How To: Resize photos in Windows using Google's Picasa
This video tutorial from adamstechvids shows how to resize photos in Windows using Picasa application.


This video tutorial from adamstechvids shows how to resize photos in Windows using Picasa application.
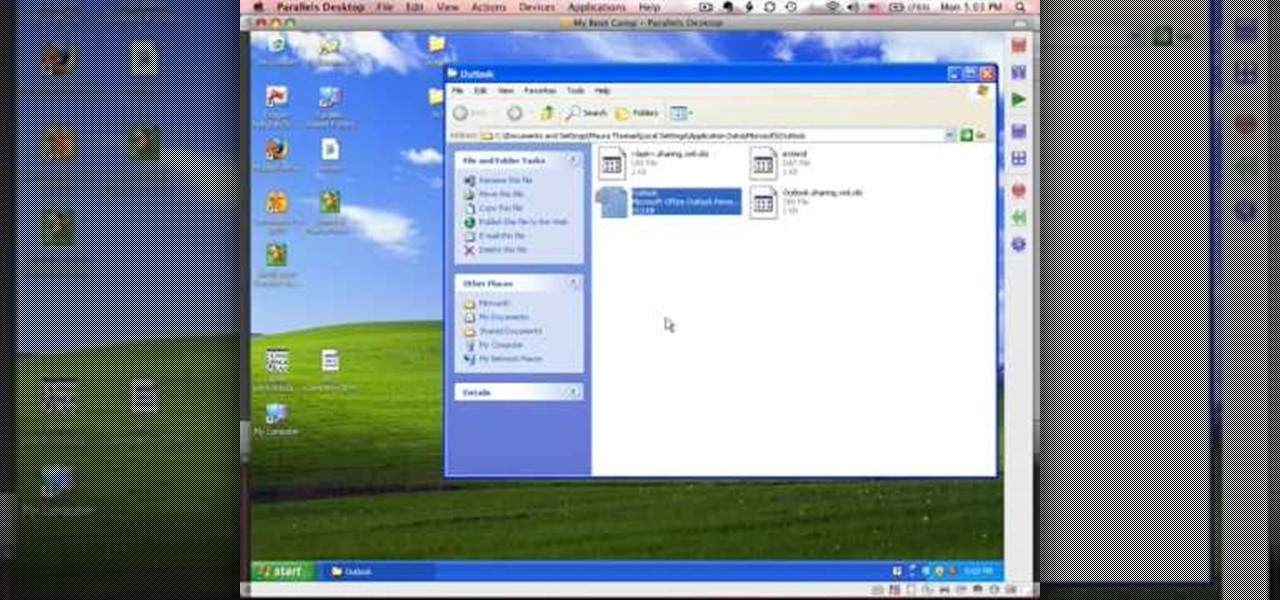
This tutorial describes how to backup the PST file of Outlook.

While it may be tempting to tell your boss where he can stick his letter opener when you’re ready to quit, it’s not a great career move. You will need a job to resign from, good stationery, acting skills (optional). Submit resignation. Submit resignation.

Job applications should be taken seriously, and filling them out with correct information, as well as specific details that make this application stand out, is an art form. Fill out job applications with tips from a career adviser in this free video on job guidance by following the instructions of the application, making it legible and addressing the value the applicant will bring to the company.

This video includes instructions on how to get your PlayStation Portable (PSP) onto the BGSU wireless network.

Watch this helpful electronics tutorial video to learn how to quickly access the Safari address bar on an iPhone. This how-to video, geared primarily toward new iPhone users, will make using quick URLs to browse the internet on an iPhone very easy.

A tutorial showing how to set up a free dynamic DNS address with DynDNS.org and configuring the home router/firewall to forward traffic to your webserver.

