Sarah Austin from Pop17 has been getting a lot of emails recently about how she makes her live show. Well, this is how she does it, so listen up carefully. She covers everything from the audio to lights and green screen.
Learn how Gmail differs from other email accounts and how to make labels and filters in Gmail to organize your mail.

Your iPhone's Mail app has a lot of fantastic productivity features, such as unsending emails, follow-up reminders, opening drafts from almost any view, the snooze option, bulk-selecting messages, and the formatting toolbar, but one of the most helpful ones might just be the one you're not using.

How do spammers get your email? You give it to them. Not directly, no — you sign up for an app or service and happily hand over your email to verify your new account, then that app or service sells your email address to marketers who now know what kinds of apps and services you like.
Many of us install TikTok just to see what it's like, but most of us stay for good. Inevitably, that involves creating an account. The problem is, TikTok assigns you a username, usually based on your email address — an odd choice for a platform made for self-promotion. If you're not happy with your random TikTok handle, you can change it.

It's finally out. After months of testing, iOS 13 is available to install on your iPhone, which means over 200+ new features you can use right now. The update, released on Sept. 19, can be installed over the air or from a restore image using iTunes in macOS Mojave and older or Finder in macOS Catalina. Ditto for the 13.1 update issued on Sept. 24.

An incredible amount of devices use Bluetooth or Bluetooth Low Energy to communicate. These devices rarely have their radios switched off, and in some cases, are deliberately used as trackers for lost items. While Bluetooth devices support MAC address randomization, many manufacturers do not use it, allowing us to use tools like Bettercap to scan for and track Bluetooth devices.

In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users.

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

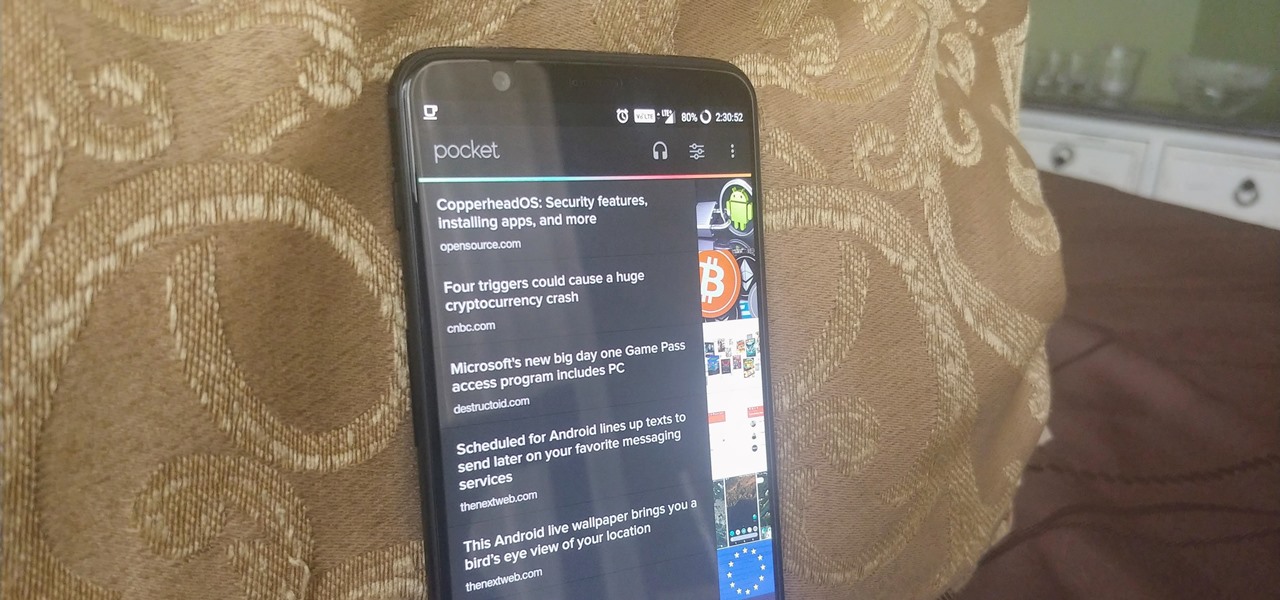
Starting your morning right is an essential first step to a productive day. Whether you're running late, rushing to catch up on the day's news, or lagging behind with early emails, little hiccups like these can have a trickle-down effect and ultimately ruin your day. Like with many problems, though, your smartphone can help.

