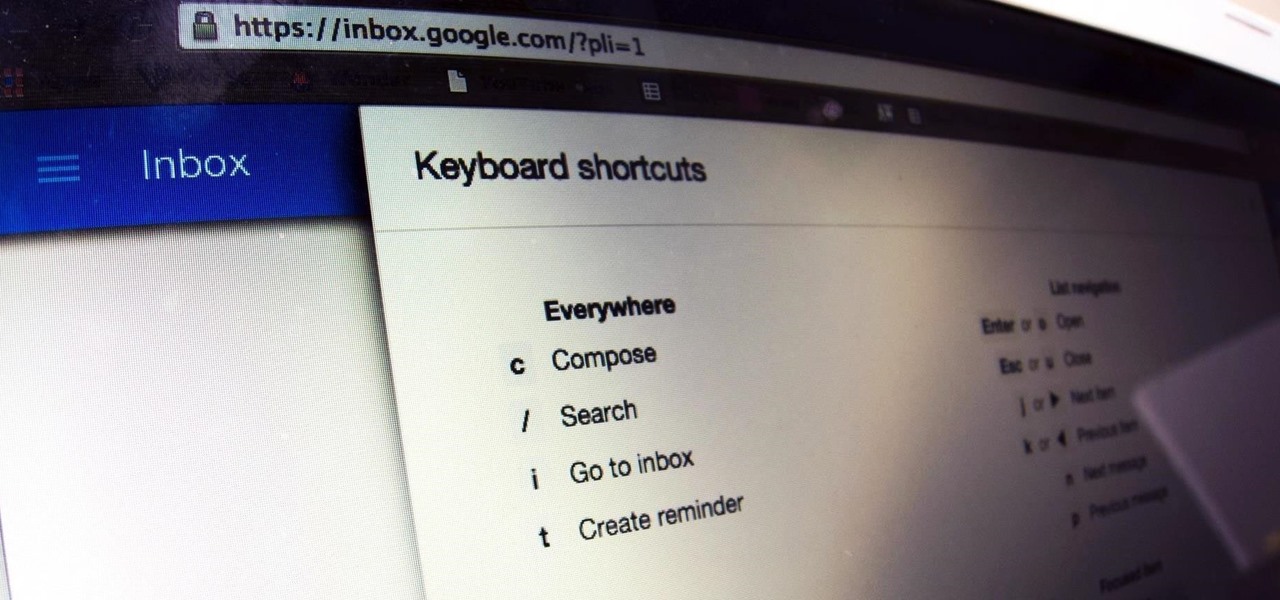
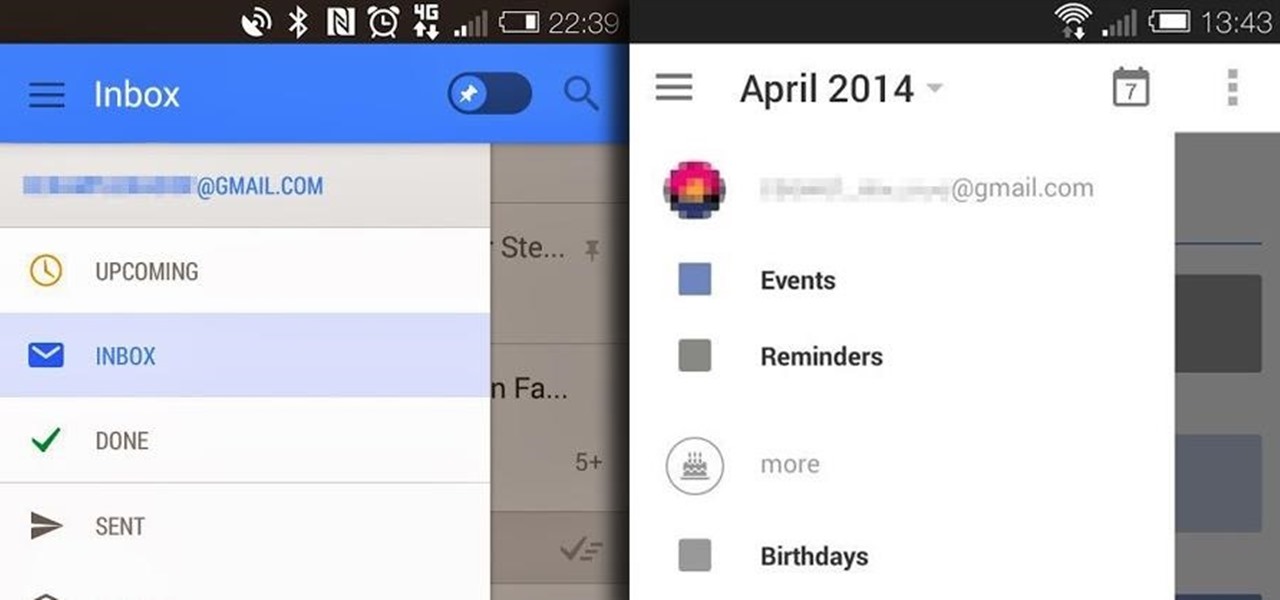
While the new Google Inbox is currently invite-only, if you were able to snag one, you'll want to learn the best ways to navigate it. Google Inbox coins itself as "The inbox that works for you," and after a brief run through of it, we think it's definitely living up to that slogan.