The first of a two part series on setting up your linux server and network for external access through your cable modem or DSL. Covers modifying the Linux servers network setting to a static IP address.
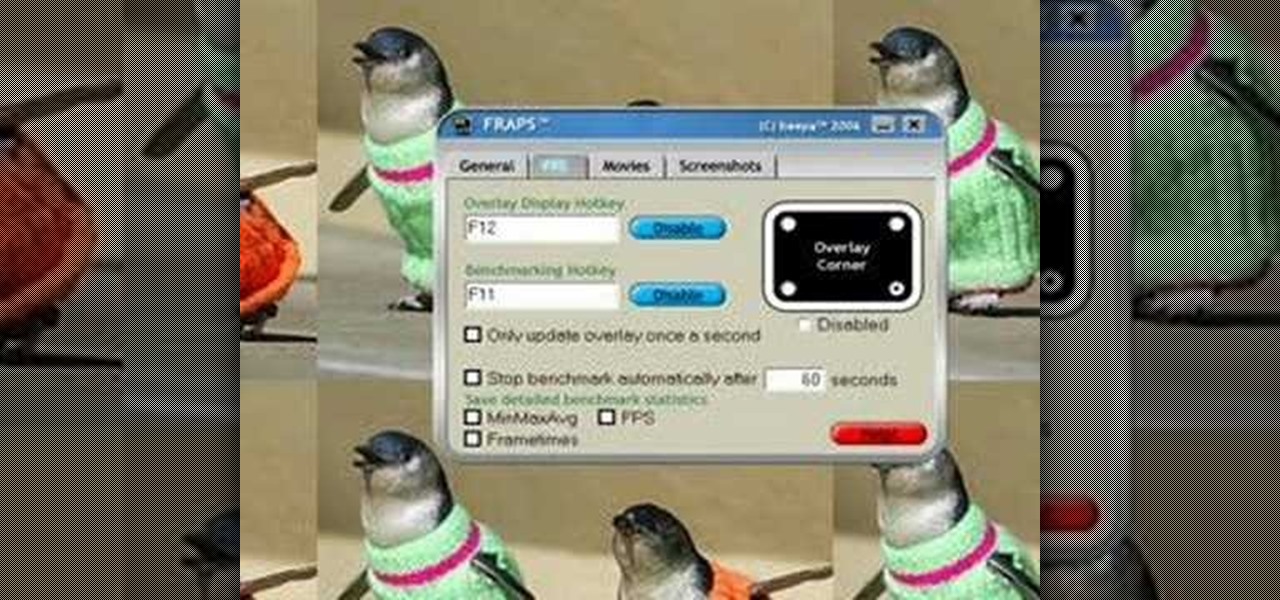
This tutorial details how you can use a program known as FRAPS to record your video games. The second video in the sequence details questions not addressed in the first video.

This is an awesome liquid dancing tutorial for novices, focusing on tips and addressing common mistakes. Stick to the rhythm

This video addresses the consonants of Hindi from velars to retroflexes, including the writing system (devanagari script). It is concluded by part 4 (b). Please watch the videos on Hindi phonetics before this part.
There has been an update with the NES emulator, so you have to put the ROMs in the /var/mobile/Media/ROMs/NES folder, and not the /var/root/Media/ROMs/NES folder.

Dave shows you how to address problems with grubs which can destroy your lawn.
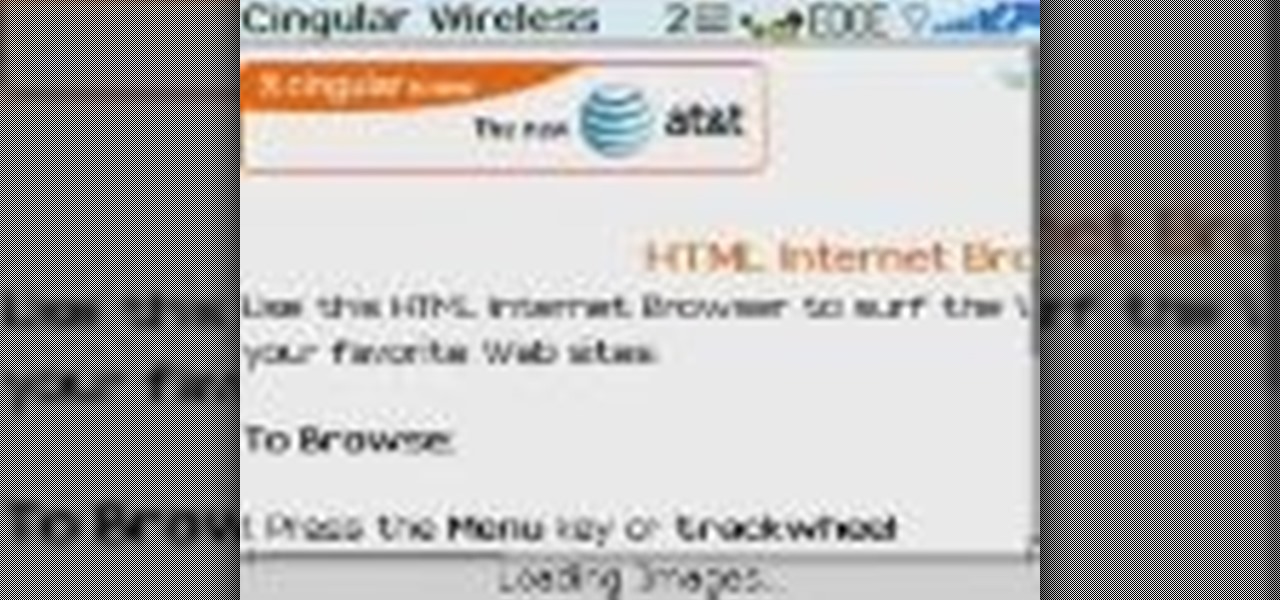
In this video, Jonathan Cohen demonstrates how to surf the web using a BlackBerry 8800. The explains how to start up the Internet on the cell phone, how to input an address, and give some hints on using the browser.