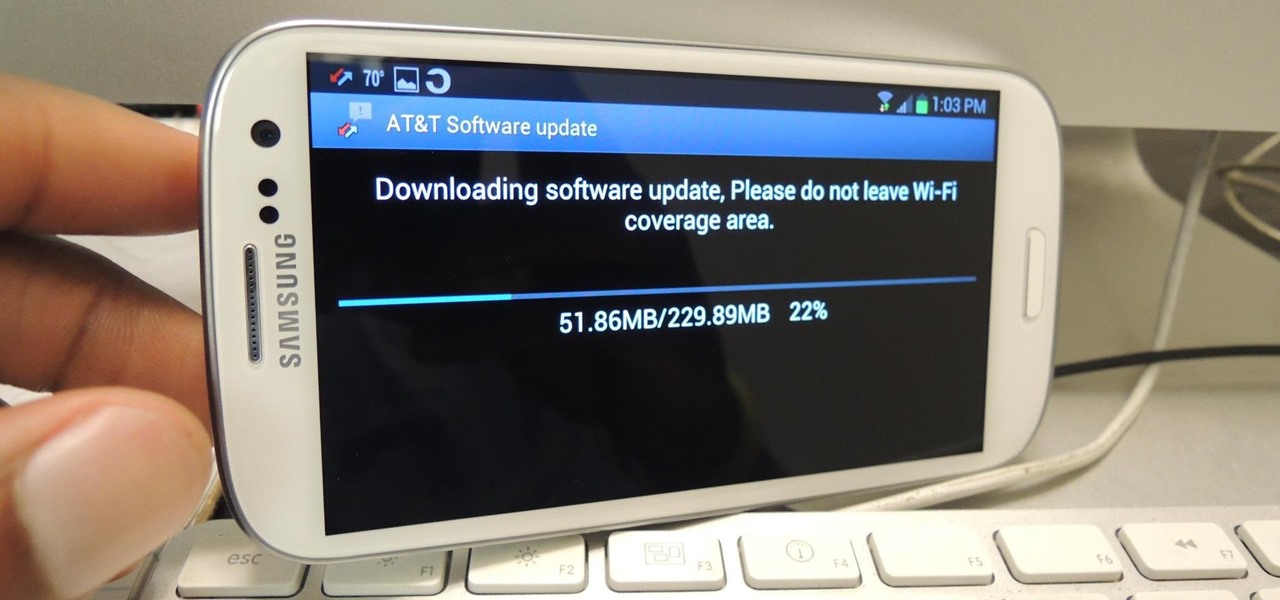
Essential just dropped the Oreo Beta Program for their flagship PH-1 phone. Users have been eagerly awaiting this update as the early Nougat builds of the PH-1 software have suffered from numerous performance issues and lag. The good news is that you can grab the Oreo update today with a few simple steps.

Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.

So, you want to perform an exploit on a victim, but you're not on the same network as their machine. In this tutorial, I'll be showing you how to set up a meterpreter reverse_tcp attack to work over the internet.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Welcome back my networking geeks. In this part we are going to keep discussing about IP Addressing and I hope after you finish reading it you will become an IP wizzard.

Hello there! This will probably be the final tutorial on functions where we will be looking over a method called pass by reference. This technique allows us to modify large amounts of data without the overhead and return multiple values. Let's go!