After a few unnecessary U-turns, I quickly realized that Apple Maps wasn't for me, which is why I hate that it opens as the default app any time I select a shared location or an address from Yelp. Copying and pasting the address to Google Maps isn't a huge deal, but it's certainly not as fluid of a process as I'd like.

Say goodbye to your boring stock Apple keyboard, because when iOS 8 is finally released, you'll be able to use Fleksy, SwiftKey, Swype, TouchPal, and other third-party keyboards on your iPad, iPhone, and/or iPod touch.

Staying on the move while managing email is a priority for many of us, from parents to students to business professionals. Seems that Apple had this in mind when improving the stock Mail application in iOS 8, which now includes swipe gestures that make marking messages as read/unread, as well as flagging and deleting, a whole lot quicker.

Shopping online can be as easy as buying cigars in Mexico. You find what you like, ask for the price, and walk away. "My friend! Come back! I give you 10% off. Just for you."

Dropbox, the cloud backup tool that is a mainstay on many of our devices, has added two companion apps to its service. Earlier today, we showed you a glimpse into a new testing version of the Gmail app, with features like pinning and snoozing to keep your inbox in check. Now, Dropbox has released Mailbox for Android, about a year after they purchased the company and its iOS app, with a simple goal: taming your inbox.

Google I/O may still be a couple of months away, and although we don't expect anything groundbreaking—no new Android versions, just fixes to KitKat—we could be treated to some new apps. No, not Pokémon inspired Maps, rather new versions of Google's Calendar and Gmail apps.

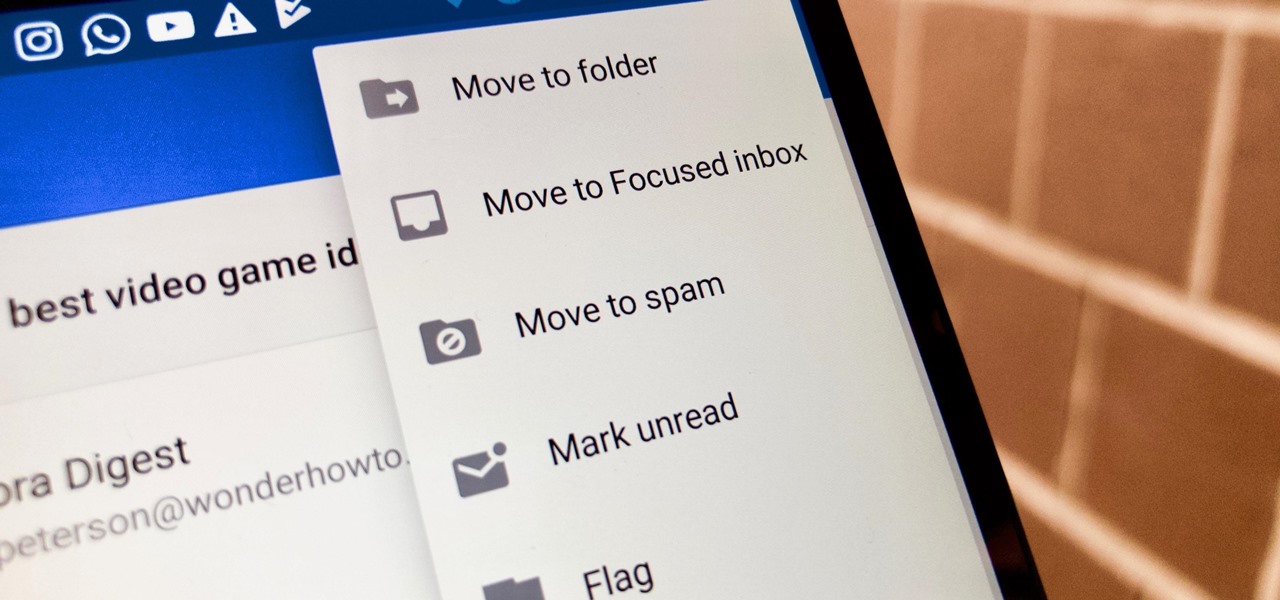
Folders help you to organize your mail in your Gmail account. In this tutorial, we are going to learn how to create these folders.

Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the server and send and receive all the communication between the two.

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

Craigslist is probably the greatest site ever created, and I'm just talking about it's classified section, both awesome and amazingly creepy. Seriously, spend 20 minutes scrolling through the personals and you'll never want to take your eyes off the screen. But I digress—Craigslist is also one of the most convenient places to buy and sell pretty much anything you can think of. I've used it to buy my bed, my old bike (which was stolen!), and my couch. And while Craigslist is great in many ways...

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

The mighty Arduino microcontroller can be used to show children how robots work, it can be used to hack into hotel rooms, or it can be used to let you know when you've got a new job opportunity!

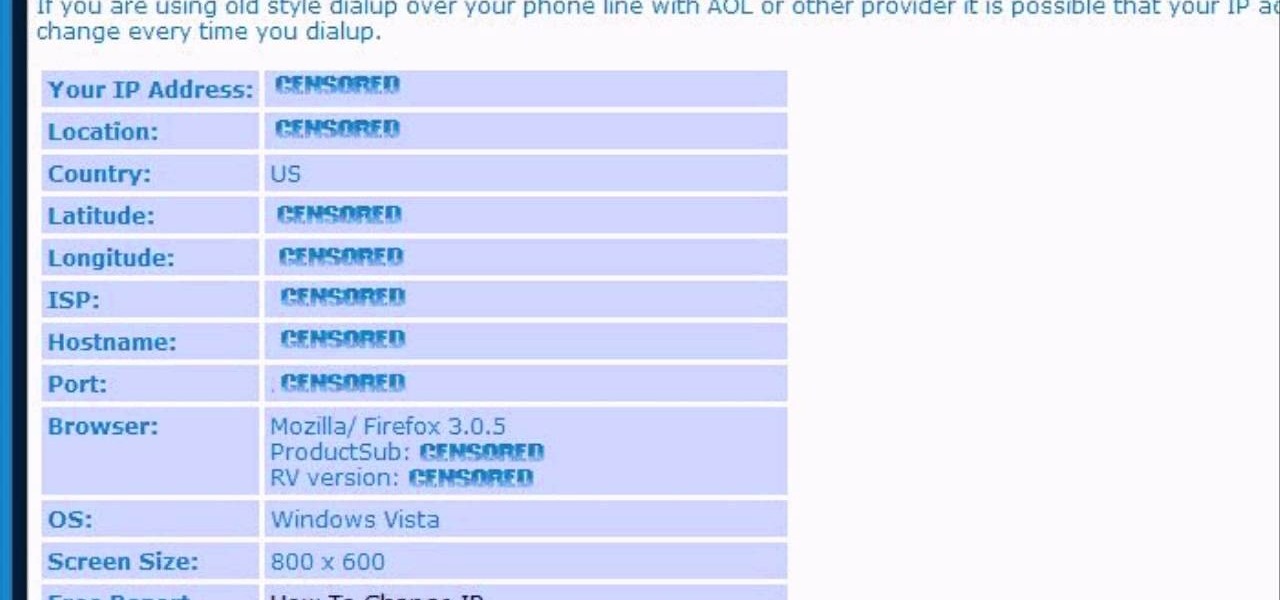
In this video, we learn how to find your IP address. First, start up your computer and open up your web browser. Next, you will type in the site: WhatIsMyIPAddress. Once you do this, you will be led to a new site which will load up your IP information at the top of the page. Once you have this information, make sure you don't share it with anyone else. If someone gets this information, they will be able to hack into your computer and ruin it. They could also access sensitive information and s...