Confused by TikTok? Trying to grow your Instagram fanbase? Aiming to create the perfect Facebook ad? Growing an audience might be challenging, but with the right strategies, it is possible — and fun.
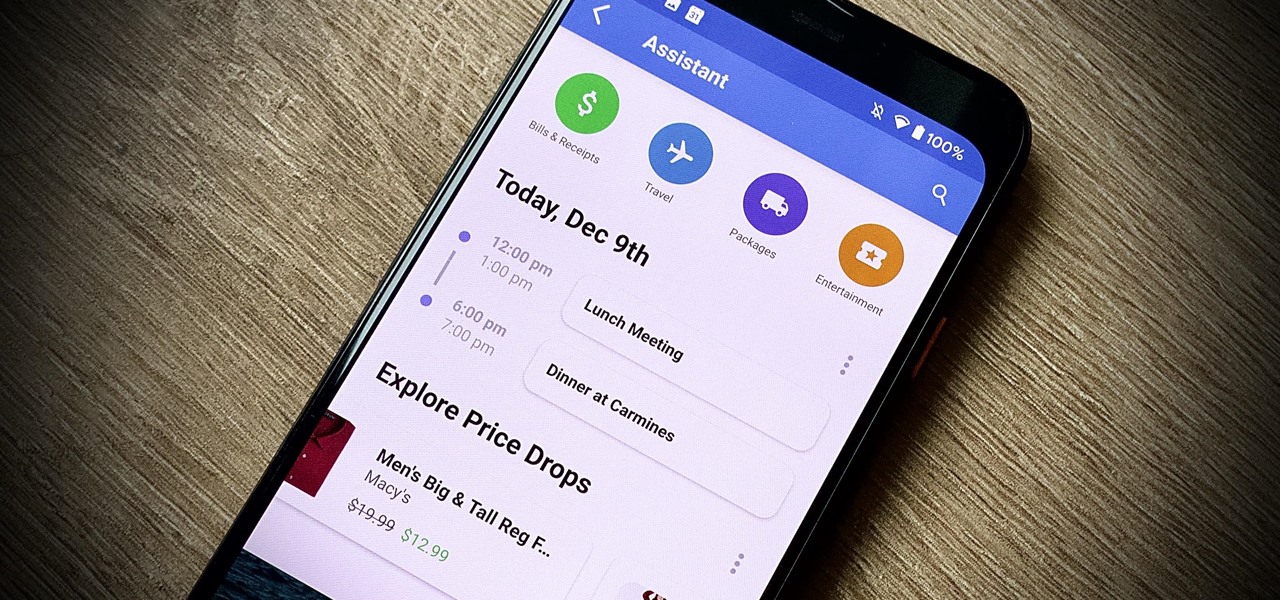
Edison Mail's big Assistant update means more features and functions for you in a convenient, efficient package. One of the most significant changes to come with the 1.17.0 (iOS) and 1.12.0 (Android) updates is calendar functionality for all connected email accounts. Other apps, like Spark, have had this for some time, but we're excited that Edison has finally jumped aboard the bandwagon, too.
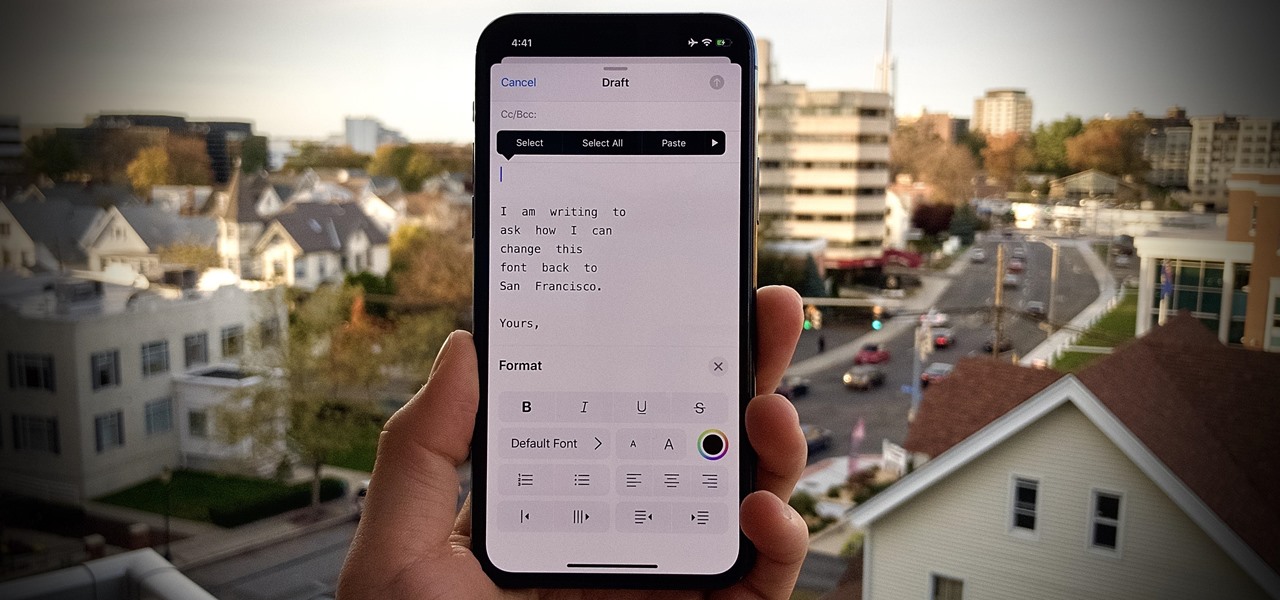
One of iOS 13's coolest features is the ability to download, install, and choose fonts in select apps like Pages and Mail. However, you might notice an issue when writing an email with a custom typeface: there's no option to return to the default font. What gives?