The end of a weekend can be depressing knowing just how bad Monday morning will be when you get back to work, but that feeling is tenfold when coming back from a lengthy vacation with zero work responsibilities.
Welcome back Hackers\Newbies!

A highly useful, yet unrecognized and under-appreciated feature in Apple's iOS 8 is the ability to seamlessly convert incoming texts regarding future dates into calendar events. Messages like "Let's chill tomorrow" can be tapped on and quickly added to the calendar. It's convenient and easy, but unfortunately, not available on most Android devices. However, it's pretty easy to get using Inviter (SMS to Calendar) from developer Sergey Beliy.

Do you take your notes on a word processor while browsing the web? Well, stop. There's an easier, less RAM hungry way to take notes by turning the tab of your web browser into a notepad. Whether it's an email address, a line of code, a new how-to, or an idea you don't want to lose, you can easily jot it down without slowing down.

Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.

For my money, one of the greatest improvements brought about from the smartphone revolution is the advent of visual voicemail. No longer do we have to slog through dial menus or trudge through every single message to get to the next. We can just look at our messages, right there on our screens, organized neatly like emails or text messages.

Using a phone that hasn't been updated is like playing NBA 2K10 in 2013. Everything works fine, but you're missing all those new features and current rosters.

Previously, if you missed a call or text on your old Samsung Galaxy S3, there was a white LED notification to let you know. It's a nice feature that most smartphones have, but wouldn't it have be nice to know what kind of notification it was before picking up the phone?

I recently had my iPhone stolen at public park and did everything I could to locate it, but with Find My iPhone disabled (I know, what an idiot) and no exact address to give to the police, I had about a .00000001 percent chance of getting it back.

There are many ways you can protect your computer from unwarranted access. For instance, you can use Lockscreen Pro to lock your Windows 8 computer and then have the program snap a photo of the culprit using your webcam.

Megaupload was one of the very first file-sharing sites I ever used. But since 2005, the beloved (and pretty gangster) Kim Dotcom, has been in a legal battle with the U.S. Justice Department over copyright infringement.

Being able to run mobile apps on a computer is nothing new. Maybe you don't have a mobile device, or maybe you just like seeing the apps on a larger screen. Whatever the reason, with programs like Bluestacks, you can use your laptop to Instagram, play Angry Birds, and run countless other apps made for smartphones.

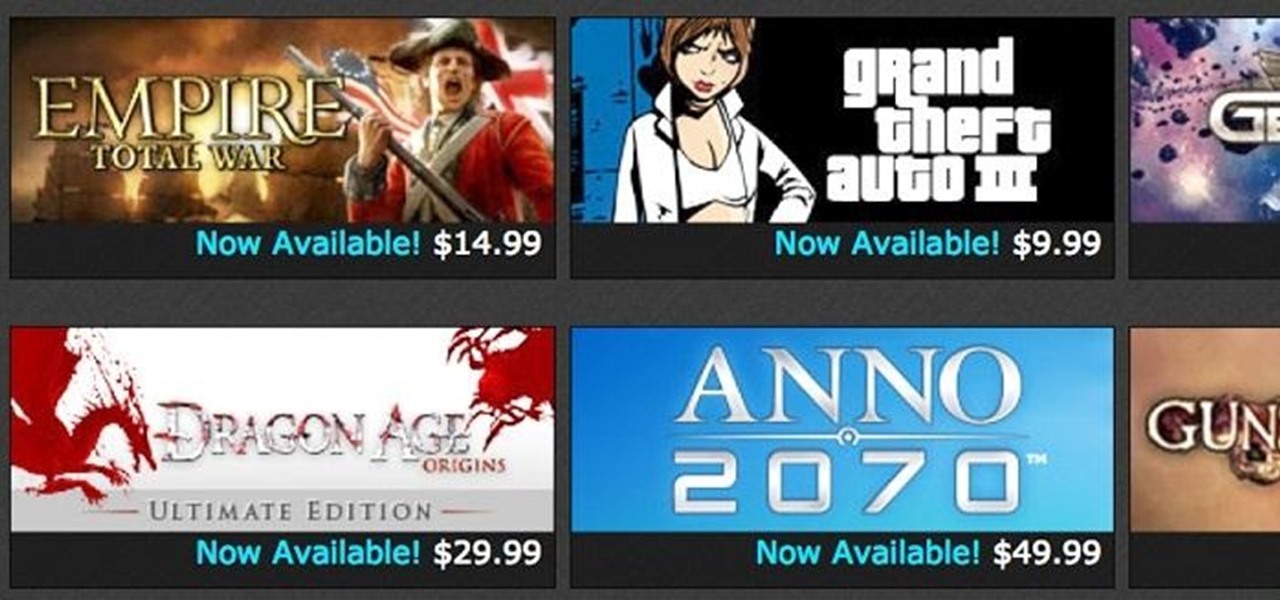
As an avid Steam user, I'm faced daily with high prices for all of the games I want to download and play. It's gotten to the point where I don't even bother going on Steam altogether because I might end up spending a bunch of money I don't have.