Apple released iOS 12.3, the latest version iOS 12 for iPhone, on May 13. Great features to know about include Apple TV Channels such as HBO and Showtime that you can subscribe to in the TV app, support for audio, image, and video streaming to AirPlay 2-enabled TVs, and the ability to use Apple Pay to pay for content and subscriptions inside Apple's own apps.

In case you thought the long and unfortunate story of ODG was over, hold on, there's one last chapter to tell.
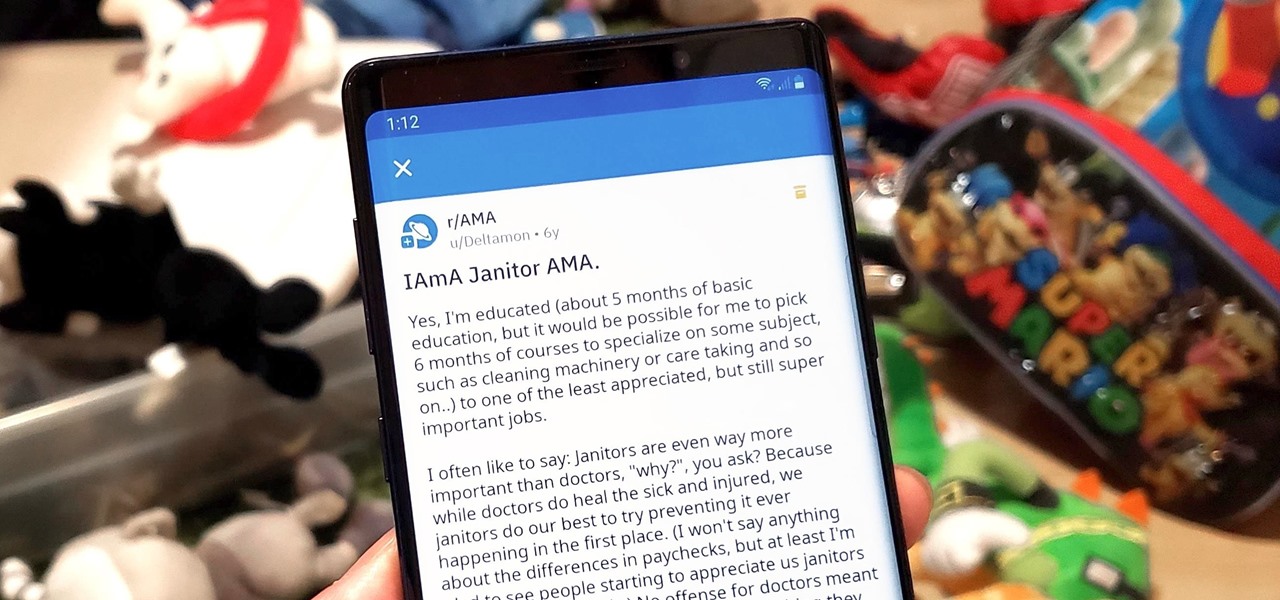
Short for Ask Me Anything, AMA threads are one of Reddit's signature features. They enable you to directly interact with a whole range of interesting personalities, from common folk with amazing life experiences to influential celebrities that help shape politics and culture.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.
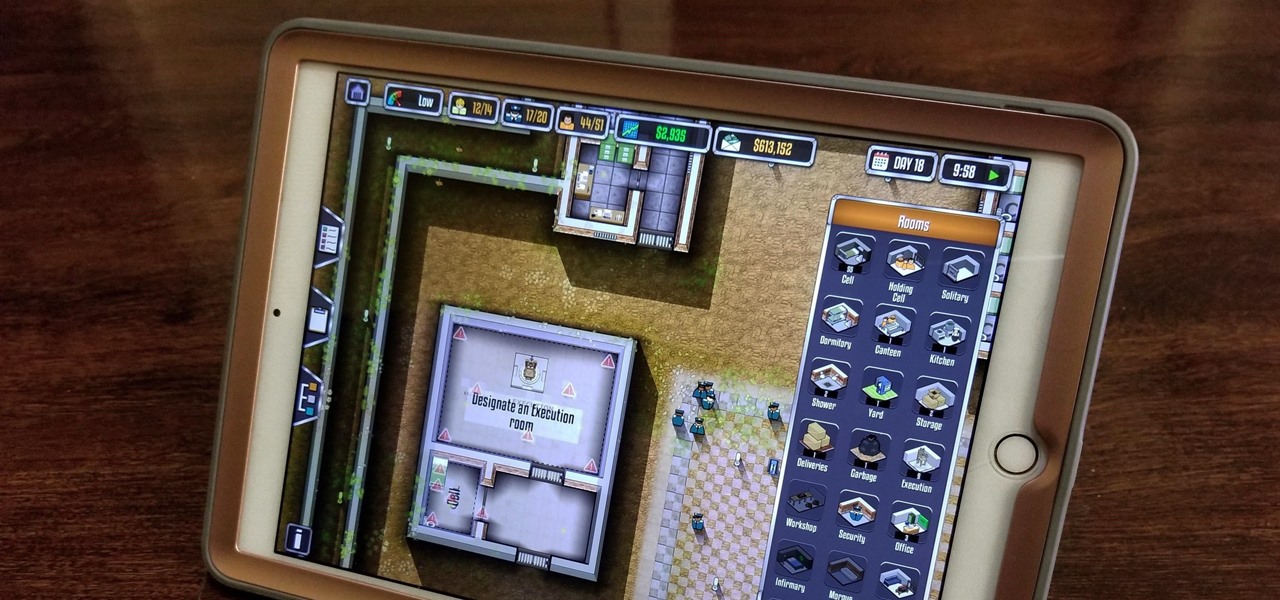
Prison Architect, the BAFTA winner for the Best Persistent Game in 2016, has finally soft launched on iOS. Originally a PC game, Prison Architect lets you build and maintain a maximum security prison. Comparable to running a small city, the game has you manage an ever-expanding correctional facility and contend not only with violent offenders and ever-present prospect of a chaotic riot, but also more mundane affairs like balancing the prison's budget and employee payroll. In addition to the s...