Emoji is the Japanese term for picture icon characters used in electronic messages. Like emoticons the icons have a wide range of characters. Though Emoji has been integrated since iOS 5 the keyboard is not visible. I'm going to show you how to add the Emoji character keyboard to your Apple iPhone, iTouch & iPad. Adding the Emoji keyboard in IOS will give you colorful character, smileys and emoticon keys to use in emails, iMessage messages and chat apps. Upon adding the new keyboard you will ...

Feeling nostalgic for Super Mario Kart, but don't want to fire up the old Super Nintendo? Never fear, with a free Flash-based emulator called SNESbox, you can relive the 90s and play all your favorite games right from your browser, without having to install anything. With 1,861 games, if there's something made for the Super Nintendo that you want to play, they almost certainly have it. Sure, there are tons of emulators you can use, but SNESbox is different in that it gives you the ability to ...

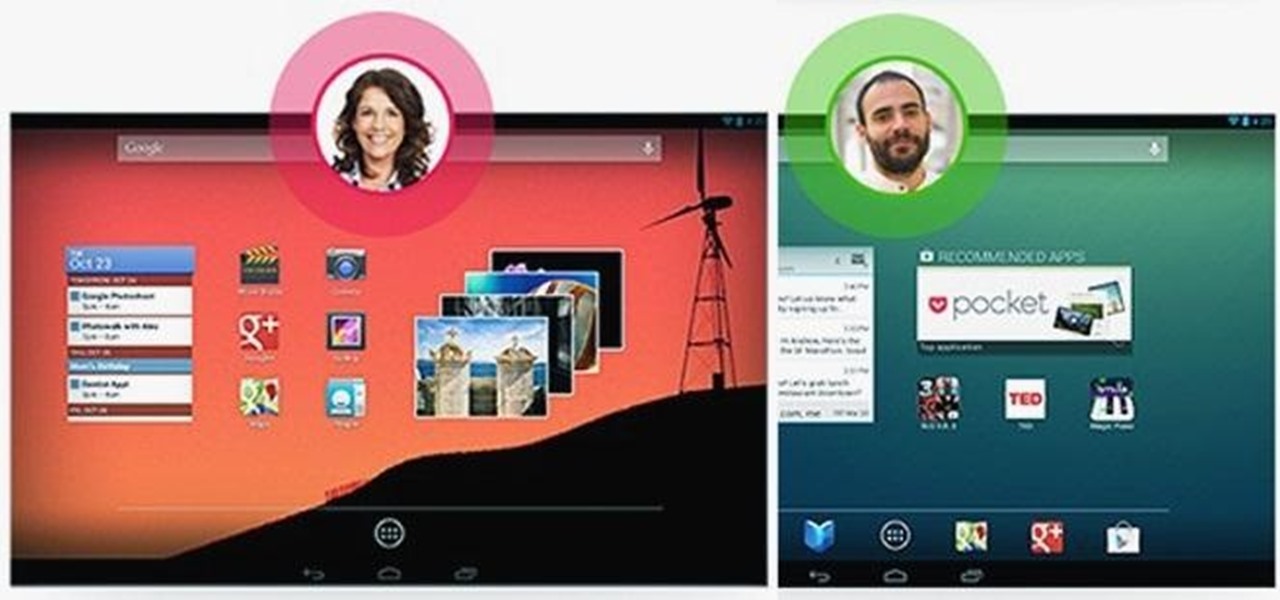
The most recent update for Android's Jelly Bean has some pretty cool new features, like better panoramic photos, gesture typing, and wireless sharing. From a security standpoint, though, the best new feature is the ability to add multiple users to one device. You can create up to 8 different accounts on Android tablets like the Nexus 7 or Nexus 10, so besides saving time hiding or protecting sensitive data, it could also save you some money. You can share a device with your family, kids, or s...