Fans of rhythm tap games and traditional one-on-one fighters finally have something to bring them closer together. DuelBeats, a fighting game that lets you perform moves by tapping to the beat of a song, has been released as a soft launch for both iOS and Android in New Zealand, Australia, and Singapore. Just because the game is exclusive to those regions doesn't mean we can't try it out for ourselves, and with a little hackery, it's entirely possible to do so.

Fans of fighting game series such as Street Fighter and Mortal Kombat are in for a treat! Skullgirls has entered the crowded field of the mobile fighting genre and has touched down in the form of a soft launch for iOS devices, which is now available for download in Canada and the Philippines. But don't let this limited release stop you from trying Skullgirls out, as it's still possible to acquire this little gem with a little finagling.

Jam City's Panda Pop was a great success that helped millions of users waste vast amounts of precious time with its bubble-popping panda cuddliness. Not wanting to mess with success, Jam City has now simply re-skinned the game to feature all the beloved characters from Charles Schultz's timeless Peanuts universe, complete with its relaxing soundtrack and a new name—Snoopy Pop.

The Meta 2 developer kit has finally begun shipping! Gary Garcia, the senior director of customer success at Meta, just sent out an email that they are shipping out to the first round of preorder customers. Waves will be building from there, up to far higher manufacturing rates near the end of Q1 of 2017.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

In this series you will learn how to use PHP to perform attacks, gather information, and setup backdoors. Along with performing attacks you will learn how to protect yourself from them. In this part you will learn about PHP as well as install Apache and PHP. What you'll need for this series

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.
Greetings null-bytians. Say you have been able to penetrate your neighbour's AP, and of course you had spoofed your MAC address. Now you go on and test to see with excitement if the password really works and the MAC is still spoofed. You login successfully and you browse the web forgetting to check what your current MAC is. Well, if you may do an ifconfig command, you will see that your permanent MAC is being used. Oh!! and guess what, ... your real MAC has been logged. Even though there is t...

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

Social Engineering was mentioned a few times here on Null Byte, but not very many explained what it is, or how to do it. I love this quote because it's true: Social Engineering is the key to carrying out client side attacks, and all you need is a little creativity!

A recently discovered bug in iOS 8's Mail app by Jan Soucek can allow the maliciously-minded to quite easily phish your iCloud password without you ever thinking something has gone awry. Using a bug that allows remote HTML content to be loaded in place of the original email content, unsuspecting victims would be prompted for iCloud credentials in a popup that resembles the native one found on iOS.

Smartphone users often wish for a privacy, where no one is able to poke his/her nose in their personal stuff. Unfortunately, none of the smartphones have been able to guard their privacy in this fashion. Smartphones usually come up with none or almost negligible built-in security to serve your purpose.

We all know that opening our work emails at home is a bad habit. Yet reading and responding to emails every time your iPhone dings is worse than you might realize. Not only are you extending the workday, but you are also sacrificing your ability to perform on a daily basis.
One of the biggest improvements in Mac OS X Yosemite came to the Spotlight search feature, allowing users to not only search through their applications, but also their emails, text messages, iCloud, and the web.

Yellow buses are beginning to trickle into traffic. Retailers are pushing pens, pencils, and notebooks. Grumbling Facebook statuses run rampant through your feed. Surely you recognize the signs—school is starting. For some, it already has.
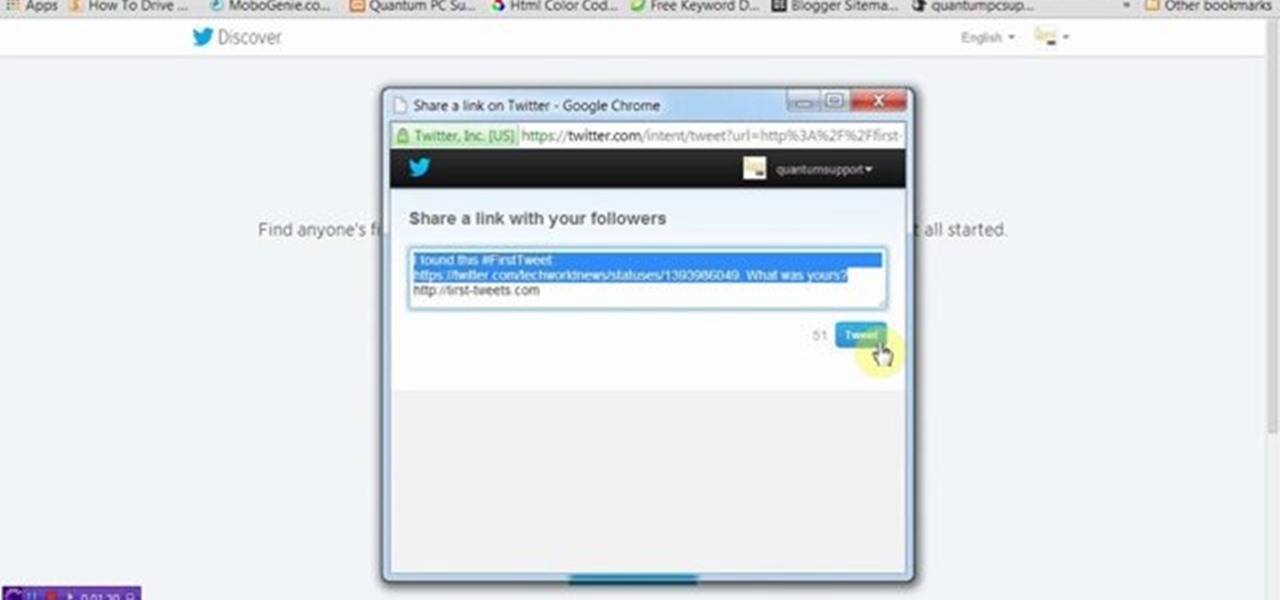
This tutorial video will show you how to find first tweet of any user in Twitter. You have to type first-tweets.com in address bar of your browser. The site will be redirected to discover.twitter.com/first-tweet page. Just type any user name and twitter will show the first twit of that user. Watch the video and try it yourself.
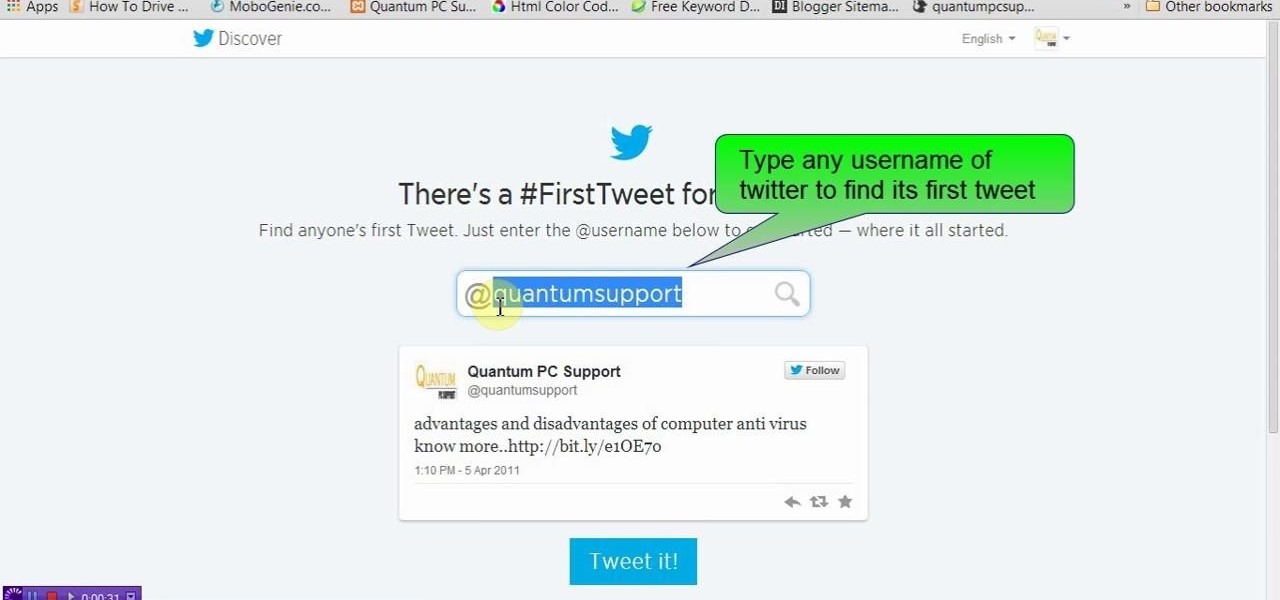
This video will show you how to see first twit of any user in twitter. You could type https://www.first-tweets.com in address bar and the site will be redirected to another place https://www.discover.twitter.com/first -tweet page. You have to enter the user name and twitter will fetch the first twit of that user. Watch the video and employ it yourself.