Most of the spam messages are commercial advertisements, phishing websites and get rich quickly messages that asks users to provide personal details and other confidential information.Spam filters in Gmail prevent its users from these spam messages and restrict them to enter in user’s Gmail inbox.Generally, it acts like a firewall between spam messages and Gmail Inbox.Gmail filters detect the sender’s email address and accordingly send the received messages in Inbox or Spam folder.

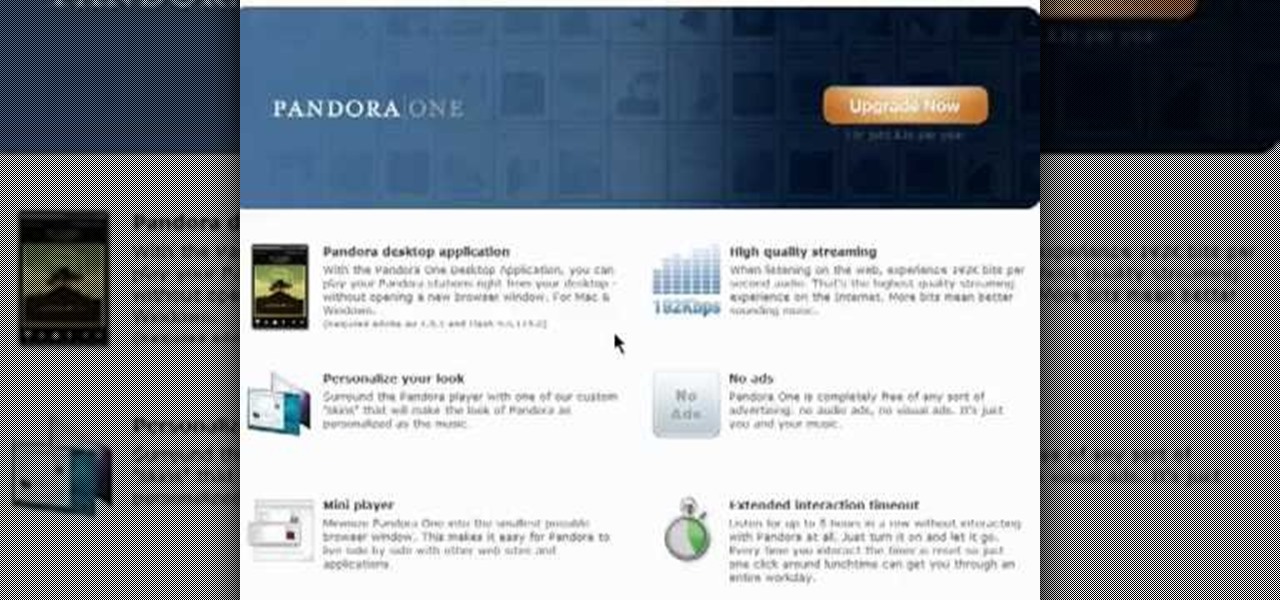
Looking for a quick guide on how to edit your account information when using Pandora Radio? This brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started changing your own account information on Pandora, take a look.

Learn how to use the various messaging features available on a BlackBerry phone. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

Looking for instructions on how to use the various messaging features available on your Samsung Intensity II mobile smartphone? You're in luck. This free video tutorial will see that you need everything you need to know to send and receive email and SMS text messages. For thorough instructions, watch this cell phone guide.

In this free video CSS tutorial, you will learn how using attribute selectors easily add images to download links and email links. Whether you're using a fancy WYSIWYG (or what-you-see-is-what-you-get) page editor like Adobe Dreamweaver CS5 or a barebones text editor like Notepad, if you want to build websites, you'll need to have some understanding of HTML (for the structure of your web pages) and CSS (for their style). And this free coder's guide will get you started along that path.

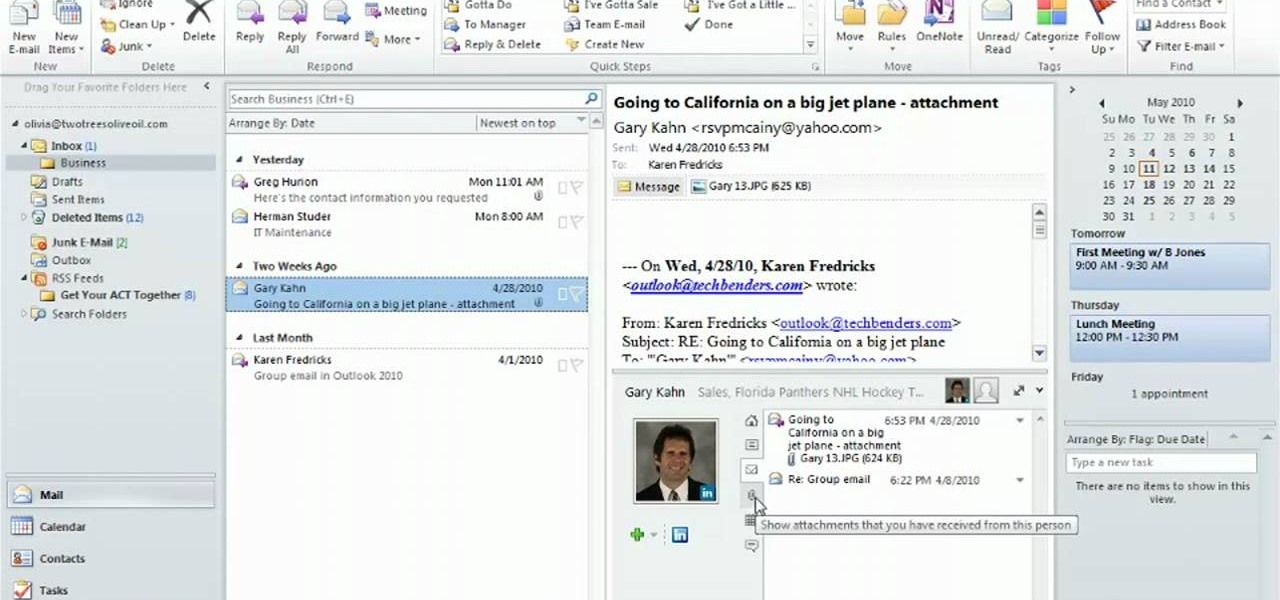
Use the Microsoft Office 2010 Social Connector tool to reach out to friends in your favorite social networks. Whether you're new to Microsoft's popular email and scheduling application or a seasoned MS Office professional just looking to better acquaint yourself with the Outlook 2010 workflow, you're sure to be well served by this video tutorial. For more information, and to get started using the Outlook 2010 tool for yourself, watch this free video guide.